Geoblocking the world except for home
-
Hi everyone. I’m very new, so apologies in advance if this is somewhere else and I didn’t see it. :)
I’m trying to block outgoing connections to all but a handful of countries, as there’s something sneaky on my network that keeps calling home to Barbados. And it’s very clever—it is a shapeshifter and tries to look different every time it calls home to ask for money. ;-)
I set up an alias with the countries I want to allow—the US, Switzerland, the UK, etc. I then set up a rule on the WAN to block anything not on the list. But it’s blocking all outgoing connections.
Thanks so much for any help you can offer. :)
-
@trigglepuff Firewall rules are processed in order, as a packet arrives on an interface. Thus WAN rules apply to inbound from the Internet. LAN rules apply to connections out to the Internet. So if you're trying to connect out, use LAN rules like:
allow from LAN Net to (alias) port 443
reject from LAN Net to * port 443
(repeat with port 80 or others)
(default) allow from LAN Net to * -
@steveits Thanks so much Steve. If my alias is countries that to which I want to allow outbound connections, am I doing this correctly in choosing an inverse match?
If so, I am thinking my next rule is to block everything outbound NOT headed to these countries. :) :)
-
@trigglepuff Inverting can be a bit tricky so I'd avoid it if you're getting started with pfSense. It's usually easier to follow the rules without those sort of things.
The two rules I posted above will allow HTTPS out to your alias and block the rest. Can you post the LAN rules you have now that aren't working?
-
@steveits Hi Steve. I created a GEOIP-based alias named pfB_SAFECNS_v4, then set it up to allow all LAN packets out. I then tried to block by inverting the match, so that if packets aren’t headed from the LAN to a safe country, they get stopped. But the latter seems to still let stuff through—which I guess could be a function of where the host’s CDN is, etc.
I also noticed that whatever my spyware is that is calling home to Barbados, it’s using some of the really esoteric ports and moves around. But when I look up the destination addresses, they’re all clustered in the same area in Barbados. And I work at a high-risk job, so I don’t like things that call home without asking me first :)
-
