(RESOLVED!!!) WARNING!! Emerging Threats Dshield rule set is now empty inside Snort and on Emerging Threats official website
-
@jonathanlee
WARNING!!
Please note this is also now seen when you visit the ruleset website !! Could be a false positive.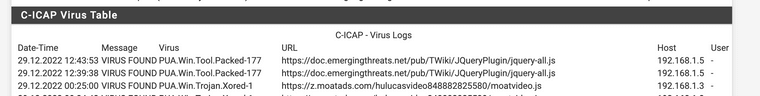
(Image: ClamAV sees a tool packed for ET website hosting the Dshield ruleset)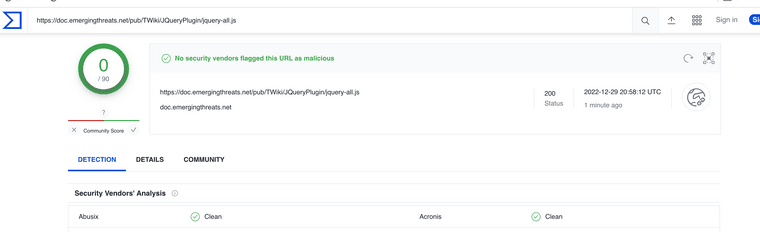
(Image: Virus total check) -
@jonathanlee pfBlockerNG has it under the ISC_Block name, which has content: https://isc.sans.edu/block.txt. That file also references URL http://feeds.dshield.org/block.txt.
-
@steveits said in WARNING!! Emerging Threats Dshield rule set is now empty inside Snort and on Emerging Threats official website:
http://feeds.dshield.org/block.txt
Thanks for the reply,
Do you know how do I change the url referenced automagically by Snort?
