Trouble with VLAN
-
@laplacian said in Trouble with VLAN:
@jarhead Ahh, that was it! I guess my printer doesn't like VLAN tags.
But how do I restrict traffic from another VLAN to/from this one? Say I wanted to block traffic from LAN to VL30_COM? Where would that rule go? Would I have to create a floating rule?
Also, I thought default firewall behavior was deny all. Why isn't the traffic from LAN blocked by default until I create a rule that allows it?
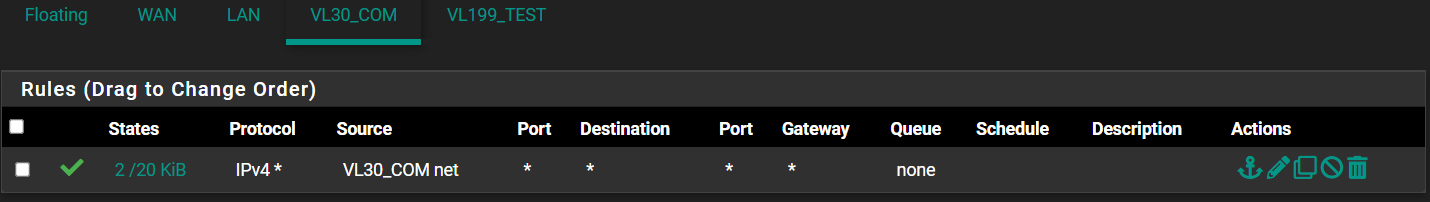
So why doesn't this ^^^ block inbound to my VL30_COM from anywhere? Shouldn't it be default deny? (I can still reach this VLAN from LAN even with these rules.)Keep in mind, the "IN" on an interface is traffic from that interfaces connected network. The "OUT" is traffic from that Interface to the connected network. It has nothing to do with any other interface.
As stated above, rules on an interface are applied to the "IN" traffic.
So if you want to block your LAN from talking to that vlan, that traffic would originate on the LAN into the firewall, so the rule goes on the LAN interface.
If you wanted traffic blocked both ways, you would need a rule on both interfaces. -
@jarhead I'm sorry, I'm a bit new to configuring pfsense, but this is not consistent with how my WAN interface is configured. My WAN has no explicit deny inbound rule, yet I know that my WAN drops inbound traffic. Is the WAN interface the only thing that does inbound default deny (and outbound default allow, apparently)? If so, why?
So are the non-WAN interfaces default allow any/any inbound and default deny any/any outbound? This is totally counterintuitive. I would expect for all interfaces to be the same: default deny inbound, default allow outbound.
Edit: I guess while this is counterintuitive to me, it is actually the expected behavior. Pfsense does do default deny inbound on WAN and default allow outbound on LAN, according to the documentation. You have to add the rules you want to deny inbound.
https://docs.netgate.com/pfsense/en/latest/firewall/best-practices.htmlHow do you do scale this approach? I will have about 8-9 VLANs on my network (not really that many), but I don't want to have to copy the same basic "deny from VLAN interface 1", "deny from VLAN interface 2", etc. to each. What do you guys do to make this easy to read, config, manage?
-
@creationguy said in Trouble with VLAN:
For example:
This VLAN is my "CAMLAN", I don't want it accessing ANY other network, not even the internet.
If you don't want CAMLAN to talk to LAN, then look at my third rule, CAMLAN net cannot talk to anything that's in that alias (90_net_blocks). You don't need to use an alias, you could specify "LAN net".With my rule, any device on CAMLAN cannot reach LAN or anything else in the alias.
Now, I want my LAN to talk to CAMLAN as it has a NVR on it that I need to see, so I allow LAN net to talk to CAMLAN net. However, I don't want my Guest net to talk to CAMLAN net so under Guest VLAN rule, I dissalow it.Thanks, @CreationGuy, this is a helpful example. So if I have several VLANS, would it be efficient/best practice to alias them all to "INTERNAL_NETWORK" or something, then create a high priority rule in each to deny traffic inbound from this alias? Then, if I have my CAMLAN network, then just add a rule afterwards that will allow the NVR network into this one? Does this work and is it a good idea to do?
