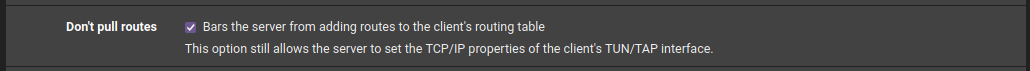
-
@viragomann said in Routing a single VLAN to a VPN:
@04cc40 said in Routing a single VLAN to a VPN:
"Don't pull routes" is already checked as per PIA instructions (not the guide itself, but a thread on their forum).
If this is checked all devices should go out to the default gateway as long as they are not policy routed.
And as your gateways screenshot shows, WAN is your default gateway. Maybe was the VPN client disconnected, as you took it?VPN was up.
Then add a policy routing rule to the subnet you want to use the VPN for none-RFC 1918 destinations to direct the packets to the VPN gateway.
Where can I read up on achieving this?
Just noticed that you did this already:
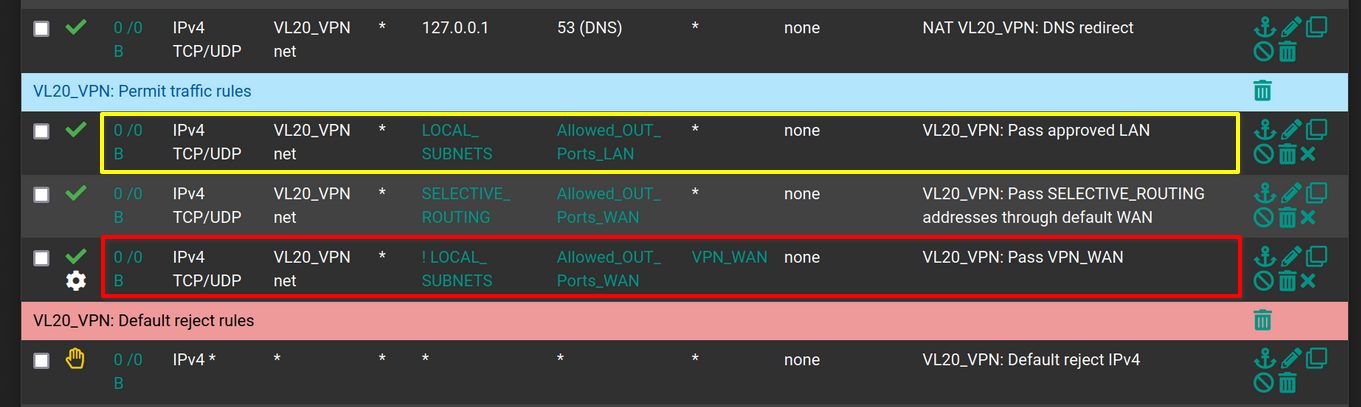
The red one.
But this rule will never be applied, because the yellow one matches before to the same traffic. So it is applied an following rules are ignored.
You have to change their positions to get the policy routing to work.I'll try changing the order and report back.
This let me assume that all your traffic went out to WAN instead of VPN as you said in your first post above.
The problem is the other way around, all my VLANS are going out through the VPN when I want only a specific VLAN to be tunneled.
-
@04cc40 said in Routing a single VLAN to a VPN:
The problem is the other way around, all my VLANS are going out through the VPN when I want only a specific VLAN to be tunneled.
