second OpenVPN server does not route
-
I just set up my first OpenVPN server (remote access TLS +auth, TLS handshake, layer 3 tunnel, etc.) and it works well. I have my VPN clients in a 172.16.200.0/24 network and allow connectivity back to various 192.168.x.x/24 networks at home. I have a WAN FW rule that allows access via port 1194 and an OpenVPN FW rule that allows the 172.16.200.x clients to go where they need to go. Split and full tunnel work appropriately.
However, I can't seem to get my second OpenVPN server to work. First, I copied the first working server (by clicking the copy button in the GUI). The only difference in this server is that it uses port 1195 and a client network of 172.16.210.0/24. I added the corresponding WAN and OpenVPN FW rules.
My client can connect to the second server and get an IP in the appropriate network, but I cannot route anywhere locally or remotely (in split or full tunnel mode). System logs show that the client is hitting DNS at UDP/172.16.210.1 often, but nothing else.
What am I missing? Is there something that I need to do to ensure my clients can route?
-
@laplacian said in second OpenVPN server does not route:
I have a WAN FW rule that allows access via port 1194
@laplacian said in second OpenVPN server does not route:
this server is that it uses port 1195
Are you 100% certain?
@laplacian said in second OpenVPN server does not route:
My client can connect to the second server and get an IP in the appropriate network, but I cannot route anywhere locally or remotely (in split or full tunnel mode).
What are the IPv4 network settings at in the server?
Screen shots are good here - they can't give partial information (unless you crop).
-
OpenVPN server 1:
port 1194 (default)
VPN client network at 172.16.200.0/24
everything routes appropriatelyOpenVPN server 2:
port 1195
VPN client network at 172.16.210.0/24
does not seem to routeBoth have "Dynampic IP" checked under Client settings, both have "Subnet -- One IP address per client in a common subnet" selected under Topology.
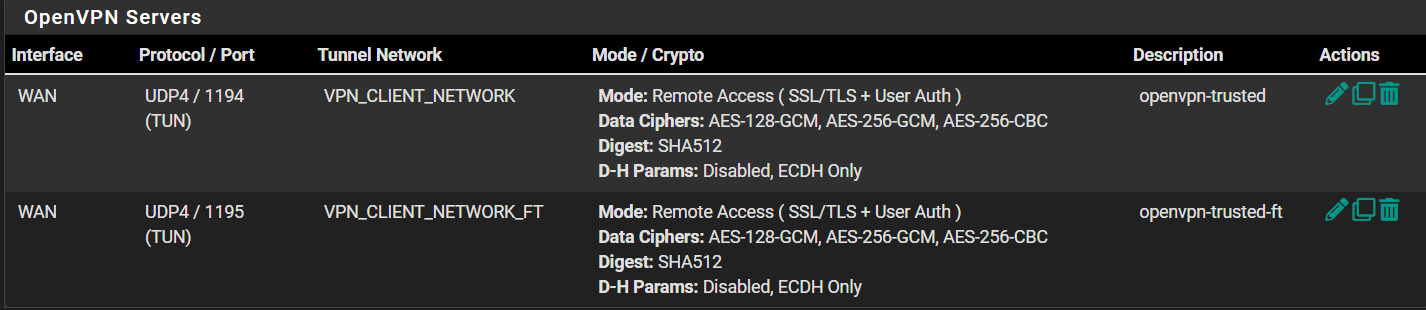
working server 1:
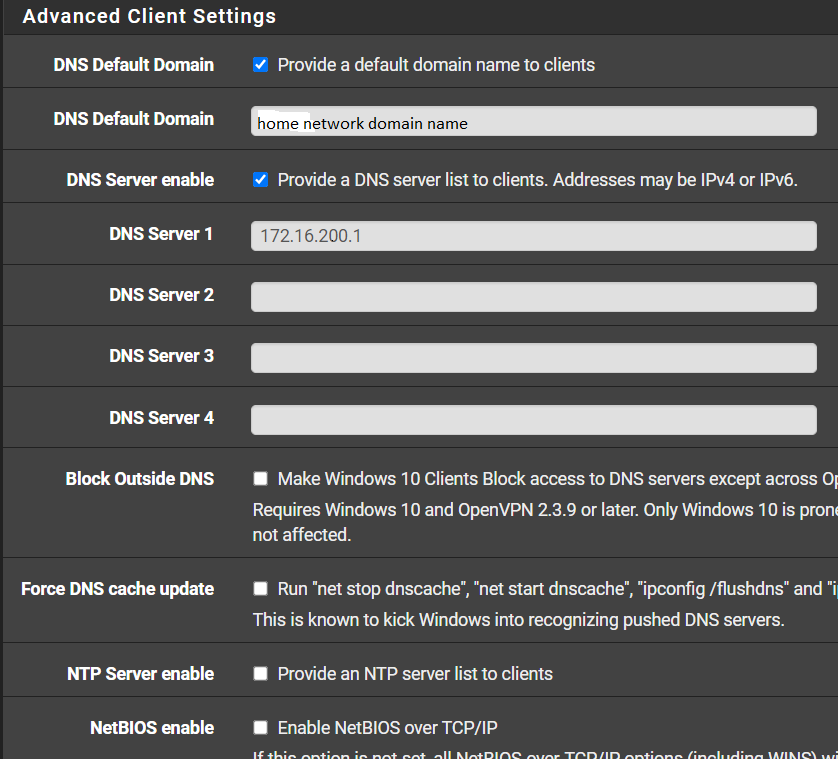
non-working server 2:
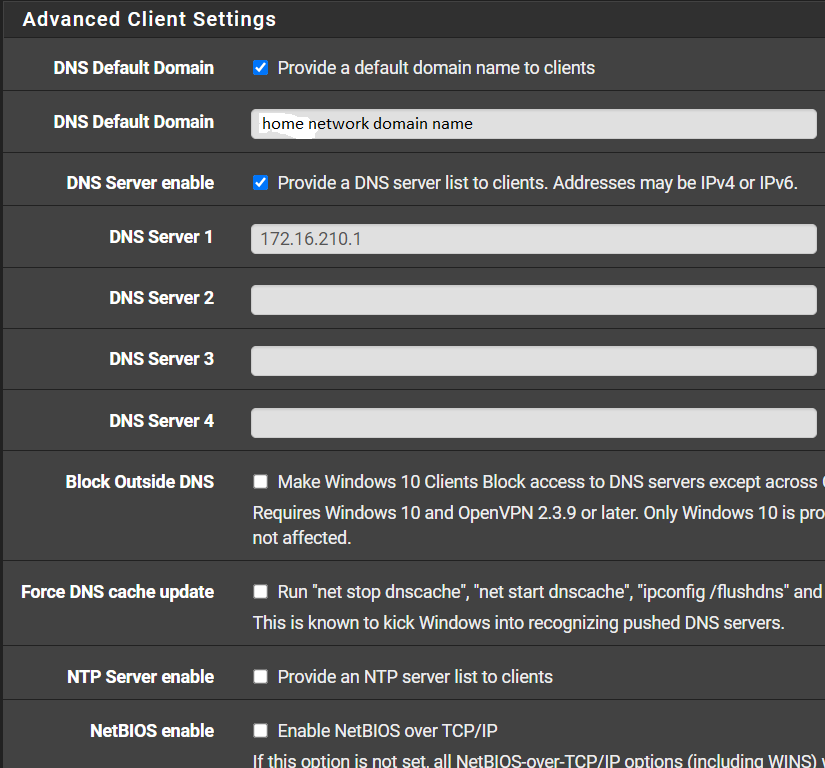
WAN rules:
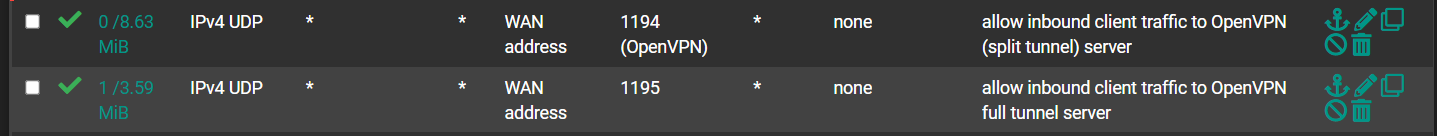
OpenVPN rules:
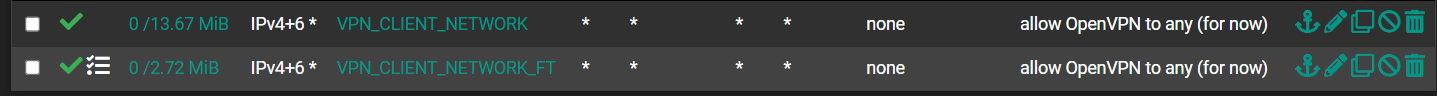
Here are a couple of lines from my system log. I connected, then attempted to resolve the weg GUI of my printer which is at 192.168.31.1. I see a log entry for that and I see one for DNS. However, my client was never able to resolve the printer web GUI or any other IP I gave it in my browser.
