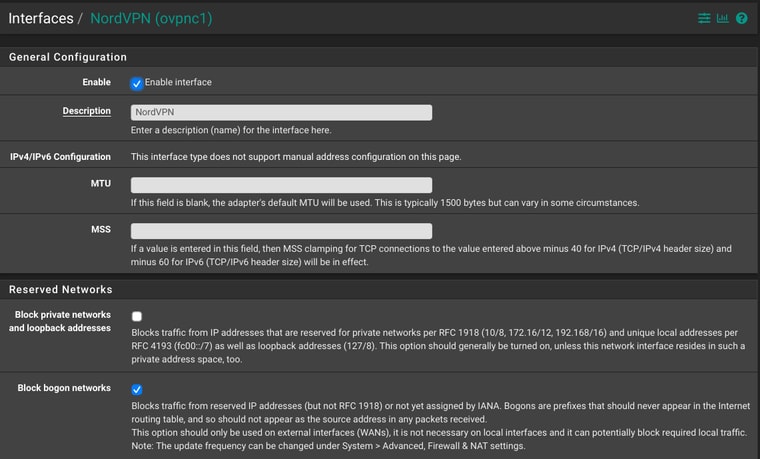
OpenVPN fails because it won’t create a tunnel
-
WAN (wan) -> mvneta2 -> v4/DHCP4: 192.168.12.143/24
v6/DHCP6: 2607:fb91:1184:d82d:207d:cea7:0:1cd/128
LAN (lan) -> mvneta1 -> v4: 192.168.64.1/24
NordVPN (opt1) -> ovpnc1 ->Feb 11 13:06:39 openvpn 43662 PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 103.86.96.100,dhcp-option DNS 103.86.99.100,sndbuf 524288,rcvbuf 524288,explicit-exit-notify,comp-lzo no,route-gateway 10.8.0.1,topology subnet,ping 60,ping-restart 180,ifconfig 10.8.0.9 255.255.255.0,peer-id 6,cipher AES-256-GCM'
Feb 11 13:06:39 openvpn 43662 OPTIONS IMPORT: timers and/or timeouts modified
Feb 11 13:06:39 openvpn 43662 OPTIONS IMPORT: explicit notify parm(s) modified
Feb 11 13:06:39 openvpn 43662 OPTIONS IMPORT: compression parms modified
Feb 11 13:06:39 openvpn 43662 OPTIONS IMPORT: --sndbuf/--rcvbuf options modified
Feb 11 13:06:39 openvpn 43662 Socket Buffers: R=[42080->524288] S=[57344->524288]
Feb 11 13:06:39 openvpn 43662 OPTIONS IMPORT: --ifconfig/up options modified
Feb 11 13:06:39 openvpn 43662 OPTIONS IMPORT: route options modified
Feb 11 13:06:39 openvpn 43662 OPTIONS IMPORT: route-related options modified
Feb 11 13:06:39 openvpn 43662 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Feb 11 13:06:39 openvpn 43662 OPTIONS IMPORT: peer-id set
Feb 11 13:06:39 openvpn 43662 OPTIONS IMPORT: data channel crypto options modified
Feb 11 13:06:39 openvpn 43662 ROUTE_GATEWAY 192.168.12.1/255.255.255.0 IFACE=mvneta2 HWADDR=00:08:a2:12:8e:28
Feb 11 13:06:39 openvpn 43662 Cannot open TUN/TAP dev /dev/tun1: No such file or directory (errno=2)
Feb 11 13:06:39 openvpn 43662 Exiting due to fatal error[admin@[redacted].[redacted].[redacted]]/dev: ls
bpf ctty cuau1 devctl2 fd geom.ctl iic0 mem mmcsd0rpmb pf random stdout ttyu1 ugen0.1 usbctl
bpf0 cuau0 cuau1.init devstat fido gpioc0 klog mmcsd0 null pfil reroot ttyu0 ttyu1.init ugen1.1 xpt0
console cuau0.init cuau1.lock diskid flash gpioc1 kmem mmcsd0boot0 openfirm ptmx stderr ttyu0.init ttyu1.lock urandom zero
crypto cuau0.lock devctl etherswitch0 full gpioc2 mdctl mmcsd0boot1 pci pts stdin ttyu0.lock ufssuspend usbThere is no IP address for ovpnc1.
Notice tun1 is missing above after configuring OPT1.
Makes it impossible to use OpenVPN as a client.OpenVPN isn’t a package, so I can’t uninstall/reinstall.
modprobe isn’t installed, so I can’t use that to fix the problem.
I can’t write to /dev so I can’t create the tunnel by hand…
Is there a way to make this work again? -
@wn7ant
Hi,Please add
pull-filter ignore comp-lzoto the client configuration file from Nord vpn and try again.
-
Thanks for trying, same error.
-
Can you please show your interfaces configuration? (In order to use an OpenVPN tun virtual adapter, it needs to be assigned to an interface first.)
