-
@skogs nice! good find. This seems like a case of turning on all rules and then turning on blocking.
For future reference, where did you go to search? I assume in the CLI -
@michmoor Additionally I'd bet the default allow LAN to any rule was also disabled. Snort/Suricata will try to block both side of the conversation, but if the allow LAN rule is still on, that sus LAN machine will still be able to do everything else just fine. If that rule is disabled, then both sides really do get blocked, and it looks like the entire machine or LAN interface ate it when it really is functioning perfectly as designed.
-
@skogs I found it this way..But im assuming you had a better method on locating this rule?
/usr/local/etc/snort/rules: cat *.rules | grep ".cc TLD" alert udp $HOME_NET any -> any 53 (msg:"ET DNS Query for .cc TLD"; content:"|01|"; offset:2; depth:1; content:"|00 01 00 00 00 00 00|"; distance:1; within:7; content:"|02|cc|00|"; distance:0; fast_pattern; classtype:bad-unknown; sid:2027758; rev:2; metadata:affected_product Any, attack_target Client_Endpoint, created_at 2019_07_26, deployment Perimeter, former_category DNS, signature_severity Minor, updated_at 2020_09_17;) -
@skogs I have had 6100 for 14 months now and Snort has been running at least 12 months without trouble with IPS Policy Selection as Security and blocking enabled.
You are right, LAN to any rule is disabled. Remove Blocked Hosts Interval in Snort is set to 3 hours, so after that normal traffic should have continued.
Thank you for explaining what happened and also thanks for @michmoor. This has been very enlightening.
-
@skogs I have been wondering this still, because Snort has always been set to block both IPs and there has been many blocking incidents without any trouble accessing pfSense or internet from the PC.
Also, this interface has default pass list configured. This list includes 192.168.1.0/24, so the PC's access to pfSense should never get blocked by Snort.
-
@pfsjap I got nothing on that. Perhaps you just run an exceptionally clean environment with zero packet anomalies.
for @michmoor pfsense does have an exceptionally good interface for managing snort rules. I used to hate it...but then have dealt with a few others...now I appreciate pfsense's setup.
I don't have a snort instance handy, but it exceptionally similar iirc.
Services - Suricata - Under interfaces click the pencil on an interface
WAN (or LAN) Rules sub tab
The 'available rule categories' section gives you the basic list...for this instance pick the emerging-dns rules list. Find all the rules and enable/disable individually with gui on each individual interface. -
@pfsjap said in LAN interface goes down randomly:
Also, this interface has default pass list configured. This list includes 192.168.1.0/24, so the PC's access to pfSense should never get blocked by Snort.
This is true for any Snort deployment. Traffic passing between HOMENETs wouldnt be subject to snort rules i believe.
There may be more in play here but without knowing how you are set up we are just guessing.
It seems you have blocking enabled. Legacy mode? If so you should be able to see Blocked Hosts. If not using Legacy mode, then individual packets will be dropped matching the rule but not the hosts from communicating. -
@michmoor Legacy mode, yes.
