Devices on VLAN can't access the internet
-
@nilocretep Those switches are a bit odd to configure.
Post pics of the 802.1Q vlan (just the bottom section is fine) and 802.1Q PVID settings pages. -
@jarhead said in Devices on VLAN can't access the internet:
Those switches are a bit odd to configure.
Depending on the model - those switches can just be bad as well, where they do not allow you to remove vlan 1.. There are multiple threads around here and about the net in general about it, there is some firmware posted that can correct it, etc.
If you can not remove vlan 1, you run into the problem where you could have multiple untagged networks - say one of your vlans and vlan 1 untagged etc..
here is an old thread talking about it
https://forum.netgate.com/topic/107152/tp-link-tl-sg108e-vlan-1
-
@heper
Ok, here are some photos of my setup.
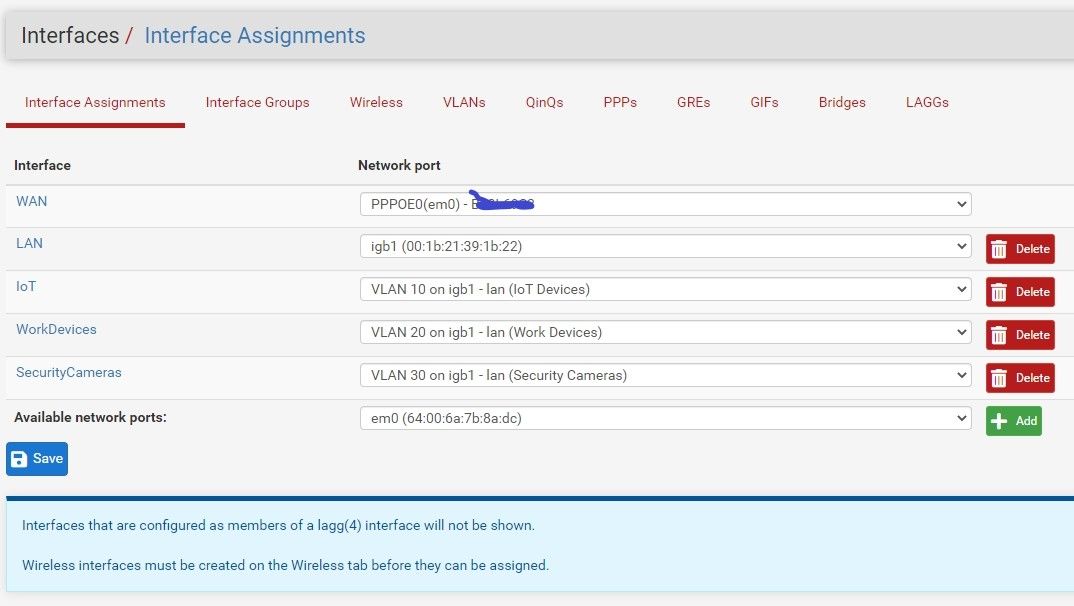
So far in my setup, I'm running ethernet from my Pfsense to my TL-SG1088E on port#1.
Ideally I'd like to pass VLAN10, VLAN20, VLAN30 and LAN to port1
Port 2: Will be going to another Switch that will have LAN and VLAN10 devices
Port 3: Blank
Port 4: LAN only to a Wireless Access Point
Port 5: Blank
Port 6: To Powerline that will have LAN and VLAN10 devices
Port 7: VLAN10 only Wireless Access Point
Port 8: To another Switch that will need VLAN10, VLAN20, VLAN30 and LAN.I'd like to make sure I can get Internet access to Port7 before moving on with anything else. At this point I'm just attempting to get it working with a laptop before I add a Wireless Access Point.
Thanks -
@nilocretep
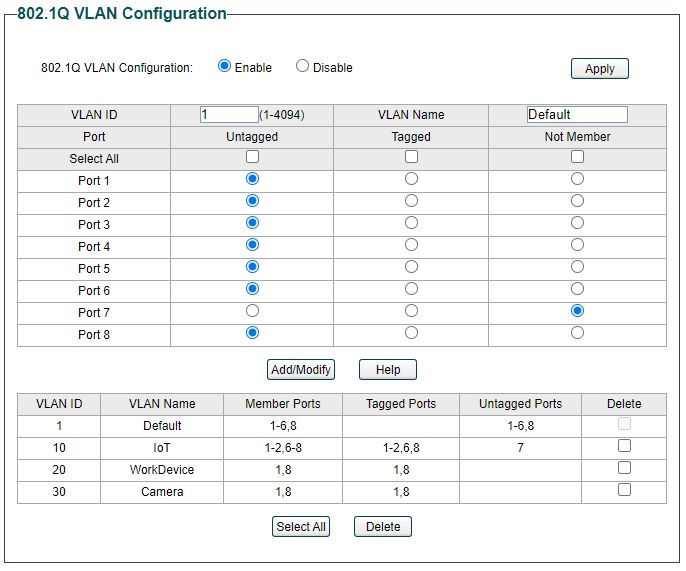
So then port 1 on the switch will be the trunk.
