pfBlockerNG not working
-
Hi,
I know there are many similar threads in this forum already but none of them seems to be considering my issue / to be a solution to my problem.I had installed pfBlockerNG for a while but never bothered too much.
Now a wanted to dive deeper into configuring it.
First I updated from 2 -> 3I followed this guide: https://www.youtube.com/watch?v=xizAeAqYde4&ab_channel=LawrenceSystems
But neither IP nor DNSBL seems to work at all.
I have AD / DNS Server in my environment all fwd DNS to pfSense.
I also tried on a test machine to configure pfSense as the only DNS server to double check.
Also tried ping and traceroute with the diagnostic tool within pfSenseI tried ping and traceroute to ie adservice.google.com or an IP from the block list.
Ping always resolves the matching address.
Traceroute always goes thru my pfSense IP.I can see in the browser the pfBlockerNG block page on 10.10.10.1 as configured.
I also configured a firewall rule to force all traffic from LAN on port 53 thru pfSense.
Nothing seems to have any effect and nothing gets blocked / filtered.
Logs dont show any weird errors.
And of course, the pfBlockerNG log is empty since nothing is passing thru.
I only see in there when I manually go to 10.10.10.1Any ideas why this may be?
pfBlockerNG Settings

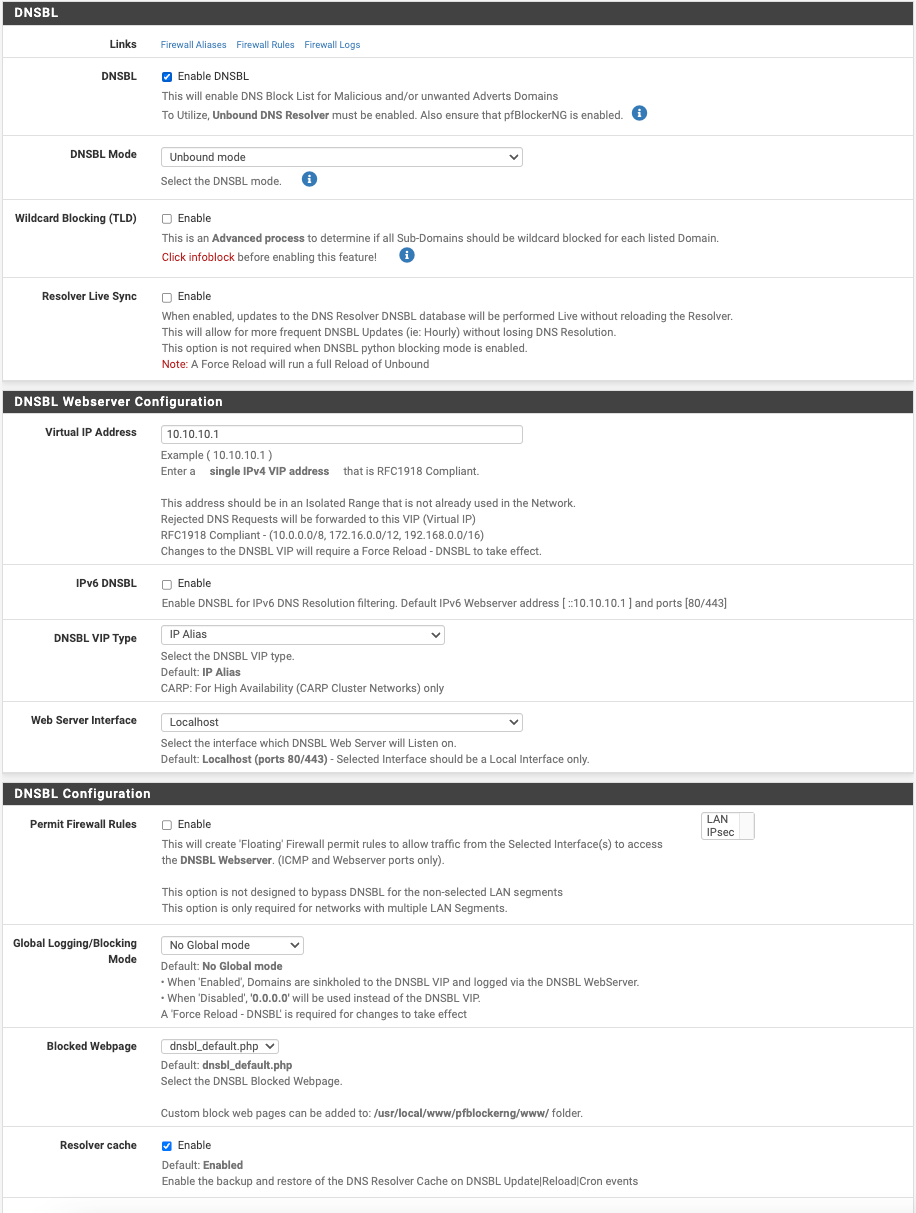
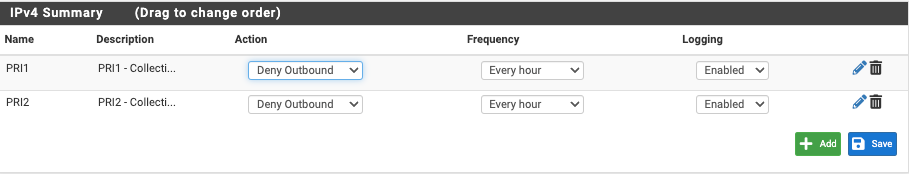
Firewall Settings
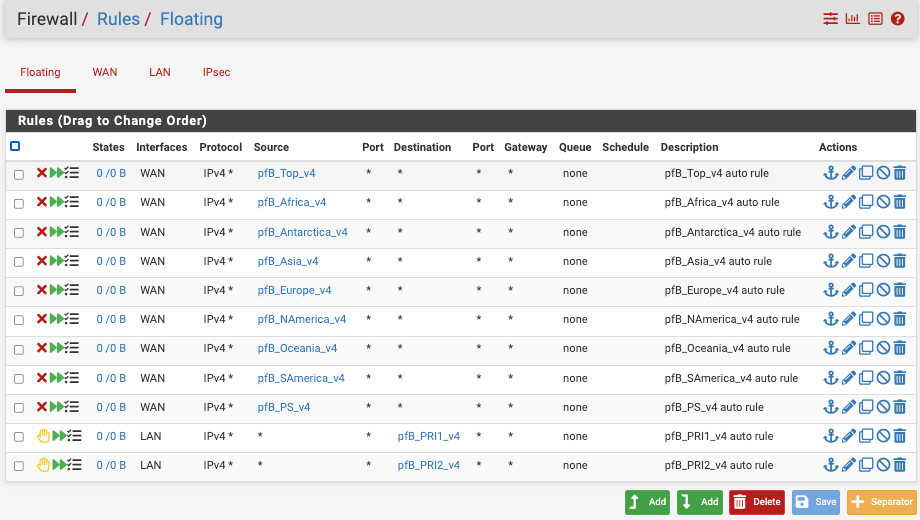
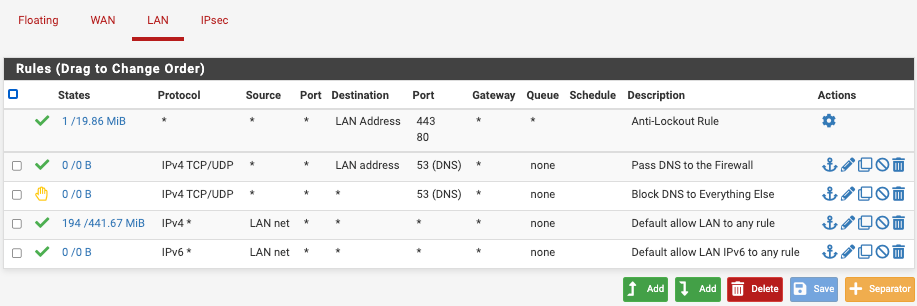
DNS Resolver Settings
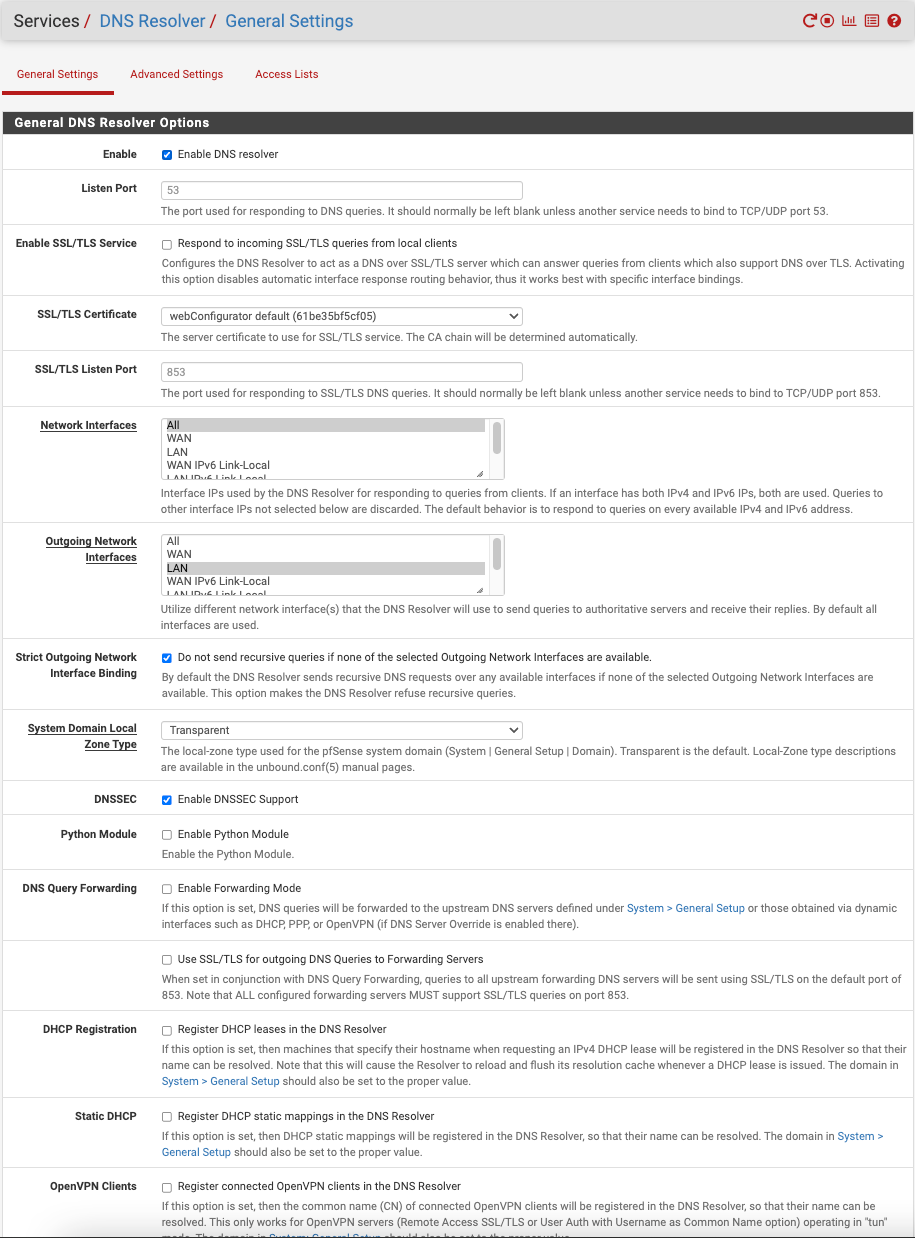
-
Where did this came from :
?
Please check other settings.https://www.youtube.com/watch?v=xizAeAqYde4&ab_channel=LawrenceSystems presumes you using default (or working) dns settings.
You are using any DNSBL feeds ?
Why :
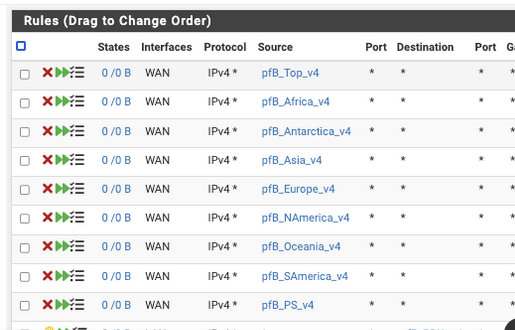
would you want to block these ?
