Block access to cable modem from guest network
-
Hi All:
I have an SG-1100 running 22.05-release. The SG-1100 has these connections:
• WAN port – cable modem (cable modem IP:192.168.100.1)
• LAN port – network switch and is my secure LAN (192.168.10.0/24)
• OPT port – wireless router with untrusted IOT devices (192.168.20.0/24)I want the IOT devices have access to network printers on the secure LAN and internet only. Here is a screen-shot on my firewall rules for the IOT network:
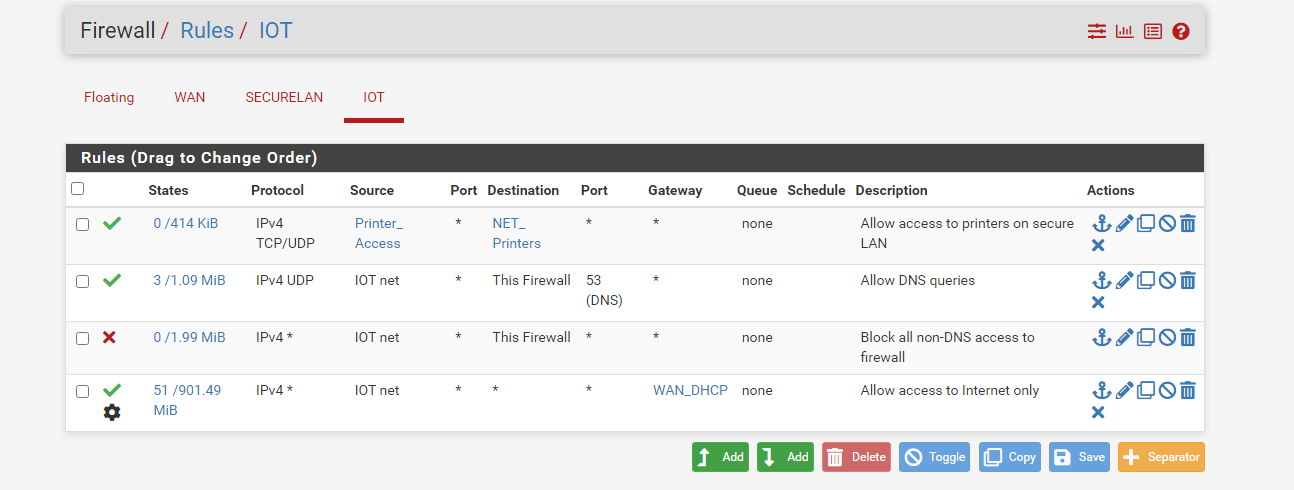
The first rule gives specified systems access to network printers. The second allows DNS to IOT systems. The third blocks all other access to the firewall and the 4th allows internet access. The problem is that IOT systems can access the cable modem GUI. I suppose I can add rules to specifically prevent that but I don’t understand why the cable mode is accessible on the IOT LAN. Can someone explain why this is allowed?
Is the safest thing to do is replace the 3rd rule with one that blocks access to ALL private IP addresses?
-
Last Rule Destination is any and this is the Problem.
Use an !RFC1918 and it will be blocked if your Modem is on 192.168.100.1.
If you use IPv6 use the RFC4193 to.
-
@kenw said in Block access to cable modem from guest network:
replace the 3rd rule with one that blocks access to ALL private IP addresses?
Then they would be able to get to pfsense gui via the public IP on its wan. While !RFC1918 could work, its better to just directly block vs blocking with an allow, ie add a rule above 3 or below 3 that blocks access to either all rfc1918 or the 192.168.100 address or netblock.
Why do you allow them to all IPs on pfsense for dns, wouldn't it be cleaner to just allow them dns to the iot address.
-
Since when are printers secure in the first place? Put them in their own (V)LAN.

-
@kenw said in Block access to cable modem from guest network:
Here is a screen-shot on my firewall rules for the IOT network:
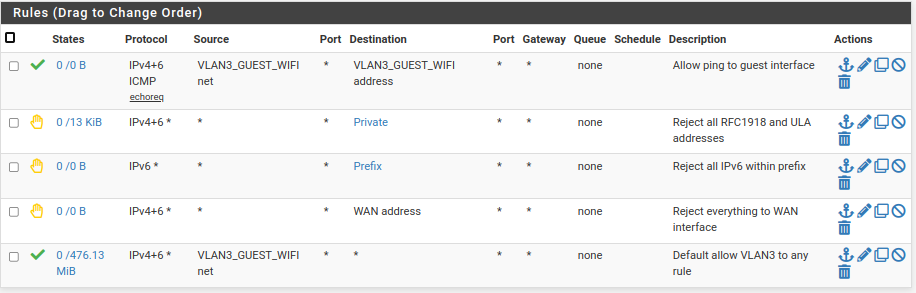
Here are my rules. They allow only access to the Internet and also ping to the interface.