openvpn client connects but no local network access
-
hi all,
I am new to pfsense and I'm trying to create an openvpn server on pfsense using the wizard.
I have read many topics on the matter in the forum but I cannot figure it out.
My setup on pfsense is:
3 WAN interfaces with different isp's each and 2 Local network interfaces with different private networks.
What I'm trying to accomplish here is using only one of the WANs (lets say WAN1) to be able to create a Vpn so someone from outside can access both internal networks and internet.
my WAN1 internal ip is 192.168.1.2
vpn tunnel network is 10.254.254.0/24
Lan1 network is 172.19.3.0/16 and
Lan2 network is 192.168.2.0/24
After completing the wizard and exporting the client configuration, I can connect from my laptop through the client with no problem to the vpn using my phone as hotspot. The windows tap-adapter of the laptop gets an ip from the vpn server (10.254.254.2). I can connect to the internet but I cannot ping or connect to either of the local networks.
What am I missing?Any help is most welcome
thank you very much -
@robbygr said in openvpn client connects but no local network access:
Lan1 network is 172.19.3.0/16 and
Lan2 network is 192.168.2.0/24Did you add this networks to the "Local Networks" in the vpn server settings?
If it still doesn't work try to access pfSense LAN IP from the client. Ensure you have a rule on OpenVPN tab which allow this access.
-
@viragomann thank you for your reply. Yes I did add the netwoks to the local networks.I also used the push route command but no luck.
I cannot access the pfsense Lan ip from the client. In the openvpn I have a rule that allows any source to any destination.
I will add a rule to allow the specific network and see if it makes a difference. -
@robbygr said in openvpn client connects but no local network access:
I cannot access the pfsense Lan ip from the client.
At least this should be possible, when the client is connected and there is a rule on pfSense OpenVPN to, which allow it.
Can you post the clients IPv4 routing table, please?
-
@viragomann hello and sorry for the delay.
here is the routing table from my laptop using the openvpn client
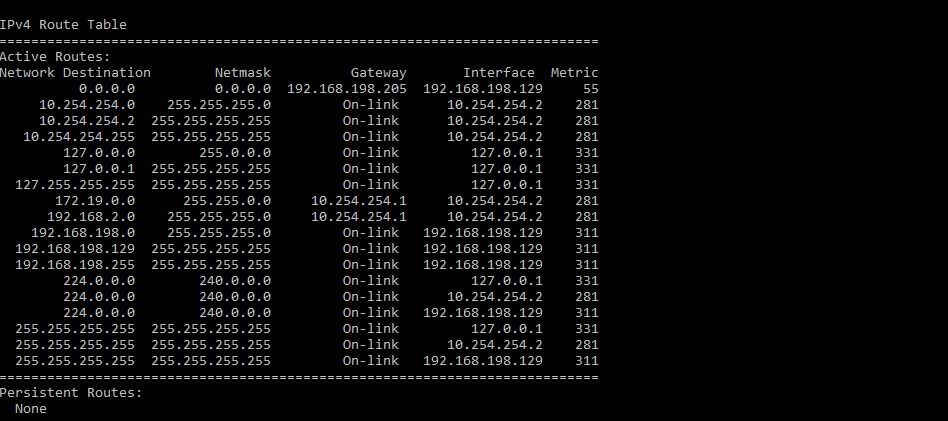
thank you -
@robbygr
So the routes are added properly. Hence access to the pfSense LANs should be routed over the VPN.The only reason I can think for not able to access the LAN IP is that it was blocked, namely something wrong with the firewall rules.
Did allow any protocol in the rule on OpenVPN, not only TCP?
Do you see any states / packets for the pass rule?Or possibly do you have a floating rule in place, which is blocking the access?
Check the firewall log. If the logging of the default deny rule is enabled, you would see blocks if none of your custom rules matches.
-
This post is deleted! -
This post is deleted!