-
@jonathanlee I do not, sorry. For block lists we use pfBlocker and hence firewall rules instead of packet matching.
Side note: running on WAN, Snort will inspect every arriving packet even if disallowed by the firewall. On LAN it will also show LAN device IPs in alerts.
-
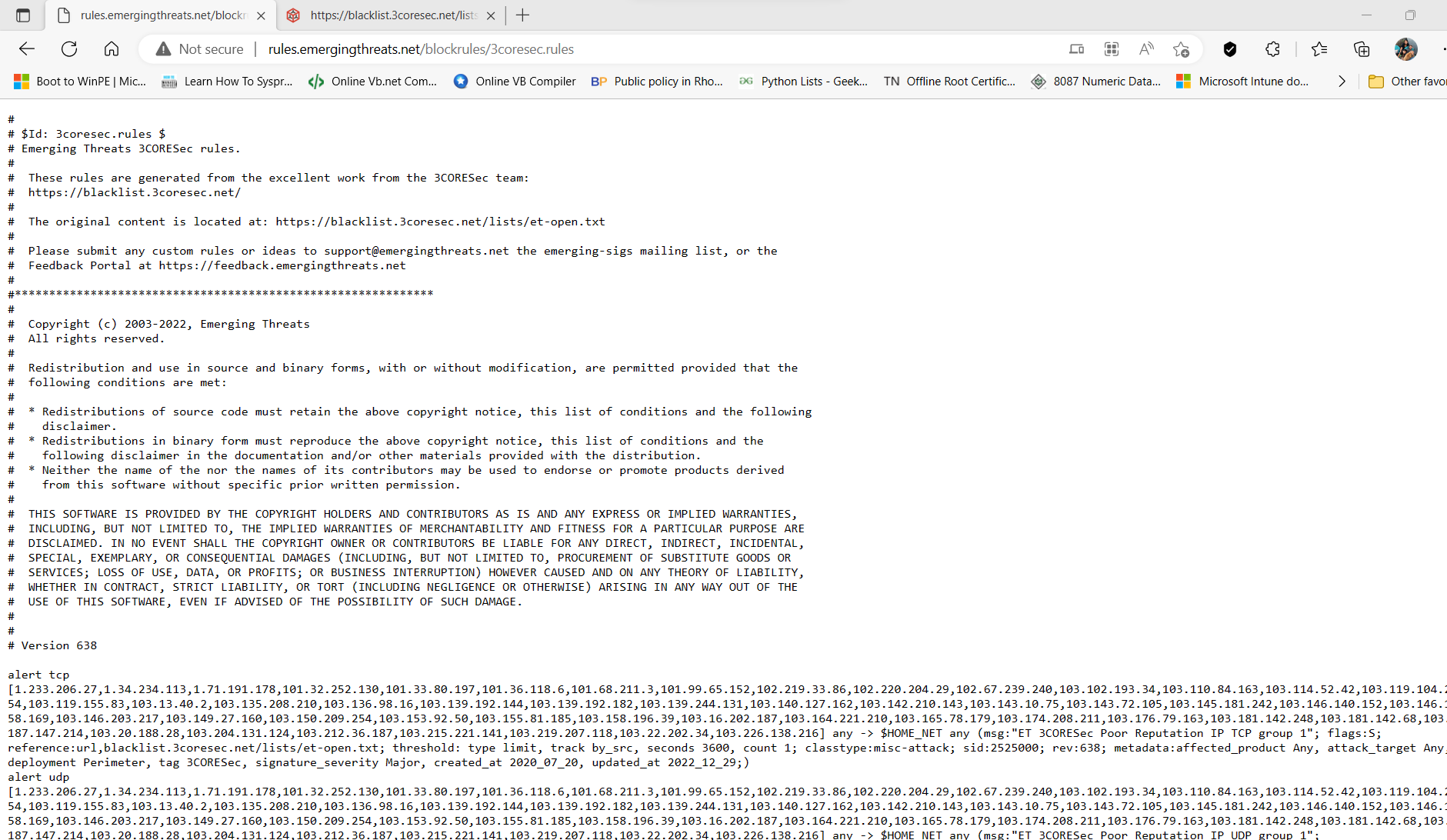
@steveits I found a way
custom is hidden at the bottom of the rulesets
Just copy and paste in the rules needed. Again, the ones that are no longer listed are emergining-dshield rulesets. Your list is the default block list that is a different ruleset.
(Image useable ruleset that does not load automatically)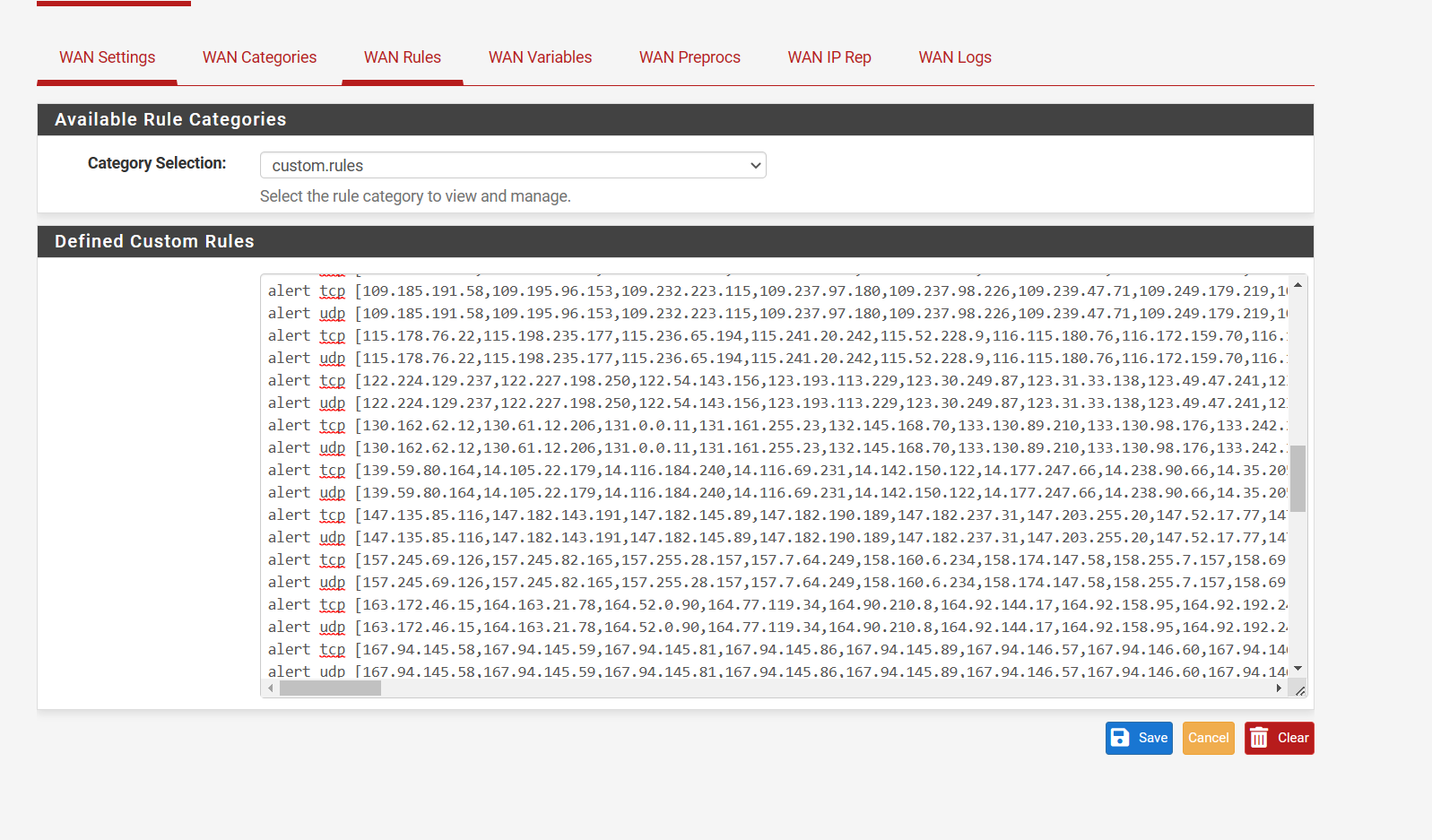
(Image plugged in)
http://rules.emergingthreats.net/blockrules/
There are many rulesets categories that are not loading you can add to custom if needed.
