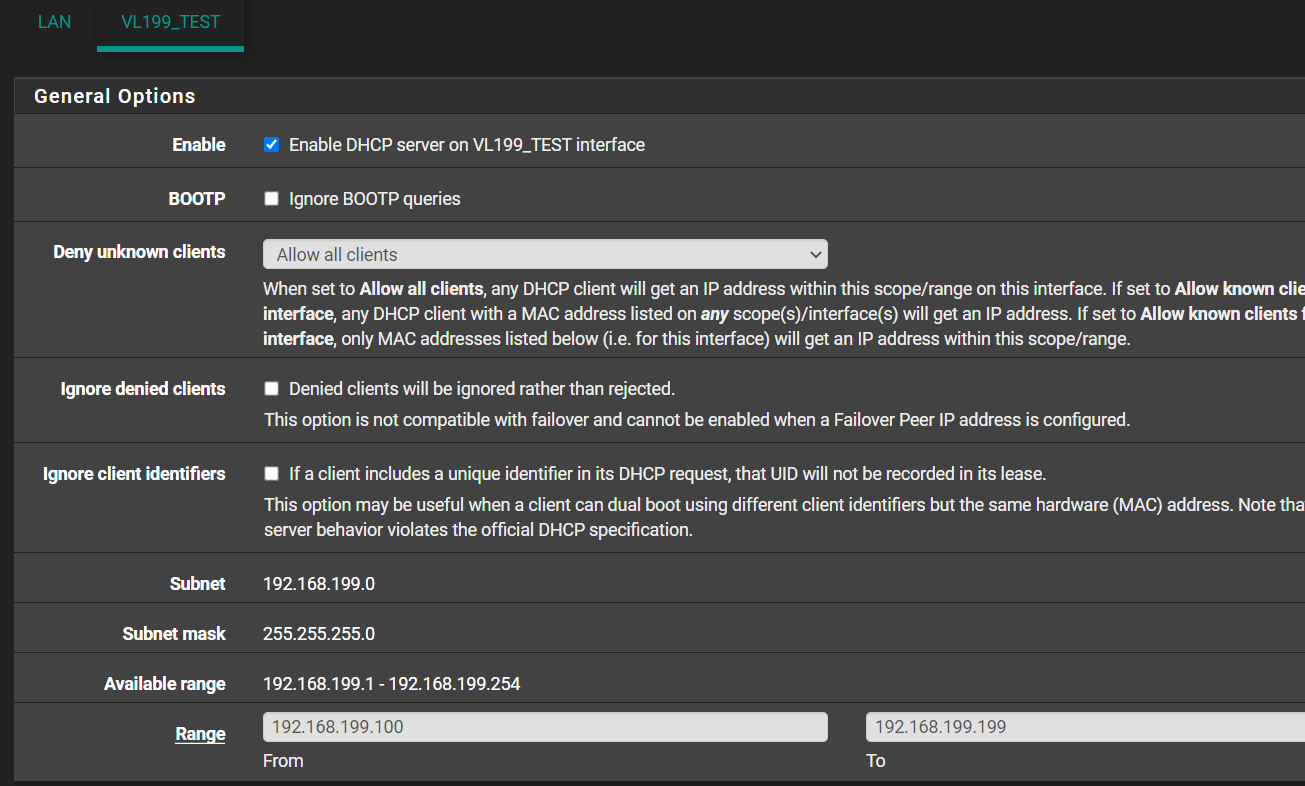
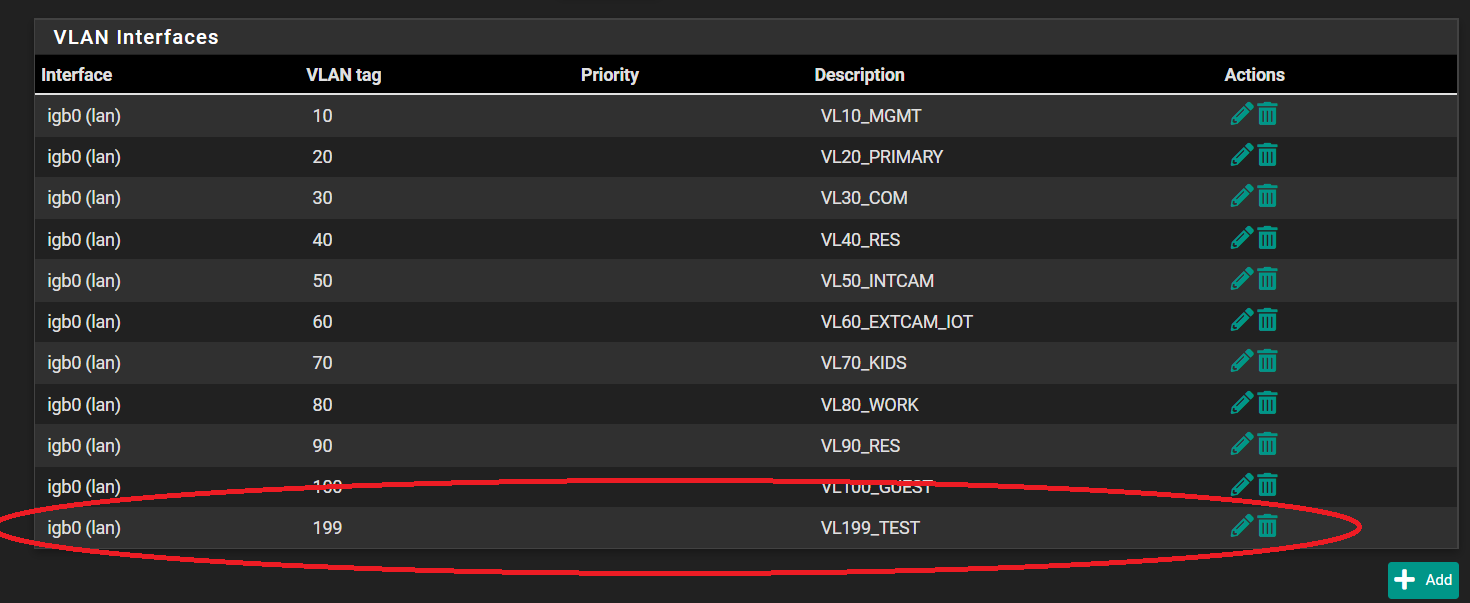
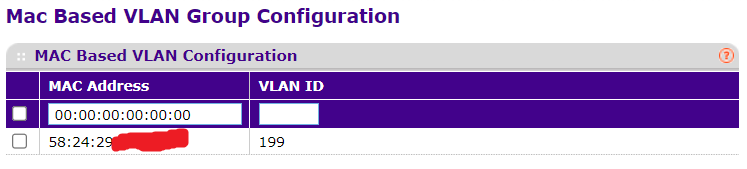
Can't get IP on VLAN
-
@rcoleman-netgate said in Can't get IP on VLAN:
You cannot pass VLAN traffic on port 9 without the VLAN being at least tagged.
When I set port 1 (pfsense) to T (tagged) and the rest, including the AP port 9, to U (untagged), then I got the behavior I wanted. Is this not expected? (This screenshot shows the config that seems to work.)
