PFSense (Netgate 4100) Setup with a Fortigate
-
I set the range to 192.168.2.10 - 192.168.2.25 and then I connected my desktop to my fortigate and then manually set the Fortigate WAN2 interface to 'Manual' configuration with 192.168.2.1/24 as the IP/subnet and still am unable to receive a DHCP lease.
-
@mofugga
So you connected WAN2 to pfSense now?Setting a static IP for the network interface doesn't result in a DHCP lease. A lease can only be assigned to a DHCP client.
interface to 'Manual' configuration with 192.168.2.1/24 as the IP/subnet
This is the IP of the pfSense LAN as you wrote above. You have the set it to some other like 192.168.2.2/24.
-
Ah yes, I meant IP assignment, not DHCP lease. Yes I have the Fortigate WAN2 connected to the PFSense Appliance LAN2. The PFsense appliance is connected to the modem.
@viragomann said in PFSense (Netgate 4100) Setup with a Fortigate:
This is the IP of the pfSense LAN as you wrote above. You have the set it to some other like 192.168.2.2/24.
I tried setting the WAN2 interface on my Fortigate to have a 'Manual' configuration with 192.168.2.2/24 and still unable to connect
-
@mofugga
Does the Fortigate show even a connection on that interface?Can you ping pfSense from it?
I assume, you have the default rule on pfSense LAN, which allow any traffic. -
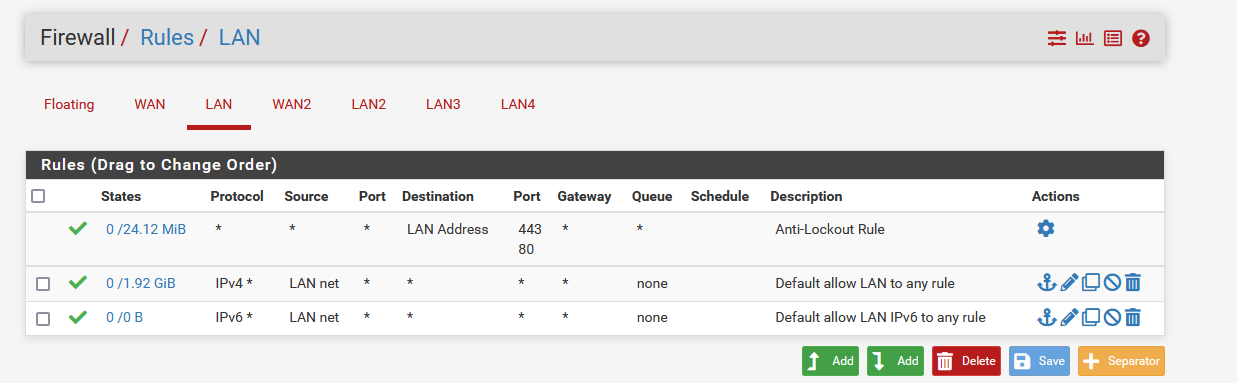
Yes, I have my PFsense rules on LAN set like this:
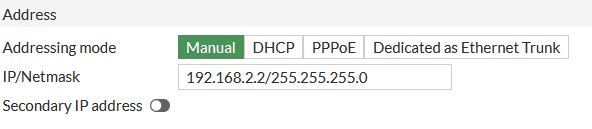
My Fortigate WAN2 interface was set like this:
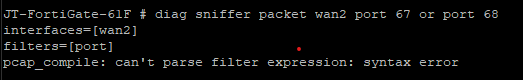
When looking at the WAN2 interface in the fortigate CLI and running 'diag sniffer packet wan2 port 67 or port 68' I get this:
It is still not seeing the pfsense appliance I don't think.
-
@mofugga said in PFSense (Netgate 4100) Setup with a Fortigate:
When looking at the WAN2 interface in the fortigate CLI and running 'diag sniffer packet wan2 port 67 or port 68' I get this:
Seems to be a wrong syntax.
