Setting drop (block) for Snort IPS policy rules in Suricata with Legacy Mode
-
@youngy I dont see
IPS Policy - Connectivitylisted in your screenshot. There are two ways of handling any rule or ruleset when using Suricata in an IPS fashion.
Enable the individual rule within the category OR enable the whole category.
Secondly you have to enabled he list and make sure its set to drop. Click save.
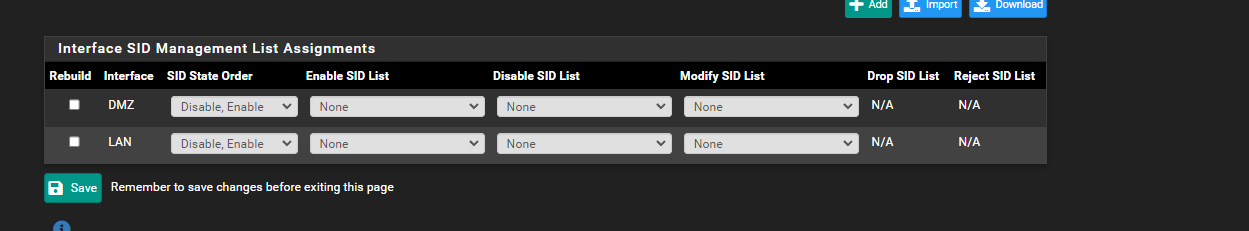
-
@michmoor Hi, Yes I've tried that - adding "IPS Policy - Security" to the dropsid.conf file - but it doesn't work for me (I'd already removed it which is why it's not in the previous screenshot). I have the correct dropsid.conf file enabled in the Modify SID list column. The approach works exactly as expected for all other rulesets except the IPS Policy - Security one.
-
@youngy You are doing something incorrectly. I enabled IPS just to test as i dont normally use it in this matter and it works just fine.
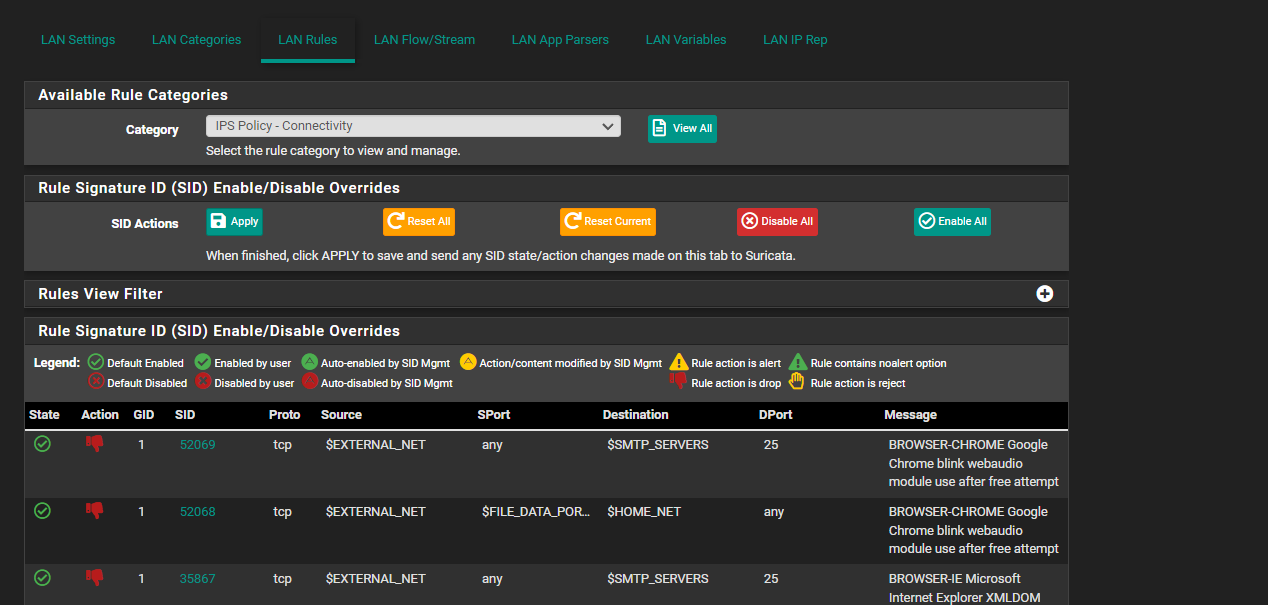
-
@michmoor Okay, thanks. It’s good to see it works for you. As you say I’m doing something wrong somewhere.