vlan 1 will stay untagged, all others need to be tagged on port 1.Port 2 will be vlan 1 untagged and vlan 10 tagged.
port 4 vlan 1 untagged.
port 6 same as port 2.
port 7 vlan 10 untagged.
port 8 another trunk with same as port 1.
Do that in 802.1q vlan config.
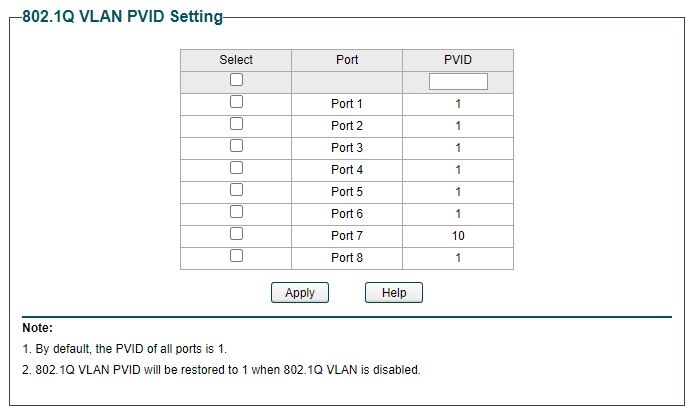
Then in PVID config,
Ports 1, 2, 4, 6 and 8 will be pvid 1.
Port 7 will be pvid 10.You have most of it correct but go over it again and you'll find the errors.
-
@jarhead
So with Port 7....should I leave VLAN 1 as untagged or Not Member? I believe I've tried both settings and had the same results... -
@nilocretep if port 7 is going to be vlan 10 only.. then it vlan 1 should not be a member.