-
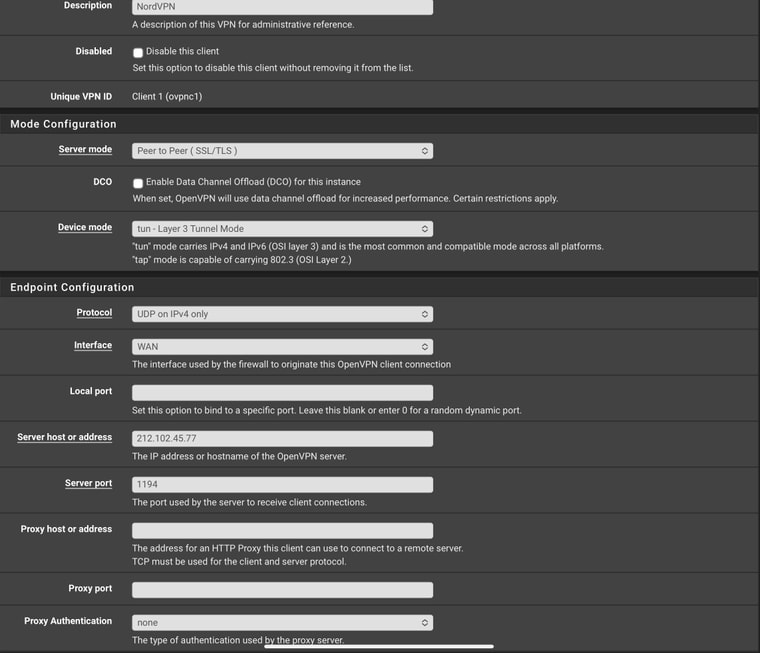
If you look at th top of this you’ll see three Interfaces listed. Two have IP’s. Here’s the configuration of the tunnel, exactly as NordVPN described it should be configured.
-
There’s the config info. I did EXACTLY what Nords directions show. I even swapped the IP for the URL and it changed nothing.
FWIW I also tried TCP and port 443.
I dropped to the shell and made sure I could reach both the IP and the URL that this IP represents.
-
@wn7ant I am late, I know and I wrote nonsense last time... To tell the truth, it was a tough week at work. Sorry. Anyway, if you did not see any joy by now, did you try turning this off:
 ?
? -
@wn7ant Also, you need to only use the url, I think? I see many dropouts with my setup, I don't even think they have a very stable OpenVPN config server-wise. They should opt for WireGuard, seeing as they heavily develop on it, anyway (NordLynx).
-
@wn7ant Sorry for 3 replies in a row... I tend to write as I see. But,
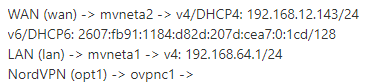
this right here could be your issue, seeing as you might be behind another (CPE, yes, but) firewall.
That means NAT with pfsense behind it.
That means that you are not using a Public IPv4.
Can't do OpenVPN reliably behind NAT, at least not with firewalls like PfSense as clients.Also, because of the way IPv4-NAT and IPv6-GUAs are routed, you might be having additional problems (and latencies) because of double NAT and a single IPv6 (/128) address on the WAN interface.
WAN needs at least a /64 IPv6 subnet to perform either DHCPv6 or do Prefix Delegation on the ifaces downstream (eg, LAN).
In the case of prefix delegation (which is strongly suggested), you need subnets larger than /64 (/60, /56, /52, /48).
It's usually /48, but that is not a given (my ISP hands out /56's).If your environment isn't a VM lab, maybe try to contact your ISP and put the CPE modem/AC/router in PPPoE (or PPPoA) passthrough mode (the CPE will still be a WiFi AC and router for any clients connected on it, like phones, TVs, PCs and such) or bridge mode (the CPE will no longer be a router or a WiFi AC, but just a bridge for PFSense, the ISPs own VoIP and/or TV). That way, you can
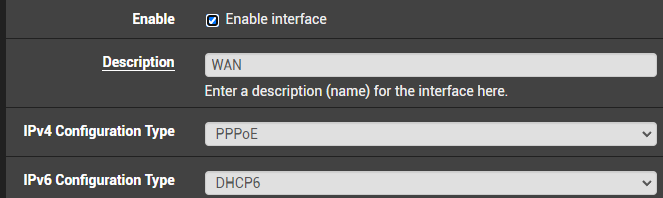
and here you usually you need your username and pass tied to your subscription account (you get those from your ISP)
In business environments, most ISPs give a static /32 IPv4 for free as an option (not advertising it, though).
In that case, you might get them to give you a static /32 IPv4 for pfsense (through PPPoE/A passthrough) AND a dynamic (usually CG-NATed) /32 IPv4 for the CPE.Also, if you are situated in a VM lab, you not only need to give pfsense a physical interface (network card) passed-through by the hypervisor, but you also need this interface to NOT be behind a CPE (router-modem or just router). If that is the case, you will encounter a lot more problems down the road. As long as you do not do that, you are under the thumb of the ISP (they control the CPE's firewall) and must accept the limitations that come with this type of setup (UDP connections are notoriously unfriendly to NAT, some applications depend on a stable internet-facing port, you might be getting a CG-NATed address on the CPE, which makes any client behind pfsense triple NATed...)
-
 N NightlyShark referenced this topic on
N NightlyShark referenced this topic on