connect subnets
-
Hi, I need to allow connection between 2 subnets, the subnet 192.168.10.0/24 must authenticate to the authentication portal on the network 192.168.20.1/24
-
@cobain
So simply allow it by a firewall rule.
We sadly don't know, what protocol and port your "authentication portal" is using. So we cannot tell you the details.Also ensure that the destination device is accepting access from the other subnet.
-
Thank you
The authentication portal uses port 8088.
Could you give me more details, an example of how to declare the rule. -
@cobain on OPT1 interface, allow from “OPT1 Network” to 192.168.20.5 port 8088. Or whatever the IP is.
-
I'm sorry, but it doesn't work, I share an image of the rules that I defined. am i doing something wrong?
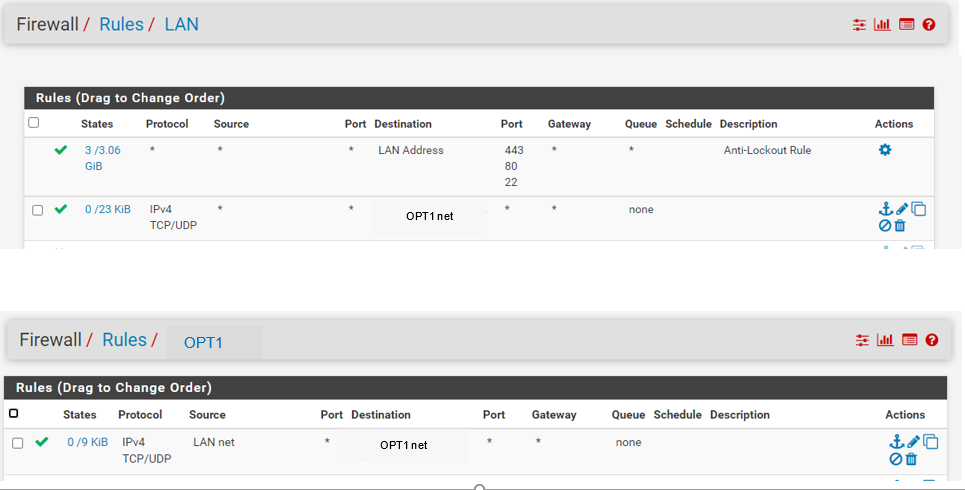
-
@cobain LAN cannot be a source on the OPT interface.
Reverse source and destination. -
@jarhead well clearly it can be ;) see that rule it has some evaluations the 0 / 9KB
Someone doesn't have actual isolation of their networks would be my guess ;)
-
@johnpoz Hello, could you explain to me what you mean?
-
Hi, Is it possible to connect?
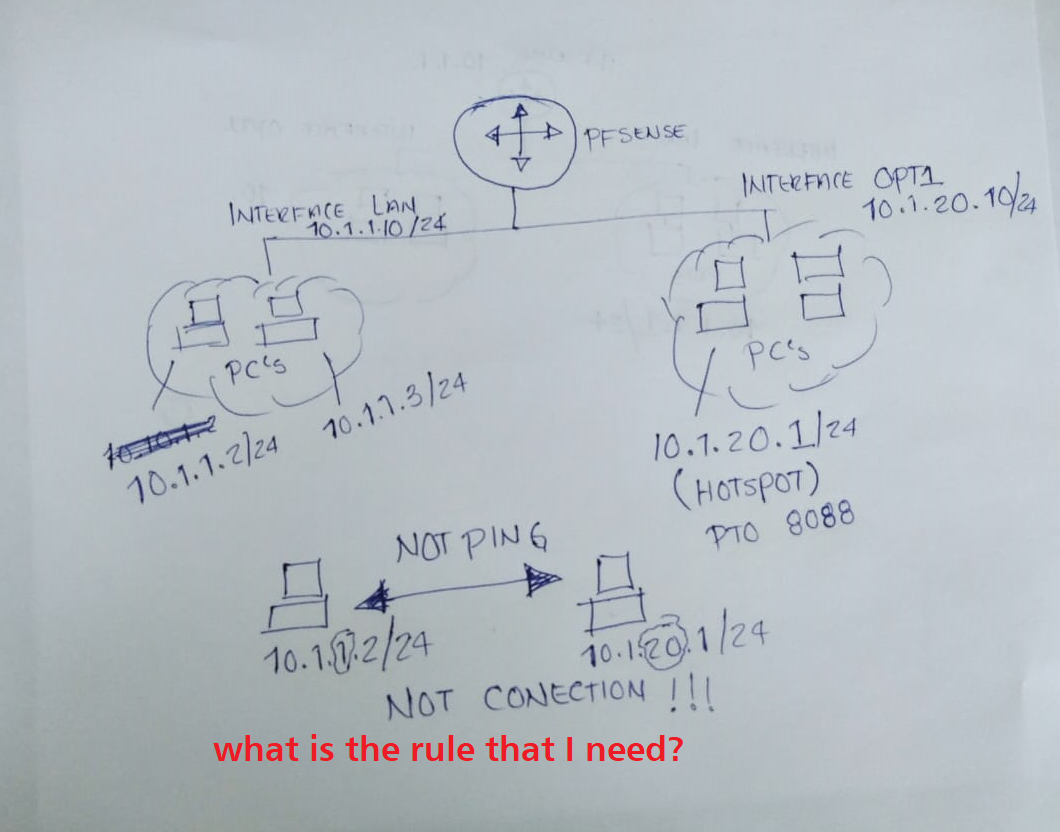
-
@cobain Just reverse the source and destination on the OPT rule above.
The LAN can never be a source on any other interface so you have them backwards. The fact that that rule shows 0/9 means there was some traffic on it. You probably have your switch set wrong as the two subnets seem to be bleeding over. -
@cobain in a correctly normal isolated networks, it would not be possible for anything other than that network to be source of traffic.
There is no possible scenario where this rule should see traffic
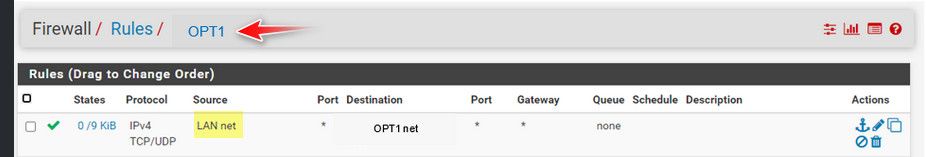
But as you can see this rule has seen some hits the 0/9 KB under states.. How would your 10.1.20 interface on pfsense see traffic from 10.1.1 into it?
The only way that could happen is if your networks are not actually isolated from each other.