-
Yeah that's what I figured. Even with that setting I still can't get out. I just hooked up a laptop, it gave me an IP of 192.168.179.111.
I can ping 192.168.178.1 (Pfsense router) successfully. Should it be able to do that? Or is because I haven't really implemented any rules for VLAN10?
-
@nilocretep
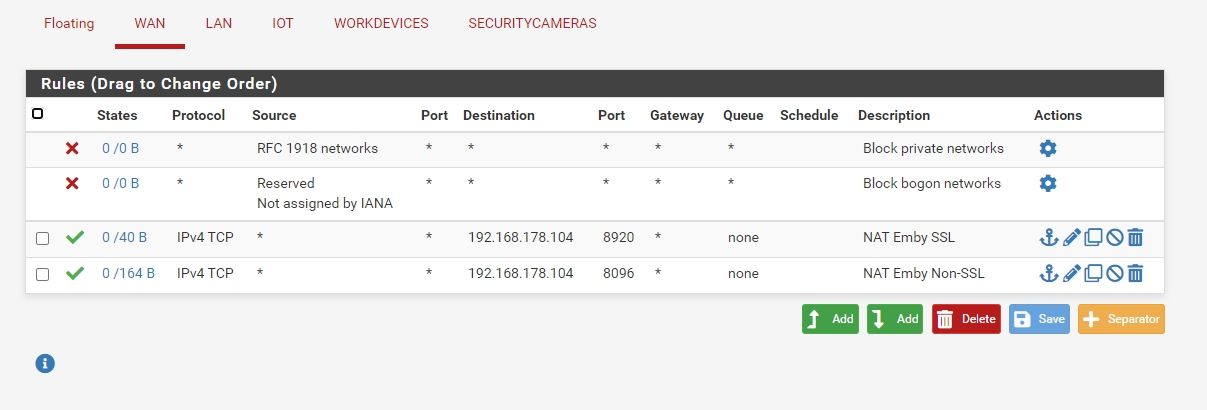
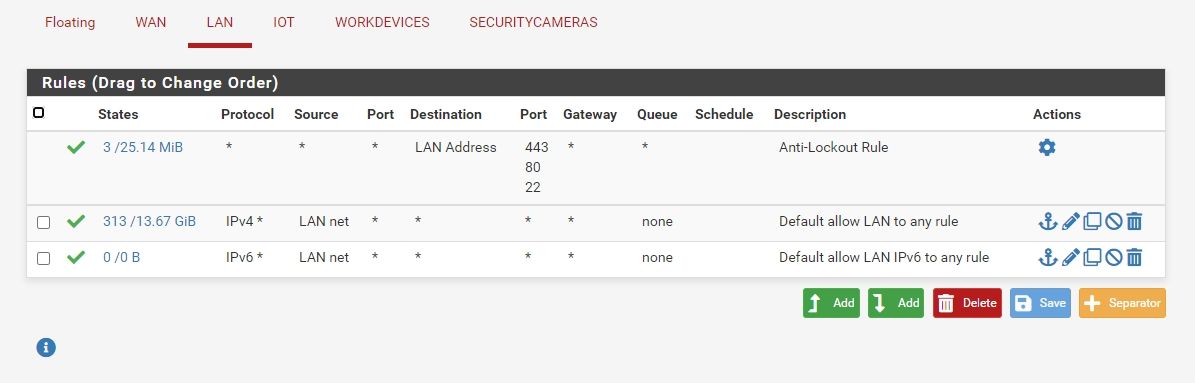
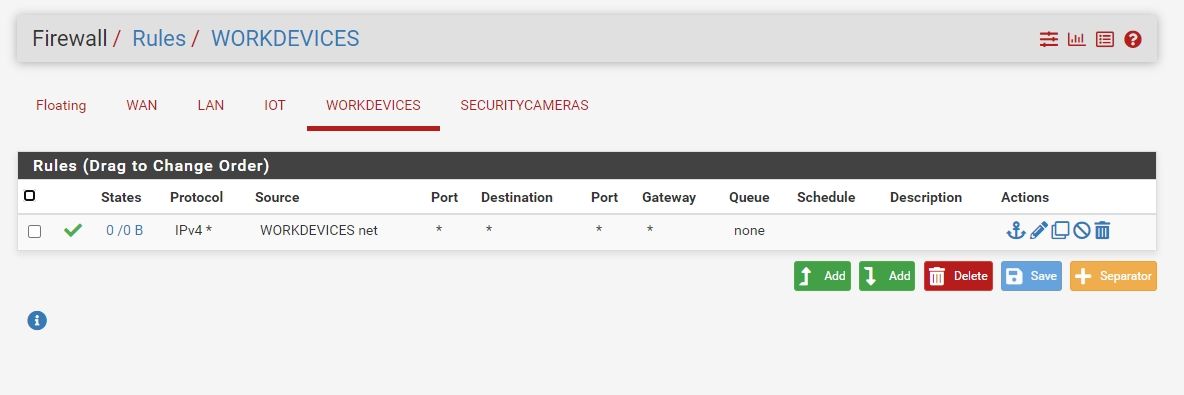
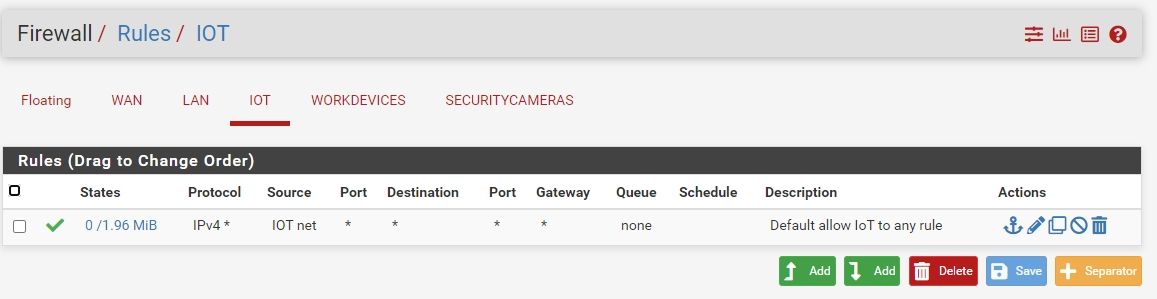
Post pics of your rules on all interfaces.And did you fix the vlans?
Cancel that, looked again, and vlan 1 is 1-6, I thought it was 1 and 6.
