Wireguard Firewall Rules
-
Have got Wireguard setup - pfsense to iphone at the second attempt. But somewhat puzzled - on Tom's tutorial the firewall rules page just has "wireguard" as an interface for rules, but mine (latest release of pfsense dev and wireguard) has an additional interface for my tunnel. The rules to allow traffic (full tunnel) only work on "wireguard".
Can someone point me to the explaination please? - I'm guessing "work in progress" and rules will eventually go on each tunnel???
Thanks
-
@thondwe It depends on if you assigned an interface (ie OPTx) to the tunnel or just assigned the IP in the Wireguard config itself.
I can't see any real reason to assign an interface to a remote access tunnel but some people seem to do that.If interface assigned, use the interface for rules.
If no interface assigned, use the Wireguard group for rules.This also depends on this setting:
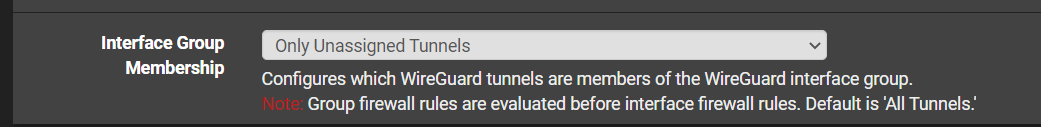
-
@jarhead Thanks got it now - read through a couple of tutorials, one of which must have including assigning the interface. I assume if I change that setting from "all", I can get the interface rules to kick in.
Assume the benefit of assigning would come into play with multiple tunnels with a need for different rules then? e.g. Test + Production? Or when using a site-to-site setup??
-
@thondwe said in Wireguard Firewall Rules:
Assume the benefit of assigning would come into play with multiple tunnels with a need for different rules then? e.g. Test + Production? Or when using a site-to-site setup??
Exactly. And how often do you have multiple remote access tunnels on the same system? Usually one would just make one RA tunnel with a big enough subnet for however many users they would need. So no real need for an interface.
But site to sites definitely benefit from the separate rules.