Access the same VLAN on two physical interfaces?
-
My test setup is a pfSense box with four physical interfaces, WAN, LAN0, LAN1, and LAN2 (the LANs are in a bridge), along with two workstations and one managed switch. workstation 1 is on LAN0, workstation 2 is on LAN1, and the managed switch is on LAN2, providing connectivity to the rest of the devices on the network. The switch is VLAN capable, so I have LAN2 set up as a trunk for all my VLANs except the admin VLAN, since nothing on the switch should have access to that anyway. I then set up the admin VLAN on LAN0 for workstation 1 and allowed it access to all the other VLANs. My issue is that I would also like workstation 2 on LAN1 to be a part of the admin VLAN as well, so that it also has access to all the other VLANs.
I cannot figure out how to make a VLAN accessible from multiple physical interfaces on pfSense. From what I've read I have a few options as workarounds:- Create a second admin VLAN, link it to LAN1 for the second workstation, then set rules to allow it to also access all the other VLANs. I don't like this solution because, as I understand, each VLAN gets it's own subnet and I would like the two workstations to be on the same subnet.
- Put the admin VLAN on the switch trunk and plug the workstations into the switch instead of the pfSense box. I don't like this because the switch is 1Gbe, while the workstations and pfSense box are 2.5Gbe, so my connection speed between workstations would drop.
- Buy a managed 2.5Gbe switch, connect it to pfSense (LAN0) and the workstations, and set the admin VLAN on LAN0, allowing the workstations to still connect at 2.5Gbe to each other. I don't like this because that'd be both buying extra hardware (2.5Gbe managed switches are not super cheap) as well as wasting a 2.5Gbe port on the pfSense (since LAN1 would no longer be in use).
Do I have any other options that I've missed for workarounds? Or better yet, is there a way to the admin VLAN accessible on both the LAN0 and LAN1 interfaces?
-
@jblackburn If you have a managed switch, why would you use a bridge?
Search this forum and you'll find out a bridge in pfSense is not a good idea.
Just use the switch as is intended to be used. -
@jarhead exactly a bridge is not actually a switch, does it mimic some things of a switch - ok, but its still not really a switch..
If you want these devices to be on the same vlan anyway, you don't need a 2.5ge managed/smart switch. You can use a 2.5ge dumb switch for this vlan.. Then your current switch for your other vlans into a different interface on pfsense.
have seen multiple 2.5ge 5 port switches for like 100 bucks..
as well as wasting a 2.5Gbe port on the pfSense (since LAN1 would no longer be in use).
How is that exactly - the 2.5ge interface could still be the uplink from your 2.5ge switch and network.
-
@jarhead said in Access the same VLAN on two physical interfaces?:
@jblackburn If you have a managed switch, why would you use a bridge?
Search this forum and you'll find out a bridge in pfSense is not a good idea.
Just use the switch as is intended to be used.Because the switch is 1Gbe and the pfSense box is 2.5Gbe. While it doesn't hit the full 2.5gbps in bridge mode, it actually does get pretty close for sustained loads.
@johnpoz said in Access the same VLAN on two physical interfaces?:
@jarhead exactly a bridge is not actually a switch, does it mimic some things of a switch - ok, but its still not really a switch..
If you want these devices to be on the same vlan anyway, you don't need a 2.5ge managed/smart switch. You can use a 2.5ge dumb switch for this vlan.. Then your current switch for your other vlans into a different interface on pfsense.
have seen multiple 2.5ge 5 port switches for like 100 bucks..
That is true, it wouldn't have to be managed if it's only the admin VLAN, but it still bothers me to simply throw more hardware at a problem that the current hardware should be perfectly capable to solving. If I can bridge two interfaces why can't I put them on the same VLAN? Seems like a weird arbitrary limitation, but maybe there's a good reason for it?
as well as wasting a 2.5Gbe port on the pfSense (since LAN1 would no longer be in use).
How is that exactly - the 2.5ge interface could still be the uplink from your 2.5ge switch and network.
The 2.5Gbe switch could use either LAN0 or LAN1 for its uplink, the other one would be unused.
-
@jblackburn not understanding your problem.. How many ports do you have on this box that is running pfsense, and what are the speeds.
