I'm sick of neer-do-wells hitting my WAN with TCP:SYN
-
@johnpoz
First, I have no ports open as of now. When I need do do that, I can make appropriate exception rules.As for why, my purpose is not to make internet noise visible. Rather, it is to discover who out there is interested in my firewall and potentially my devices behind it.
Here's my rationale: There are 65K /16 subnets out there, each of which may contain one or more entities who have entirely different motives than me for being connected to the internet, and undoubtedly some of those are malicious. Let's just say that of those 65K subnets, one percent of them contain one or more malicious actors. That means I only have to block ALL communication with 655 of the subnets.
They get a black mark by TCP:SYN'ing me and by denying them any form of communication, I would make it impossible for them to receive anything at all from my protected LAN.
I agree that this is far from being a complete solution, but don't you think that it has the potential of eliminating a useful number of threats?
-
@henderbc said in I'm sick of neer-do-wells hitting my WAN with TCP:SYN:
First, I have no ports open as of now.
Then what do you think this accomplishes.. Other than extra work for you to do that does nothing. The default is deny, creating another deny does nothing..
If you don't want to see the noise then turn of logging of default.
You understand out of the box some box sending you a syn or ping or whatever gets ZERO back, the traffic is just dropped.. You're not accomplishing anything creating another block..
Such rules only make sense when you have port forwards and want to limit who can actually talk to your port forwards..
-
I honestly do not understand the rationale here. It’s nonsensical.
I’m not trying to be mean but seriously I don’t get it. I read your post 3 times. I’m thinking maybe there’s some high level plan here that I’m missing. It happens I’m human.
But at that end of the day you have no open ports to the internet. Absolutely no way an inbound session can be initiated to you at all. You want to create blocklists for already blocked IPs to do what exactly?One more edit:
Then you want to create a block rule to block nets on boundaries such as /16. That’s insane as the internet doesn’t work that way. And do this because an IP is sending a SYN?!? -
@michmoor said in I'm sick of neer-do-wells hitting my WAN with TCP:SYN:
lock rule to block nets on boundaries such as /16.
Yeah that is going to block a lot of stuff, other companies, etc. I would see doing huge large nets preventing access to you port forwards. But if you block that outbound, you most likely end up breaking big chunks of the net..
But as you already said you don't have any port forwards..
-
@johnpoz I guess I've done a poor job of explaining my plan. Perhaps an analogy would help.
There are several shopping malls in the town where I live. As it turns out, one of them has, upon occasion had muggings take place in the parking lot. It seems logical to me to simply choose to shop elsewhere because I can. The store owners were not responsible, nor were the thousands of other shoppers who regularly go there. I don't really care about the details of the last mugging that occurred. I just draw conclusions about that place that make me want to avoid it.
Similarly, my firewall plan has nothing directly to do with somebody on some subnet sending me a TCP:SYN packet. I am well aware that my firewall will simply ignore that packet. However, the fact that somebody decided to not mind their own business and reach out to my unique WAN port (repeatedly in many cases) is evidence that, for whatever reason, makes me prefer to get my information elsewhere. In other words, if someone on some subnet touches my box, I will block that subnet going forward, not just from unsolicited traffic on the WAN side, but also potential threats coming from inside my network in the future.
I am essentially trying to build a crime map of the internet much the way some web sites build a crime map of big cities in the US, coloring whole city blocks 'red' - not because all the people in that block are criminals, but rather because it only makes sense to choose to spend my time in 'green' areas.
At the moment, this is just an hypothesis for me. It may well turn out that I have to block the entire internet.
But maybe only 1% of it.
-
@henderbc said in I'm sick of neer-do-wells hitting my WAN with TCP:SYN:
I have a plan I would appreciate comments on
I suggest starting with pfblockerNG-develop and use the feeds to block known bad players and VPN.
Then see what is left.That should explicitly block most scanners. Then when you want to open a port you know most bad players will not see you.
-
@patch Well your going to not have much of the internet to use then..
Like saying oh, there was a mugging in Chicago - not going to go to US ever..
There are many CDNs where boxes are run, where 1 bad user now blocks you from all good stuff on their whole network. So you get a one bad stray syn from say AWS, and your not going to go to any AWS ip.. Welcome to non functioning internet.
Some of that traffic is orgs trying to map how open the internet is.. Run on legit CDNs that house lots of other stuff..
-
@johnpoz
I find a selection of the feeds in pfBlocker relatively specific for my use case. Sad to hear your find them less useful. -
@patch I didn't say that - those are rules that can be very specific for someone wanting to do what he is doing. What I am saying finding an IP and then blocking the /16 that IP come is going to be problematic at best if you actually want to use the internet.
