Relative position, Subnet <> Gateway <> Firewall <> Services
-
Sometimes I am wondering how pfSense exactly behaves. And that is in situations where computers within a subnet are interacting with other computers in the same local subnet and services provided by pfSense.
To mention example situations:
-
if a computer on a subnet-A related to an interface-A sends a dns-query towards an dns-services provided by interface-A, is then the dns service before or behind the FW-function? Assume I define a rule IP-address-computer-B is not allowed to access the DNS-related to interface-A will it pass or not ....
-
A computer is using an IPv4 Multicast Address for example '224.0.0.1 ' which has as definition 'All Systems on this Subnet', you would expect that all computers on the local subnet implies:
- is including the gateway
- the firewall would not play a role since it is not passing the subnet
However ..... that does not match what I see here
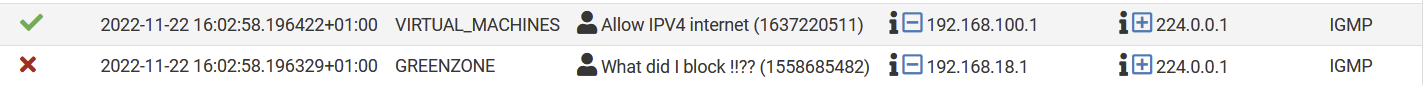
You see an example where one time a firewall passes an 224.0.0.1 query and in the other case it stops that query ....
However how is that possible ...... if it is within the same subnet !?
-
-
pfSense can not block packets , that is NOT passing one of it's interfaces.
Packets to/from devices on the same L2 subnet , are not passing the pfSense interface, they use "arp & L2" to communicate, not routing.As you noticed, there is a "single" exception to the above rule, as your multicast example describes. The pfSense interface it self , pfSense can block packages for that ip, because it "passes the pfSense interface".
/Bingo
-
You know, it is all about this picture ......
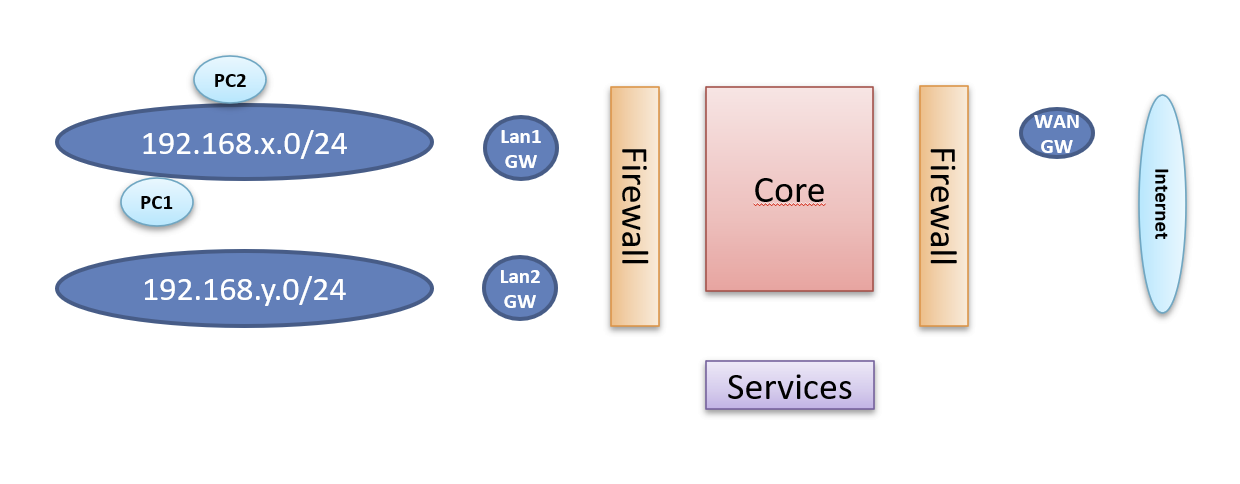
- Is the GW before or behind the firewall
- Are the services before or behind the firewall
- Is the GW yes or no part of the subnet
- If the GW is part of the subnet, which the IP suggest. How can it be behind the firewall !!??
Sometimes I think, to know. Next time I am (very) confused
-
@louis2 Packets are inspecting as they enter the firewall interface from the attached network.
So on the LAN, any device that transmits a packet will be inspected as it enters the LAN interface, from there it will either be allowed to enter, or denied.
All interfaces work the same. -
Yep, all interfaces work the same. For my self I also see the WAN interface as just one of the interfaces (with some extra functionality).
However that is not my problem. The problem is:
- what is the internal structure of the firewall and as a consequence
- how is it behaving !
Lets take the 224.0.01 message as example. There are a few strange things there:
- it is initiated by the gateway itself / by the gateway address
- it is a message towards the subnet 'All Systems on this Subnet'. I assume the subnet 'controlled' by the GW
- it is passing the firewall, otherwise there would not have FW-related alarms
- the firewall determine in one case to pass the message and in the other case to block the message
- however where is the message coming from and where is it passed to the core? passed to the local network?, not processed at all?.
- In general what is happening here!
Note that I am using multicast in my network. I have to better understand what is happening eventually is going wrong. Perhaps it is related to different FreeBSD14 behavoir, perhaps the network, perhaps .... I just do not yet know ....
-
I found the cause of '224.0.0.1' example behavoir (pimd-beta running with a wrong config) and fixed it, but that does not take away that I am another time confused.
So if any one could explain how the wired behavoir could happen and more general what the interconnections is the drawing are, what the order of the building blocks exactly is,I would appreciate.
-
This is the information you may be looking for. It describes traffic flow between interfaces.
Network Address Translation - Ordering of NAT and Firewall Processing
https://docs.netgate.com/pfsense/en/latest/nat/process-order.htmlThe order is LAN > FIREWALL > GATEWAY.
When a packet arrives at a network device and it is destined for another device on the same physical layer in the same subnet, it goes directly to that device without needing to go through a firewall or router. When a packet enters a LAN interface on pfsense, it is first checked for matching firewall rules. These could either be rules on the LAN interface or floating rules. Then it starts to use the "gateway" functions. If this packet was going to the internet, pfsense would check if there are any manually specified outbout NAT rules. If there are none, it will use the default outbound rule for WAN. This changes the packet from your private addess to your real IP address and forwards the packet outside of your network.
There are other steps that I didn't explain for cases using port forwarding or 1:1 NAT. It is more detailed on that page.