radius and wpa3 with client wpa2 ?
-
Hi,
have tried googling but not found the answers I need. I am setting up, or more accurately, refreshing my wpa2 enterprise setup of radius/eap-ttls/mschapv2 to use wpa3 instead.I have on the unifi side set up a new wifi using wpa3. When trying to connect I can see the network in the list, but am not able to connect to it, no error I can find. As my client is wpa2, will wpa3 be backwards compatible - thus, should this setup be possible to get working? But maybe more important, will I get any benefits of wpa3 when only using a wpa2 capable client?
As far as I have been able to read, it should be backwards compatible, but still refuses to connect - even with minimal changes (apart from wpa2 -> wpa3 then)... Logs on pfSense are clean, freeRadius starts as it should and awaits connections... How can I better test this?
Thanks -
@furom From the pfsense CLI run radsniff -x you may see something.
FWIW I had to untick WPA2 + WPA3 Personal on my Aruba InstantON AP22.
-
@nogbadthebad Thanks, I will check out radsniff :)
-
@furom I need to get back to this - I had disabled the wpa2 enterprise auth I was using when my company freaking locked their phone down so hard could no longer install profiles.
But no longer work for that company, and I can now do what I want with my phone ;) So should be able get back to doing eap-tls auth.
I do have wpa3 working - I have a thread around here somewhere about doing that with unifi and validating your phone is using it via developers profile from apple you can install... Let me see if I can find that thread. And when I get a chance maybe I will fire up wpa3 enterprise again.
edit: here is the old thread I mentioned
-
@johnpoz Probably a given answer here, but I suppose I need to install PCAP to mitigate this error?
: radsniff -x Logging all events Defaulting to capture on all interfaces radsniff: No PCAP sources available``` -
@furom I’ll have a look at radsniff when I get back home, it used to just work.
-
@furom that seems odd - what version of pfsense are you running?
When I run that it starts listening on all my interfaces
[22.05-RELEASE][admin@sg4860.local.lan]/: radsniff -x Logging all events Defaulting to capture on all interfaces Sniffing on (igb0 gif0 tailscale0 igb1 ovpns1 igb2 ovpns2 igb3 ovpnc3 igb4 igb2.4 igb5 igb2.6 lo0 pflog0)[22.05-RELEASE][admin@sg4860.local.lan]/: radsniff -v radsniff version 3.0.25, built on Jun 2 2022 at 00:26:34 libpcap version 1.9.1 [22.05-RELEASE][admin@sg4860.local.lan]/: -
@johnpoz I wonder if he’s ran it on the AP.
-
@johnpoz Agreed. I am running latest pfSense Plus (22.05) I just found this topic, which shows a few this I did not have configured strangely enough. I was following a guide before I no longer have, so guess a wipe and redo is what I need to do. Biggest woes is what I will need to configure in Unifi?
-
@nogbadthebad Its not available on any of my unifi APs
Hallway-BZ.6.5.26# radsniff -ash: radsniff: not found Hallway-BZ.6.5.26# -
@nogbadthebad said in radius and wpa3 with client wpa2 ?:
@johnpoz I wonder if he’s ran it on the AP.
Nah, the 'radsniff -x ' was issued in pfSense CLI via SSH.
-
@furom said in radius and wpa3 with client wpa2 ?:
Biggest woes is what I will need to configure in Unifi?
There shouldn't be much to configure on the unifi side, let me see if I still have it there as option that just not using.
My profile is still there

That IP is the IP of pfsense on the vlan the AP sit on for their management..
I even have the setup for the AP in freerad on pfsense - just not using it currently..
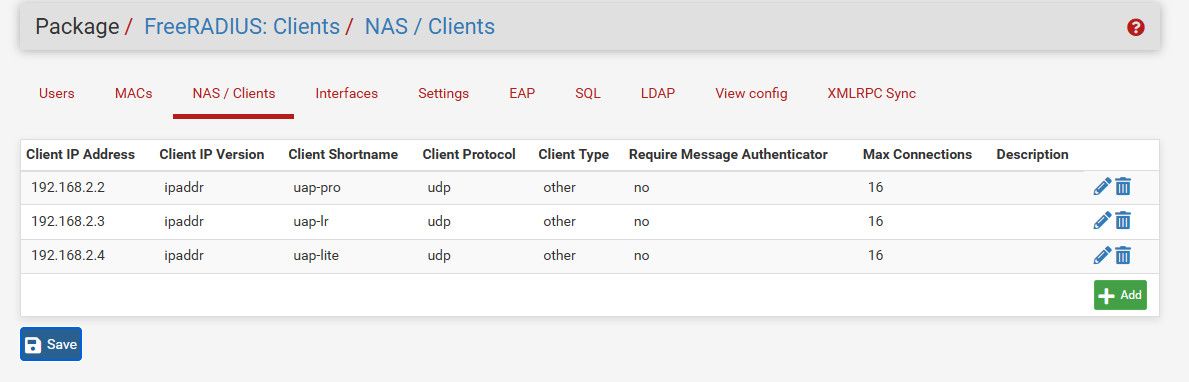
Not exactly sure when I will get around to testing this out again - got football this weekend, and tonight is movie night with the wife.. But I am normally up early, so might get around to testing it out tmrw morning before the wife gets up, etc.
