Prevent log of port 10001 in firewall log
-
Hi,
I have purchased a UniFi USW-Lite 8 port switch and am was looking forward to getting a good switch. As such, it also works fine, but I am being driven to the brink of all the Ubiquiti Device Discovery Service records that keep coming up in my PfSens log file. (port 10001)
For the ports I do not want to see in the log file, as can be seen in the attached photo, I have created reject rules that stop it before they reach Block All Outbound Not Permitted Previously, which logs everything.
I have tried in vain to make similar rules for port 10001, the ip address it comes from, both IPV4 and IPV6 regardless All IPV6 is total disconnected in my 4100 device, but nothing helps, they still appear continuously in the log file.
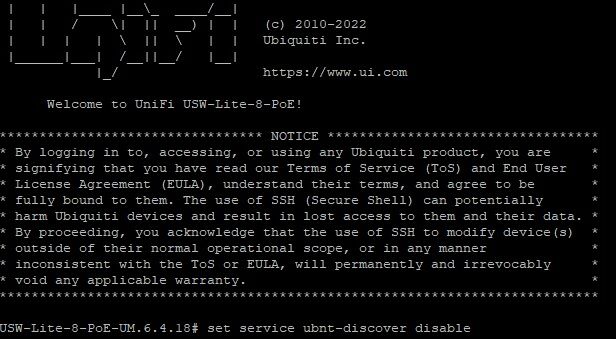
I have tried to log in to the UniFi USW-Lite 8 with putty, and close discovery, as shown in the photo, since it is the only ubnt device I have, it does not work either.Is there anyone here who can help
;o)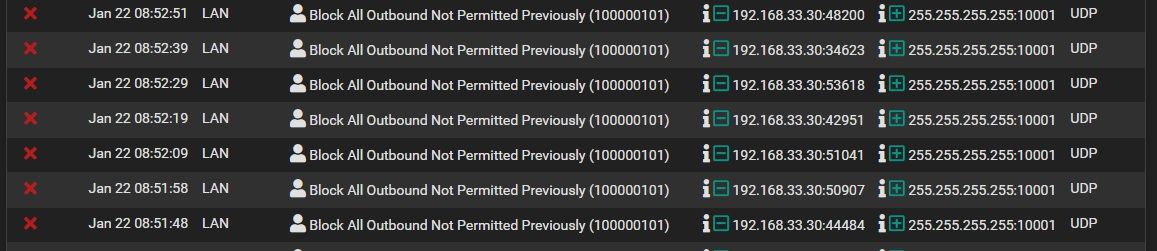

-
@felix-4 create a block rule, set it to don’t log and place it above your pass rule.
-
-
@felix-4 Try killing the firewall states
-
@nogbadthebad
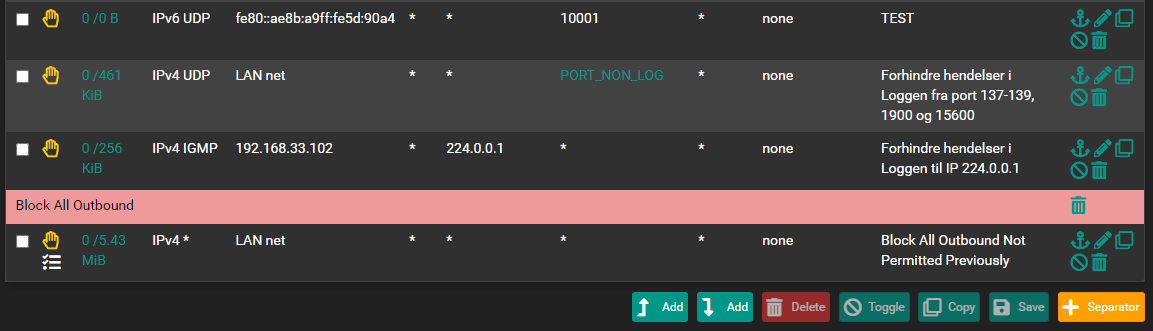
You can see the rule I've made in one of the photos I've attached, it's the one for IPV6, it should be ok, a similar one for IPv4 is also created, it didn't show up in my photo.
During my tests, I have backed them up at the top, without effect.There are no stats from switch ip. I've tried rebooting PfSense after doing what you suggest, again to no avail. The firewall log is jammed with info about port 10001.
-
@felix-4 You could try changing the global setting Status -> System Logs -> Settings -> Log firewall default blocks.
-
I have disconnected a 4 - 5 sites that deal with IPV6, so all sites that deal with it are disconnected.
I have tested unchecking Log Packets from Default Block Rules and it works. However, it apparently works too well, because the information and attacks on my WAN ip also disappear.
