Blocked IP reaching server anyway
-
@cdsjerry said in Blocked IP reaching server anyway:
All the services are the mail server have been stopped and started since then so there shouldn't be any previously opened connections out there.
I don't think it is working like this. Reset the state-table to be sure. Also you could go to the states and search for that IP.
-
@viragomann said in Blocked IP reaching server anyway:
@cdsjerry said in Blocked IP reaching server anyway:
There isn't a single pass entry above this rule.
I meant other tabs, floating or interface group.
If you are not sure, which one passes the traffic, you will have to enable logging in each of your pass rules and check the log to find the responsible rule.
I've now reset the states-table. I don't see anything in the floating rules or interface group that would have allowed it in. Mine is a pretty simple system for a tiny company so no complex network to deal with.
I have to go to a meeting but I'll turn on logging in the rule and see what shows up tomorrow.
-
@cdsjerry said in Blocked IP reaching server anyway:
. All the services are the mail server have been stopped and started since then so there shouldn't be any previously opened connections out there.
Rebooting a server behind pfsense doesn't guarantee the state on pfsense would be cleared.
Your rule shows it has been evaluated a few times.. See the 0/27MB
-
To add a little bit to what @viragomann says, I find the output of pfctl -s rules very helpful in determining the exact order of the rules. You can run it from either the web interface (Diagnostics, Command prompt) or console/ssh in.
I can never keep straight which rules get applied first, as in "is it floating before interface or something else?", so I go straight to the cli.
Also as others say states on pfSense play a big role, so clear/flush
-
@mer I've never used that command before. I may have to explore it a bit but at first glance, how would I identify the IP of the person coming in? The only IPs I see are my WAN IP and the IP of the server their headed to.
For example:
pass in quick on mvneta2 reply-to (mvneta2 my.wan.ip.here) inet proto tcp from any to my.mail.serverIP.here port = pop3s flags S/SA keep state label "USER_RULE: Allows access to mail server domain.name" label "id:1431121752" ridentifier 1431121752As I scroll through the output from pfctl -s rules all of the output looks like the above example.
My pfSense is in Passthrough mode so perhaps that's making a difference here.
-
@bob-dig I reset the state-table yesterday just before running off to that meeting. But this morning I see that same IP is still attacking the mail server so it's still passing through pfSense. It attacks for a bit then stops for a few hours then comes back again. It's pretty much flushing the log files on pfSense before I happen to notice he's back so I'm not seeing the entry in the logs.
I know I don't know much about pfSense, but it seems like if I have a block IP rule entered in the top of the rules list before any allows, that the IP should be blocked, even if a rule below it would have allowed it. Isn't that the point of the rules order?
I notice I have an error showing. Would this error stop all the other rules from loading, essentially disabling the firewall? ```
"There were error(s) loading the rules: /tmp/rules.debug:27: cannot define table pfB_Europe_v4: Cannot allocate memory - The line in question reads [27]: table <pfB_Europe_v4> persist file "/var/db/aliastables/pfB_Europe_v4.txt" -
@cdsjerry Search the states for that IP. Maybe it gives you a hint, where you made a mistake.

