OpenVPN/pfSense [Site-to-site ]: rules and interfaces problems
-
Hi there,
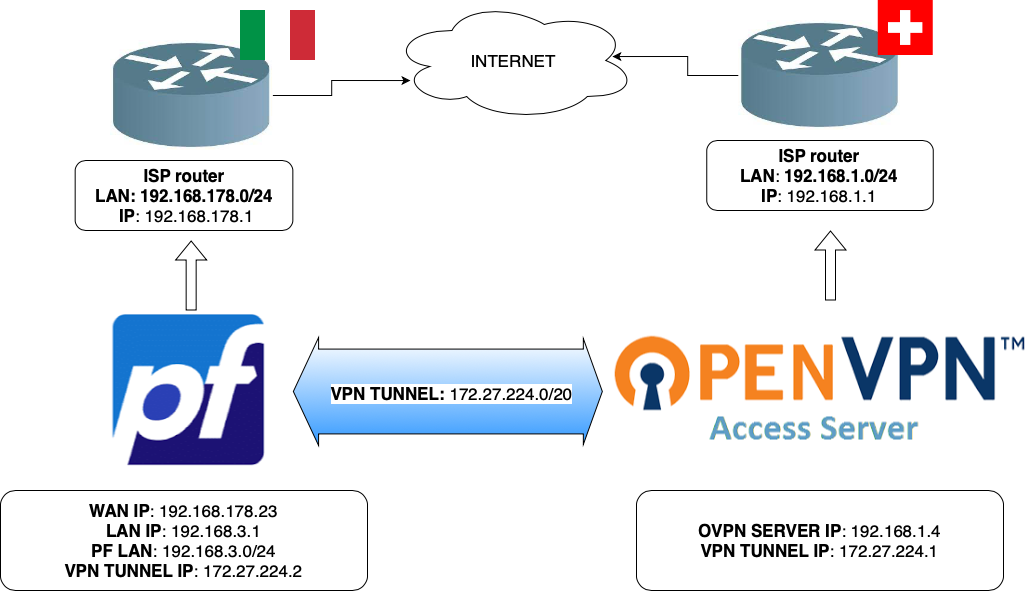
I was struggling with a site to site configuration which has been set as follows:
- Server OpenVPN (running on Ubuntu) (Switzerland)
- Client OpenVPN Pfsense (Italy)
The connection between those 2 is now up and running, except from 2 issues I'll explain hereunder.
In order to set up the vpn tunnel I followed this guide here: https://openvpn.net/vpn-server-resources/site-to-site-routing-explained-in-detail/
QUESTION 1
Since I'd like to prevent LAN 2 clients (192.168.1.0/24) to freely reach the others from LAN 1, I was trying to implement some rules in pfSense...
As you can see from the screenshot here above, pfsense created a virtual interface (OpenVPN) from which I can manage all the traffic passing trough the tunnel (OVPN_CH).
Why pfsense created this new (virtual) interface? I believed I could manage the traffic to/from the tunnel by means of the interface OVPN_CH (which was created when I configured the OpenVPN client on pfsense). Instead, any kind of rule I try to set on this interface, sort no effect on traffic.
QUESTION 2
I used to connect to my LAN 1 (192.168.3.0) with another openVPN client (with a different tunnel and configured on my smartphone only - you'll see this interface among the others in the pic: OPENVPN). However, since all the traffic from both the vpns gets now managed inside the new interface (OpenVPN), I have problem distinguishing whether it comes from my smartphone' client or from any client within the site-to-site.Is there a way I can separately manage the two VPNs?
The only way I found, for example, to block access to a client in LAN A (let it be 192.168.3.5) from LAN B is the following rule:action: block
interface: OpenVPN (if I set OVPN_CH: the traffic is not blocked at all, neither from the smartphone, nor from the site-to-site)
source: net 192.168.1.0/24
destination: 192.168.3.5Problem: if my smartphone connects to its separate vpn while being connected to LAN B' wi-fi, it has no chance of reaching the 192.168.3.5 and gets obviously blocked by pfsense.