I learn something new every day on this thing.
-
Suricata also allows you to enter an unlimited number of custom rules download URLs on the GLOBAL SETTINGS tab. So, you can easily enter the complete rule download URL there and they will be constantly updated by the cron task just like the other already included rules.
You don't have to use the Custom Rules option for this, but you can if you want to.
-
(Image: Custom Rules now generating alerts)
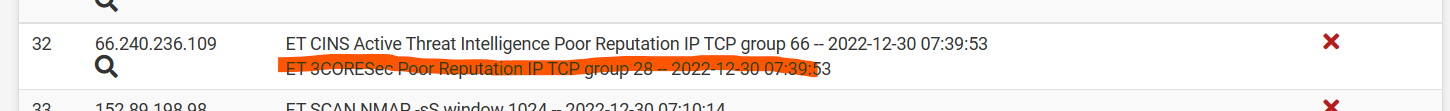
(Image: Custom Rules not generating blocks)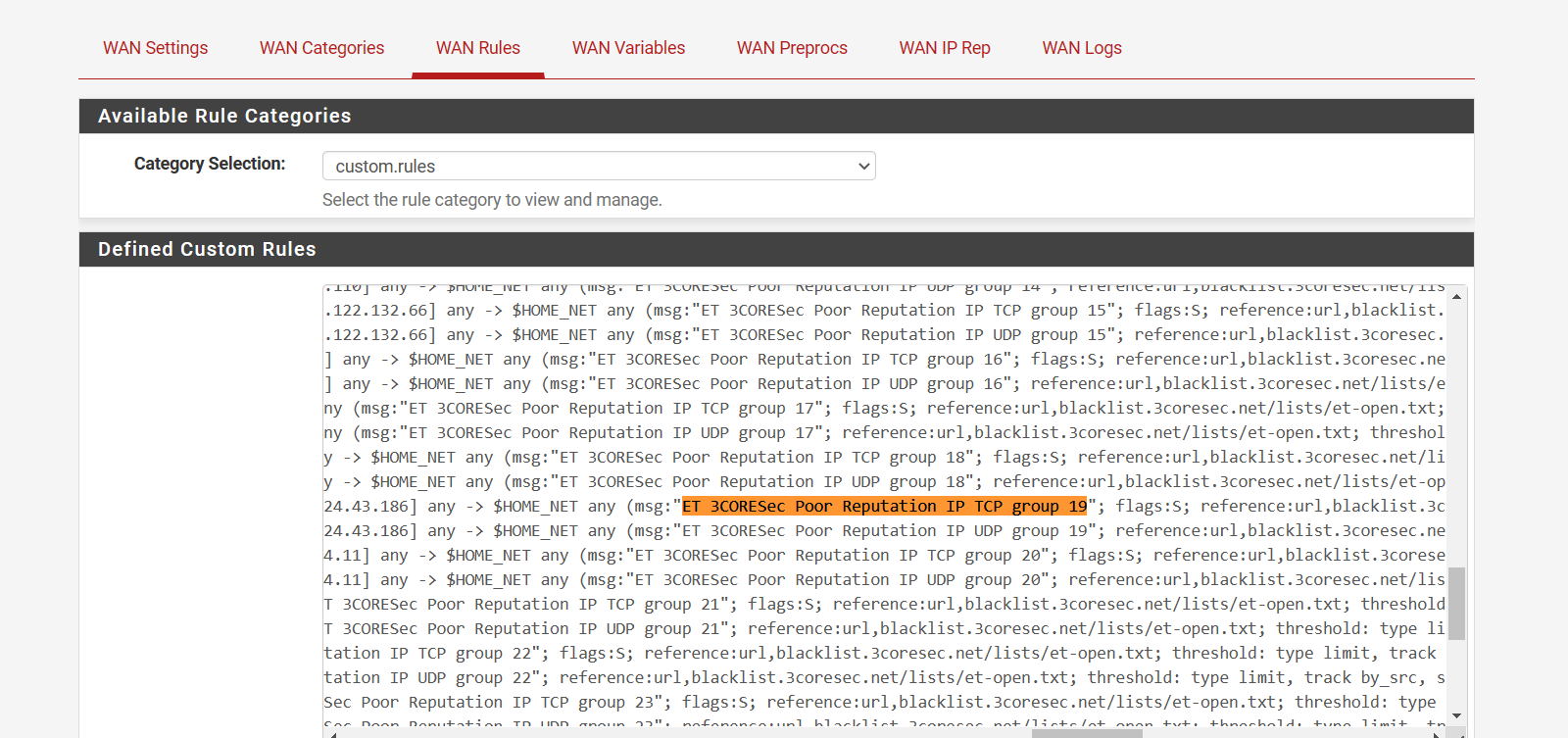
(Image: Ruleset source is inside of the custom rules that were just loaded)3CORESEC OPEN RULES LOADED:
This was loaded via custom option inside Snort for Pfsense -
@jonathanlee Did you already email support@emergingthreats.net from the feed file?
-