-
@johnpoz Thanks, that looks what I had there already, then selecting that profile in the wifi setup... I will have to debug this I think. Thank you both for your support so far, I'll start over and set it up again, there is something odd somewhere. :)
-
@johnpoz said in radius and wpa3 with client wpa2 ?:
Not exactly sure when I will get around to testing this out again - got football this weekend, and tonight is movie night with the wife.. But I am normally up early, so might get around to testing it out tmrw morning before the wife gets up, etc.
No rush, this is for sure not critical, but fun and I do appreciate the help :) Thanks!
-
@furom well that was easy.. Clicky Clicky back in.. using wpa3 enterprise..
The biggest issue I had was update in openssl and or apple or whatever and now adding a password to the .p12 wasn't working, took me a bit to find adding -legacy to the end..
So all my stuff was still in place, just just created a new ssid using wpa3 enteprise, with my freerad profile.
Installed the ca and freerad server certs and my user cert and key, after adding password with openssl
here is the cmd I used
openssl pkcs12 -export -certfile freerad.crt -in johnsXR.crt -inkey johnsXR.key -out user.p12 -legacyI just used the old cert I had on this new phone.. name doesn't matter as long as all matches up with your user your create in freerad and the cert cn, etc.
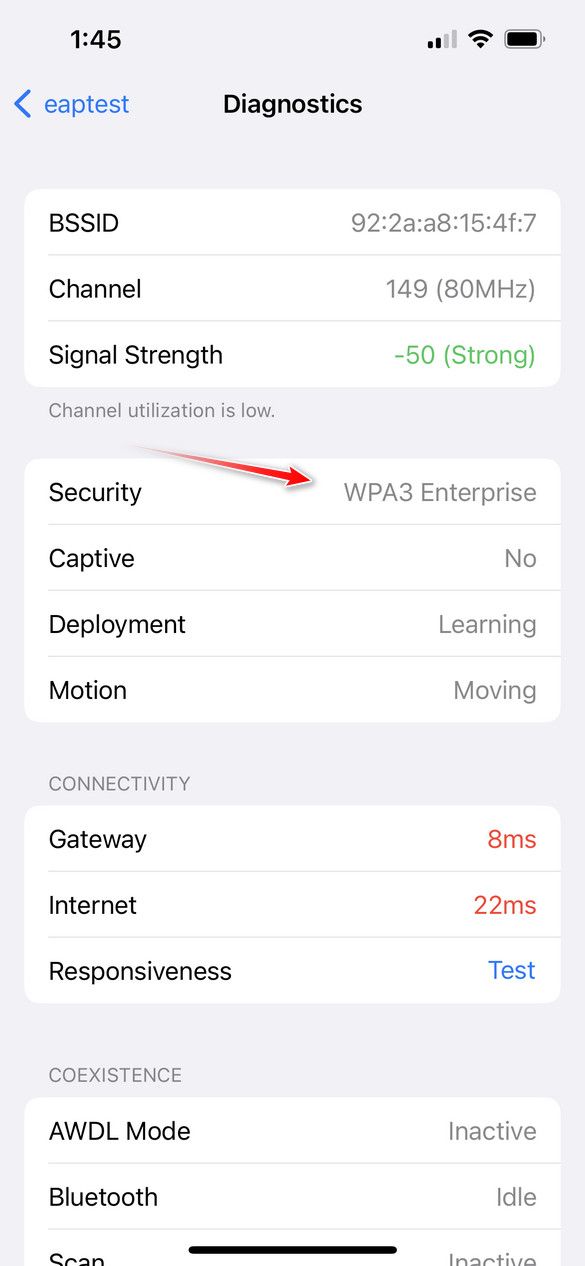
edit: now wonder if work with the 192 fips setting?? hmmm
edit2: well shoot, my APs don't support it - shucks!Well now that got it up and running again - what exact question(s) do you have??
turned logging back on
Jan 27 14:05:49 radiusd 89431 (7) Login OK: [johnsXR/<via Auth-Type = eap>] (from client uap-pro port 0 cli BE-61-59-13-C9-48) 192.168.2.2 Auth-Type: eapedit3: are you trying to setup wpa3 enterprise - what eap are you using. I have always used nothing be eap-tls, ie a cert to auth.. I could try changing the eap.. But to me if your going to to the trouble of setting it up, might as well use the added strength of certs vs just some username password.. I reread your first post, does your client not support wpa3?
-
@johnpoz said in radius and wpa3 with client wpa2 ?:
I reread your first post, does your client not support wpa3?
Thanks for testing! I have been so far been using eap-ttls when on WPA2 Enterprise. That is really my goal here, but any config working must be the first...