Thank you
Luca -
L lucaset256 referenced this topic on
-
@lucaset256
"OpenVPN" is an interface group, implicitly created by pfSense when you configure your first OpenVPN instance, either a server or a client.
This interface group includes all OpenVPN instances configured on pfSense.There is no way to remove it.
Consider, that firewall rules on an interface group tab are evaluated before rule on its members. If the traffic matches the rule it is applied and further rules are omitted.
To assign an interface to OpenVPN servers is only needed in special circumstances and it's probably not necessary for your access server.
Anyway, you can create interfaces to the servers and add your firewall rule to them.So best practice in your case, since you have already created interfaces for all OpenVPN instances, is to remove all rules from the OpenVPN tab and add your rule only to the members.
Rules on your manually created interface are only applied to the respective OpenVPN instance. -
@viragomann thank you so much, that was it!
By the way, I can now reach LAN B (external) from LAN A (internal) but I have to access to LAN B from the other internal LAN C. Do you know how can I route the traffic?
LAN A --> interface 1 on pfsense
LAN C --> interface 2 on pfsenseI tried to send a 121 from DHCP with no luck
18:C0:A0:01:00:C0:A0:03:01 --> which should route 192.168.1.0/24 through 192.168.3.1Herebelow my static route
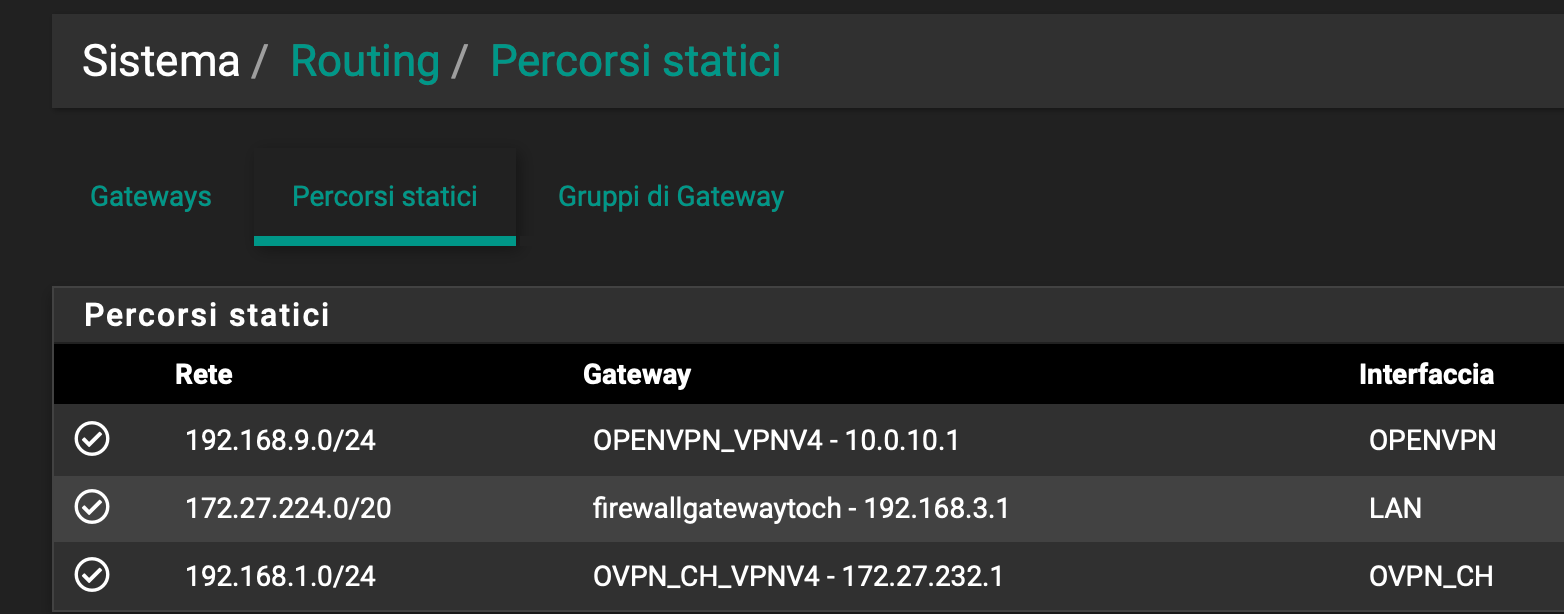
and my gateways
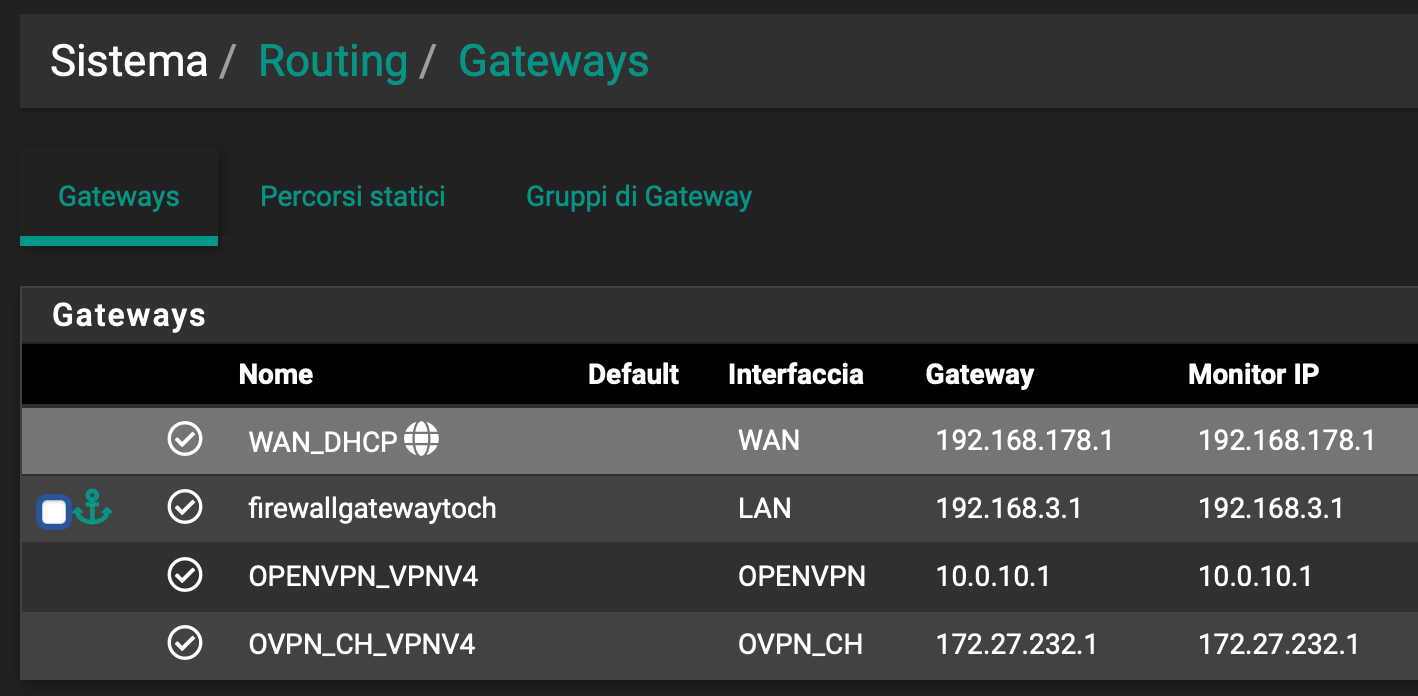
Thanks for helping!
-
@lucaset256
You shouldn't create static routes to VPN gateways. The routing should be done by OpenVPN.To do this for the site-to-site VPN enter the respective remote Lan network into the "Remote Network/s" box on each site.