They are already blocked by default. -
@gertjan said in pfBlockerNG not working:
Where did this came from :
?
Please check other settings.I can recall if I set this?
But when I set it to ie ANY I cant reach any website anymore
EDIT: I unchecked "strict outgoing network interface binding" and selected ANY as outgoing. This seemed to have fixed that issue...
@gertjan said in pfBlockerNG not working:
would you want to block these ?
They are already blocked by default.These were automatically created when I selected all the Geo-IPs
The auto-rules for DNSBL are the two at the bottom.Here are my DNSBL Feeds
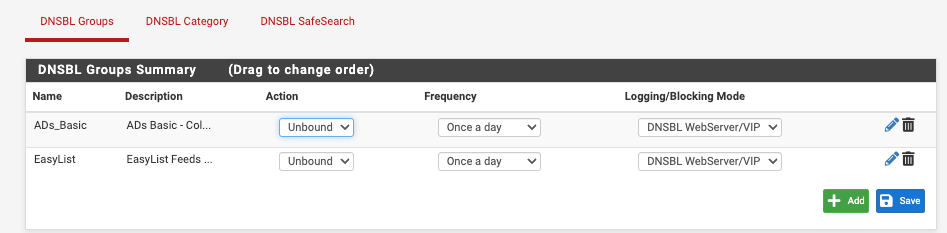
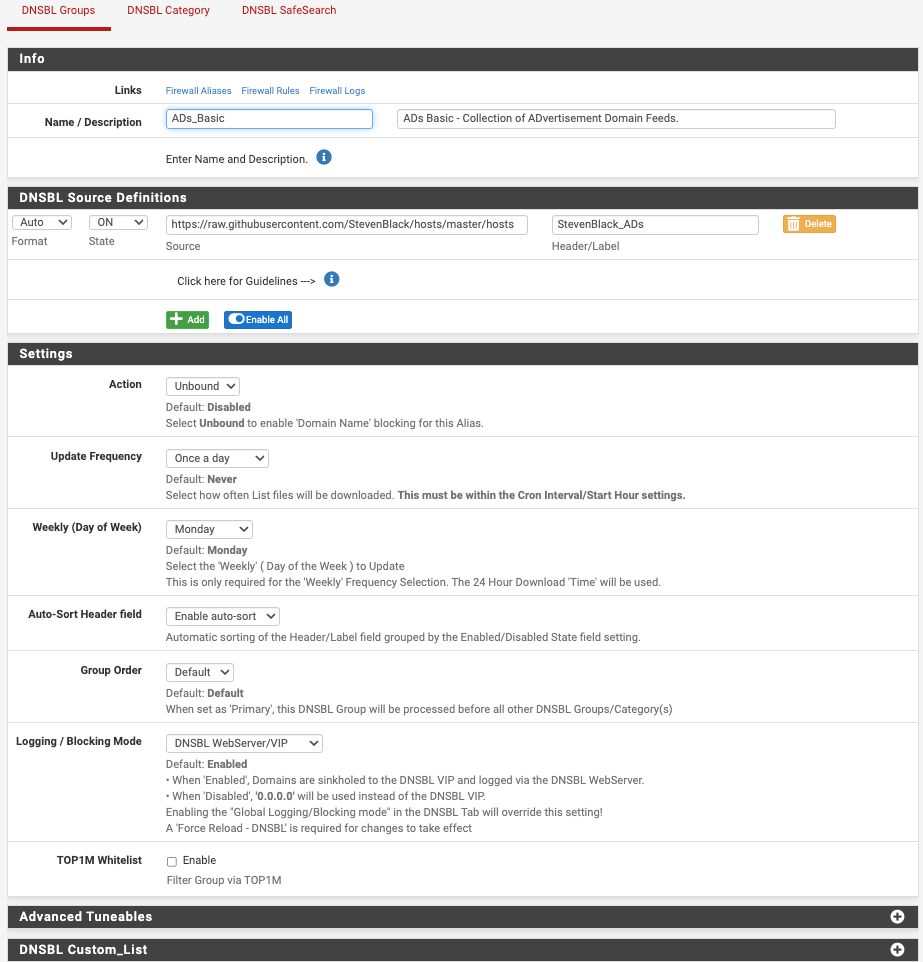
-
@pinkie2 said in pfBlockerNG not working:
But when I set it to ie ANY I cant reach any website anymore
ANY ?