Client for now is an older android tablet, only capable of WPA2 Enterprise, but still thought I'd set server-end up with WPA3 if I later should upgrade the client. I thought WPA3 Enterprise was backwards compatible, but must have missed something obviously.
I thought I was ready for test so retried the radsniff -x via ssh, but was still getting the same error as before; No PCAP sources available. So figured it could have something to do with permissions... So I ended up installing sudo - which now allows me to run 'sudo radsniff -x'..! :) So a little progress at least.
Unfortunately, it captures no activity what-so-ever when trying to authenticate my client. My SSID is visible in the list on the client as "saved" only, and when hitting 'Connect', it just closes that dialog, nothing else...
Since my certificates worked fine on WPA2 Enterprise until the other day when I decided this was a great idea :) I suppose they are not to blame for this mishap.
Perhaps I should retry with WPA2 Enterprise just to verify the rest of the setup... If that works, a new client will perhaps be a good idea after all...
-
@furom Well... tested reverting back to WPA2 Enterprise (eap-ttls/mschapv2) and then realized one issue was my tablet actually forgot about the certificate which then had to be reinstalled for WLAN, but after that it worked fine. :)
Switching back to WPA3 Enterprise, thinking it now perhaps could work, I had to install the cert once again strange enough, and after authenticating it just shows the SSID as "saved" in the list once again... No other messages or activity on Radius server (radsniff).
Based on this I can only assume it is some sort of limitation on client side. And as nothing gets in the logs I don't know how to really verify the actual cause, but not working is perhaps clear enough... :) I will continue for a bit to see if there is something that can be done to get it working, but suppose I have to upgrade the tablet if I want WPA3...
Edit: Found several posts saying WPA3 is backwards compatible with WPA2, but that this is not the case for WPA3 Enterprise. This from Unifi config seems to confirm that;
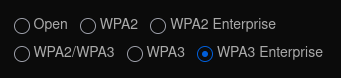
Thanks @johnpoz & @NogBadTheBad !!
-
@furom you understand security protocol be it wpa2 or wpa3 psk or enterprise is from the client to the AP right. This has nothing to do with the auth being done from the AP to the radius server.
if your client is not able to do wpa3 enterprise then no it wouldn't work. Update your client to something that supports wpa3 enterprise and you should be fine.
You can see my iphone shows that its using wpa3 enterprise via the developer profile I added on the phone to get that info.
Or just use wpa2 enterprise - I do not believe there is much more security in wpa2 enterprise vs wpa3 psk for example.
If your client is not able to negotiate with the AP to auth, then no the AP would never send anything to radius so no your radsniff wouldn't see anything..
Here I grabbed my phone.. And connected to my wap3 enterprise ssid, while running radsniff on my pfsense

-
@johnpoz said in radius and wpa3 with client wpa2 ?:
@furom you understand security protocol be it wpa2 or wpa3 psk or enterprise is from the client to the AP right. This has nothing to do with the auth being done from the AP to the radius server.
if your client is not able to do wpa3 enterprise then no it wouldn't work. Update your client to something that supports wpa3 enterprise and you should be fine.
You can see my iphone shows that its using wpa3 enterprise via the developer profile I added on the phone to get that info.
Or just use wpa2 enterprise - I do not believe there is much more security in wpa2 enterprise vs wpa3 psk for example.
Yes I do get the setup, but the woe was if the protocol in fact was backwards compatible or not, which it for Enterprise turned out not to be.
You have a valid point... I automatically assumed I would want to go for WPA3 Enterprise... I need to do more reading on what WPA3-psk offers over WPA2 Enterprise. I surely don't "need" all this, but if available, why not? :) Thanks!
-
@furom said in radius and wpa3 with client wpa2 ?:
surely don't "need" all this, but if available, why not? :) Thanks!
I hear ya - and agree, if I can do wpa3 enterprise, why not use it! ;) Problem is with any new protocol, is its going to take time for everything to catch up..
And good luck with shit devices like iot devices, have never seen one support wpa enterprise anything. They only do psk, which ok they should support wpa3 psk.. But that prob going to take quite a few years, and the current iot stuff you have will most likely not just have a software upgrade, etc. so if you wanted to true go to wpa3 all your iot stuff prob have to be swapped out for stuff that supports it.
When it first came out, I tried making my guest network wpa3 psk only - guess what, nobodies clients that came over supported it ;) And I had to drop it back to wpa2.. I really don't think there is much point in running compatible mode wpa2/wpa3 psk - if you have devices that are still doing wpa2 kind of defeats the point of wpa3 being stronger, since wpa2 is still there..
Other than you can ;) and nice to get new stuff working - even if only partially. Which ticks me off about both iphone and unifi - why not show what the client used to auth.. This is good info to know if your trying to move to the new standard.. In unifi it would be really helpful to see which clients are authing with the new wpa3 psk, and which ones are still using wpa2
At least with the iphone I can install that developers profile and get the info, but the profile is only valid for a couple of weeks, and then it has to be reinstalled..