Anyway you won't see any packets on these ports, since there is no DHCP client enabled now.But again, can you ping 192.168.1.1?
Apart from the IP and mask you also have to state the pfSense IP as upstream gateway.
-
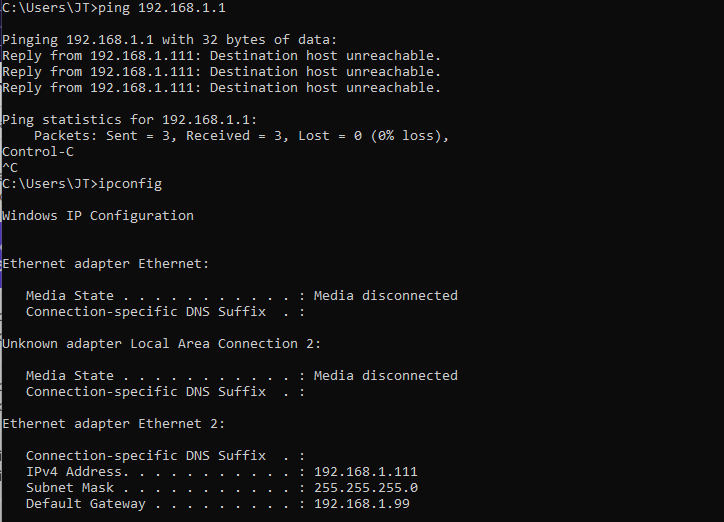
When I try to ping 192.168.1.1 I get this:
@viragomann said in PFSense (Netgate 4100) Setup with a Fortigate:
Apart from the IP and mask you also have to state the pfSense IP as upstream gateway.
What do you mean state the pfSense IP as upstream gateway? I think I may know what you mean but I am not sure how to do this. My desktop sees 192.168.1.99 as the gateway which is my fortigate device. However I want it to be 192.168.2.1 which is my pfsense appliance. Perhaps my fortigate device is not seeing my pfsense appliance?
-
@mofugga
I was talking about the Fortigate.
Run the ping on the Fortigate. I assume, there is a possibility to do this.And you have to set the default gateway on the Fortigate to 192.168.1.1.
-
I added a static route to the fortigate to try to go to 192.168.2.1 which is what I have the pfsense appliance to.
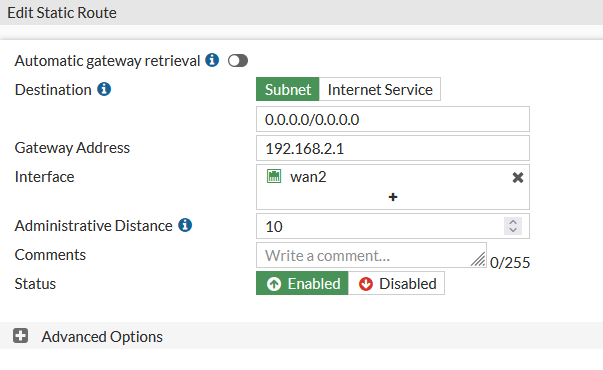
And then I checked the WAN2 interface on the fortigate. The fortigate and PFsense appliance are connected on the fortigate WAN2 and PFsense LAN2.
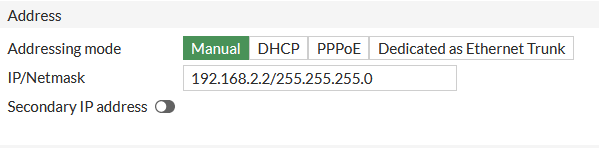
And then I went to the fortigate CLI to try to ping the pfsense appliance from the fortigate. Still not connectivity.
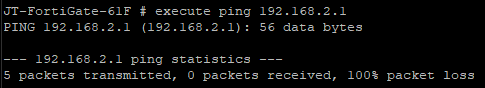
-
@mofugga
Show your pfSense "Connect interface definition" , where the fortigate is connected.Always check the Firewall logs , when having issues.