-
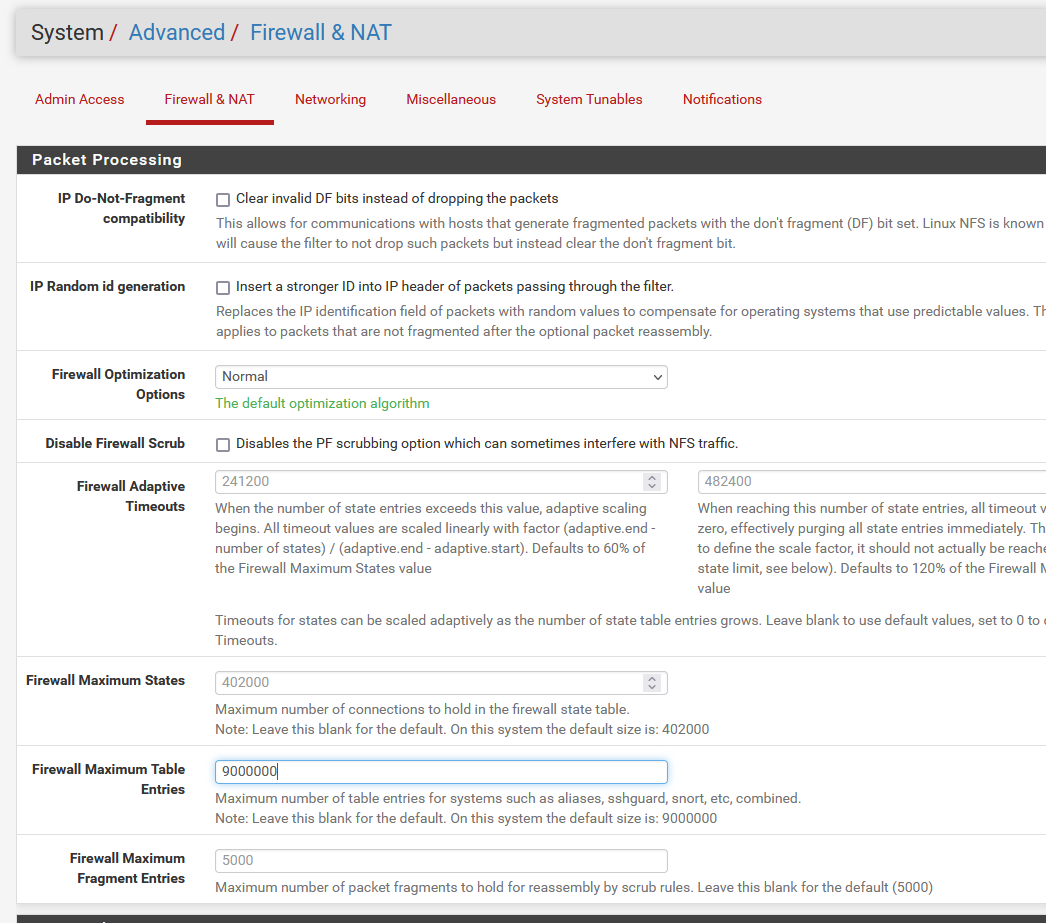
@cdsjerry If you have memory left, raise the Firewall Maximum Table Entries to some millions. I use 9 million on my pfSense.
-
@bob-dig I found it.. but not sure what it means. It's hitting multiple mail server IPs such as the .51 below. What is the FIN_WAIT_2:FIN_WAIT_2 4/5 mean?
WAN tcp 117.66.241.77:10113 -> My.IP.51:25 FIN_WAIT_2:FIN_WAIT_2 4 / 5 172 B / 208 B -
@cdsjerry said in Blocked IP reaching server anyway:
I notice I have an error showing. Would this error stop all the other rules from loading, essentially disabling the firewall? ```
Probably yes, do what I did and reboot the firewall afterwards.
-
@cdsjerry
You say you have a block rule but you never said what interface it's on.
Being that you said you don't know pfSense very well, I'm betting it's on the wrong interface.
Post pics of your rules pages per interface, the whole page, not just that one rule. -
@jarhead I didn't set it up by myself. I had an expert with me and we set it up together the first time. He's no longer available. I did pay for support service one other time to review all the settings and they found everything was OK. That was a couple of years ago but there haven't been many changes since then. Mostly just me adding repeat mail server attackers to an Alias when they launch DoS attacks on my mail server and bog it down.
I only have one WAN interface. All the rules apply to that WAN interface.
Is it safe to post pictures of the entire rules pages? I mean, that's giving information that could help someone get around the firewall isn't it? They would know what IPs might be easier to attack or spoof. I guess I could black them out but since it's not hard to find my IP range wouldn't that still be risky?
-
@cdsjerry That command dumps the ruleset as loaded, in the order they are evaluated.