@bmeeks I wonder if Snort has a URL option that you can use inside of the custom area.
-
@jonathanlee said in WARNING!! Emerging Threats Dshield rule set is now empty inside Snort and on Emerging Threats official website:
@bmeeks I wonder if Snort has a URL option that you can use inside of the custom area.
No, Snort does not currently have a custom URL option like Suricata.
-
@steveits Yes I emailed the yesterday, they may have disabled that ruleset for some unknown reason. If not, I did email them that it is blank, they might have moved it to pro.
-
They have just replied, they are looking into the issue,
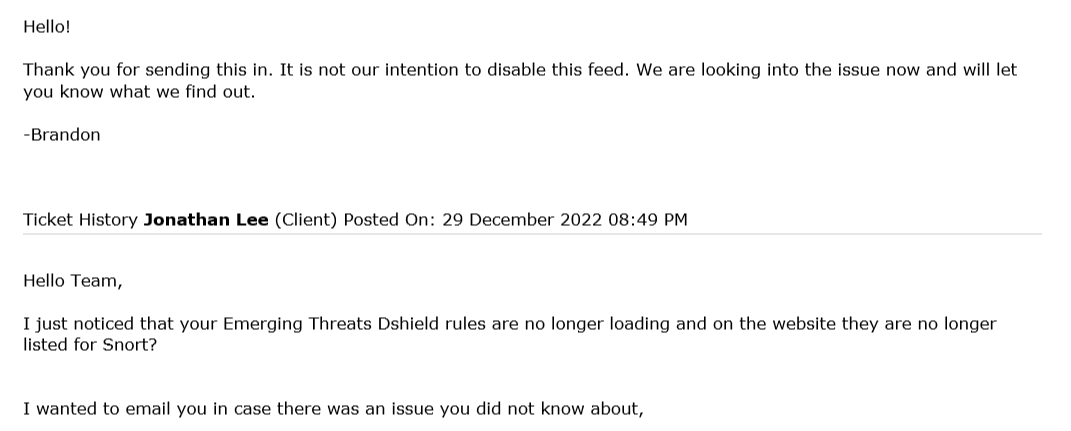
I guess it was not the intention to disable that feed. I am glad they are looking into it. I wonder what happened? Some rulesets have been blank for some time now I started wondering about it when the alarms stopped coming in.