-
@laplacian said in Trouble with VLAN:
Edit: I guess while this is counterintuitive to me, it is actually the expected behavior. Pfsense does do default deny inbound on WAN and default allow outbound on LAN, according to the documentation. You have to add the rules you want to deny inbound.
No. Out of the box there are rules on the first LAN that allows connections and there are no rules on WAN. No rules means nothing can come in. Every new interface you may create will be the same, they have no rules, so nothing will be able to come in. It is that easy.
-
@laplacian said in Trouble with VLAN:
@jarhead I'm sorry, I'm a bit new to configuring pfsense, but this is not consistent with how my WAN interface is configured. My WAN has no explicit deny inbound rule, yet I know that my WAN drops inbound traffic. Is the WAN interface the only thing that does inbound default deny (and outbound default allow, apparently)? If so, why?
So no rules means everything is blocked. Even when you add a rule there is still an explicit deny at the bottom of the list that is hidden from view, but it's there.
So are the non-WAN interfaces default allow any/any inbound and default deny any/any outbound? This is totally counterintuitive. I would expect for all interfaces to be the same: default deny inbound, default allow outbound.
The only interface with a default allow any is the LAN interface. All other interfaces you create will have no rules, so deny any.
Edit: I guess while this is counterintuitive to me, it is actually the expected behavior. Pfsense does do default deny inbound on WAN and default allow outbound on LAN, according to the documentation. You have to add the rules you want to deny inbound.
https://docs.netgate.com/pfsense/en/latest/firewall/best-practices.htmlDon't think of outbound traffic. All traffic is evaluated on the inbound side except for floating rules. Try not to use floating rules unless you absolutely have to.
How do you do scale this approach? I will have about 8-9 VLANs on my network (not really that many), but I don't want to have to copy the same basic "deny from VLAN interface 1", "deny from VLAN interface 2", etc. to each. What do you guys do to make this easy to read, config, manage?
Easiest, and most used, way is to create an alias with RFC1918 address space in it. The logic is any vlans you create will use private IP addresses so having that alias used in a "block vlanx from RFC1918" will block traffic between vlans. And then you would fine tune by adding pass rules above that one.
Some people still use public IP's on private networks, I have no idea why, but they do, in which case that alias wouldn't work. So just use private addresses. -
@bob-dig said in Trouble with VLAN:
No. Out of the box there are rules on the first LAN that allows connections and there are no rules on WAN.
Per Netgate documentation here:
"...pfSense software utilizes default deny on the WAN and default allow on the LAN."@jarhead said in Trouble with VLAN:
Easiest, and most used, way is to create an alias with RFC1918 address space in it.
Cool, I already have that alias. But if I write a rule that says block inbound RFC1918 space from VLAN 1, then what happens internal to VLAN_N? Technically devices in VLAN 1 are in RFC1918 space. I get that VLAN 2, 3, etc. will be blocked inbound, but what about VLAN 1 devices? Will they be blocked from other VLAN 1 devices also?
Sorry, one more question. Let's say I want VLAN to isolate all devices from each other and just give access outbound to internet only. What would that rule look like?
Thanks again for the tips--this has been helpful.
-
@laplacian said in Trouble with VLAN:
@bob-dig said in Trouble with VLAN:
No. Out of the box there are rules on the first LAN that allows connections and there are no rules on WAN.
Per Netgate documentation here:
"...pfSense software utilizes default deny on the WAN and default allow on the LAN."With no rules there is a default deny rule. You're misunderstanding what Bob said, he's correct and the documentation is correct. They're saying the same thing.
@jarhead said in Trouble with VLAN:
Easiest, and most used, way is to create an alias with RFC1918 address space in it.
Cool, I already have that alias. But if I write a rule that says block inbound RFC1918 space from VLAN 1, then what happens internal to VLAN_N? Technically devices in VLAN 1 are in RFC1918 space. I get that VLAN 2, 3, etc. will be blocked inbound, but what about VLAN 1 devices? Will they be blocked from other VLAN 1 devices also?
You don't block RFC1918 from vlan1, you block vlan1 from RFC1918. I don't think you're grasping the rule application yet but you will. There was an analogy on here a while back, think of the front door to your house, if you let someone in they can go anywhere they want in your house and leave through any other door. That's how rules are applied. If you don't want to allow someone into your house, you stop them at the front door instead of letting them in but telling them they can't leave through the back door.
