Unable to connect to IPs on different subnet
-
@valepe69
Show pics of the rules on both interfaces.
Show pics of your switch config.Is the built-in switch the only switch being used?
If you plug a pc into a camera vlan port on the switch, do you reach the NVR and cameras?
If another switch is involved, most common problem is people tag the vlan on the switchports when it should be untagged. -
@jarhead said in Unable to connect to IPs on different subnet:
@valepe69
Show pics of the rules on both interfaces.
Show pics of your switch config.these are the rules I have:
LAN side
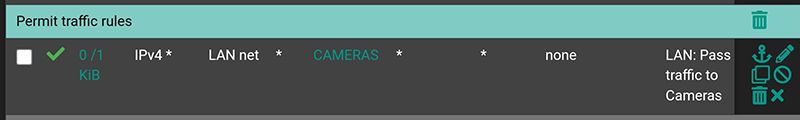
Camera VLAN side:
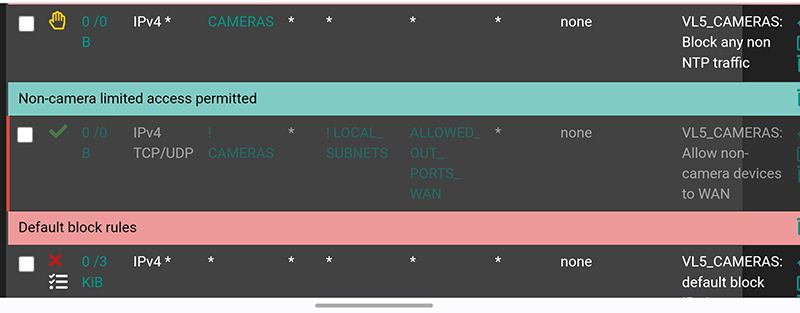
- the middle rule is disabled
Is the built-in switch the only switch being used?
No, the builtin switch is connected to my main managed switch
If you plug a pc into a camera vlan port on the switch, do you reach the NVR and cameras?
Yes, I can reach cameras without issues
If another switch is involved, most common problem is people tag the vlan on the switchports when it should be untagged.
No, the port (assigned to the cameras link) is untagged with the correct PVID of the camera VLAN
The CAMERAS alias is configured as 10.1.1.0/24
-
@valepe69 do the cameras have a gateway set on them? Have seen many a camera that do not allow for setting a gateway. If you can not set a gateway on the camera so it knows to send traffic back to pfsense when it sees traffic from an IP that is not on its local network - then no you wouldn't be able to talk to it from any of your other vlans.
The work around for this sort of issue is to setup an outbound nat on your camera vlan interface, ie source natting.
This way when you talk to one of the cameras at 10.1.1.x from your 192.168.1 network the camera will think you talking to it from pfsense IP on the camera network 10.1.1.2
Cleaner solution is to setup a gateway on your cameras - but if that is not possible or they do not allow access from anything other than their local network, then the outbound nat is a valid work around.
-
@johnpoz said in Unable to connect to IPs on different subnet:
@valepe69 do the cameras have a gateway set on them? Have seen many a camera that do not allow for setting a gateway. If you can not set a gateway on the camera so it knows to send traffic back to pfsense when it sees traffic from an IP that is not on its local network - then no you wouldn't be able to talk to it from any of your other vlans.
The work around for this sort of issue is to setup an outbound nat on your camera vlan interface, ie source natting.
This way when you talk to one of the cameras at 10.1.1.x from your 192.168.1 network the camera will think you talking to it from pfsense IP on the camera network 10.1.1.2
Cleaner solution is to setup a gateway on your cameras - but if that is not possible or they do not allow access from anything other than their local network, then the outbound nat is a valid work around.
The cameras network is setted up by the switch builtin in the NVR.
So I can't touch anything in the camera network configuration (I worried to touch anything here to avoid issues between NVR and cameras).I'll try to add an outbound NAT rule from LAN net to NVR net.
Thanks
-
@valepe69 remember that outbound nat would be on your NVR interface. Not the lan interface..
-
@johnpoz said in Unable to connect to IPs on different subnet:
@valepe69 remember that outbound nat would be on your NVR interface. Not the lan interface..
Do you refer to the pfSense interface connected to the poe switch of the NVR, right?
Otherwise I'm out. No control over the network managment of the camera side on the NVR.
The nat should be something like:
NVR net to LAN net -
@valepe69 said in Unable to connect to IPs on different subnet:
NVR net to LAN net
The outbound would be something like this
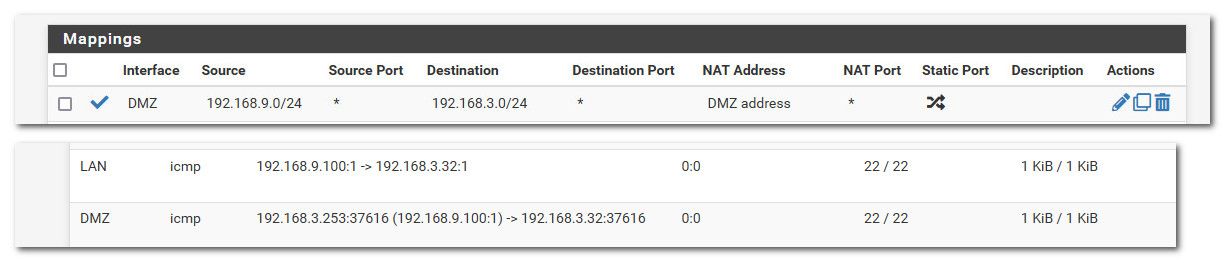
Lets say my DMZ interface was where my NVR network was, and it was 192.168.3.0/24, now my lan is 192.168.9.0/24
If I want traffic from my 192.168.9.0/24 network to look like its the dmz IP.. See from the outbound nat, and then my state table when pinging 192.168.3.32 from my 192.168.9.100 PC
you can see where pfsense natted that to look like the ping is coming from my pfsense dmz interface address (192.168.3.253)
You can get as specific as you want with a /32 for source and or destination so the nat only would be for specific ip talking to other specific IP... You could set that it only does it on port 80, etc..
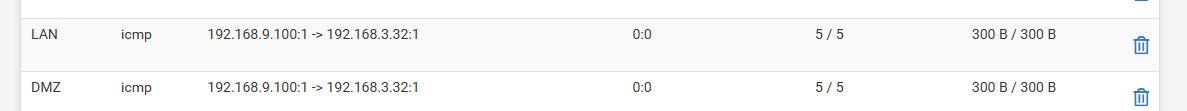
edit: so here is what it normally would be, I removed the outbound nat on my dmz interface - now when I ping the 3.32 address here are the states
-
@valepe69 said in Unable to connect to IPs on different subnet:
The cameras network is setted up by the switch builtin in the NVR.
So I can't touch anything in the camera network configuration (I worried to touch anything here to avoid issues between NVR and cameras).I'll try to add an outbound NAT rule from LAN net to NVR net.
Thanks
That's what I figured.
The NVR is a router. Is it Hikvision by any chance?
You'll have to port forward in the NVR itself. -
@johnpoz Dahua one.
You can't add rules to its network behavior. Well, you can but the changes will not survive a reboot -
@johnpoz Thanks a lot, it works!