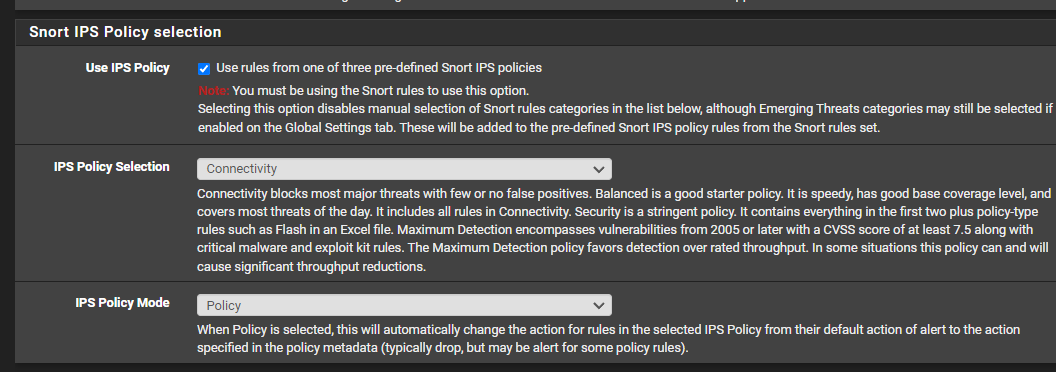
I don’t see the IPS Policy Mode selector in my settings (see the LAN categories screenshot I my first post). Are you using Legacy Mode with Block on Drops selected?
-
@youngy said in Setting drop (block) for Snort IPS policy rules in Suricata with Legacy Mode:
I’m unsure about how the selected Snort rules trigger drops (blocks)
When using Legacy, any alert triggers a block for the configured Remove Blocked Hosts Interval global setting time (15m, an hour, etc.). My understanding is "block on DROP only" basically tries to work around that. Is that your goal, to not block on everything? Otherwise one can just block on alerts, and then ignore/suppress/pass connections that should not be blocked.
-
The "Block on DROPs Only" mode for Suricata is a special option that lets you set the action of some rules to ALERT and that of other rules to DROP. When this mode option is enabled, only rules whose action has been changed to DROP will block an IP. This can be advantageous when compared to the older default Legacy Mode Blocking where any alerting rule results in a block of the IP address unless the IP is on a Pass List.
Suricata and Snort on pfSense both contain a custom output plugin compiled into the binary. This output plugin is called each time a rule alerts. However, the two binary engines differ in how much information they provide to the plugin for an alerting rule. Snort is particularly difficult because unless you tell the binary at startup that it is running in IPS mode, it essentially refuses to honor DROP as a rule action and changes them all to ALERT for you. Suricata does not behave that way. When a rule alerts and the custom output plugin is notified of the rule triggering, the output plugin receives information about the alerting rule including the "action" verb it was set for. Thus the custom plugin in Suricata can look at the alerting rule's action and make the appropriate response. Over on the Snort side, the binary does not work that way, and therefore there is no "Block on DROPs Only" mode in Snort.
-
Dear All,
Many thanks for your input. I’m using Suricata in Legacy Mode with ‘Block on DROP Only’ selected. My query is about dropping (blocking) Snort subscriber rules according to the selected IPS policy. I’m managing the ET Open rules with automatic SID management files (drop, disable, etc), and it’s working well.I’m struggling with the Snort subscriber ruleset. I’ve selected ‘Use IPS Policy’, and ‘IPS Policy Selection’ is set to balanced. I’ve read about, and seen screenshots of, the ‘IPS Policy Mode’ selector (below the above two selections in the GUI), which tells Suricata to drop (block) the Snort IPS policy ruleset based on rule metadata (e.g., policy ips-balanced drop).