Traffic is blocked at the interface it originated in. You don't let it into the firewall so it can't go anywhere else.
Make sense?
As far as internal, you can't block a computer from talking to another computer on the same network, that's layer 2 traffic and would never even go to the firewall. Switching only, has no reason to leave the switch.Sorry, one more question. Let's say I want VLAN to isolate all devices from each other and just give access outbound to internet only. What would that rule look like?
Thanks again for the tips--this has been helpful.
Again, all devices on the same vlan can't be isolated from themselves but if you mean isolate all devices on the same vlan from anything else except internet, that you can do.
Keep in mind, everything is blocked by default on any interface except LAN.
So by default, a vlan won't talk to any other interface including the WAN. To allow internet only you would need to allow DNS and HTTP and HTTPS.
This will allow you to browse but some sites (like speedtest.net) need more than just the basics so it may be easier to just block RFC1918, then allow any below that rule. Basically that's just stopping vlans from talking to each other and allowing anything else. You can always fine tune as needed though. -
@jarhead said in Trouble with VLAN:
You don't block RFC1918 from vlan1, you block vlan1 from RFC1918.
So I want a rule that does
Block: souce: VLAN 1/any , dest: RFC1918/any...and another on VLAN 2 that does
Block: souce: VLAN 2/any , dest: RFC1918/anyNot sure I understand your front door analogy (seems like the opposite to me), but I think I understand what I need to do.
@jarhead said in Trouble with VLAN:
all devices on the same vlan can't be isolated from themselves
Okay, understood...they are connected via Layer 2, which does not route to pfsense anyway. So what do you guys do when you want to create a guest, internet-only subnet? Guest users rotate in and out. What do you do? Basic home WiFi routers provide this functionality on their offered "guest" networks. How do you do it via pfsense and a managed switch?
-
@laplacian A guest network is no different than a vlan with internet only access. So basically what I described in the previous post.
As far as through the switch, depends on if you have a separate physical interface or using a vlan on a physical interface.
If separate, just connect to a switchport that is in a separate vlan, then send that same vlan to your AP. If you only have 1 AP that will be used for multiple ssid's, you would trunk the switchport going to the AP tagged with the additional vlans.If using a vlan on a physical interface you would trunk that switchport and tag the additional vlans on it, then repeat above for the AP port.
-
@jarhead said in Trouble with VLAN:
Don't think of outbound traffic. All traffic is evaluated on the inbound side except for floating rules.
Sorry, I'm still having trouble here, and I'm trying some experiments that aren't exactly working.
Let's say I create VLAN 1. By default no rules are created.
So this means that all traffic on VLAN 1 is denied inbound and outbound. (True/False)
Now I want to allow traffic from a specific external alias (say, from another VLAN or LAN) into VLAN 1. So I create a rule on the VLAN 1 interface that allows the alias to talk to VLAN 1. (True/False)
-
@laplacian false... Traffic outbound is denied... But traffic coming from say vlan X would depend on the rules on the vlan X interface.
Traffic is evaluated as it comes into pfsense.. Thinking of it as a doorman standing in front the door entering a building.
Does the doorman check his list or your id as you enter the building, or as you exit the building?
So you walk up to the front door from the street, and want to go to the back yard of the house. Walking into the front door the doorman will check his list, oh your trying to go to the backyard - sure come on in.
And your free to go to the back yard.. When you come back from the back yard (the reply to where you were going) the doorman on the back door lets you back in because your on his list (the state table) the front door man created when he let you in.
But if someone from the back yard wants to enter the back door to leave, that doorman - says hey wait I have no list saying you can do that, so your denied.
Traffic evaluated as it tries to enter the house (pfsense) from any of its doors. But leaving a door is not checked (outbound) from a door, unless you create a floating rule.
-
@johnpoz Okay, thanks, for that analogy.
So if I want traffic to be allowed from my NVR (alias for a host on my LAN) to my VLAN1 (internal cam VLAN), then what do I do? Should I create a rule on my VLAN1 that says allow from NVR to VLAN1?