Find it here: Status --> System Logs --> Firewall
Imho you should concentrate on : Getting the fortigate to ping the pfSense IF on the connect net (192.168.2.1)
Remember to allow ICMP on that connect interface , or the pfSense would drop the packages.Edit: Why does the fortigate show WAN2 .... Do you have a WAN1 Active on the fortigate ???
-
This post is deleted! -
EDIT: Deleted and reposted for formatting.
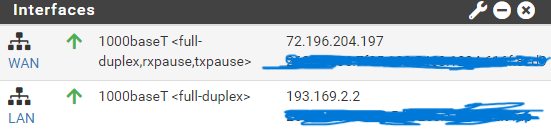
Here are my PFSense Interfaces. Because the Fortigate has a default IP address of 192.168.1.99 and default subnet of 192.168.1.X I changed the PFsense subnet to 193.169.2.X:
PFsense Interfaces
PFSense LAN2 Rules (Where the PFSense LAN2 Interface is connected to the Fortigate WAN1 inteface
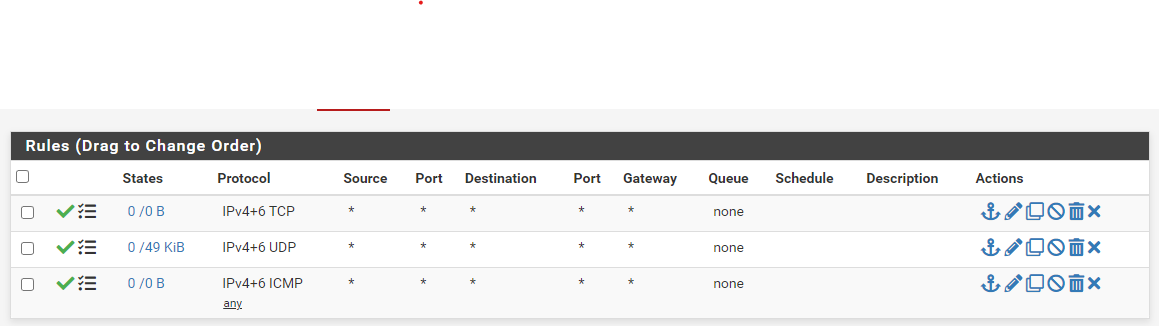