By the way, I can now reach LAN B (external) from LAN A (internal) but I have to access to LAN B from the other internal LAN C. Do you know how can I route the traffic?
I cannot see in your graphic, which one A, B and C is.
Which of these are connected by a VPN? -
thank you once again; I've made it.
I deleted all my previous configs and started again. The problem was declaring the VPN tunnel on my pfsense client configuration. Since the server has been set to dynamically provide IP addresses through the VPN tunnel, I think it conflicted somehow.
Just for anybody else facing this issue, I've managed it in this way:
SERVER SIDE:
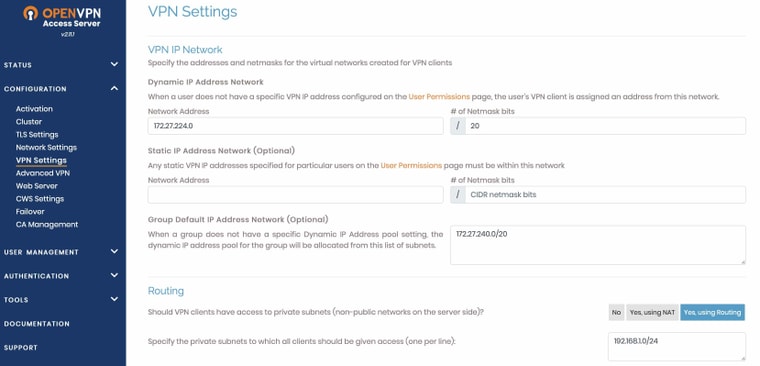
(note the dynamic IP address network)
then I declare the subnet to which all clients should be given access (I previously named this subnet LAN B)
Then, on specific USER PERMISSION (OPENVPN ACCESS SERVER) I set:
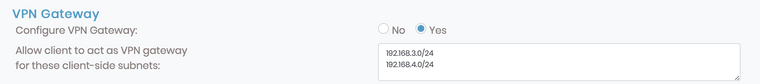
So that the user I'm connecting from will be capable of reaching both my client side LANS (the pfsense's ones)
CLIENT SIDE (pfsense)
No tunnel ip has been declared (because it is dynamically provided by the server)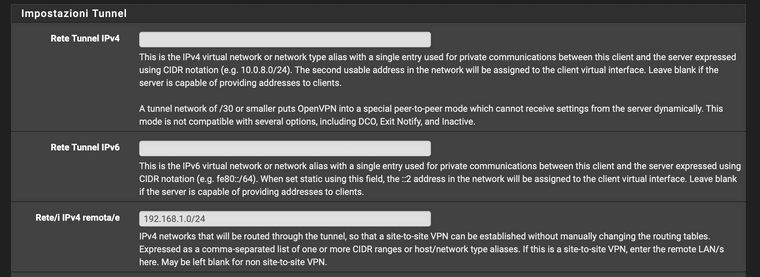
The remote LAN I want to reach has instead been declared (192.168.1.0/24 - SERVER SIDE LAN)
NO GATEWAY NOR STATIC ROUTE HAS BEEN MANUALLY SET; THEY GOT CREATED BY OPENVPN CLIENT ITSELF
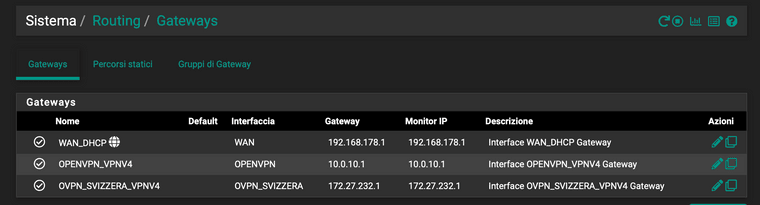
Everything's working now: I can ping the external LAN (server side - 192.168.1.0/24) from both my pfsense LANs (192.168.3.0/24 and 192.168.4.0/24).
Thank you once again!