-
@laplacian the format I use for each Lan / vlan interface is
- Local rules banner / separator
- allow rules from this lan to other local addresses (ping pfsense, access pfsense gui, access resources on other lan / vlan)
- Reject all other traffic to other local addresses (use and RFC1918 or equivalent)
- Internet rules banner / separator in pfsense rules
- allow or block specific out going traffic to internet (if you require this eg to log)
- allow everything else or no further rules to default to block & log everything else or explicit block everything else it you don't want it logged
-
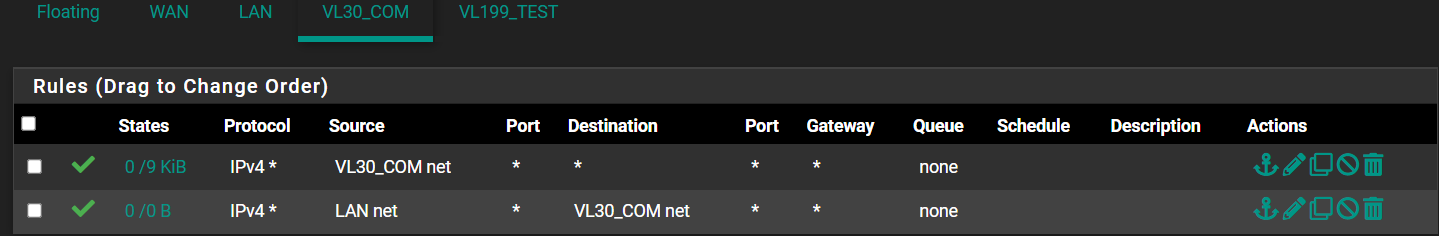
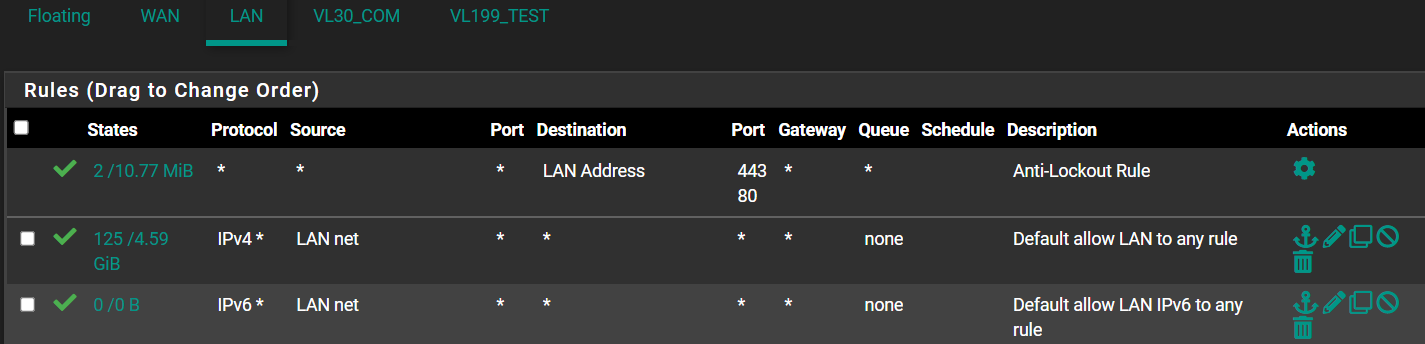
@patch Thanks, I'm trying to do that, and look at the example from @CreationGuy. I'm testing a very similar use case to his: VLAN with internal cameras that are blocked from internet and from everything else on my other VLANs and LAN, but allow access to a single host alias (my NVR).
