TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
-
Hello World,
I am hoping someone in this community is able to help me, I know a little about networking but am no expert. I have been following youtube videos from the likes of Lawrence Systems but have not been able to implement a working OpenVPN server with outside connections.
Lawrence Systems "Tutorial: pfsense OpenVPN Configuration For Remote Users 2020"
https://www.youtube.com/watch?v=PgielyUFGeQpfSense system
This issue I have is a PC within my local network is able to connect to the OpenVPN server so I know the credentials and authentication are correct however when I try to connect with my mobile device on 4G I get timeout errors. I have a Family member whom I believe was testing with his windows computer and received the error message:-
2023-01-30 22:36:05 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)I'm waiting for him to clear his log retest and send me this information.
My successful connection, local computer Log output is below:-
2023-01-30 19:28:22 OpenVPN 2.5.2 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Apr 21 2021 2023-01-30 19:28:22 Windows version 10.0 (Windows 10 or greater) 64bit 2023-01-30 19:28:22 library versions: OpenSSL 1.1.1k 25 Mar 2021, LZO 2.10 Enter Management Password: 2023-01-30 19:28:28 TCP/UDP: Preserving recently used remote address: [AF_INET]10.132.152.178:1194 2023-01-30 19:28:28 UDPv4 link local: (not bound) 2023-01-30 19:28:28 UDPv4 link remote: [AF_INET]10.132.152.178:1194 2023-01-30 19:28:29 [EMBY SERVER SC] Peer Connection Initiated with [AF_INET]10.132.152.178:1194 2023-01-30 19:28:29 open_tun 2023-01-30 19:28:29 tap-windows6 device [Local Area Connection] opened 2023-01-30 19:28:29 Set TAP-Windows TUN subnet mode network/local/netmask = 10.0.8.0/10.0.8.2/255.255.255.0 [SUCCEEDED] 2023-01-30 19:28:29 Notified TAP-Windows driver to set a DHCP IP/netmask of 10.0.8.2/255.255.255.0 on interface {26AEFC9F-261E-4EE7-920F-48A8B1C9E54C} [DHCP-serv: 10.0.8.254, lease-time: 31536000] 2023-01-30 19:28:29 Successful ARP Flush on interface [6] {26AEFC9F-261E-4EE7-920F-48A8B1C9E54C} 2023-01-30 19:28:29 IPv4 MTU set to 1500 on interface 6 using service 2023-01-30 19:28:34 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this 2023-01-30 19:28:34 Initialization Sequence Completed 2023-01-30 19:28:42 SIGTERM received, sending exit notification to peer 2023-01-30 19:28:44 SIGTERM[soft,exit-with-notification] received, process exitingI saw on the Netgear documentation that you can assign an interface to the server which I believe I have also compelled and set up the correct NAT and Firewall rules however I feel this is where the outside connections are failing.