The source on opt1 would be opt1 network, not lan net.. Looks like you pasted that opt1 in to the headings?
edit: the only time you would see non interface network traffic into an interface, is that interface was being used as a transit network. But lan net would never be into opt1 as a transit...
-
@jarhead Thanks, for the help, I already made the adjustments in the interfaces, but sadly I can't get there to be communication between those 2 subnets.
Do you have any other suggestions that could help me? -
@johnpoz Thanks, for the help, I already made the adjustments in the interfaces, but sadly I can't get there to be communication between those 2 subnets.
Do you have any other suggestions that could help me? -
@cobain Well, if you did that correct it would work so you would have to provide pics of the config on the pfsense and switch.
You obviously have something misconfig'd. -
@cobain what are you rules.. please post up what you currently have set for lan and opt1
If they are really any any rules, and you don't have any floating rules that would block. And your not policy routing traffic out some gateway, like your wan or some vpn then issue with clients not being able to talk is either they are not actually using pfsense as their gateway. The clients have the wrong mask on them, seen this quite a bit actually.. Where users set static IP on a client and use say a /16 mask.. So it thinks the other network/vlan is just local and never sends traffic to its gateway to get to the other network, or to answer traffic.
Client firewalls is always big overlook by users..
Wrong protocols for example - your rule there were lan was source to opt1 on opt1 interface was only tcp/udp - so no pinging even if the rule was correct wouldn't work..
you can always sniff (packet capture on pfsense) to validate traffic is actually getting sent to pfsense on your lan for example, and then sniff on your opt1 interface to see that traffic is being sent on to your destination IP..