I have the "Log packets that are handled by this rule" box checked for all rules here.LAN2 Attempting DHCP Configuration

However, when I attempt to physically connect my desktop to my Fortigate and initiate an outbound connection in this configuration. I can see in my Fortigate logs that traffic is being sent out correctly, but return traffic is being stopped further upstream, presumably at my PFSense appliance.
This is the configuration I mean.
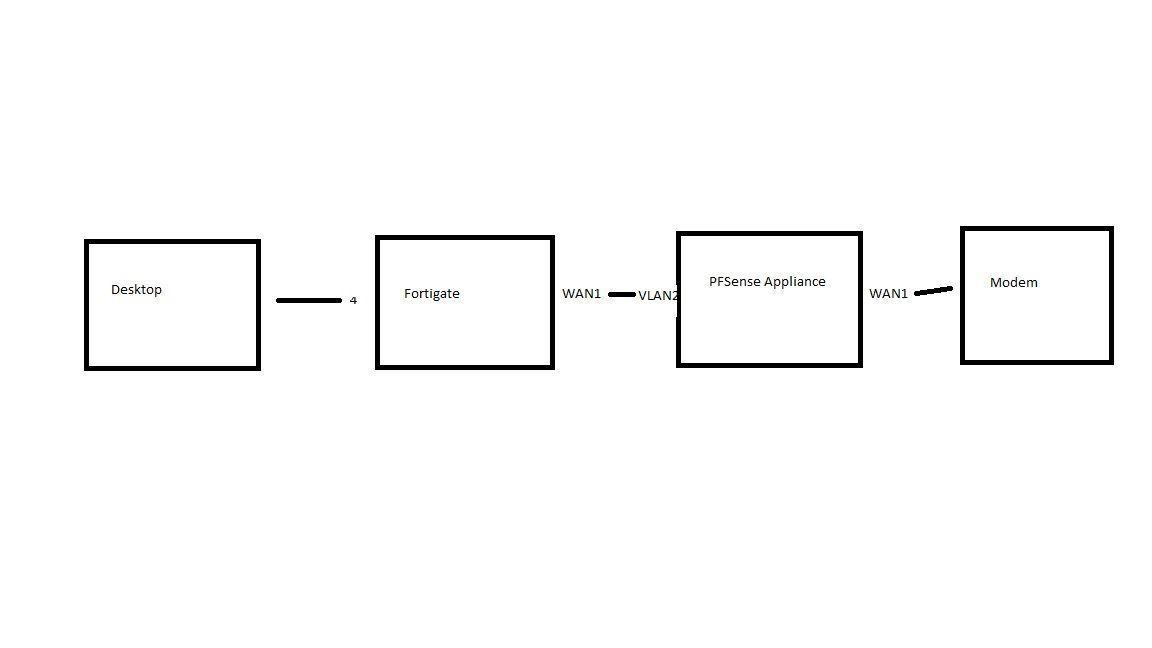
My desktop is connected to the fortigate's LAN port 4, the fortigate WAN1 is connected to the PFSense appliance VLAN2, and the PFsense appliance is connected to the modem.
When running in this configuration and making a browser request to google.com I am still not getting and response back.
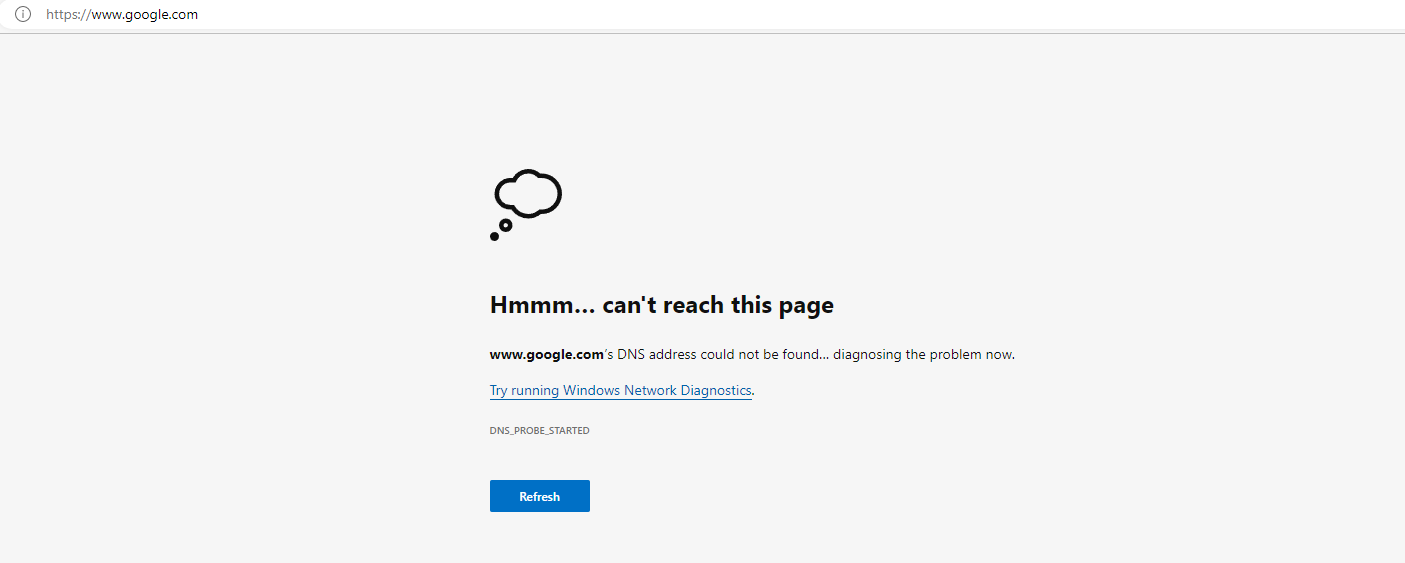 .