Here is what I have on my internal camera VLAN:
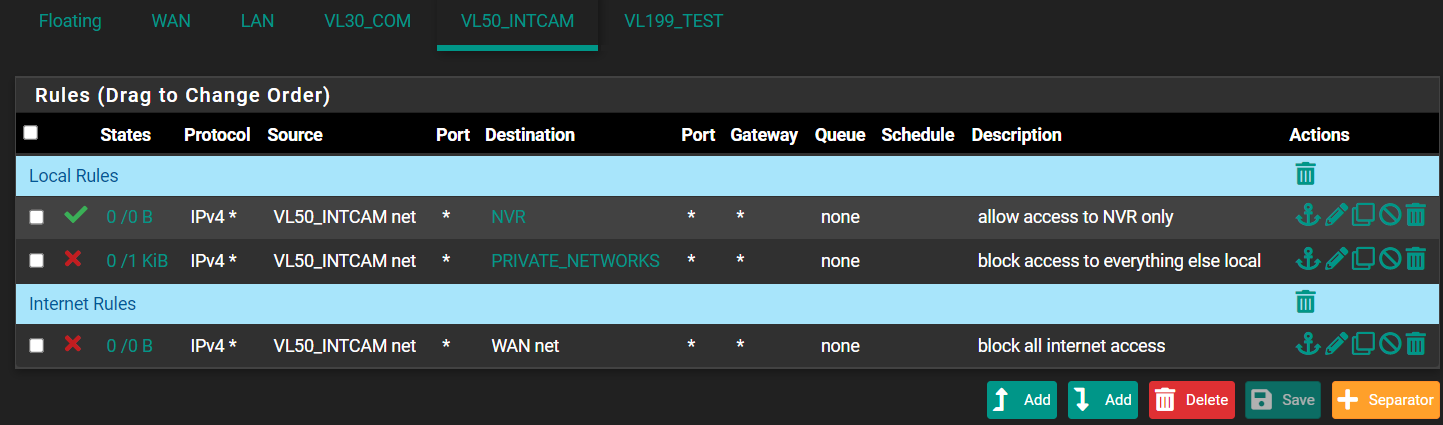
And here is the allow rule on my LAN. (Eventually, I'll get rid of my LAN and put everything in VLANs, but I'm still trying to test and figure this out).
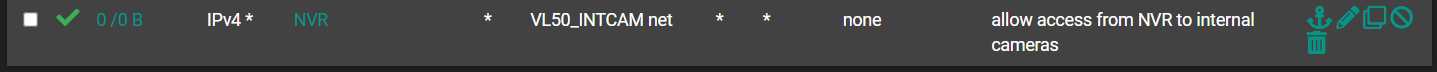
Something here is wrong. I know I must be asking the same question over again, but I just don't seem to be understanding how to write the rules correctly. Any additional help is much appreciated.
-
@laplacian enable logging on your rules to see what is happening.
The status shows your camera is being blocked while trying to access another local lan addresses.It may require access to the pfsense DNS, ntp or some other local resource.
-
@patch Yes, you're right, it is blocking DNS on the VLAN interface. Why? I haven't seen any other tutorial explicitly allow DNS for pfsense. What could I have misconfigured?
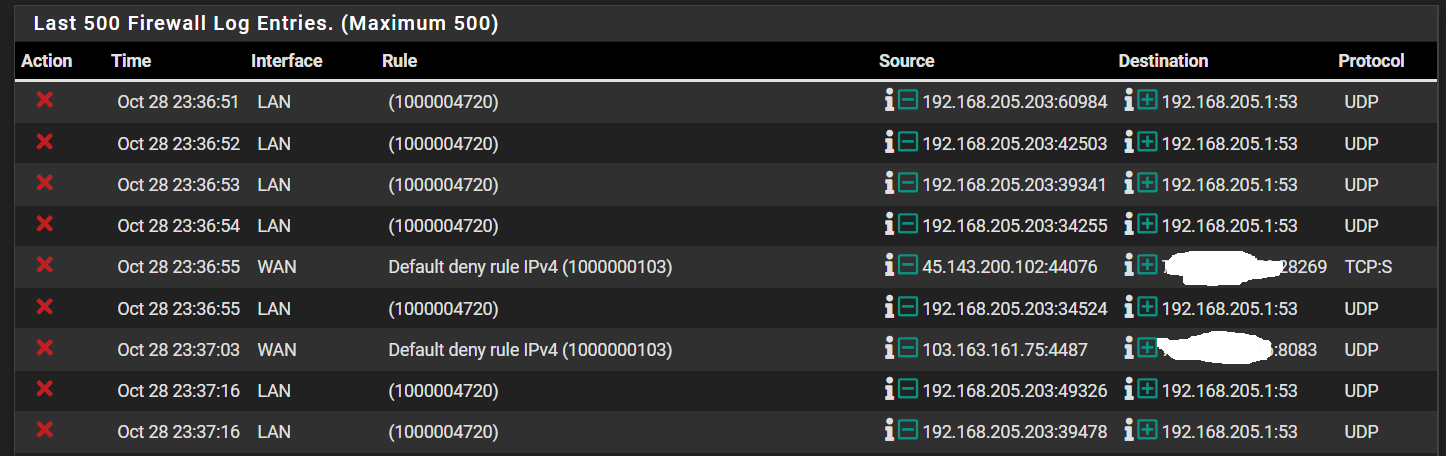
Incidentally, it is also blocking some stuff going out to the internet via "Default deny rule IPv4". Does this mean that my WAN block rule is unnecessary?