There are maintained lists already, say for example the shodan scanner
https://wiki.ipfire.org/configuration/firewall/blockshodan
And sure the lists in pfblocker - no reason to try and reinvent the wheel here.
Blocking based on AS vs a arbitrarily random cidr of /16 would be a better option..
-
@johnpoz Indeed:-
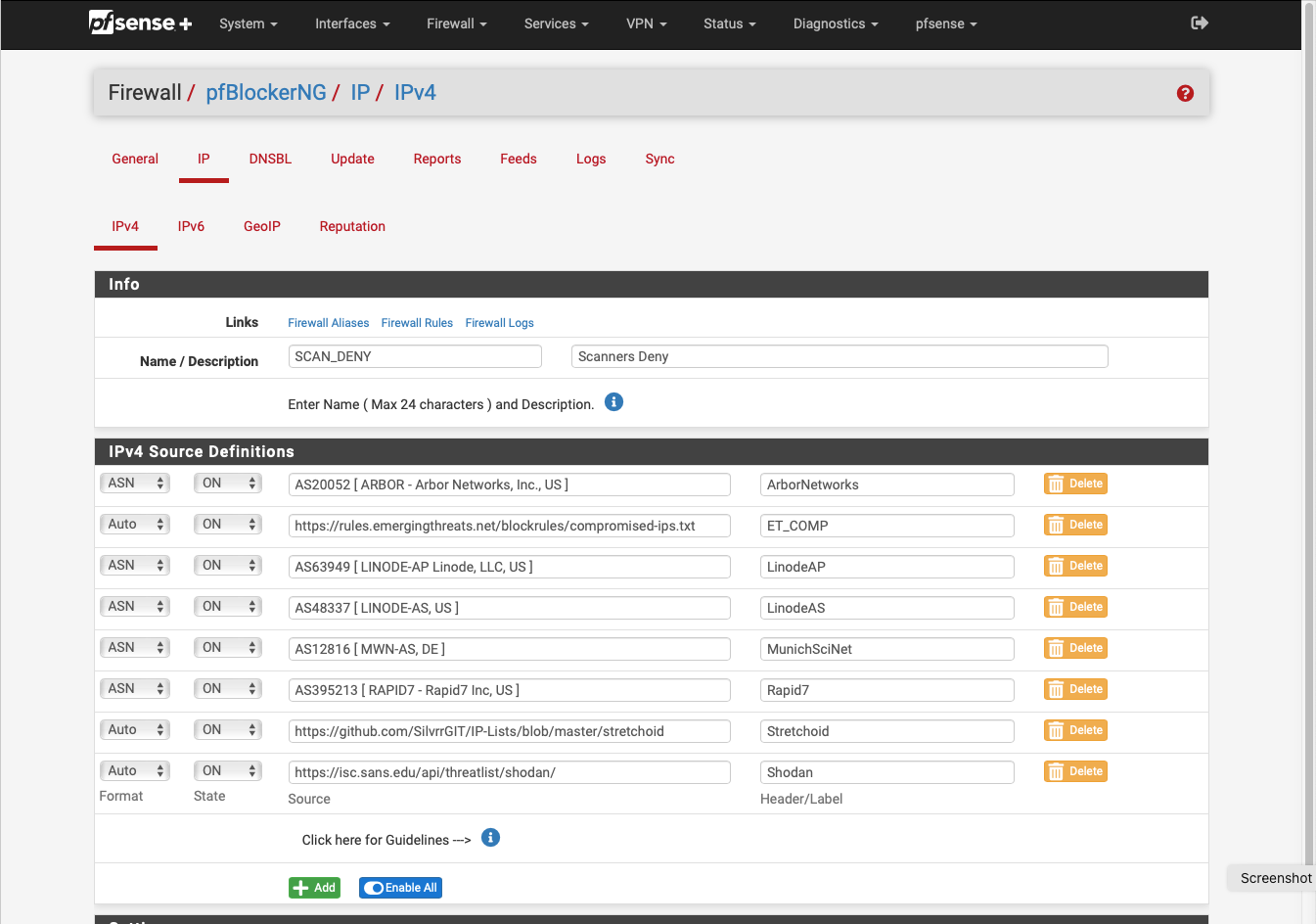
-
@johnpoz OK - I'm convinced. My plan is going to take a lot of work without much payoff.