-
-
@jonathanlee Nice !
Curious, why not use pfblocker for the IP blocking you need? -
@michmoor I like Snort's IDS (Intrusion Detection System) and IPS (Intrusion Prevention System) software. I had snort software as a kid when it was a wireless scanner software much like Wireshark, it has much improved over the days of the late 90s early 2000s. It use to be called AirSnort!!

Anyway fast forward to today. I like that it will scan and use emerging threats and has auto updated rule sets. I use Squid Proxy it just works well, it even stops Nmap scans cold in their tracks. I have never used pfblocker, with HTTPS over 443 DoH all over the place total reliance on a DNS based version kind of worries me. With use of Squid it uses HTTP headers so you can see if something is port jumping to a new DoH server. Plus I have it working with HTTPS for SSL so Clam Av works for HTTP and HTTPS on it. It did take me some time to get to working with the configuration, however it blocks and protects now. I can see in the logs huge lists of items blocked or viruses stopped over the proxy.
I have never used pfBlocker why do you like that one? Got any screen shots?
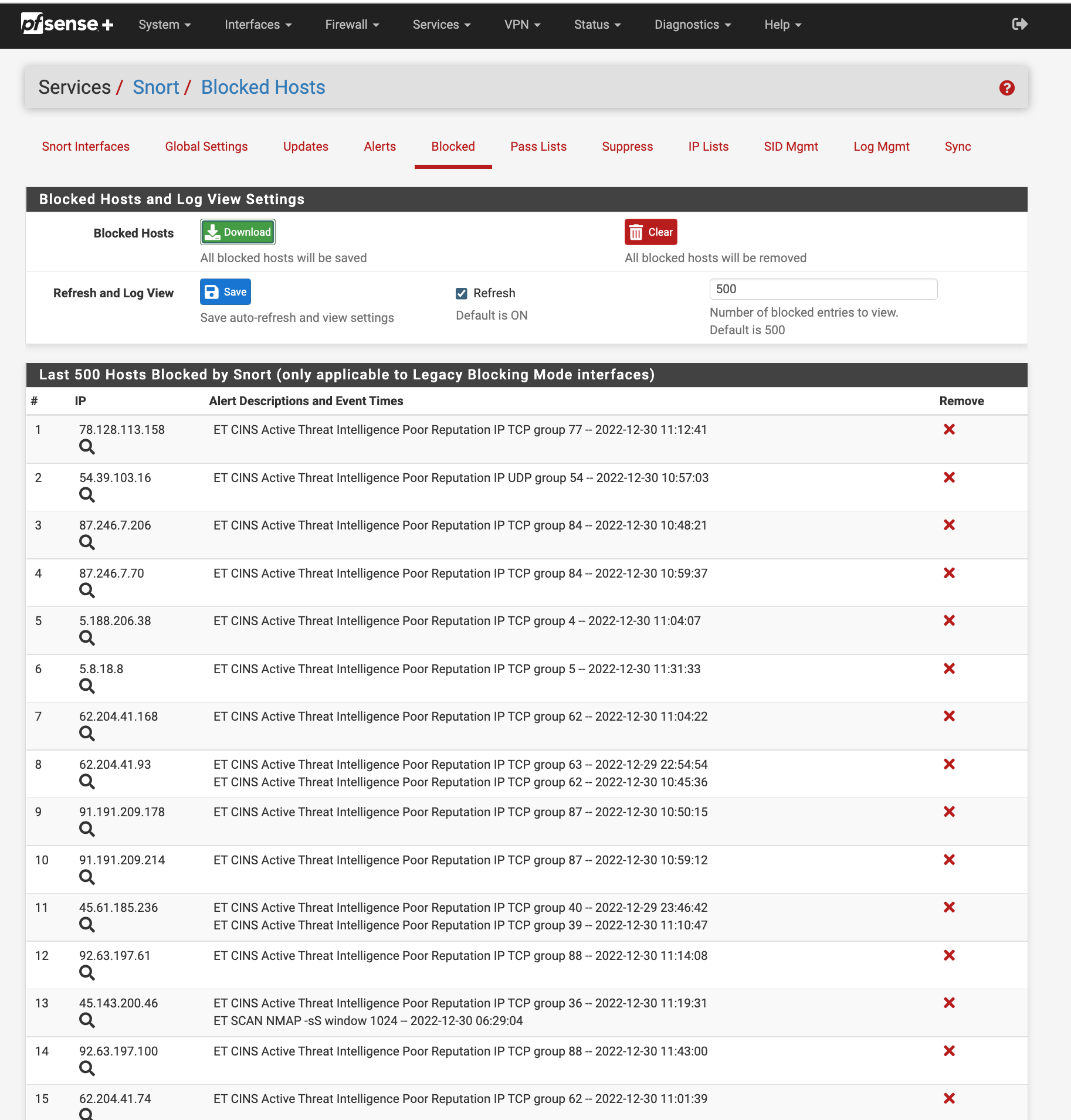
(Image: 50 items over the last 1 hour blocked)
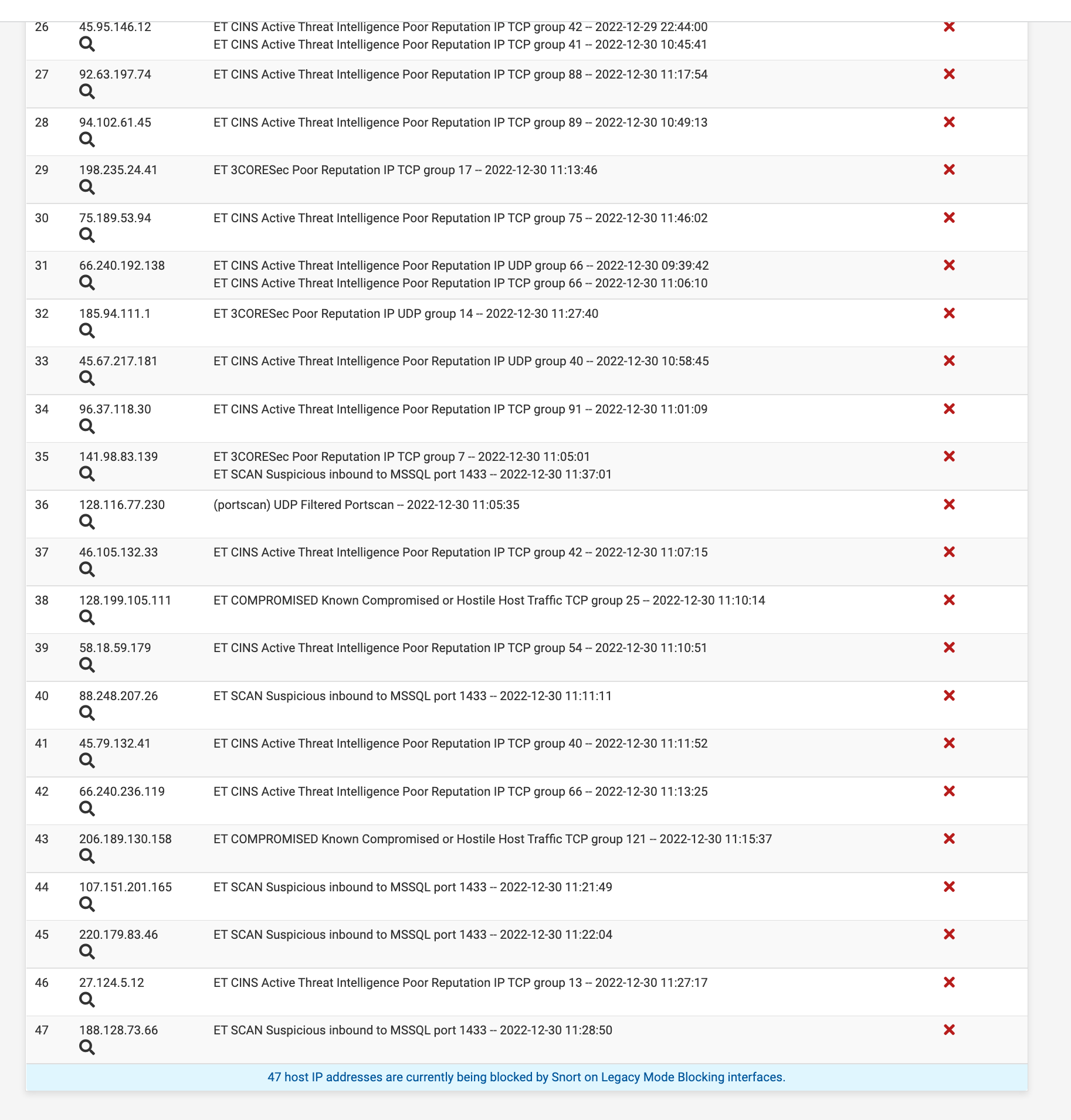
(Image: Caches UDP scans even)
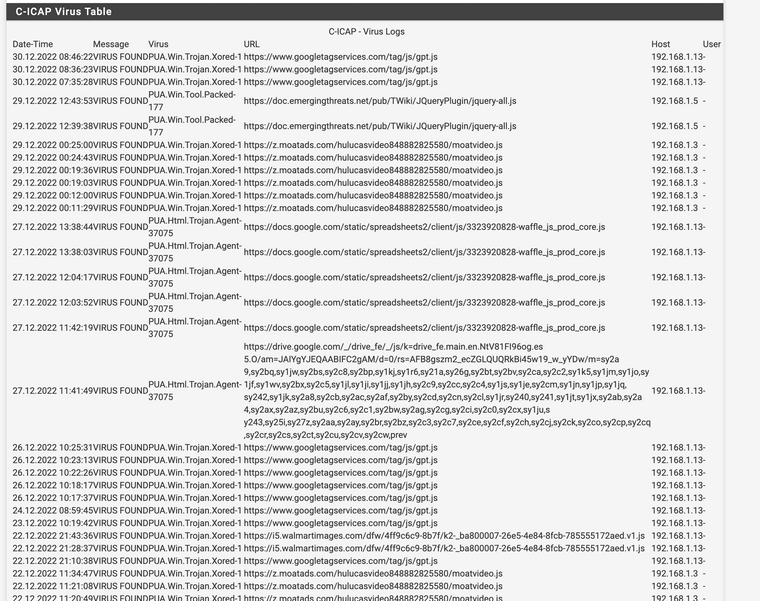
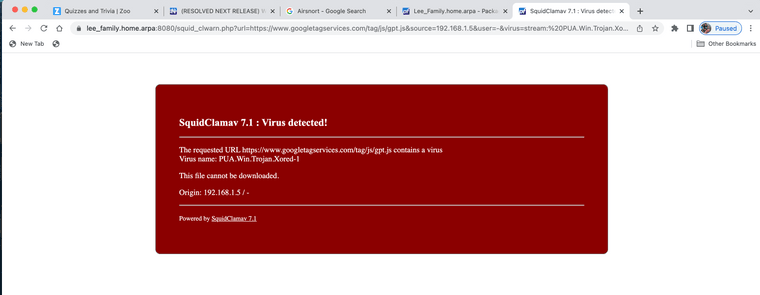
(Image: ClamAV viruses caught last couple days over HTTPS)
Yes they have some false positives, again that means it is working. The fine tuning takes some time. I have never seen pfBlocking yet, I should check it out.