If you want to bridge your network you use for admin.. Go right ahead what does that have to do for your other network/vlans?
Lets say you had 4 ports, all 2.5ge - is your wan 2.5, I could say your wasting that interface then because your not using it to its full potential ;)
But 2 2.5ge ports bridged on your admin network and put your boxes boxes in that network.. Then use the other port for your other network/vlans..
Bridging ports is not a switch make that is for damn sure. Buying a switch for stuff that you want to be on the same network is not throwing money - its doing it correctly!
Why exactly do these 2.5 ge boxes have to be on the same network? You can allow admin from any network if you want, you can allow only admin from a specific IP on any network to access the gui, if you want, etc.
-
@johnpoz said in Access the same VLAN on two physical interfaces?:
@jblackburn not understanding your problem.. How many ports do you have on this box that is running pfsense, and what are the speeds.
It has 4x 2.5Gbe ports, WAN, LAN0, LAN1, and LAN2.
If you want to bridge your network you use for admin.. Go right ahead what does that have to do for your other network/vlans?
Lets say you had 4 ports, all 2.5ge - is your wan 2.5, I could say your wasting that interface then because your not using it to its full potential ;)
It is actually, but by "wasting" I meant that one of the ports would be entirely unused, not that it might be running slower or something. The managed switch is already at 1Gbe anyway.
But 2 2.5ge ports bridged on your admin network and put your boxes boxes in that network.. Then use the other port for your other network/vlans..
How would I go about putting two ports on the admin network if I can't put two ports on the admin VLAN?
Bridging ports is not a switch make that is for damn sure. Buying a switch for stuff that you want to be on the same network is not throwing money - its doing it correctly!
Yes, but with the hardware I have, a bridge is perfectly capable of 'switching' traffic across two ports at close to 2.5gbps.
Why exactly do these 2.5 ge boxes have to be on the same network? You can allow admin from any network if you want, you can allow only admin from a specific IP on any network to access the gui, if you want, etc.
Sorry, by admin I mean an admin VLAN which has access to the other VLANs, not just access to the pfSense GUI. The VLANs I currently have set up are admin, home, and iot. Admin has access to the internet, home VLAN, and iot VLAN. Home has access to internet and iot VLAN. And iot has access to just the internet.
-
@jblackburn said in Access the same VLAN on two physical interfaces?:
if I can't put two ports on the admin VLAN?
It is quite easy to bridge two interfaces and put them on the same network.. That is what a bridge is.. Your the one trying to use it for multiple vlan and put other networks at the same time, etc.. Yeah that is going to be problematic..
So why is this not viable in your scenario..
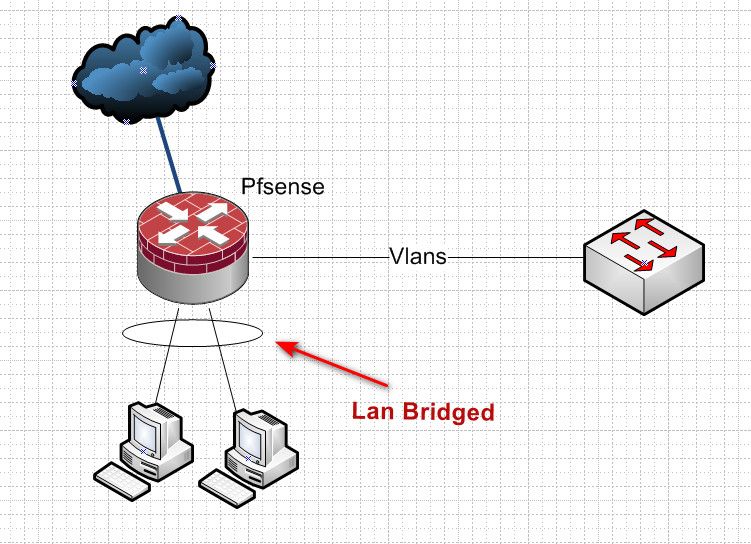
You bridge an interface to your lan (anti lockout, admin network) you put your 2 devices there. And then put your other devices on how ever many you want vlans and uplink them to the other interface from your managed switch.. What your going to have a problem with is trying to run vlans over a bridge..