The ‘IPS Policy Mode’ selector isn’t available to me (presumably because I’m using Block on Drop in Legacy Mode). I’ve therefore been trying to select the IPS Policy Mode for the Snort rules using the dropsid.conf file by using the ruleset name (IPS Policy – Balanced) or the regex example, and variations of it, from the sample dropsid.conf file. However, neither of those approaches has worked for me.
I can drop (block) the Snort rules (individually or in groups) by including their GID:SID in the dropsid.conf file but would like to tell Suricata to use the Snort rule IPS policy metadata to achieve the same if possible. So far this is what I’ve failed to do.
-
@youngy said in Setting drop (block) for Snort IPS policy rules in Suricata with Legacy Mode:
Dear All,
Many thanks for your input. I’m using Suricata in Legacy Mode with ‘Block on DROP Only’ selected. My query is about dropping (blocking) Snort subscriber rules according to the selected IPS policy. I’m managing the ET Open rules with automatic SID management files (drop, disable, etc), and it’s working well.I’m struggling with the Snort subscriber ruleset. I’ve selected ‘Use IPS Policy’, and ‘IPS Policy Selection’ is set to balanced. I’ve read about, and seen screenshots of, the ‘IPS Policy Mode’ selector (below the above two selections in the GUI), which tells Suricata to drop (block) the Snort IPS policy ruleset based on rule metadata (e.g., policy ips-balanced drop).
The ‘IPS Policy Mode’ selector isn’t available to me (presumably because I’m using Block on Drop in Legacy Mode). I’ve therefore been trying to select the IPS Policy Mode for the Snort rules using the dropsid.conf file by using the ruleset name (IPS Policy – Balanced) or the regex example, and variations of it, from the sample dropsid.conf file. However, neither of those approaches has worked for me.
I can drop (block) the Snort rules (individually or in groups) by including their GID:SID in the dropsid.conf file but would like to tell Suricata to use the Snort rule IPS policy metadata to achieve the same if possible. So far this is what I’ve failed to do.
What you want is not specifically supported. It might work with the proper PCRE, but getting the syntax just right might prove tricky.
IPS Policies are specific to the Snort VRT rules, and the policies are based on metadata embedded within each rule's message body. The SID MGMT logic is not parsing for that information when selecting rules for matching. It looks for GID:SID and category names mostly. But an IPS Policy is not a true category name. Category names are created from the actual filename of the *.rules file containing the rule, and since there is no corresponding *.rules file for an IPS Policy, there is no category name to match.
-
@bmeeks Bill,
Thanks for clearing this up. I'll use the GID:SID of the rules in the policy grouping.
Best wishes,
Dylan -
@youngy said in Setting drop (block) for Snort IPS policy rules in Suricata with Legacy Mode:
@bmeeks Bill,
Thanks for clearing this up. I'll use the GID:SID of the rules in the policy grouping.
Best wishes,
DylanI was just now looking over the PHP code and realized there is a rather simple change I can make to make the IPS Policy Mode feature work with both Inline IPS Mode and "Block on DROPs Only" Mode in Suricata. Currently there is drop-down selector for choosing what action to take for IPS Policy rules that is hidden when not running with Inline IPS Mode. However, I can fairly easily make that selector visible and functional for either Inline IPS Mode or the Block on DROPs Only Mode.
I will put that on my TODO list.
-
 Many thanks for the time and effort you put in to these packages.
Many thanks for the time and effort you put in to these packages. -
@youngy said in Setting drop (block) for Snort IPS policy rules in Suricata with Legacy Mode:
 Many thanks for the time and effort you put in to these packages.
Many thanks for the time and effort you put in to these packages.I have created a Pull Request containing this new feature. It is awaiting review and merge by the Netgate developer team: https://github.com/pfsense/FreeBSD-ports/pull/1212.
This change will initially be only in the new 2.7.0 CE and 23.01 development snapshots, but will go to general release at the same time those new versions do. So far as I know (and I have no inside knowledge), that is scheduled to be this month or perhaps early February for the new pfSense release.