@trigglepuff Note if there are open states when you add rules, pfSense will honor the state and continue to allow the traffic.
https://docs.netgate.com/pfsense/en/latest/troubleshooting/firewall.html#check-the-state-table
"If the rule is a block rule and there is a state table entry, the open connection will not be cut off. To see an immediate effect from a new block rule, the states must be reset."If you do something like
reject from LAN Net to (!alias)
...I would probably expect that to block the pfSense IPs since they are not in the alias. One can work around that by adding an allow rule above it.If you create a rule to reject from LAN Net to Barbados and log it you can find the IPs connecting out.
-
Am I not understanding the idea here... It seems to me that it's as simple as going into pfBlocker > IP > GeoIP and then under each region simply mark all the countries that should be blocked. Then select outbound, inbound or both, for each region...
If it's just a few countries that should be allowed, do a select All and then Ctrl click the few you want to deselect...
All the rules will be created automatically after that... -
@gblenn IMO its much better to create an an alias rather than use the GeoIP tab and use it in a firewall rule:-
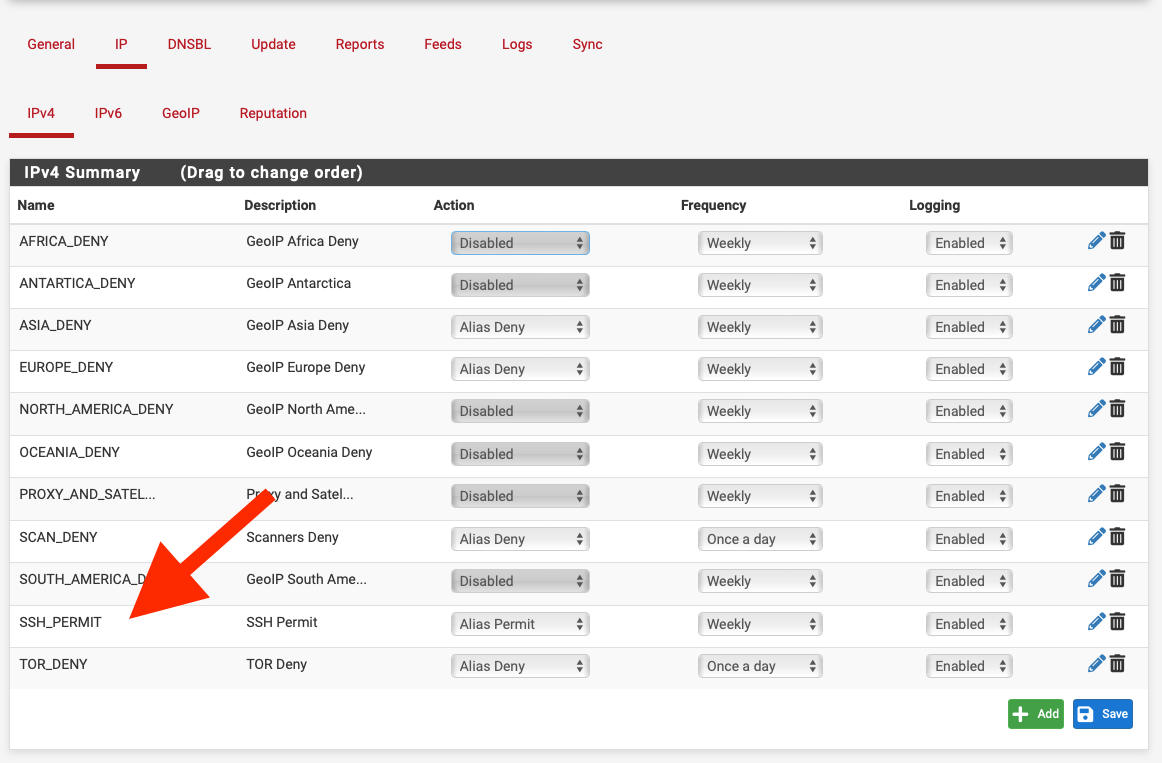
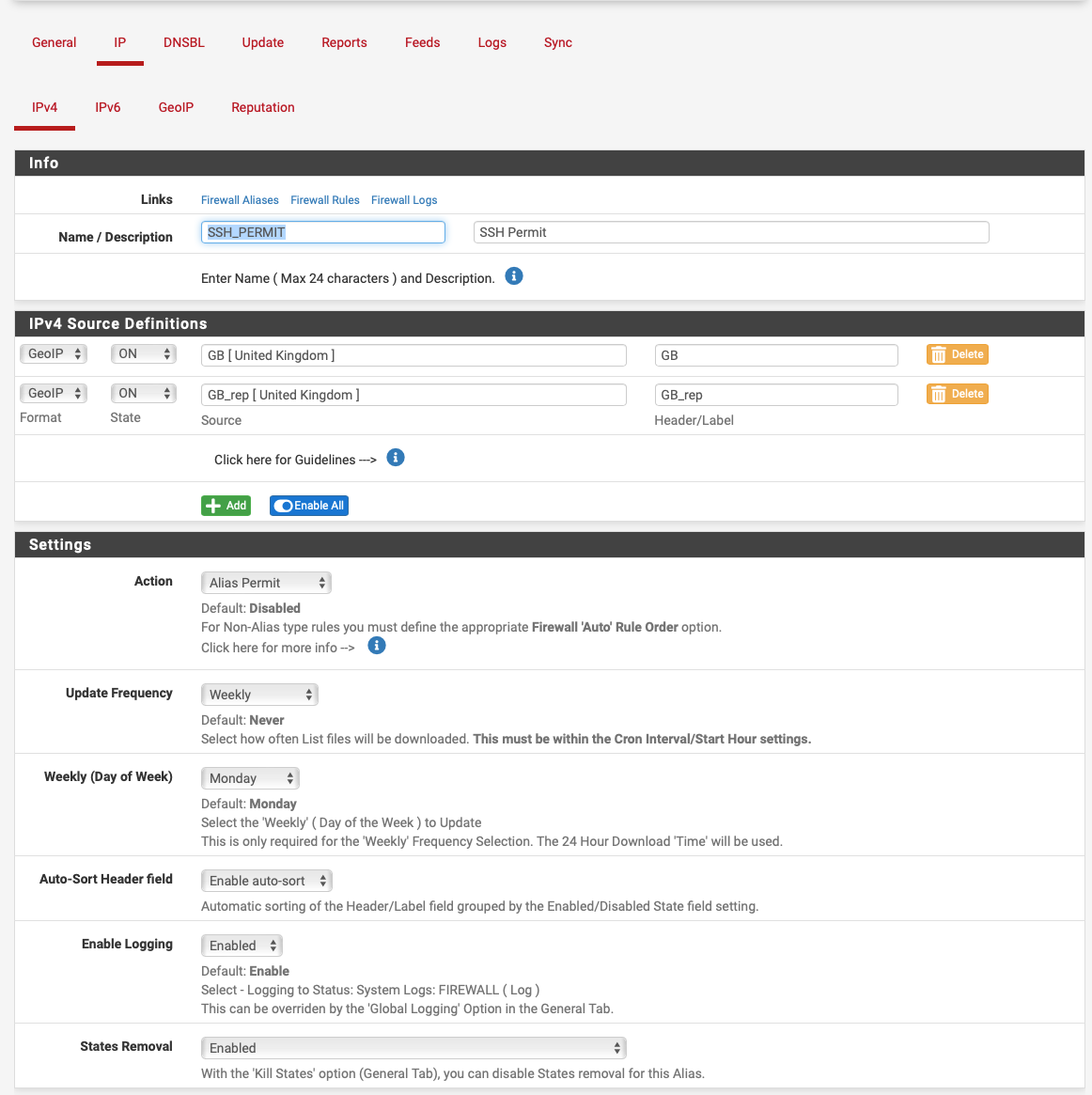
-
@nogbadthebad Since you showed "alias permit" just be aware that reportedly de-dupes across other permit or deny lists. There was a thread last year sometime where someone pointed out IPs were being removed. Alias Native will leave the lists unchanged.
@Gblenn You're not wrong. :) Aliases are a bit more flexible, for instance we can allow traffic to certain IPs, then block the country. pfB deny rules insert together, by default at the top of the list of rules (per "Firewall 'Auto' Rule Order").
-
@steveits I think I have to dig into Aliases a bit more. Using it for simple stuff like ports and device IP's of course but it seems like there is a lot to learn...
-
@steveits said in Geoblocking the world except for home:
@nogbadthebad Since you showed "alias permit" just be aware that reportedly de-dupes across other permit or deny lists. There was a thread last year sometime where someone pointed out IPs were being removed. Alias Native will leave the lists unchanged.
Cheers I've changed them :)