PFBlockerNG, Redirecting Client DNS Requests and VLANs not working as it should
-
Hi,
I've setup an pfSense.
Everything fine and running, but I do have an issue concerning my Guest Network not able to Ping and surfing the web.
I think it has something to do with my firewall rules.
I do have a NAT > Port Forward Rule (see screenshot) and do have guests rules (see screenshot).
Whats the problem:
- devices from "Guest Net" cannot ping or reach anything and I don't know why.
- devices from "Lan Net" can ping - without any issues
Did I do something wrong?
Are these the wrong rules?FYI: pfblockerng is set to python mode.
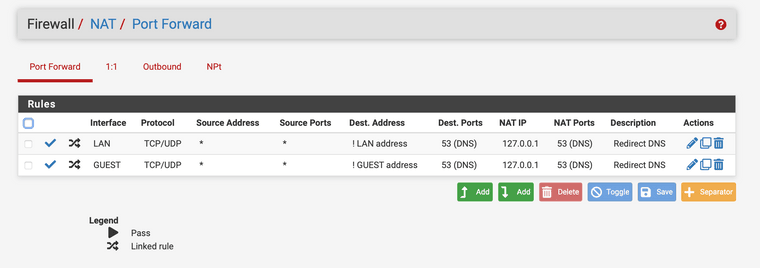
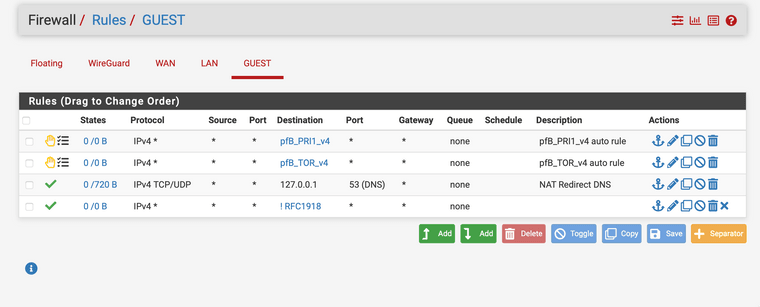
EDIT:
And this is the Lan Rules. Where everything is working fine. Looking nearly the same like Guest rules.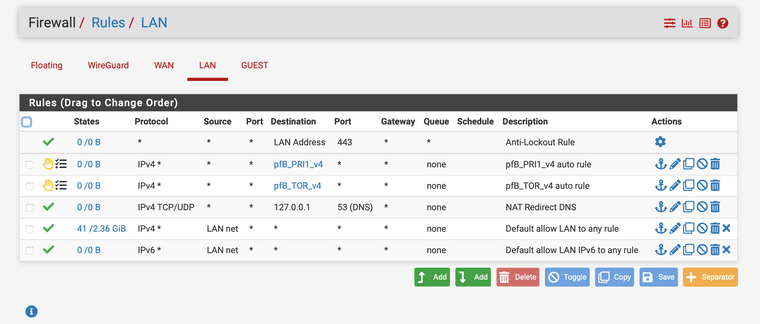
-
@thundergate
The rules look fine so far.Are the guest clients able to resolve host names?
Try a ping to 8.8.8.8.
What's in the state table for the guest network?
-
@viragomann Thx for your feedback.
Ping to 8.8.8.8 and every other IP or domain-name will bring a timeout.
I think I found the issue. When I change the Guest Network the 'Destination' from !RFC1918 to !PrivateNetworks it works without any issues.
But I don't know if that's the right way.
-
@thundergate said in PFBlockerNG, Redirecting Client DNS Requests and VLANs not working as it should:
When I change the Guest Network the 'Destination' from !RFC1918 to !PrivateNetworks it works without any issues.
So what's behind the RFC1918 alias? Normally it should include private network ranges only.
-
10.0.0.0/8
172.16.0.0/12
192.168.0.0/16 -
@thundergate
So the pass rule on the guest interface should allow ping to 8.8.8.8.
That makes no sense to me. -
@viragomann What I found out is, when I use the invert rule with RFC1918 it cannot ping to it's own subnet-gateway and/or unbound in same way.
If I change it Private Networks (does not include the Guest-Subnet) then it works.
Looks like !RFC1918 is blocking internal resolution to unbound.
-
@thundergate Just found out, that ping does work with this rule. But host resolution is not working.
EDIT: Did a restart and now as said the ping to several domains does work (via IP), but not via Hostname
-
@thundergate
We get a bit closer.Could be, that your devices are requesting the guest IP. This is not redirected by the NAT rule and there is no firewall allowing this access.
Best the set the destination in the pass DNS rule to "This firewall". -
@viragomann Understood.
But I cannot change the rule that easy, as it's actually my NAT Port Forward Rule for DNS
(https://docs.netgate.com/pfsense/en/latest/recipes/dns-redirect.html)I took this rule, so that every device cannot use hardcoded DNS.
Thought the rule from Netgate is the right one to choose?
-
@thundergate
The document doesn't concern the filter rule association. You can let the NAT create an unassociated filter rule, so you can edit it. -
Before I do mess it up now I will write down what I wanted to achieve.
- running pfblockerng in python mode with unbound
- having two networks (LAN, Guest)
- want, that both networks use pfblockerng and unbound
- Guest is not allowed to enter LAN network
- no one is allowed to use hardcoded DNS > they must use my unbound (pfblockerng system)
That's what I want.
So I took the rule from netgate and also made the other small !RFC1918 rule
At the moment I cannot understand, why the Netgate Rule as described doesn't work within that conditions.
And sorry for asking as I'm quite new into pfSense and still have a lot to lern.
So what would be the best way to achieve my goal?
-
@thundergate
I understand, what you're trying to achieve.So I took the rule from netgate and also made the other small !RFC1918 rule
I don't know, where you've got this from. But if it's from Netgate I assume, that there is also a hint to add additional pass rules for services running on pfSense itself.
The RFC1918 alias is a good way to only cover private or public ranges. But as used in your pass rule on guest, it does not cover access to pfSense services like DNS.
You need a rule to allow this explicitly, expect DHCP, which is implicitly allowed if the DHCP server is enabled on the interface.So either change the filter rule association in the NAT rule as mentioned above or add an additional pass rule to allow DNS requests to pfSense (predefined "This firewall" alias). "This firewall" covers any pfSense IP, including loopback.
-
@viragomann Thx for your help.
I have to think about which would be the best way now. As it's a testing setup I have no problem starting everything over again.