Default deny rule IPv4 (1000000103) blocking MS RDP connection
-
How do I stop PFsense from blocking an LAN RDP connection? I can't find an option to edit the Default deny rule IPv4. I tried adding rule to allow traffic for RDP but it's not working.
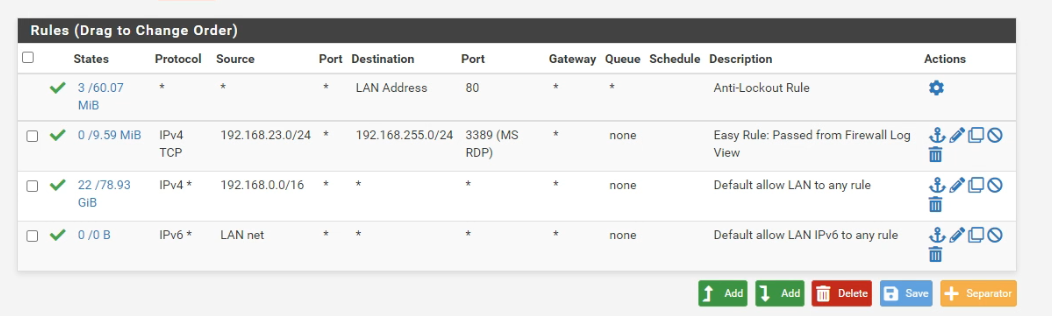
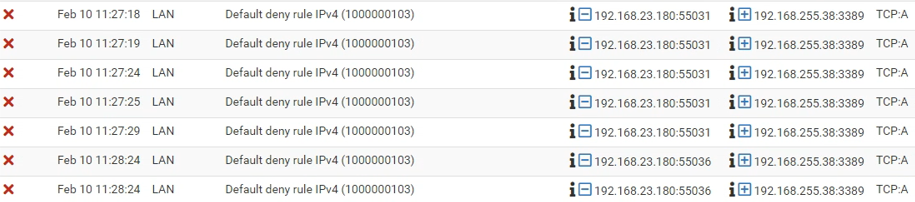
-
There is a .255. in that IP address.
Check with that device, and change it to anything else.Also, MSRDP, wasn't that using (also) 'UDP' ?
I agree, your Allow all IPv4 /16 rule should permit all LAN IPv4 traffic.
Btw : you can't edit the final 'block all rule'.
-
@gertjan said in Default deny rule IPv4 (1000000103) blocking MS RDP connection:
There is a .255. in that IP address.
Why is this a problem? (it is not at the end of the IP) Just asking :-)
-
@dfsense said in Default deny rule IPv4 (1000000103) blocking MS RDP connection:
How do I stop PFsense from blocking an LAN RDP connection? I can't find an option to edit the Default deny rule IPv4. I tried adding rule to allow traffic for RDP but it's not working.



Which IP range is your LAN? Is that 192.168.23.180 device actually in the IP subnet defined on your LAN? If not, then you need to put the PASS rule for RDP traffic on the interface where that host's subnet lives.
In pfSense, you put firewall rules on the interface where traffic "enters" the firewall from the wire. So if you have an interface whose subnet is defined as 192.168.1.0/24, you would never put a rule there that said this:
192.168.4.23 --> some-other-host
because nothing with a source IP of 192.168.4.23 would be a "legal" host in that 192.168.1.0/24 subnet. You would instead put the PASS rule on the firewall rules tab for the 192.168.4.0/24 network.
To summarize -- I believe you may have your RDP pass rule defined on the wrong interface. It needs to go on the interface where the 192.168.23.0 network is defined.
-
@fireodo said in Default deny rule IPv4 (1000000103) blocking MS RDP connection:
@gertjan said in Default deny rule IPv4 (1000000103) blocking MS RDP connection:
There is a .255. in that IP address.
Why is this a problem? (it is not at the end of the IP) Just asking :-)
True.
I made a 'better safe then sorry' reflection. -
@dfsense those blocks are all Acks (A)... that points to out of state traffic..
https://docs.netgate.com/pfsense/en/latest/troubleshooting/log-filter-blocked.html
-
MSRDP, wasn't that using (also) 'UDP'
It was TCP originally. UDP was added a few years ago. My experience (us and a couple clients) on Windows 10 is using UDP results in random hangs, where a disconnect/reconnect is necessary. For the last year Windows 11 seems to not have that issue, though we haven’t enabled UDP again on Windows 10. UDP is not required.
-
@steveits doesn't really matter if using tcp or udp here. His rule below that easy rule is an any so either would be allowed. But the issue I see in his logs are those blocks are out of state blocks. They are not blocking SYN, they are blocking Acks.. If they were blocking syn that would mean his rules do not allow the traffic, blocking anything other than syn only points to reason for the block is lack of a state.
-
Hi all,
Just wanted to report that the issue has been resolved. Someone recommended adding a static route in Windows command prompt. I don't know much about networking so I'm not sure how it worked. Thank you for the responses on this.
route add 192.168.0.0 mask 255.255.0.0 192.168.23.1 -p
-
@dfsense Well that is wrong solution to a self inflicted issue.. Is pfsense not the default gateway to these devices?