These are the default settings :
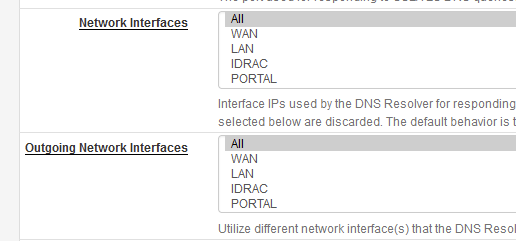
If that doesn't work for you, I advise to go to default pfSense settings. That will work for sure.
-
-
I activated "Alienvault" manually as per the tutorial I had followed.
Now I tried deactivating it and at least now it seems that ie ads are blocked and I'm getting redirected to the pfBlockerNG site when I try to browse to blocked domains.That is at least one success.
But as soon as I activate any GeoIP list ie Top Spammers and set it to "Deny Inbound" All DNS requests from my LAN are not successful?
-
@pinkie2 said in pfBlockerNG not working:
I'm getting redirected to the pfBlockerNG site when I try to browse to blocked domains.
Nice, but rather unusefull.
The web server page that pfBlockerNG use to redirect a user when this user uses a web browser, and he want to visit a 'forbidden' host name, this works only for http access.
It can't work for https access as https can't be redirected.The thing is : user don't use http sites any more, as these do not exist any more.
Google, for example, doesn't list them any more.@pinkie2 said in pfBlockerNG not working:
activate any GeoIP list ie Top Spammers and set it to "Deny Inbound"
Serious ? Lawrence could not have advised that.
"Deny outbound" maybe.Again : you don't have to block anything on WAN : it is already blocked. And who cares where 'they' came from, when knocking on your door.
GEOIP looks like a nice thing to have. And then you start to deal with the false positives, and then you start to get enough of it, and you stop using it. -
This pfBlockerNG site was a simple test for me if anything is getting blocked. Since this didnt work at all before I fiddled with the settings.
But am I assuming correctly that ie Ad's should now be less with the DNSBL activated?
The reason for GeoIP / why I had hoped to find a way to use this is that I have servers running behind pfsense (ie Exchange).
Obviously, the required ports are pointing at the servers (ie SMTP).
I'd wanna filter some more spam out by blocking IP's from funky places.
I have Proxmox MG as an additional filter in between to get rid of spam too.
But GeoIP (i hope) could be an additional safety mechanism? -
@pinkie2 said in pfBlockerNG not working:
The reason for GeoIP / why I had hoped to find a way to use this is that I have servers running behind pfsense (ie Exchange).
Obviously, the required ports are pointing at the servers (ie SMTP).
I'd wanna filter some more spam out by blocking IP's from funky places.That might be a reason to 'protect' you internal, LAN based mail server.
I wasn't aware you were exposing 'public' services to the internet.@pinkie2 said in pfBlockerNG not working:
But GeoIP (i hope) could be an additional safety mechanism?
Dono.
I've a postfix multi IP / multi (many) host names) dedicated 'barebone' server, but mine isn't behind a ISP IP (that would be a disaster for me as my mail server is also used for a company).
I don't block IPs by default, so my mail server is open bar. But, rules do apply. Remote mail servers that try to drop mails that don't play the rules, like : no/bad SPF, no/bad DKIM, no/bad DMARC, mails using TLS1 or 1.1, etc are marked as such.
Mails that are dropped on the mail backup server why the master server is running : they are marked ans scrapped for good.
Etc etc.
Test results are logged, end then handled by failtoban, who feeds the firewall (iptables as this server is a Debian).
Depending on my mood, the position of the moon, and the colour of the dress of my wife, I'll blacklist them for xx days : see here.