How to route LAN traffic thru OVPN
-
Hello guys,
I have the following network infra:
1 X ROUTER (192.168.10.1)
1 X ESXI server ( WAN_ESX 192.168.10.4) connected to ROUTER with 2 vSwitches: 1 assigned to WAN_ESX and 1 assigned to LAN_PFS pfSense.
On the ESXI server i have installed as a virtual machine pfSense 2.6.0 wich has 2 NICs: WAN_PFS (192.168.10.5) and LAN_PFS (192.168.15.1) with DHCP enabled.
1 X windows 10 virtual machine with LAN_WIN (192.168.15.11) connected to LAN_PFS.
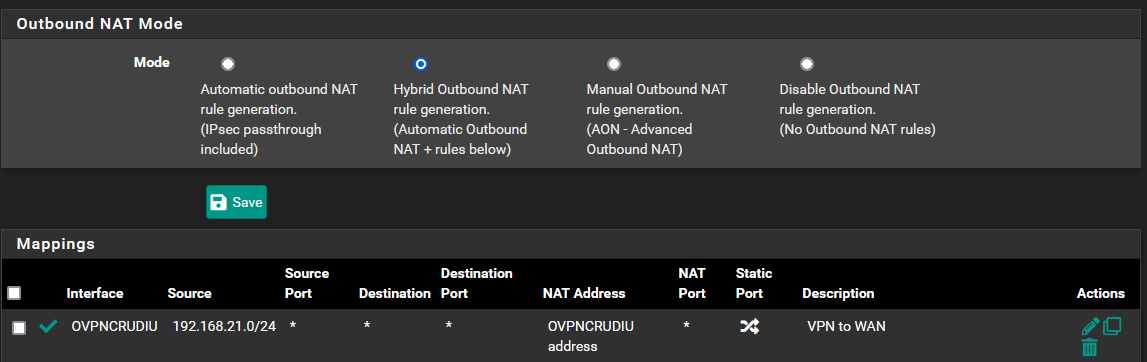
I managed to setup successfully 1 OVPN client to remote locations (ping to remote location LAN works) and I want to route all LAN_WIN in/out trafic thru OVPN connection.I tried to setup FW LAN rule by alow trafic from LAN_WIN to ANY using OVPN GW and Outbound NAT Mode is set to Hybrid.
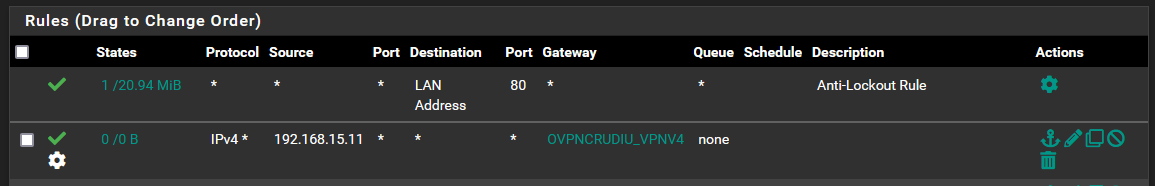
And FW rule on OVPN connection is also enabled.
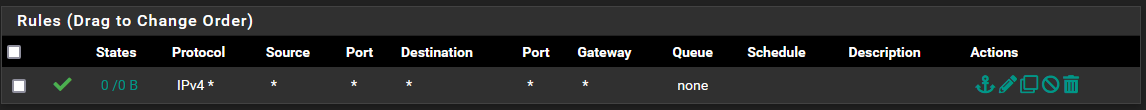
But ... seems that is not working, i have NO ping to remote LAN ... NO ping to google.
Could anyone have any ideea maibey some route missing ?!Thank you.
-
@ispasoiumircea
In the outbound NAT rule the source has to be your LAN, so 192.168.15.0/24 presumably.Consider that the policy routing rule on LAN directs all matching packets to the OpenVPN server. Hence it doesn't allow access to any internal destinations like DNS from this device.
This can be done, but you need to use a DNS server on the concerned machine, which is accessible over the VPN. If there is any, you can simply forward DNS requests with a port forwarding rule on pfSense and need nothing to change on the device itself.
Otherwise add an additional rule to pass internal traffic above of the policy routing rule.The rule on the OpenVPN is only needed for inbound traffic. But I guess, you don't want any, so you can remove it.
-
@viragomann said in How to route LAN traffic thru OVPN:
@ispasoiumircea
In the outbound NAT rule the source has to be your LAN, so 192.168.15.0/24 presumably.Consider that the policy routing rule on LAN directs all matching packets to the OpenVPN server. Hence it doesn't allow access to any internal destinations like DNS from this device.
This can be done, but you need to use a DNS server on the concerned machine, which is accessible over the VPN. If there is any, you can simply forward DNS requests with a port forwarding rule on pfSense and need nothing to change on the device itself.
Otherwise add an additional rule to pass internal traffic above of the policy routing rule.The rule on the OpenVPN is only needed for inbound traffic. But I guess, you don't want any, so you can remove it.
Hello,
Thank you. Its worked just adding outbound NAT rule from LAN to VPN.
Good day,