trafic sortant par vpn, si vpn KO bloquer le trafic
-
Hello,
I have a problem with outbound traffic only over VPN.The default gateway (without vpn): WANGW
The gateway with the VPN: INT_VPN_OUT_VPNV4My firewall rules:
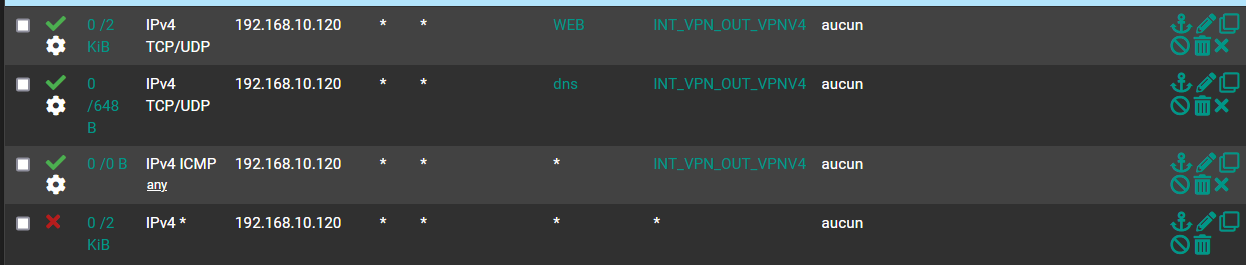
Line 1 I say all web traffic goes through "INT_VPN_OUT_VPNV4"
Line 2 I say all DNS traffic goes through "INT_VPN_OUT_VPNV4"
Line 3 I say all ICMP traffic goes through "INT_VPN_OUT_VPNV4"
Line 4 I say all remaining traffic is blocked.If I say allowed traffic must pass through a defined gateway. Why if the VPN gateway drops all traffic goes through the default gateway.
Thank you for your lights.
-
Your question is not that clear to me but, even when you use a VPN connection, all traffic will pass first through the default gateway the difference is that the traffic it is now encrypted on the wire.
A VPN connection does not magically make your outgoing traffic magically ignore your default gateway to your VPN endpoint or gateway.
Outgoing traffic will always go through your default gateway unless you create a different route, in which case, your
INT_VPN_OUT_VPNV4must be your default gateway for that route and the interface's IP should be reachable within the same network.Firewall rules won't change packets route, you should use
System>Routingfor that.Not sure what you are trying to accomplish, so please can you explain with more details.
Merci
-
The default gateway is WANGW because it is the direct gateway used by other devices.
I have an IP address "192.168.10.120" which must go through the VPN, and in the case where the VPN and down in no case the traffic must go directly through the gateway without VPN (WANGW).
Currently when the VPN gateway is working, the WEB and DNS flow is routed through the VPN gateway.
I just have to fix the problem of when the VPN drops.
Here is my setup:
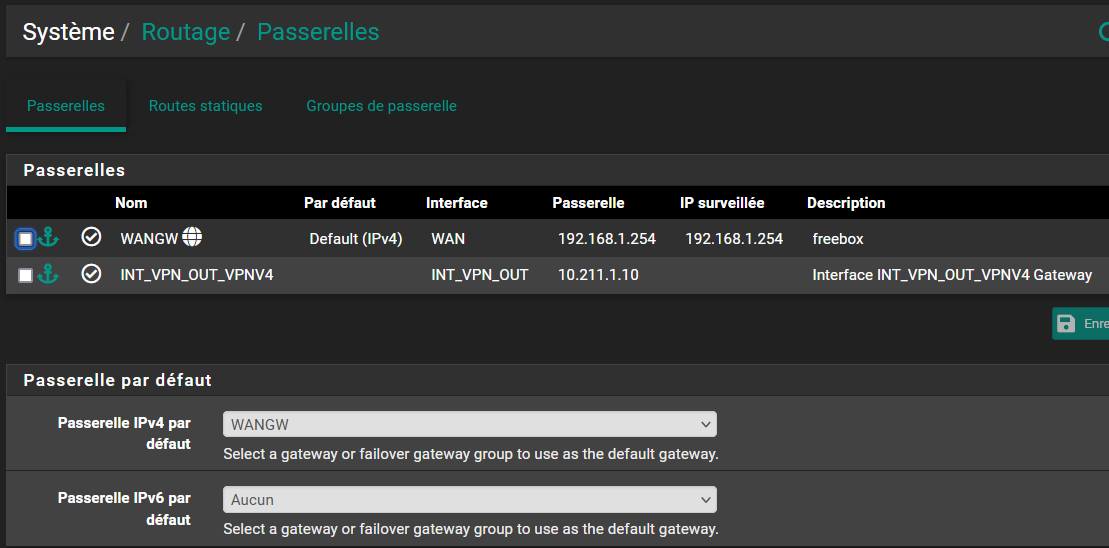
If I change the default gateway to "none" the VPN daemon no longer connects.
I'm just trying to do a "kill switch". -
Ok I found the solution by using "tag" and tagged" to do KILL switch with the rules.
Thanks -
Ok I found the solution by using "tag" and tagged" to do KILL switch with the rules.
There is an option for "kill switch" in
Routing>Gateways>Edit: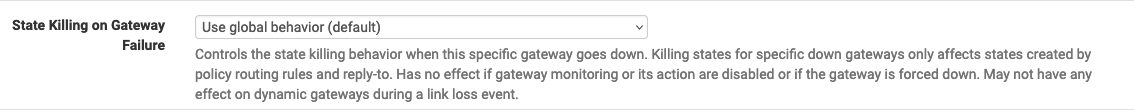
This is perhaps what you want, I didn't see any "tag" or "tagged" options with the rules.
Either way, happy to help!