-
Some tests :
When you disable "server 2", and edit server 1, change port 1194 UDP to 1195 UDP, does server 1 behaves correctly on port 1195 UDP ?And the other way around : disable server 1, edit server 2, shift port 1195 UDP to 1194 UDP : doe sit work now ?
For both test, export a temporary client config.
Compare also the client config files for differences. Only port and certs should differ.This :
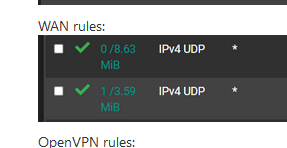
looks fine : traffic is coming in.
You the console access and compare the server config files.
You'll find theme here :
/var/etc/openvpn/server1/
and
/var/etc/openvpn/server2/Both folders will contain a config.ovpn file : compare them.
Did you instantiate both "Openvpn" interface ? (go to Interfaces => assignment and create an interface. Put the firewall rules on these instantiated interfaces, double check that the resolver listens also on these interfaces for dns conditionality)
-
@laplacian said in second OpenVPN server does not route:
However, my client was never able to resolve the printer web GUI or any other IP I gave it in my browser.
Did you give access to a specific port to a specific path? If you want to do that the source port MUST be "ANY".
-
@gertjan said in second OpenVPN server does not route:
When you disable "server 2", and edit server 1, change port 1194 UDP to 1195 UDP, does server 1 behaves correctly on port 1195 UDP ?
And the other way around : disable server 1, edit server 2, shift port 1195 UDP to 1194 UDP : doe sit work now ?Server 1 on port 1195 did work. Server 2 on port 1194 did not work.
By "not work", I mean the same as before: it connects, gets an IP, but can't connect to any local or remote server/app. Logs show connections attempts to DNS 53 and some of my internal IPs.
(Previously, I had server 1 on 1194 and server 2 on 1195.)@gertjan said in second OpenVPN server does not route:
Compare also the client config files for differences. Only port and certs should differ.
Actually, I just re-used the same cert and user for the configs. Here is the only diff in the files:
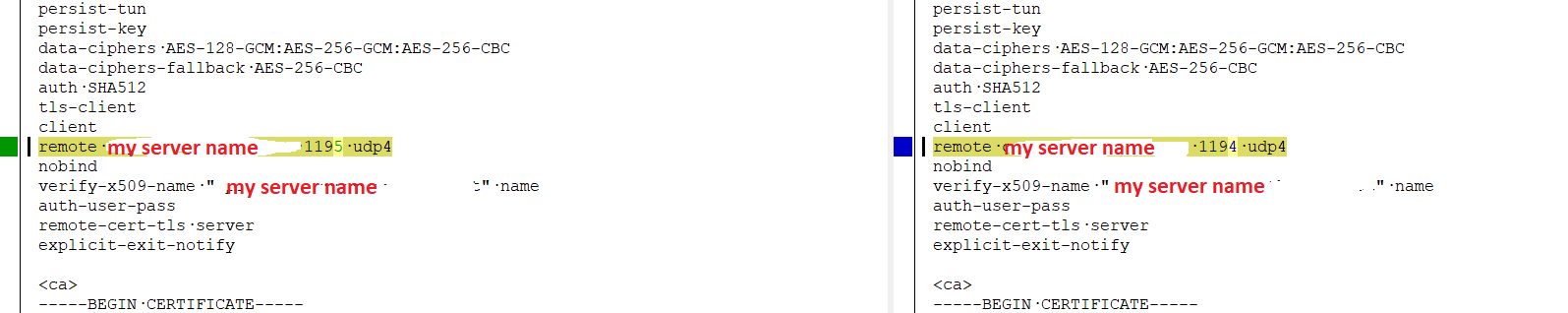
@rcoleman-netgate said in second OpenVPN server does not route:
Did you give access to a specific port to a specific path? If you want to do that the source port MUST be "ANY".
Not sure what you mean here...I included screenshots of my WAN and OpenVPN rules in a post above. On WAN, I am allowing any/any to WAN address/port 1195.
@gertjan said in second OpenVPN server does not route:
Did you instantiate both "Openvpn" interface ? (go to Interfaces => assignment and create an interface. Put the firewall rules on these instantiated interfaces, double check that the resolver listens also on these interfaces for dns conditionality)
No, I did not. Is that necessary? Maybe that's my issue...let me check that.
