No traffic allowed on VLAN to outside at all
-
@ydyw8rdm8i7dfd said in No traffic allowed on VLAN to outside at all:
Just like you mentioned. The device connect to the switchport need to have their traffic tagged.
Maybe you're misunderstanding, the point is to NOT tag a vlan on an access port so you don't have to tag the nic. Access ports should be untagged with the vlan needed on that port.
I also changed the switchport that connects to the virtual machine host to trunk mode. I wonder if that's necessary? If it is, wouldn't it be a good idea to change every port to trunk mode? And then manage the separate in pfSense?
Any time you need multiple vlans going to the same place, you'll most likely need a trunk port. The other option would be to run multiple cables with a separate network on each.
pfSense can't manage your switchports.I find it impossible to set firewall rules in LAN to achieve the separation.
That's because it is impossible. Layer 2 traffic doesn't go through the firewall/router at all, so no rule on the LAN interface will work on another LAN device.
But now that I learned an access point cannot handle multiple VLANs, I'm defeated again
 .
.Who told you that?? They lied.
Almost all AP's support vlans these days unless you're buying a $20 'special'.
This is the part where I do suggest unifi, their AP's are good and do anything you want if you use their controller with it. Another good one is Engenius which can do anything you want with no need for a separate controller. -
hey,
as mentioned by @Jarhead before:the connection between pfsense and smart switch should be trunk, meaning this link transports all your vlans between those devices.
So, vlan1 is always UNTAGGED on a trunk while VLAN x-y is TAGGED on that trunk
Those ports working as access port should be configured with the wanted/needed VLAN ID.
So might be:
pfsense LAN1 is connected to switch (trunk) port 1 (vlan1 untagged, all other vlans tagged)
the remaining switch ports work as access, so they get configured with a VLAN ID. such "belonging" to that VLAN. Here, this VLAN is UNTAGGED.Your switch puts the correct tag on your incoming traffic from switch access port X.
:) -
@jarhead said in No traffic allowed on VLAN to outside at all:
Maybe you're misunderstanding, the point is to NOT tag a vlan on an access port so you don't have to tag the nic. Access ports should be untagged with the vlan needed on that port.
This is what I meant. See on the VM setting there is a place to configure VLAN tag. I thought this is necessary. The VM host connect to one switchport (gia0/0/6), I also made this port trunk.
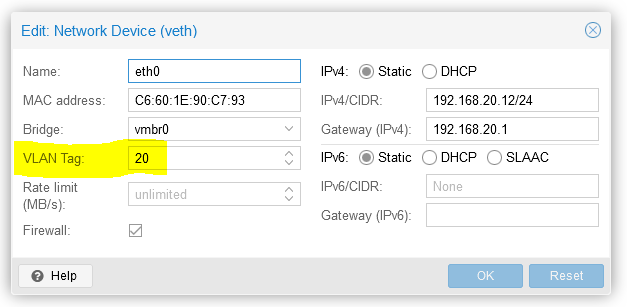
@jarhead said in No traffic allowed on VLAN to outside at all:
Who told you that?? They lied.
I think I misread "access port" to "access point". If unifi AP works well, I might consider get one. Thanks for the recommendation.
@jarhead said in No traffic allowed on VLAN to outside at all:
Any time you need multiple vlans going to the same place, you'll most likely need a trunk port. The other option would be to run multiple cables with a separate network on each.
pfSense can't manage your switchports.I was thinking of using pfSense to manage separation of VLANs using firewall rules. If every switchport is trunk, then they are all connected by default. Maybe that's not a good idea.
@jarhead said in No traffic allowed on VLAN to outside at all:
That's because it is impossible. Layer 2 traffic doesn't go through the firewall/router at all, so no rule on the LAN interface will work on another LAN device.
That's not exactly what I tried to achieve. I wanted to force the traffic of two groups of devices to go through two different sets of VPN gateways. They were in one LAN, but I find it very difficult to make rules works the way I wanted. That's why I now try to separate them in different VLANs so each one can have a set of rules for themselves.
-
@the-other Thank you for the advice

@the-other said in No traffic allowed on VLAN to outside at all:
So, vlan1 is always UNTAGGED on a trunk while VLAN x-y is TAGGED on that trunk
Those ports working as access port should be configured with the wanted/needed VLAN ID.That's the concept I failed to understand and still struggle to apply to my use case. I actually don't need any of my devices to be physically assigned to a VLAN. I don't want any switchport to be assigned to one VLAN. Because they either connects to a VM host server with many VMs that should be running on different VLANs, or they are connected to an AP which also connects to a dumb switch and both of them have devices that needs to be on different VLANs.
In short, I was expecting VLANs to be completely virtual and only based on their IP address. I did not expect that I need to assign a switchport to a VLAN, and that makes this port exclusive to one VLAN. I thought I can switch the VLAN of one connected device by assigning the IP from another VLAN to it.
-
@ydyw8rdm8i7dfd
Hey,
Well, one could use dynamic vlans as well...there you do not have a vlan bound to a simple port, but a radius server decides which vlan a device is put in to depending on mac or credentials or...
But i don't think that's the point here.You could buy a small smart switch (simple tplink with vlan capapbility, here around 20 euro) and then you get vlans for your entire network.
For your vm question...use a vlan for the parent server running your hyper v. For your vms use the hypervisor virtual switch...
-
Post your running config of the 3750
Webgui is ok but some of us have a better time visualizing if we see the actual config.
-
@the-other Thank you for the suggestion. My set up is somewhat working as expected now. I will continue my learning journey. I probably will eventually buy another more user friendly switch. But that's another project for anther long weekend. I am so tired of working on networking now

PS: interesting this website banned the ip address of the VPN I use. Welp, it means the VPN is working

-
@flat4 I actually just learned a the "show run" command a moment ago. I didn't even know it's existence when I posted my question.
The webgui on 3750x sucks. It is slow and has very limited features. It does not allow VLAN management on webgui.
I wanted to share my "show run" result, but this website flags it as spam

I wonder what had happened before. -
@ydyw8rdm8i7dfd
You prob needs some "likes" aka "Thumbs up" , to gain some "credit".
I just gave you one.You could try to upload the config as a .txt file
-
@ydyw8rdm8i7dfd yes a 3750 is really not for beginners but if you YouTube some basics for Cisco switches and learned the basics you'll will not regret it.
-
@flat4 I just did. It's very interesting how it's managed. At least for VLAN it's not that hard.
-
@bingo600 It is working now. I think my settings are mostly correct. I made those switchport who might be connecting to APs/Servers/Switches trunk port.
interface FastEthernet0 no ip address ! interface GigabitEthernet1/0/1 switchport trunk encapsulation dot1q switchport mode trunk ! interface GigabitEthernet1/0/2 switchport trunk encapsulation dot1q switchport mode trunk ! interface GigabitEthernet1/0/3 switchport trunk encapsulation dot1q switchport mode trunk ! interface GigabitEthernet1/0/4 ! interface GigabitEthernet1/0/5 ! interface GigabitEthernet1/0/6 switchport access vlan 20 switchport trunk encapsulation dot1q switchport mode trunk ! interface GigabitEthernet1/0/7 switchport trunk encapsulation dot1q switchport mode trunk -
Just note that when you set switchport mode trunk , it will "default" allow all Vlans on the trunk.
If you feel for it you could do a further restriction :
switchport trunk allowed vlan 868-870,872-876,897,898Remember the "add" on allow , else you will be sorry

/Bingo