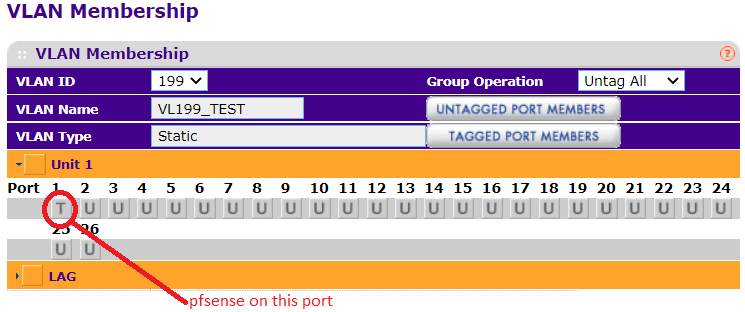
Tagging port 1 (pfsense) and leaving the rest of the ports blank does not give me the behavior that I want. (This screenshot shows the config that does not seem to work.)
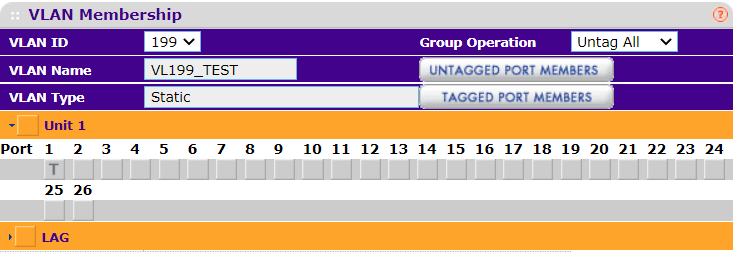
I am not sure what the difference between "U" and blank is in my switch...
-
@laplacian Blank = not assigned. U = Untagged. T = Tagged
Tagging = the VLAN appears in the ETH packet.