-
@gertjan said in second OpenVPN server does not route:
Did you instantiate both "Openvpn" interface ? (go to Interfaces => assignment and create an interface. Put the firewall rules on these instantiated interfaces, double check that the resolver listens also on these interfaces for dns conditionality)
Okay, just did that. Now neither one of my servers work. I have 1 allow any rule on the OpenVPN server 1 interface, 1 allow any rule on the server 1 interface, and no rules on the auto-generated OpenVPN tab.
-
@laplacian said in second OpenVPN server does not route:
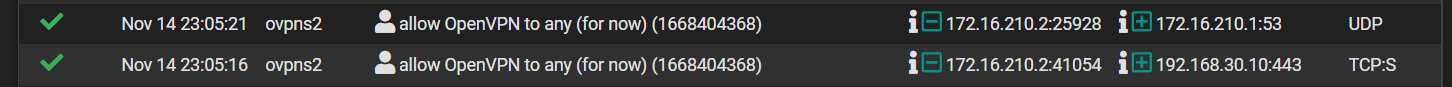
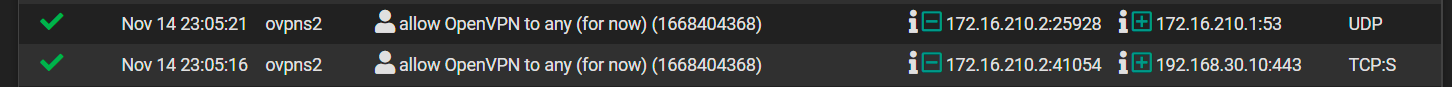
Not sure what you mean here...I included screenshots of my WAN and OpenVPN rules in a post above. On WAN, I am allowing any/any to WAN address/port 1195.
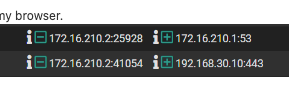
this indicates otherwise. -
@rcoleman-netgate said in second OpenVPN server does not route:
this indicates otherwise.
