Rule for disallowing all internet traffic
-
Yeah I just tested it using a schedule: unless I manually reset states after the rule takes effect, the rule seems to have no effect: users can still browse the internet. I see some config settings about max states the rule is allowed to create, etc., but I don't see anything like "reset all states automatically when rule takes effect and when rule stops taking effect".
-
@uniqueusernamebetween2 I would check out
https://docs.netgate.com/pfsense/en/latest/firewall/time-based-rules.html
I don't use schedules, and have not played with them in a long time - but when done correctly yes they should kill any states.
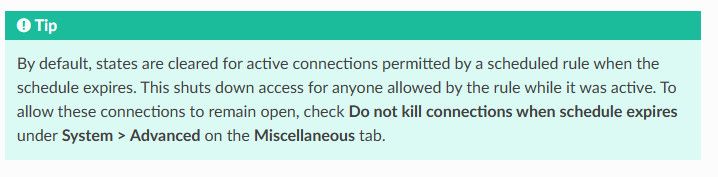
If your still having issues, let me know and post up your schedule, etc. and I will take look at what could be wrong.
I take it your trying to maybe block with a schedule vs allowing with a schedule? That could be problematic.
-
Thanks, that must be the issue: that I'm blocking with a schedule instead of allowing with a schedule. I'll create a bunch of aliases to make management easier then start allowing with a schedule. I appreciate all your help!
-
I've tried a few different configurations with no luck. Even when I disable the rules that allow Http or Https traffic, apply the changes, then reset the state table, I can still browse the internet without any problems. I'm on the latest pfsense software version. :( Below are my current rules: every rule not displayed is disabled. Interestingly, IMAP/SMTP wasn't working until I enabled them, but Http or Https traffic works to the internet regardless of what rules I configure, even without any schedule.
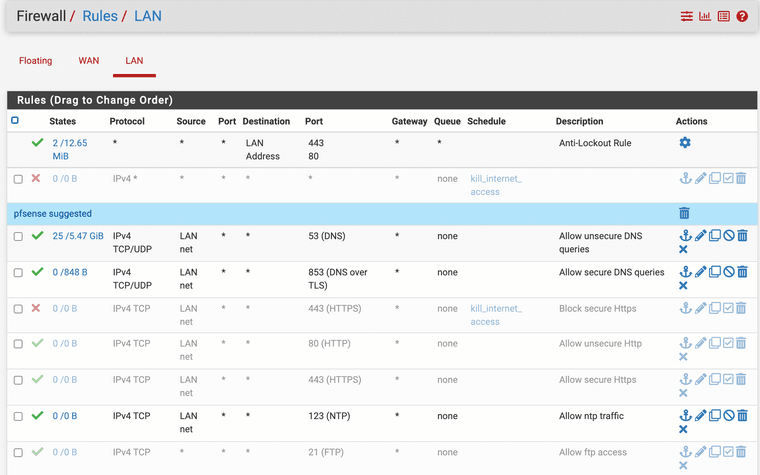
-
@uniqueusernamebetween2 not sure how you think smtp would work - you have nothing allowing smtp.. port 25.
There are no rules allowing anything other than ntp and dns and dot.. So unless your not showing all the rules, or you have rules on floating tab that allow traffic.
The only thing that would work with those rules as shown would be dns,dot and ntp.. Unless you had a existing state allowing the traffic.
-
Thanks, I appreciate your patience! I found the culprit, but I can't explain how yet. My laptop uses Mullvad VPN to connect to the internet. When this VPN is disabled, all the rules in pfsense work as I expect, so that's good. When this VPN is enabled, they're all bypassed and I can browse the internet without any issues. If I figure out how this happens I'll post again.
-
Think of a your VPN as a pipe. That pipe passes right through your router. Much like the pipe that supplies water to your house does not (intentionally) just spill its water out into your basement/subarea.. This VPN pipe is probably there to keep your laptop segregated from your home network.
My company laptop has a VPN for the same reason.. My company does not control my home network so they want their network protected from mine.. just in case. Make sense?
-
@uniqueusernamebetween2 how would your vpn even connect with those rules?
But sure if you had a rule setup before, or that is allowed out then none of your other rules would have any effect on traffic inside the vpn.. @chpalmer gave a good analogy..
-
@johnpoz said in Rule for disallowing all internet traffic:
how would your vpn even connect with those rules?
No clue. :( I did a packet capture and saw normal port 53/443 calls while the VPN is active.
Is there a way to set up the WAN on a timed schedule, as opposed to port rules on the LAN? That is, to disable the entire WAN interface regardless of ports, according to a schedule? If so that should prevent anything from connecting to the internet.
-
@uniqueusernamebetween2 said in Rule for disallowing all internet traffic:
Is there a way to set up the WAN on a timed schedule
Normally, WAN access isn't scheduled.
pfSense itself also needs WAN for NTP, DNS, package upgrade tests etc.What you probably want is this : Time Based Rules.