If you don't want 199 traffic on a port do not assign the VLAN to the port (make it blank). If you want ALL the traffic on the port to be untagged (basically what you would do in a WAP that does not have VLAN capability but should be limited to a VLAN upstream) or a single device that gets on that VLAN (like a security camera, desktop, etc.) you would have it untagged. If you are passing many VLANs over a port you will want them tagged -- you could send all untagged traffic but that's how you get the wrong DHCP address to appear on your device.
You cannot have MAC-based VLANs without tagged VLANs - you can have MAC-based access on a WAP (typically) but without 802.1Q support on a device you can't do VLAN assignments on the device and it has to be controlled on the port itself.
-
@rcoleman-netgate said in Can't get IP on VLAN:
If you are passing many VLANs over a port you will want them tagged
I think this is the case that I'm in. I'll want many VLANs on a single switch port via my AP. (I'll have other use cases where I'll have a a dumb switch in another room connected back to my main switch, connected via single managed switch port, so same thing there.)
However, when I try this (see screenshot here)
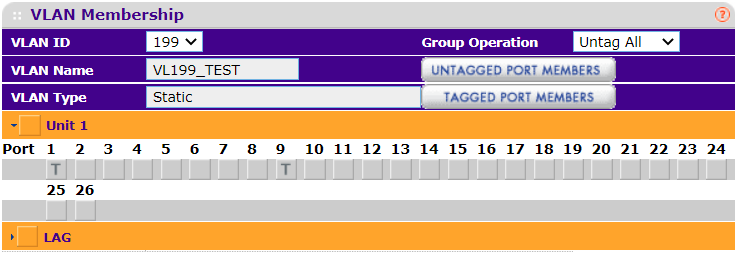 ...I get the same problem: my device can't get an IP address.
...I get the same problem: my device can't get an IP address.I certainly don't want to have DHCP errors later when I set up my other VLANs, but setting all ports to U and pfsense port to T is the only thing that seems to work.
I'll read through 802.1q a bit more also to see if I can understand a bit better.
-
@laplacian Run a PCAP on the pf on that VLAN and look for the MAC address of the device you're expecting.
Also run it on the other VLANs/interfaces, too.
But if you're not getting 802.1Q-tagged packets... you will continue to have issues getting things to talk correctly.
-
I was able to dig up a bit more info about MAC-based VLANs. According to my switch manufacturer (Netgear), all ports are supposed to be untagged.
https://kb.netgear.com/21597/How-do-I-assign-a-MAC-based-VLAN-using-the-web-interface-on-my-managed-switchThis other article seems to suggest that also.
https://www.solutiontales.com/how-do-vlans-work/
It says that the packets are untagged, then tagged according to MAC assignments.However, I absolutely must make the pfsense switch port tagged or else nothing gets routed (I have to factory reset the switch and start over).
-
I'm actually getting some weird routing when leaving my AP port as Untagged. I can't route to my switch from the test 199 VLAN. I can route to everything else, and everything else on my AP seems to route normally. I think I need to read up a bit more on MAC-based VLANs...
-
@laplacian said in Can't get IP on VLAN:
So I set the pfsense physical port to tagged, but the rest to untagged. After doing that, my device now gets an IP address in the VLAN pool!
Is this the correct thing to do? I would assume so, since I don't want any other device interpretting my tags except for my pfsense box.
@viragomann , is this what you were suggesting to do?Yes, the port connected to pfSense has to be tagged for each VLAN you have configured, no matter if other ports of the VLAN on the switch is MAC- based or conventional. It's the "trunk" port.
The port for the AP must be assigned as untagged to the VLAN. MAC- based cannot be used here, since the switch sees all MACs from the connected WiFi devices.