Edit: my VLAN is configured with static IPv4 of 192.168.205.1/24, in case that wasn't clear from the snippet.... I have enabled the pfsense DHCP server for this VLAN interface and it serving IP addresses in this range correctly.
-
@laplacian your camera is likely to want access to a DNS to know were to find your NVR or where on the internet other resources it would like to access are.
When a device on a Lan acquires a local IP address it is normally also told where the local DNS is, which by default is pfsense. For that device to actually access the pfsense DNS, you need to add a local LAN firewall rule to allow that.
-
@patch Like this?
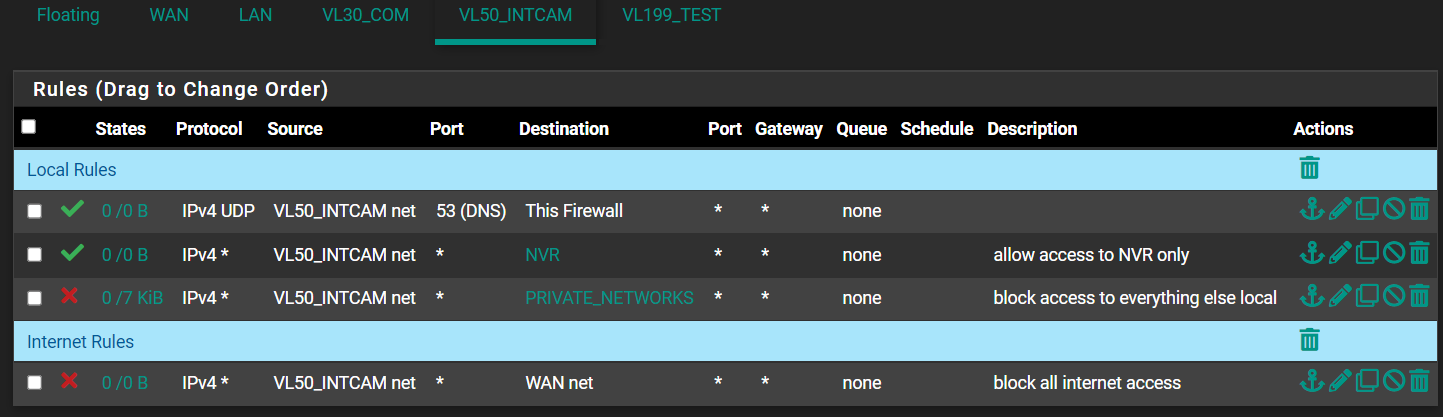
That still didn't seem to do it. -
@laplacian Your camera is not triggering your DNS rule for some reason.
Note your states count are zero which should not be the case if the rule is being triggered.
-
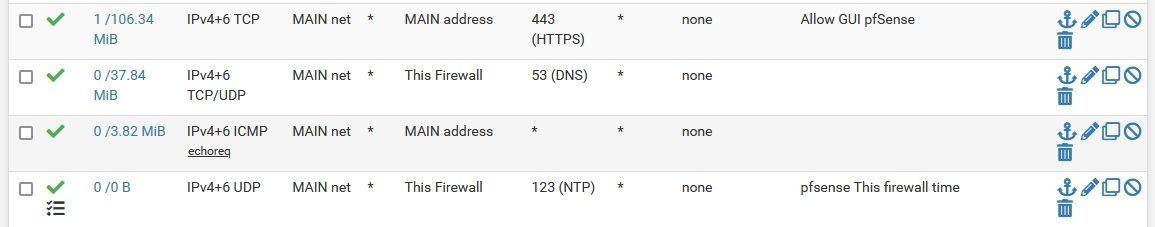
@laplacian You have to put the DNS port in the destination port.
Also don't use WAN_net, it is only a small subnet which is on your WAN port, take a look at Status/Interfaces how small it is.