Switch looks good. -
@nilocretep said in Devices on VLAN can't access the internet:
Or is because I haven't really implemented any rules for VLAN10?
If you didn't put any rules on your interface - you wouldn't be able to ping. So your either pinging something else on the network with that IP or you have rules that allowing ping on your vlan 10 interface in pfsense.
When you create new interfaces, they don't have any rules - and no traffic would be allowed inbound into the interface..
If you want something on a new vlan your creating to access internet, you would have to allow for that in the rules - you would also need to allow for dns (internet isn't very good without that) and your outbound nat would have to account for this new vlan you created. This is normally done auto, unless you messed with the outbound nat rules and took it off automatic?
Why are you setting a manual IP on this device your using for testing - is dhcp not working. That points to connectivity issue in general if dhcp is enabled on this interface - when you enable dhcp server on an interface, pfsense auto creates rules to allow for dhcp even if you have no other rules on the interface. Your 2 mentioned IPs are different networks - so your using a /23 mask not /24?
Is it possible you setup /24 on pfsense, and your client you setup /23 - this could be a reason why outbound nat or other rules you setup are not working? etc.. There are always lots of pieces to any puzzle.. Without the details - its hard to tell what piece of the puzzle is missing to find the problem.
-
-
@nilocretep
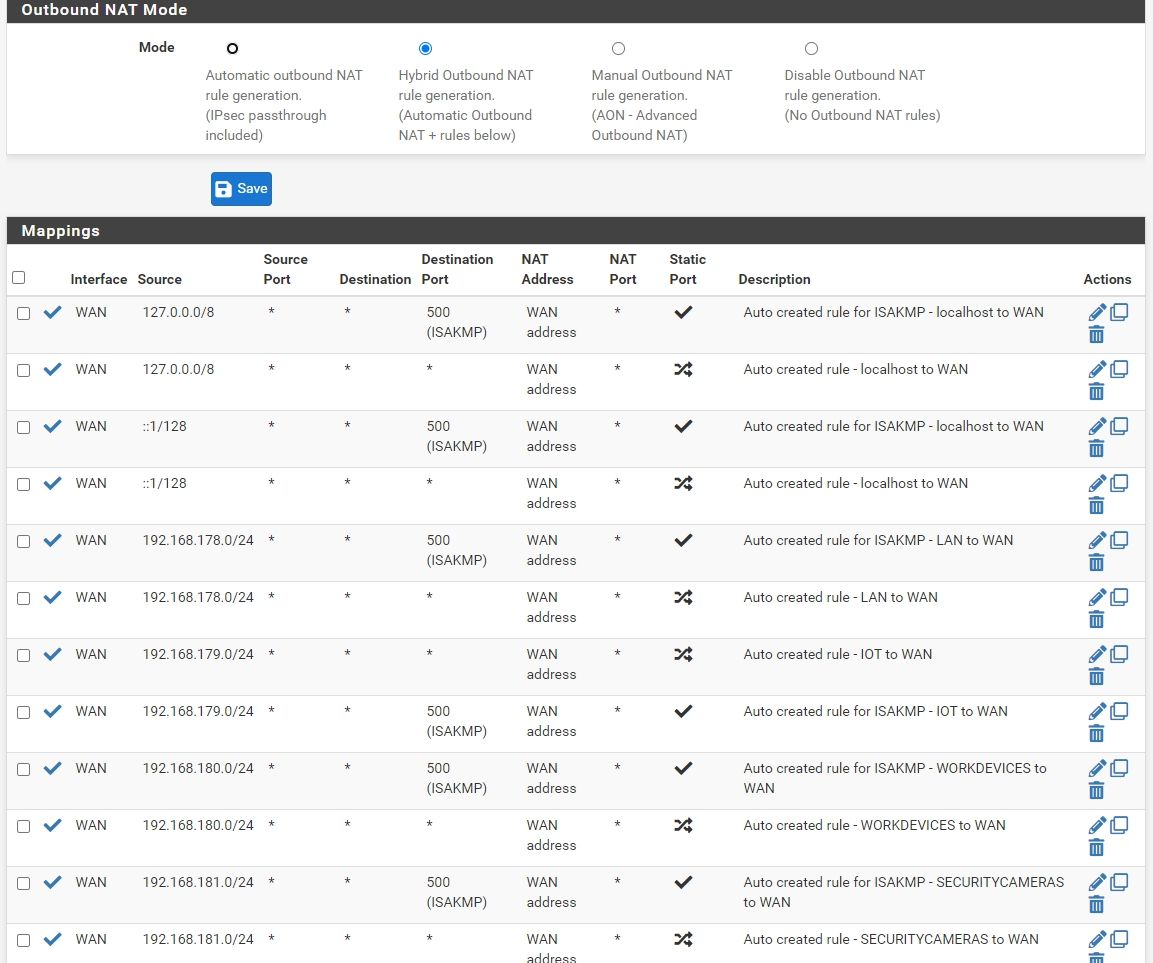
With those rules you would be able to ping the LAN gateway and should also be able to get out to the internet.