You have a rule that uses an alias to block traffic from specific sources.The example you posted is an "allow from any to my mail server" has the keyword quick. That means if a packet matches this rule, no rule after it matters.
Now look for a deny/block rule that references your badguys alias; is it before or after the example one? If the deny/block rule is after the allow rule, then the deny rule never gets hit.
I don't know what pfSense "Passthrough mode" does so can't answer that.
People often edit the screenshots of the rules, redacting any public IPs or sensitive information.
-
@mer all of the allow rules are below the set of blocks, including the alias. So it should have been blocked by the alias and never moved down to the pass rule.
I'll black out some IPs and post the rule page in just a bit.
-
@mer Here are the 3 pages of WAN rules plus the page of floating rules. The IP we've been looking at is in the Badguys5 alias.
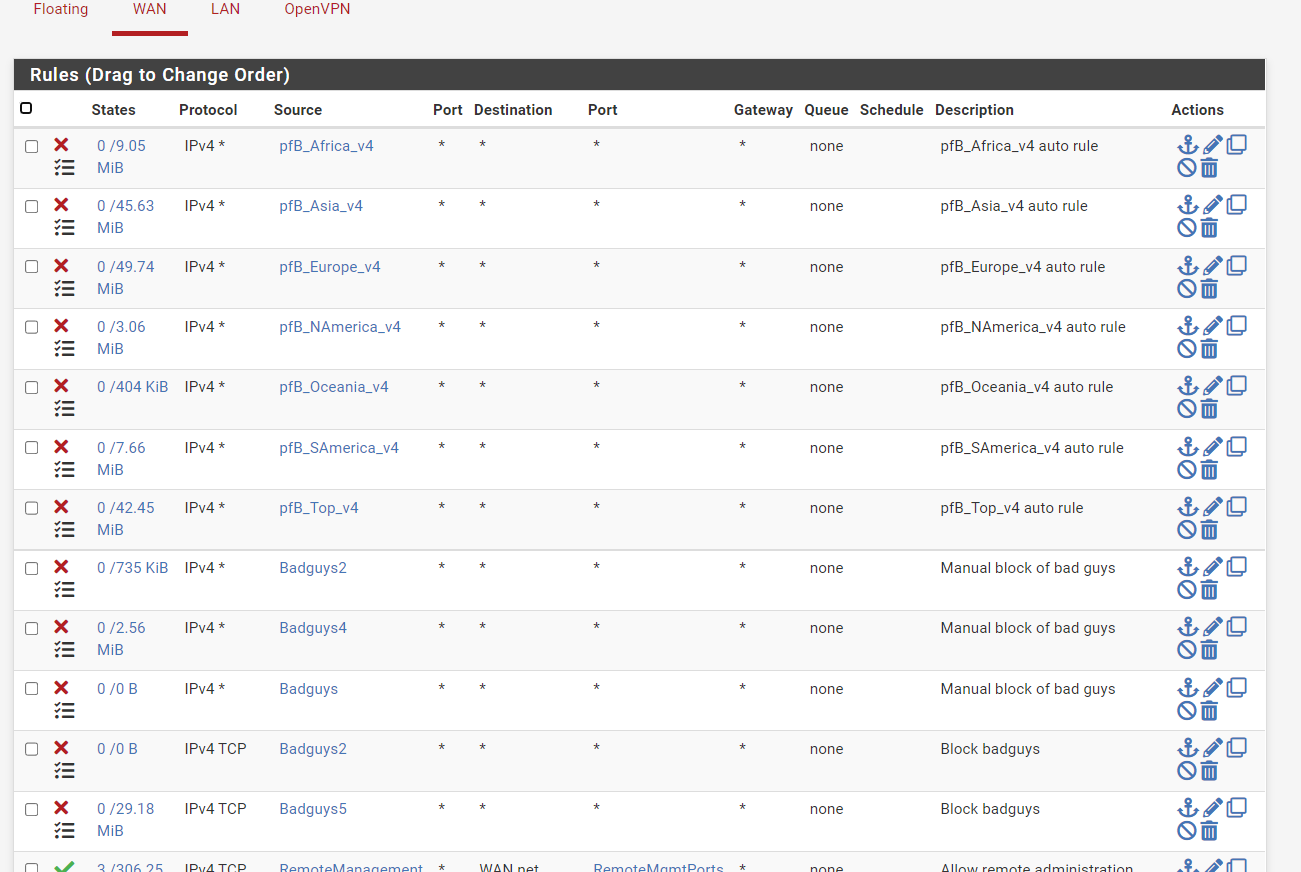
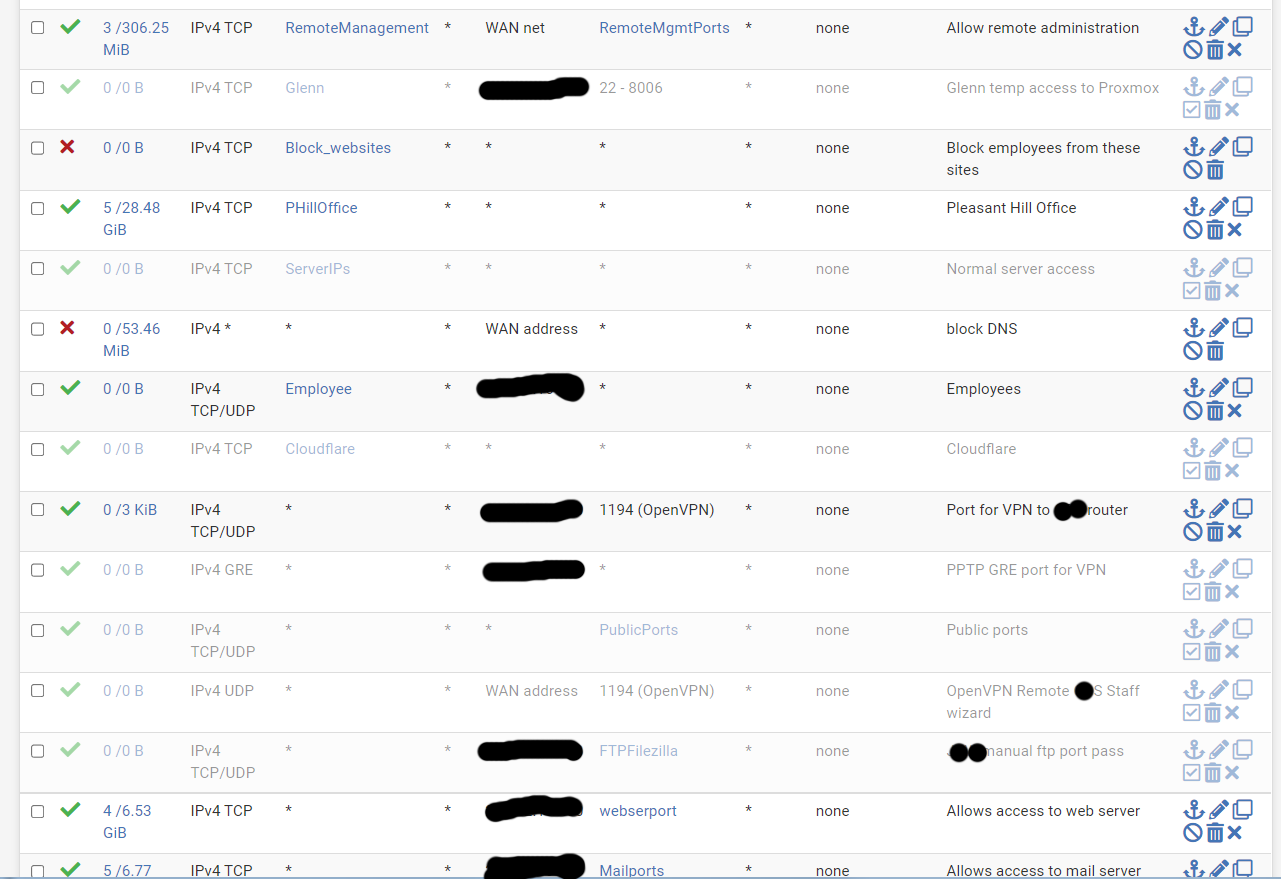
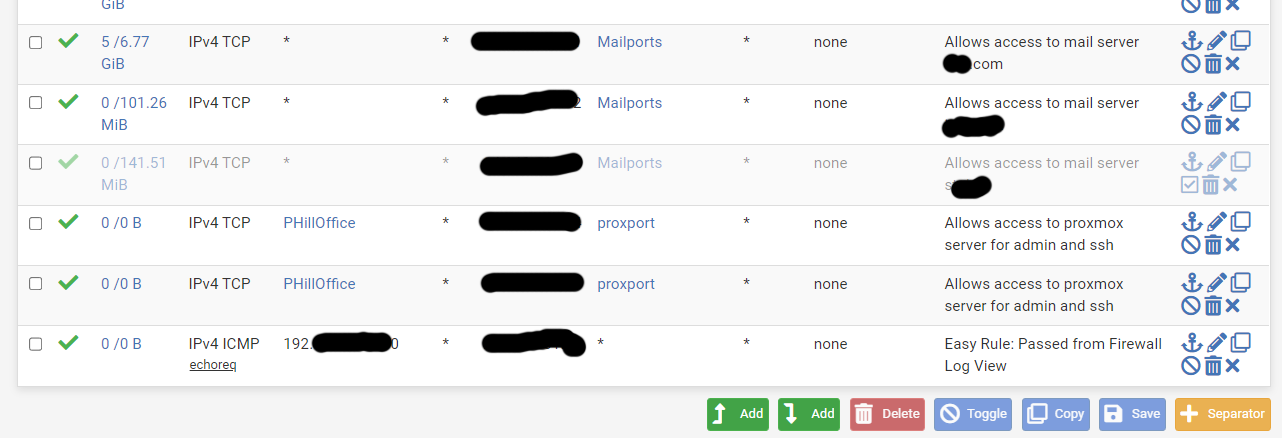
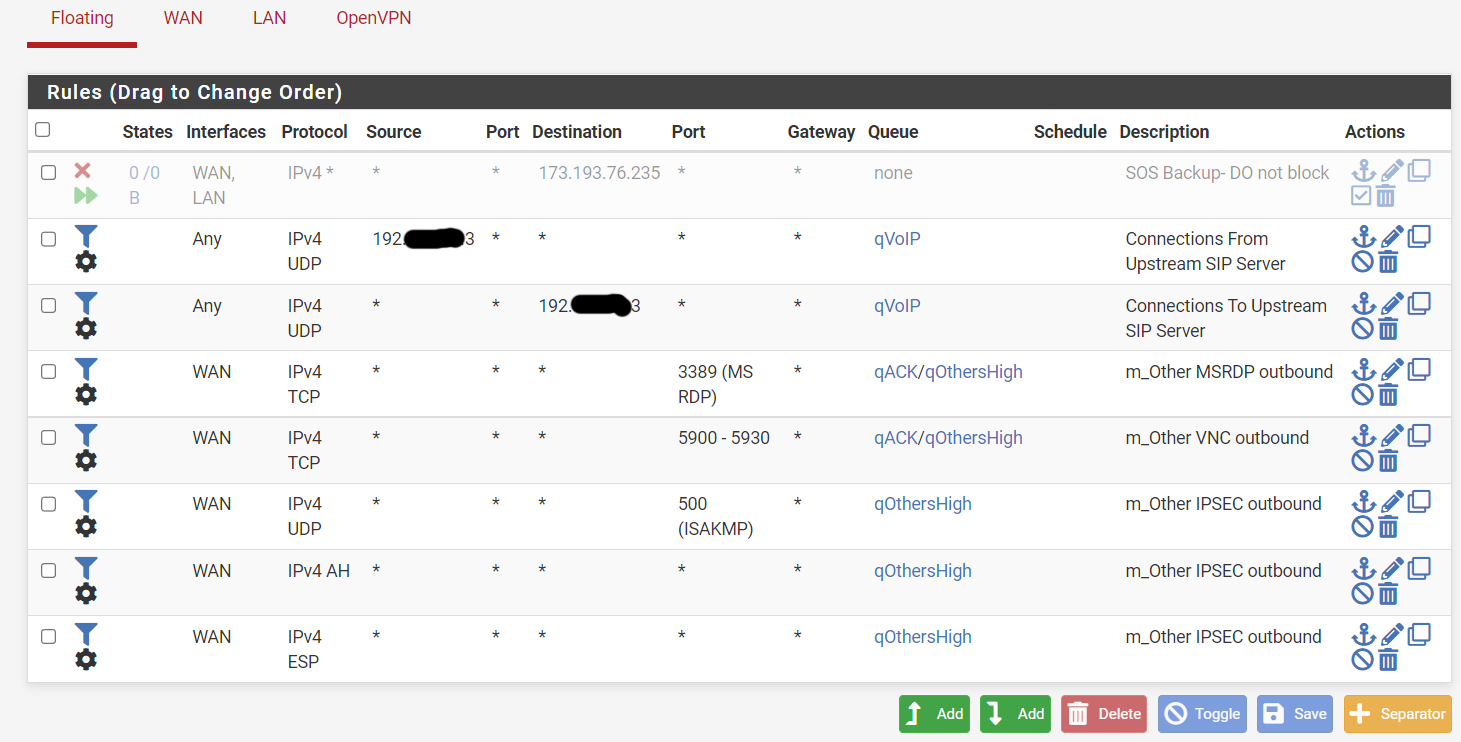
-
@johnpoz I'm still seeing logs in the mail server from IPs that should have been blocked by pfSense. I disabled pfBlocker for a bit since I was getting the error on it mentioned above. I thought perhaps the rest of the rules weren't being loaded once it hit that error. However with it pfBlocker disabled and all the States reset, I'm still having the same issue with IPs in the Badguys5 block rule still getting to the mail server. While the IP listed below is a different IP