-
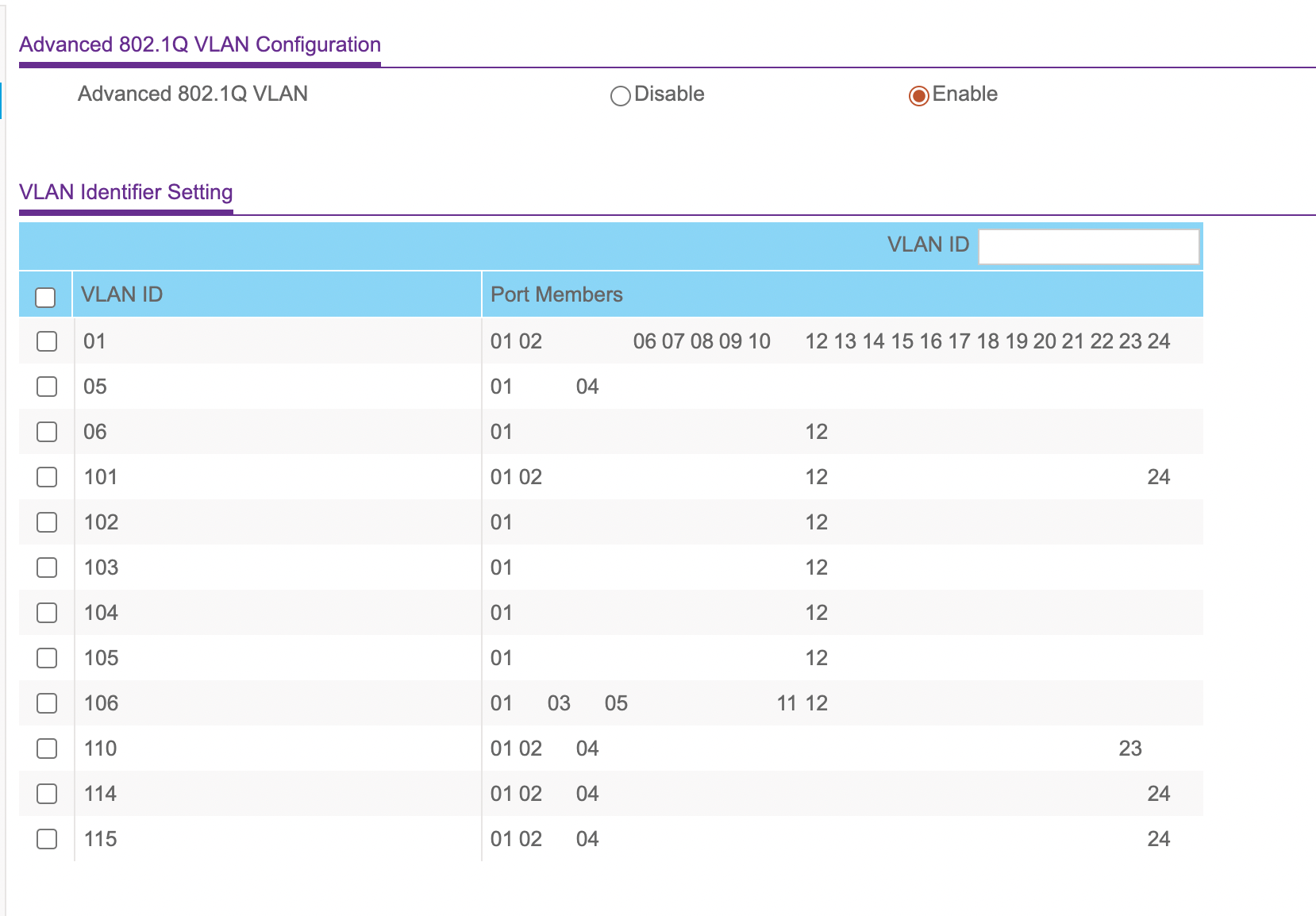
@laplacian Here's the 24-port switch on my desk... VLAN1 is my core -- you probably shouldnt use 1 but I did and it doesn't matter to me.
5 is my functional network for Netgate. I have a PC and an uplink.
My AP is located at ... which port do you think? Yep, 12.
All of those are tagged interfaces unless they are the ONLY device on it. VLAN106 ports 3 and 5? Untagged, but tagged on port 1 so they go through the 10G core switching to the firewall. No, and I repeat NO, interfaces have more than one untagged VLAN on it - that will cause traffic to cross networks.
-
Okay, thanks for the info. I think I need to read up on what Netgear considers MAC-based VLANs and how to use their switches to implement them.
One last question: Say I am able to put a majority of my devices into VLANs correctly. If another device comes along and plugs into one of my dumb switches or connects to my guest WiFi, how can automatically put that device into a Guest VLAN, subject to the pfsense firewall rules designed for Guest VLAN?
-
@laplacian said in Can't get IP on VLAN:
If another device comes along and plugs into one of my dumb switches or connects to my guest WiFi, how can automatically put that device into a Guest VLAN, subject to the pfsense firewall rules designed for Guest VLAN?
By having all VLANs as tagged and leaving the guest VLAN untagged on all the ports that might be exposed, additionally putting a lock on the door where the data cabinet is located.
If you want something like AAAA or Cisco ISE you need different hardware. pfSense doesn't do AAAA on its own and most systems like that (x501) need a third system to do management anyway and those are done on the switch level. I did a little of that with Aruba in the last gig but not too much - we would find it easier to spin up an SSID in a part of a building for a single user most of the time.