It's a solution, but I'm puzzled by the discovery from ubnt, why can't it be blocked from the log, in a similar way as port 137-139 and similar.
After I disconnect what you suggest my log does not update with WAN info. Then again, you could make a log rule about logging, but that is a major circumvention. -
Your solution has if I configure what to log is a workaround. I would really like to know why you can't use the normal solution. The one you mentioned in the first place, and which I have also used until now, if there were irrelevant things in the log that needed to be removed from occurring.
What makes that switch so difficult to handle. -
Nogbadthebad, thanks for your help today, it has provided a temporary solution to the problem. I am very happy for your help.
If someone comes across this thread who can see why normal rules for eliminating events in the firewall log do not work in this case, you are very welcome to write.
I'm not the kind of person who lets me put up with the fact, that now it's resolved, and I don't think about it anymore. I would like to get to the bottom of it, and know, what is at the root of the challenges in this case.;o)
-
@felix-4 well block all Ipv6 is a rule that is hidden and evaluated early - which would explain why that is showing up.
That first rule doesn't show it was ever evaluated, see the 0/0 B on it - means nothing ever matched it.
I would just turn off the block all IPv6 to be honest, if your not running IPv6 and have no rules to allow it - its just going to create noise in your logs.
I don't see anything in those rules that would prevent the noise you posted. The block all IPv6 is early, which explains why your rule shows no evaluations.
I don't see any rule that would block but not log that traffic to broadcast 10001, your 2nd rules description doesn't list 10001 port.
-
Thanks for reply,
If you do not see a rule that prevents the "noise" that comes in the log as shown, both from and to an IPV6 address, and from and to an IPV4 address, then can you enrich with a proposal for a solution to the problem.
What would you suggest as a rule, to prevent that noise?;o)
-
@felix-4 as I already said turn off the block all IPv6
Check this box
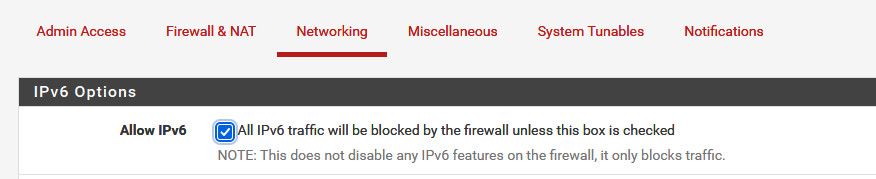
As to that 10001, port you need a rule that would match that.. You don't have such a rule, your 1st rule is a ipv6 source, which that is not, and your ipv6 block, blocks it before that rule is even evaluated anyway. your 2nd rule - add the 10001 port to your alias..
-
@johnpoz
Many thanks johnpoz, now I have closed the ubnt spam in my log file.
I have been incredibly careful to disable all IPV6 everywhere in PfSense. This is because I don't know enough about it to take care of those setups. And handling IPV6 in general.
Is there anything security-wise I should be aware of now that I have allowed IPV6 based on your recommendation.
Otherwise, I'd rather buy another switch that doesn't cause those problems. -
@felix-4 said in Prevent log of port 10001 in firewall log:
I'd rather buy another switch that doesn't cause those problems.
And why do you think a switch is causing this? None of your logging had anything to do with any switch.
Do you have any rules that allow IPv6? If not then its blocked. Did you setup IPv6 on your wan? Set it to none, did you setup IPv6 on your lan via track on your wan? Set it to none..
-
It started when I installed my new switch as described. It constantly broadcasts discovery on port 10001, and apparently it cannot be disabled on the model I have.
https://help.ui.com/hc/en-us/articles/204976244-EdgeRouter-Ubiquiti-Device-Discovery
-
@felix-4 Edge router - is not a "switch"
Broadcasting discovery has little to do with pfsense logging.. Yeah lots of stuff send out noise.. you should see the noise all my smart lightbulbs send out.. Its multicast so I block it at the switch, but also I don't log it..
That article you linked to directly says how to disable it ;) on the Edge router..
You prob want to turn this off in your controller, scan from devices..
https://community.ui.com/questions/Edgeswitchs-24-Lite-network-discovery-options-activate-on-their-own-after-deactivating-them/386aedf5-ad38-40d3-8470-db9d2a71ed21?page=1
-
@johnpoz
Yes, my switch is not the type mentioned, it was more to show the problem. I have found several links like the one you found, and as you can see from my photo, I log into the switch directly, it seems to receive the command to disable discovery, it just doesn't work. I have examined all the settings in the UniFi NetWork Application that manages the switch, but have not found anything useful.
That's why I have to sweep it in PfSen's log, it's usually not a problem, but just in this case.
Noise must be removed so that relevant information relating to safety can be easily observed. -
@felix-4 I concur its better to remove the noise from the network if possible.. But not logging it is simple as well..