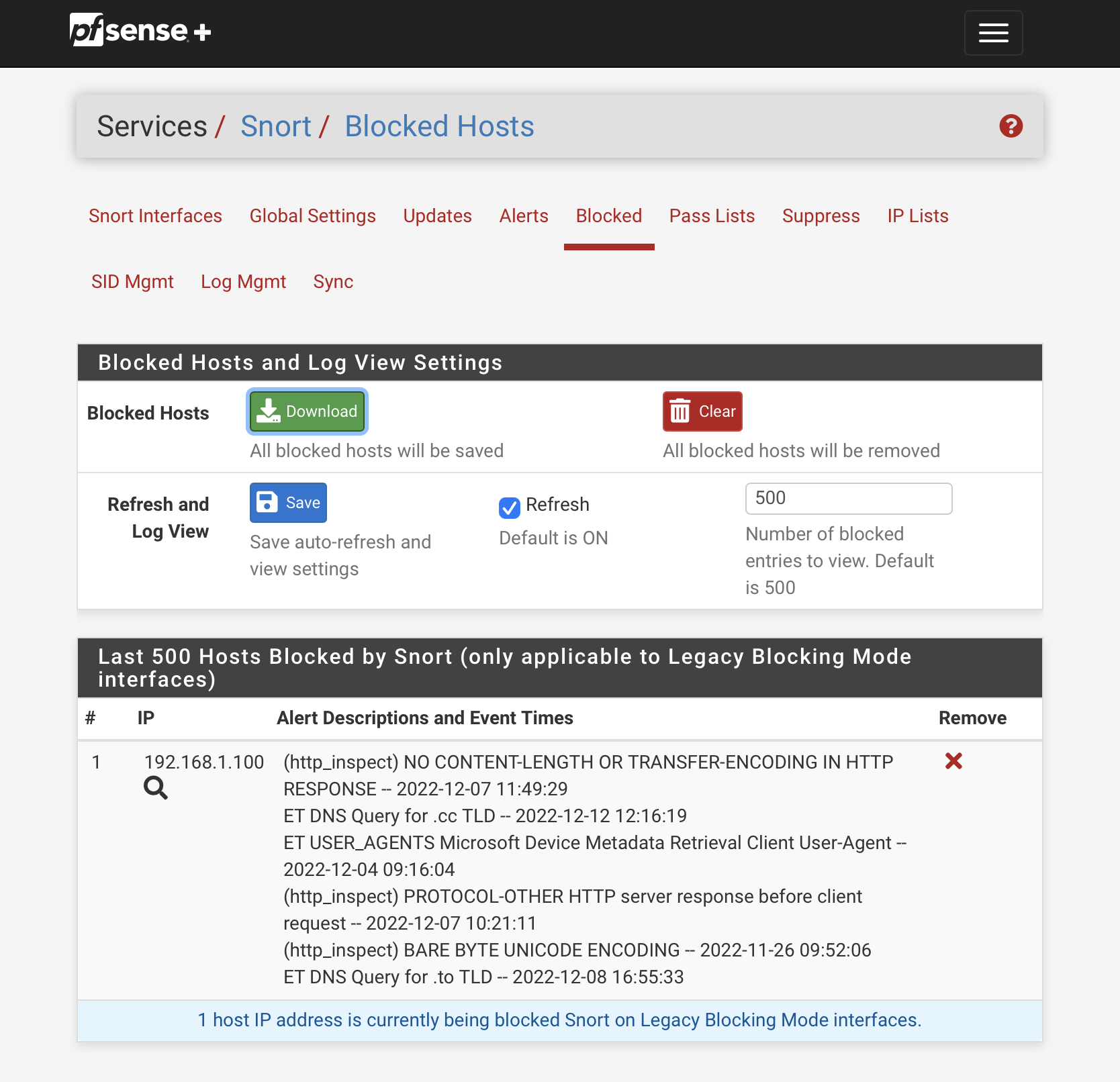
Today 2022-12-12 I set up access to pfSense for iPad in another LAN to be able to see what is going on. Snort had been shutdown since it was clear, that it was the cause.
Started Snot and sent browser to the problem URL and PC's IP came up right away in Snort blocked list. It is in the Home net and Pass list, so why was it blocked? It is also strange, that the dates in the screenshot are from last week, not from today.
Edit: There is also one from today.
-
@michmoor I would prefer inline mode, but have not applied it, because default action of the rules would have to be manually changed from ALERT to DROP.
-
@pfsjap I think at this point you should set to Alert until you can get a handle on your rule set: you can also use SID MGMT if you want to change mass rules from alert to drop
-
@michmoor Snort has a checkbox "Enable Packet Captures" to automatically capture packets, that create alerts. I thought I would have a look at the DNS query packet (i.postimg.cc) and enabled the checkbox & restarted Snort for the interface. When entered the "bad" URL into browser, to my surprise PC's IP was not blocked.
I reverted the checkbox and restarted Snort and PC will still not get blocked. So seems like Snort behavior is back to normal for now. Strange.
-
R rcoleman-netgate moved this topic from General pfSense Questions on
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.