Is outbound NAT set to auto?
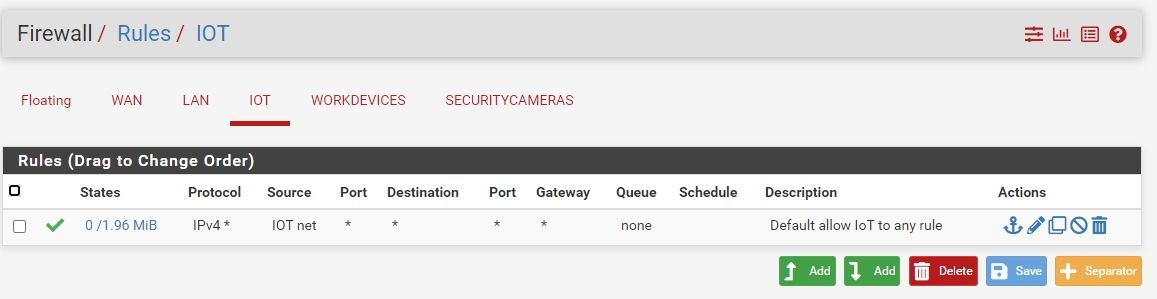
Did the IoT network get added to it? -
@jarhead
I didn't put on a manual IP on the laptop. It was assigned one via dhcp from VLAN10. So at least that portion is working. All interfaces (LAN, VLAN 10, 20, and 30) all have a setup of /24.What configuration would I need to do for DNS?
-
@nilocretep
DNS would already work with those rules.
Just noticed you already posted outbound NAT and it's fine too.Do a packet capture on the WAN and try to get out from the IoT.
Do you see the packets leaving? -
@jarhead
Sorry for my ignorance; but how would I do that?
I can ping 8.8.8.8 successfully from my IoT laptop. If that helps. -
I'm starting to think this might be a part of the problem. I first implemented this when I setup Pfsense: https://arkojoardar.com/adguard-on-pfsense/
-
@nilocretep Yup, I bet you're right.
Disable it and see what happens. -
@jarhead
Yep, that was it.
Thanks for all your help! -
@nilocretep said in Devices on VLAN can't access the internet:
all have a setup of /24.
well why are you pinging 198.168.178.1 from 192.168.179.111 - why would you not ping the IP of pfsense on that interface? but yeah if that was another IP on pfsense rules allow it then sure you could ping it.
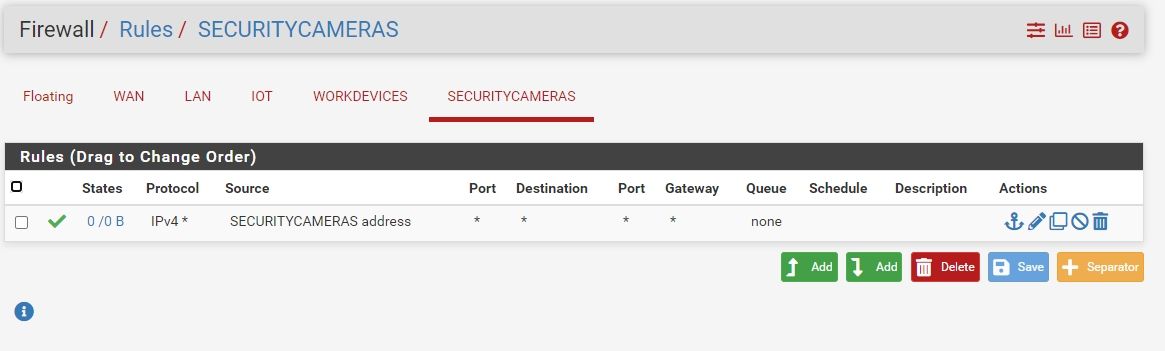
Also you rules for security cameras never going to allow anything - you have the source as the securitycamera address not the net.