As you might have guessed by now, I'm pretty much a pfSense NOOB and
I appreciate all of your insights and expertise.It looks like I'll be investing some work in pfBlocker. Can anyone suggest the best (simplest) step-by-step guide to getting a basic pfBlocker setup started?
-
@henderbc Use pfBlocker like my example to create aliases and then use those on the WAN interface.
There is a wizard to do the basic install, you'll also need to sign up for a MaxMind license key if you want to use their GeoIP data.
Install the pfBlockerNG-devel version.
https://www.youtube.com/watch?v=xizAeAqYde4
https://www.youtube.com/watch?v=oNo77CMoxUM
-
@nogbadthebad Here's what running the wizard gave me:
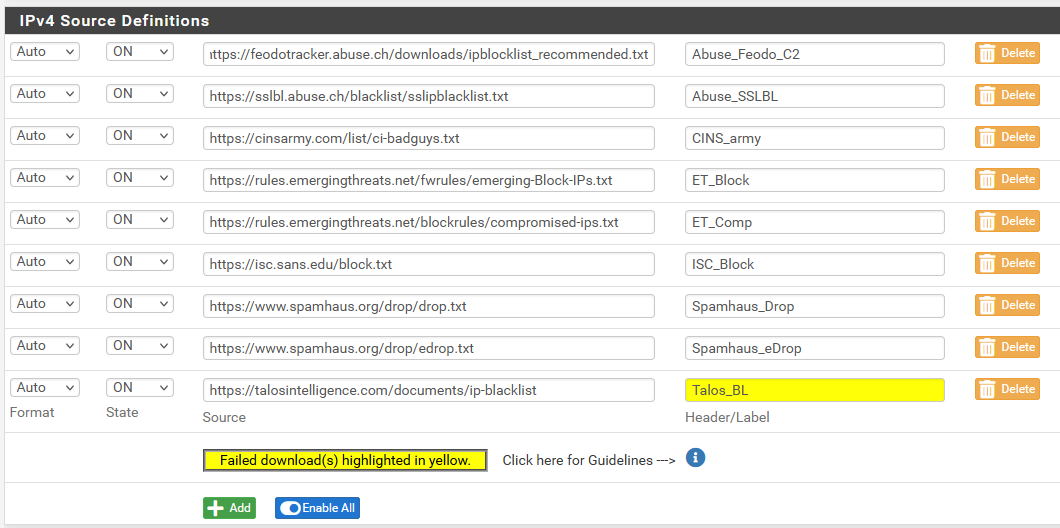
Would you recommend I use your entries instead of these or as well as?
-
@henderbc I don't seem to have any problem downloading that talos list
https://www.talosintelligence.com/documents/ip-blacklist
Can you open that link in a browser? It redirects to different location, but can get a list of IPs in my browser - does that work for you?
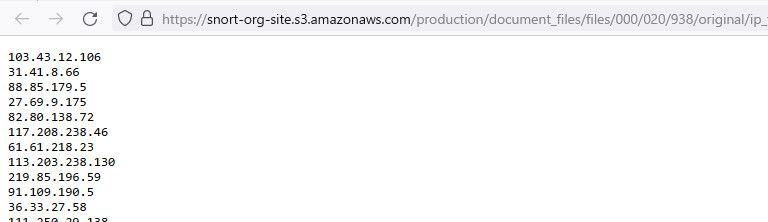
-
@henderbc It's up to you to be honest, I wanted to create my own list rather than the standard one.
I just started looking at what was hitting my WAN interface and built up a list of what was doing a port scan on my WAN.
It started from the shodan list and sort of expanded.
-
@nogbadthebad ^ exactly what I would suggest, what you want to block would be up to you.. But again keep in mind if you have zero ports opens its all pretty pointless other say not logging this traffic to keep your firewall log smaller?
If your phone ringer is off, does it really matter if a spammer calls you - you don't answer the phone anyway because the phone doesn't ring.. But you might not like picking up your phone and see missed calls.
So if you don't want to log these scanners that valid, but if your still going to log them, and you don't have any ports open anyway.. Not sure what the point is? Other than say info on how much traffic is coming from these known scanners. Another big scanner is recyber.net but atleast they have an optout where you can put in your IP and they are suppose to exclude your IP from their scanning.
-
@johnpoz said in I'm sick of neer-do-wells hitting my WAN with TCP:SYN:
If your phone ringer is off, does it really matter if a spammer calls you - you don't answer the phone anyway because the phone doesn't ring.. But you might not like picking up your phone and see missed calls.
My ringer is on as I have an IPSec VPN & SFTP server local