I believe that I have identified the inbound connections (pfSense logs seem to update very slowly! ) but I never seem to identify outbound traffic to the inbound IP address.
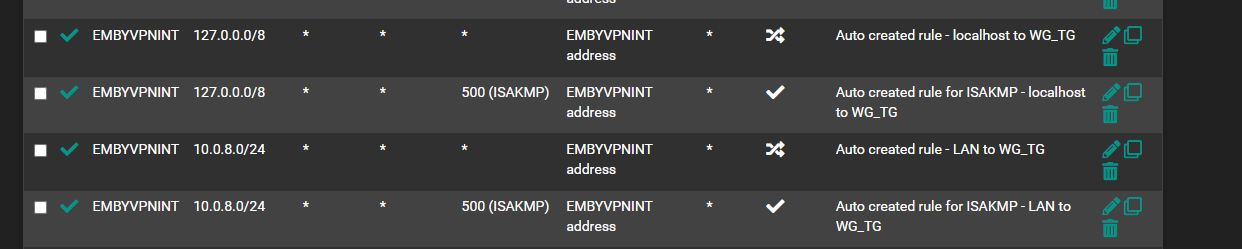
NAT Rules
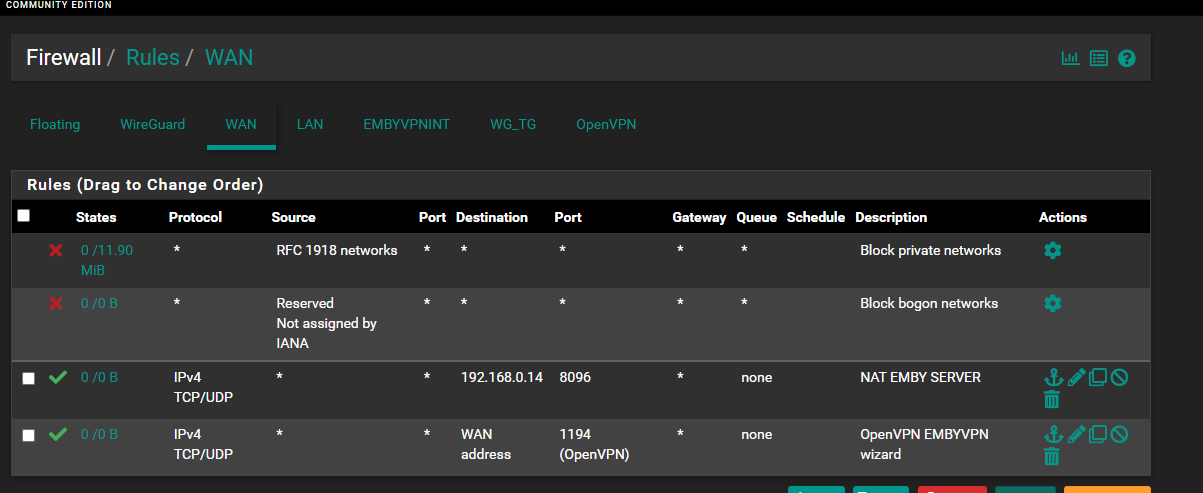
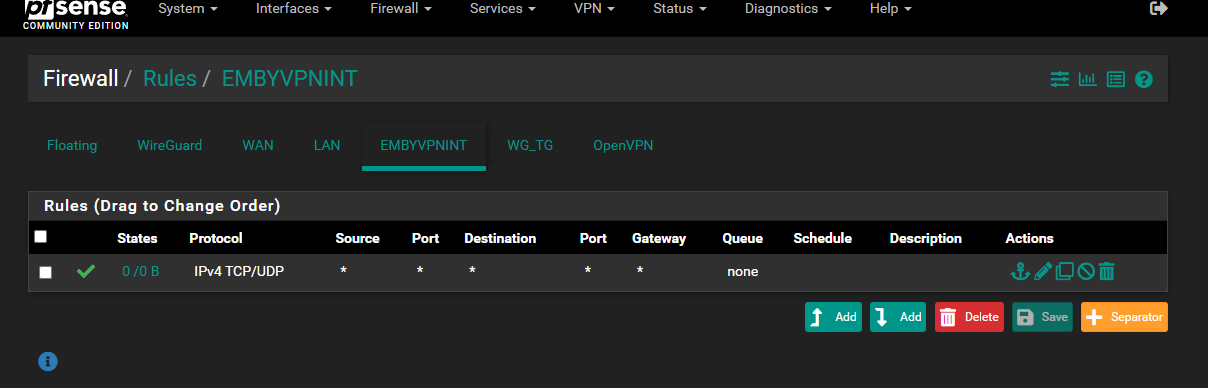
Firewall Rules
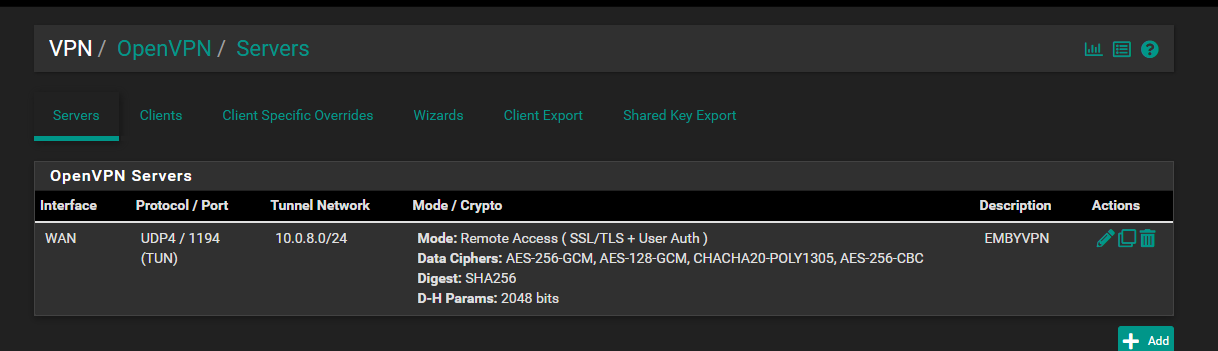
OpenVPN Server
.ovpn
dev tun persist-tun persist-key data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:AES-256-CBC data-ciphers-fallback AES-256-CBC auth SHA256 tls-client client resolv-retry infinite remote 10.132.152.178 1194 udp4 nobind verify-x509-name "EMBY SERVER SC" name auth-user-pass remote-cert-tls server explicit-exit-notifyPlease can someone help point me in the right direction?
-
@dmaj
I am missing information about what is in front of your WAN. Your WAN has obviously a private IP, so is there an ISP router in front of it?If so you have to forward UDP port 1194 on it to the pfSense WAN address.
-
Hello @viragomann
Thanks for posting. No other router exists. Fiber to the home then is converted into RJ45 straight into pfSense network adapter.
-
@dmaj
I see 10.132.152.17 in your config and log as your WAN.
If this is your WAN address there is sadly no way to access it from the internet. It's a private address and between this and the www might be a router who doesn't forward anything to you. -
And I assume if I tried to use my public IP address without my ISP forwarding traffic it would not hit my router? I also tried dynamic DNS service but at the time I was not seeing anything different in my test results, I'll quickly double-check this statement.
-
@dmaj
As mentioned, all I can see is a private address. If there is no ISP router at your location it's at the ISPs site and your WAN IP will not be reachable from the internet.Dynamic DNS services often refuse private IP addresses, but some may accept it.
-
I appreciate your help, it pushed me in the right direction, there must indeed have been my ISP router out in the street box/head office. My WAN was using a private IP address with I assume the public IP address at my ISP router.
I believe that traffic was hitting my Pfsense router but the outbound traffic was not being NAT'd correctly by the ISP router.
Anyway, I upgraded to have a public IP on my router which resolved the issue.