If you had a dumb 2.5ge switch you could even do something like this to leverage your managed switch and put stuff on that switch in your admin vlan
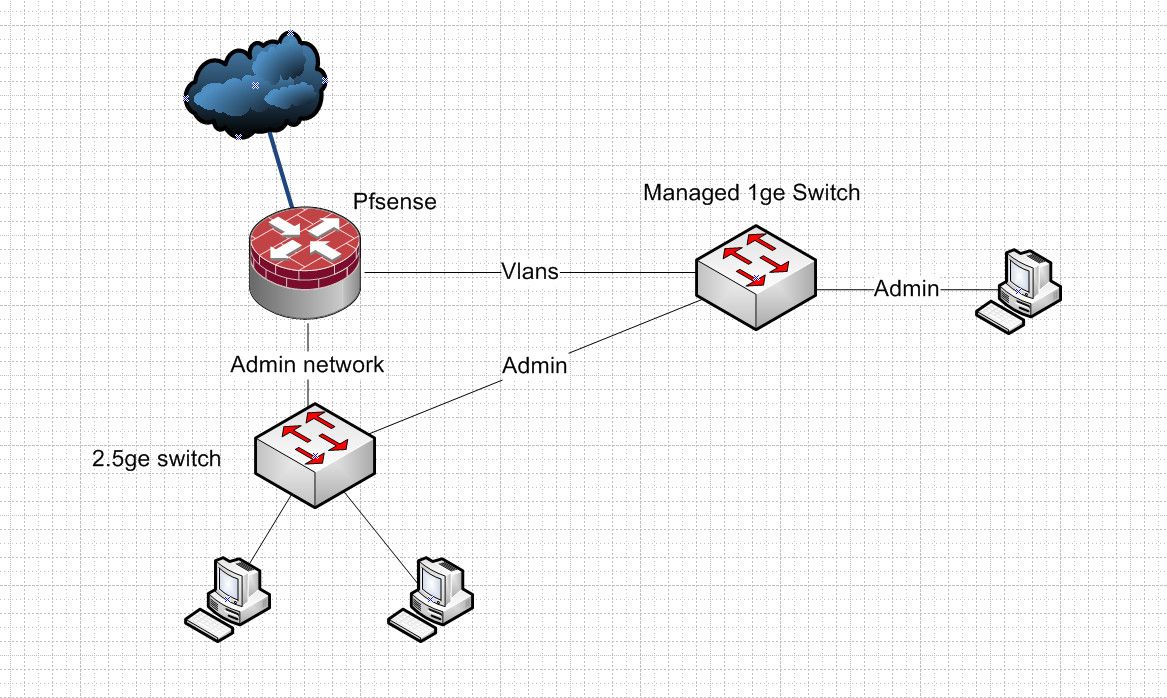
And not a bridge in sight - you could also leverage say another interface to your managed switch with lacp to have 2x1 into your pfsense for your vlans, etc. So you know your not "wasting" a port ;) Lots of stuff you could do really.
Or you could break out a vlan to its own uplink - depends on what sort of traffic you have between vlans, etc.
-
Access the same VLAN on two physical interfaces?
-
Make both ports being a member of that vlan you want
to give access to. Most common way as I know it. -
"Some one" route between the them (pfSense or the Switch) and you set up two vlans with different subnet like;
- VLANx = 192.168.178.0/24
- VLANy = 192.178.168.0/24
EDIT:
Route where you can do it, bridge where you must do it
-
-
@johnpoz I see now, ok that seems like a decent solution. I still don't understand why you can't just assign a VLAN to a bridge instead of just a single physical interface, but for now I guess I'll just accept that's the way it is.
-
@jblackburn A bridge is a medium that allows two different types of networking protocols to communicate (ether and virtual, WiFi ether switch and router... etc) at the layer 2 level.
The intended use of a bridge is:
- Physical iface (Ether, WiFi, DSL...) <-> 2.Specific VLAN tag traffic iface (on the physical NIC) <-> 3. Switch <-> 4.Bridge <-> 5. Other iface
A switch is different in that it is an actual electronic switching circuit. A bridge doesn't switch anything by itself, it needs software to forward packets.