.When checking the Fortigate logs, I can see the outbound traffic being sent, but that 0 bytes are being received:
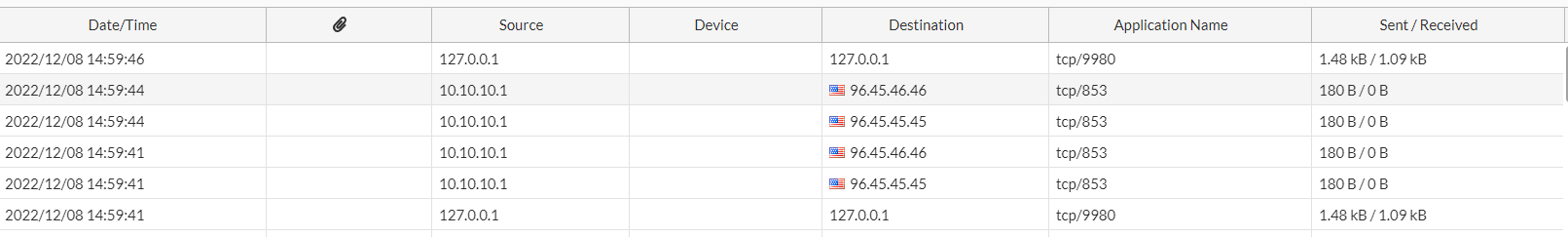 .
.
However, I do not think this is because of my Fortigate firewall policy. This is the only policy I have from my internal traffic to WAN1:
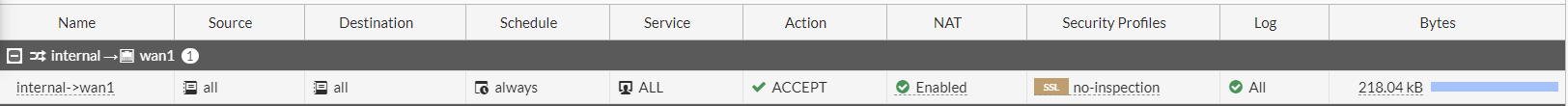 .
.I do have Squid setup on my PFsense device.
I am still unable to ping the PFSense appliance from my Fortigate device even though I changed all of the rules on LAN2 of the PFSense appliance to accept IPv4+6 TCP/UDP/ICMP traffic and to log all captured packets. DHCP works fine in this configuration when I remove the Fortigate from the equation entirely:
 .
.The DHCP lease is also assigned correctly when I have it in this configuration as well. 192.169.2.11 is my desktop.
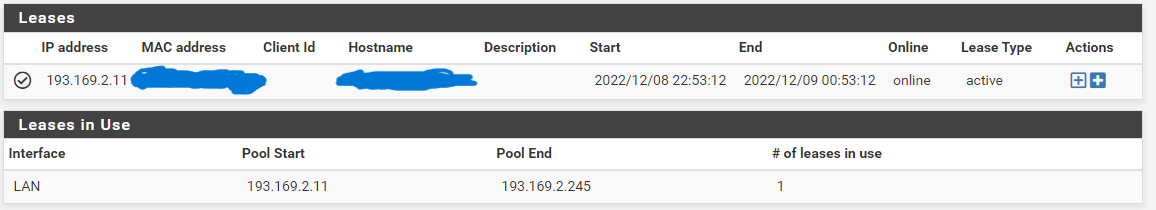 . But for whatever reason, the testing I have done to have PFSense and Fortigate find each other on the network either when I set the interface on the Fortigate to MANUAL or DHCP - they still seem to be unable to find eachother.
. But for whatever reason, the testing I have done to have PFSense and Fortigate find each other on the network either when I set the interface on the Fortigate to MANUAL or DHCP - they still seem to be unable to find eachother. -
Never mind. I figured it out. I had to configure the LAN interface to have the appropriate rules. Thanks everyone for your help.