as the first example seems to be giving me a break for a bit, this IP is in the same alias for blocking and it's getting past pfSense
Dec 28 11:25:15 WAN 38.27.110.8:55033 my.mail.ip.1:25 -
@cdsjerry whenever you add something new to an alias or just specific block on that IP. You have to make sure there are no existing states. Blocks will not take effect until there are no states that match.. States are evaluated before any rules, floating is first, then the interface..
example
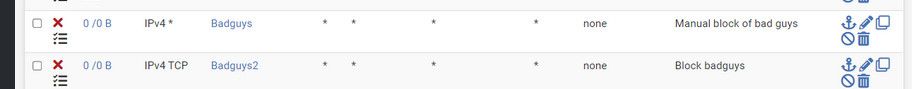
These rules are not showing any evaluations - see the 0/0 on them
-
@johnpoz But in this case I've reset the states and it still shows up. Wouldn't resetting the states allow the block to work? Is rebooting the firewall needed or something?
I mean adding an IP to a block list and expecting that IP to then be blocked doesn't seem all the unreasonable to me. I did the Apply. I reset the States. What more has to be done to actually stop traffic from that IP (and all the others on the blocked list)
-
@cdsjerry see my example above - you have 2 rules with badguys alias that are not triggering.
-
@johnpoz I didn't know how to interpret those numbers. So the 0 is showing no "triggers" for that rule, yet the IPs inside that rule are still getting through. I still don't understand that. Why would it not be triggered if that IP is accessing my server? Are you saying a Floating rule is allowing it to pass before it reaches these rules? My Floating rules are posted above, I don't know how it would be getting past? I'm obviously missing something.. but what?