-
For just plain IP blocking, a package such as pfBlockerNG-devel is more efficient than Snort or Suricata. For content inspection, you must use an IDS/IPS package. But remember that end-to-end encryption can severely cripple an IDS/IPS. That being said, some features of IDS/IPS are still useable to some degree -- for example, the OpenAppID feature of Snort.
And if you do MITM SSL termination, then an IDS/IPS can be very useful for payload inspection. But there is quite a bit of extra work involved with MITM setup.
I will say, that for IP-only rules, Suricata can also be quite efficient. That's because when it identifies and sorts rules based on that criteria, there is very limited packet inspection. It simply checks the IP address and makes a quick decision. So, for IP-only rules, Suricata will be nearly as efficient as the firewall itself. An IP-only rule is one where there is no payload content matching specified in the rule.
-
@bmeeks I agree the MITM setup took me some time to get it to work with all the certificates.
-
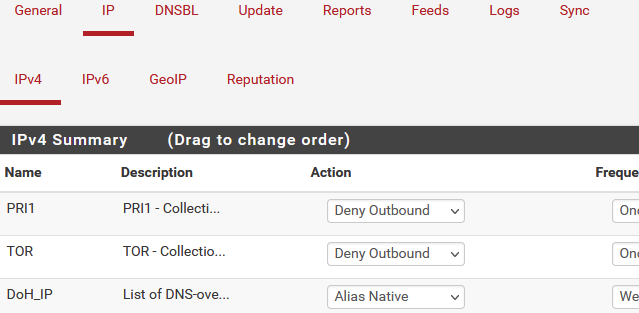
@jonathanlee I'd say pfBlocker has three main elements:
1a) IPv4 and IPv6 feeds
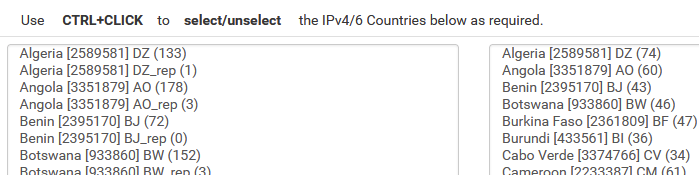
1b) geoIP lists by country
2) DNS block lists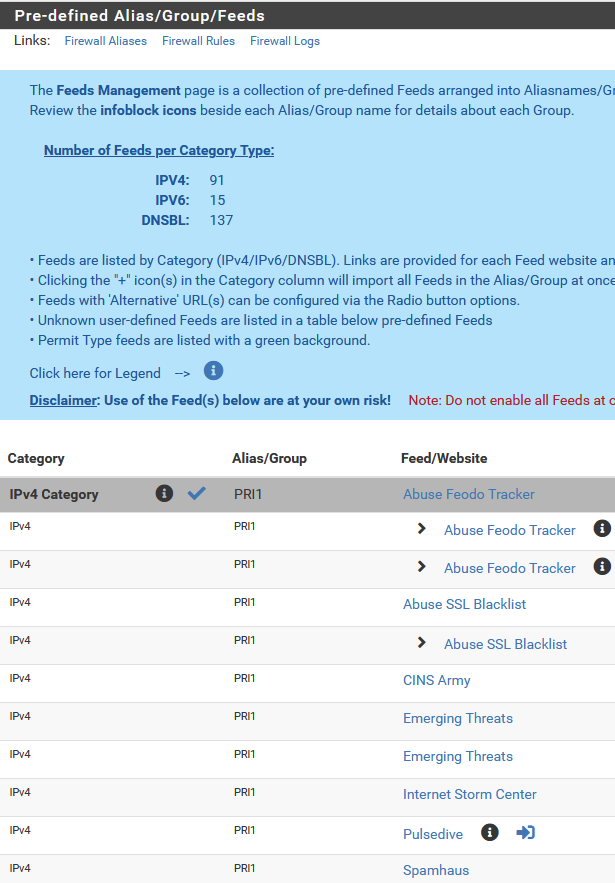
IP lists that are enabled have options:
geo:
-
@steveits thanks for sharing that looks like amazing software. I have never seen that package installed or screenshots of it until today. Again I hear about it in the discussion posts all the time. Thanks for sharing.
-
@steveits Palo Alto does country blocks also.