How so? Those log entries show a device with an IP in my VPN client range connecting to DNS and to my printer. Those two connections are both in RFC1918 space, private LAN-LAN, essentially. The external WAN rules are posted above and show any/any to 1195.
-
@laplacian said in second OpenVPN server does not route:
Okay, just did that. Now neither one of my servers work. I have 1 allow any rule on the OpenVPN server 1 interface, 1 allow any rule on the server 1 interface, and no rules on the auto-generated OpenVPN tab.
@Gertjan
Oops, I spoke too soon. Netgate documentation says you have to restart the servers after creating new interfaces. When I did that, I'm back to square 1: server 1 works as expected and server 2 (port 1195) does not seem to route.I also did a diff of the server configs. The only things that differ are the port numbers and the interface IPs:
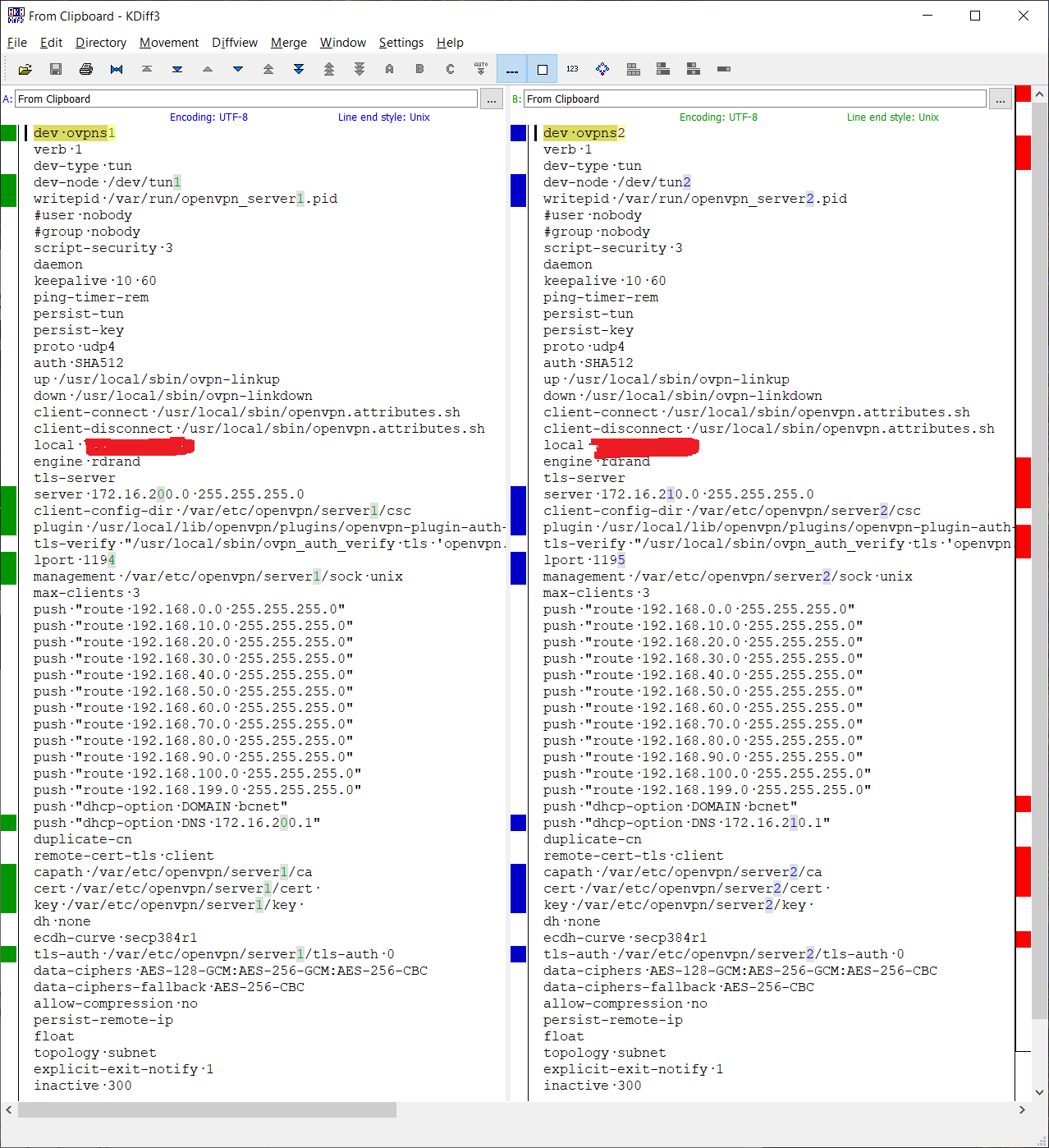
The routing seems normal:
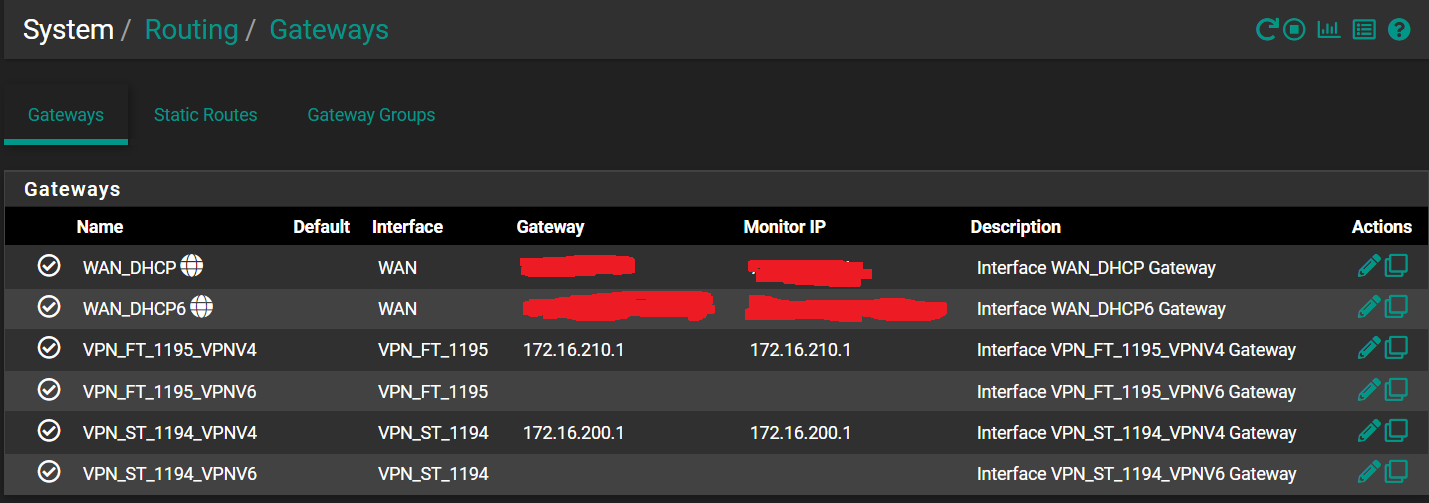
Thanks for the tips so far, but is there anything else I can audit or compare between the two? This is really strange (and frustrating...)