Yes, I noticed that. But this makes no sense to me. This sign indicate the actual default gateway:
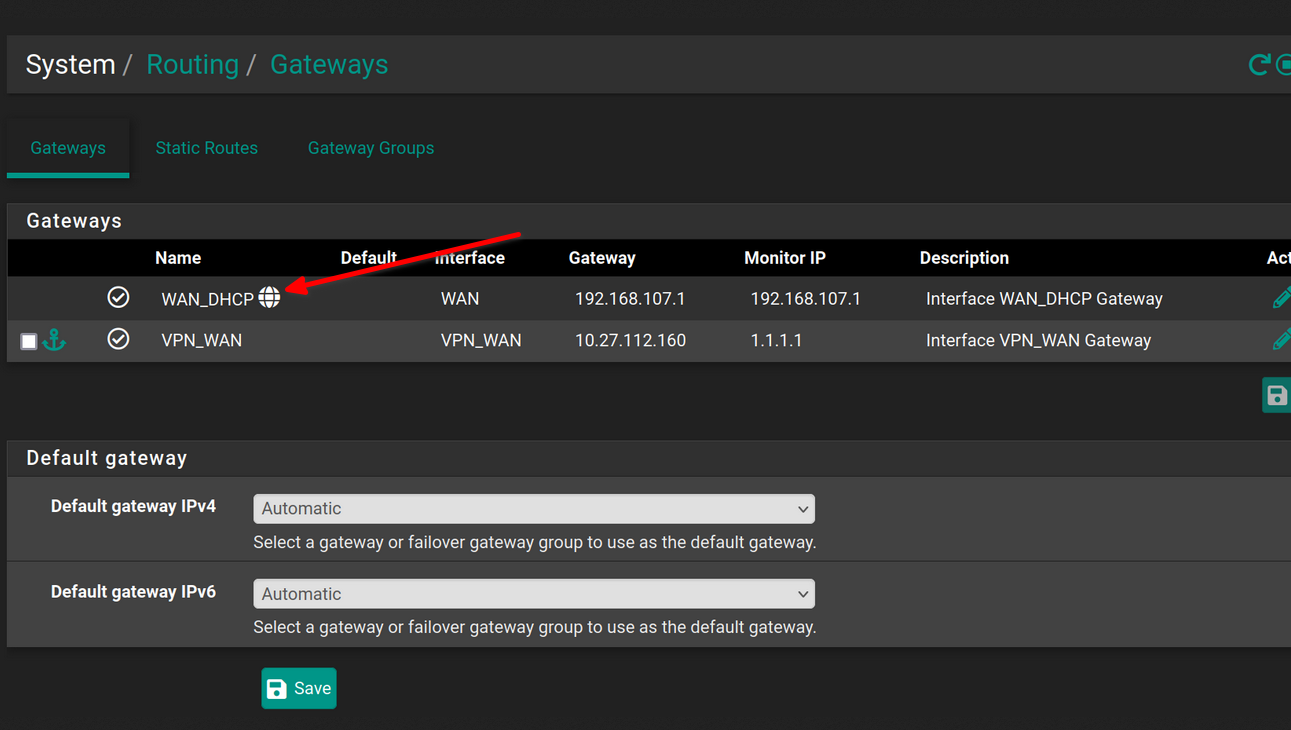
So if this is next to the WAN gateway, I expect that the traffic goes out to WAN.
Below you can select the default gateway manually. But as this is also in automatic mode, it shouldn't use the VPN. -
@viragomann I am partially glad this makes no sense to someone else.
I have changed the order of the rules and the problem persists. For example VLAN_30 is supposed to be a clearnet and is not specified to be tunneled through the VPN_WAN gateway:

VPN connection is established:
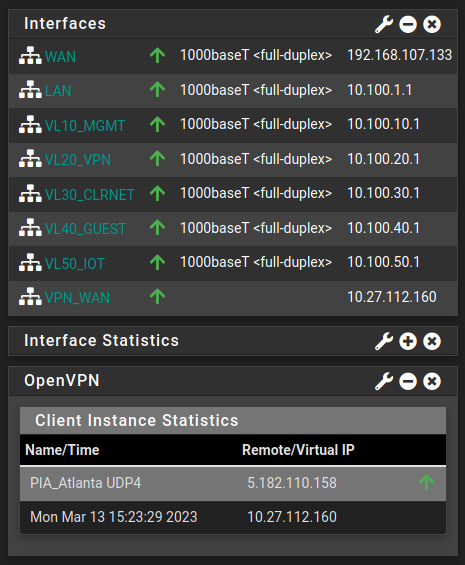
My computer is connected to an SSID assigned to VLAN_30 and is being assigned an IP within that subnet:
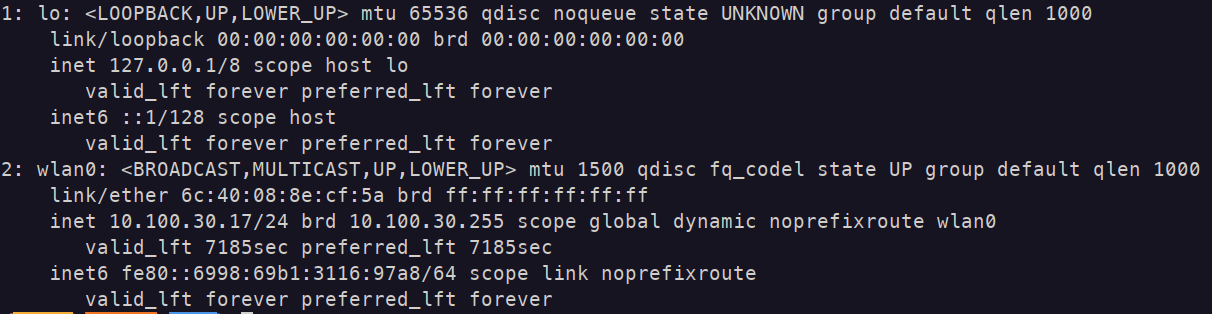
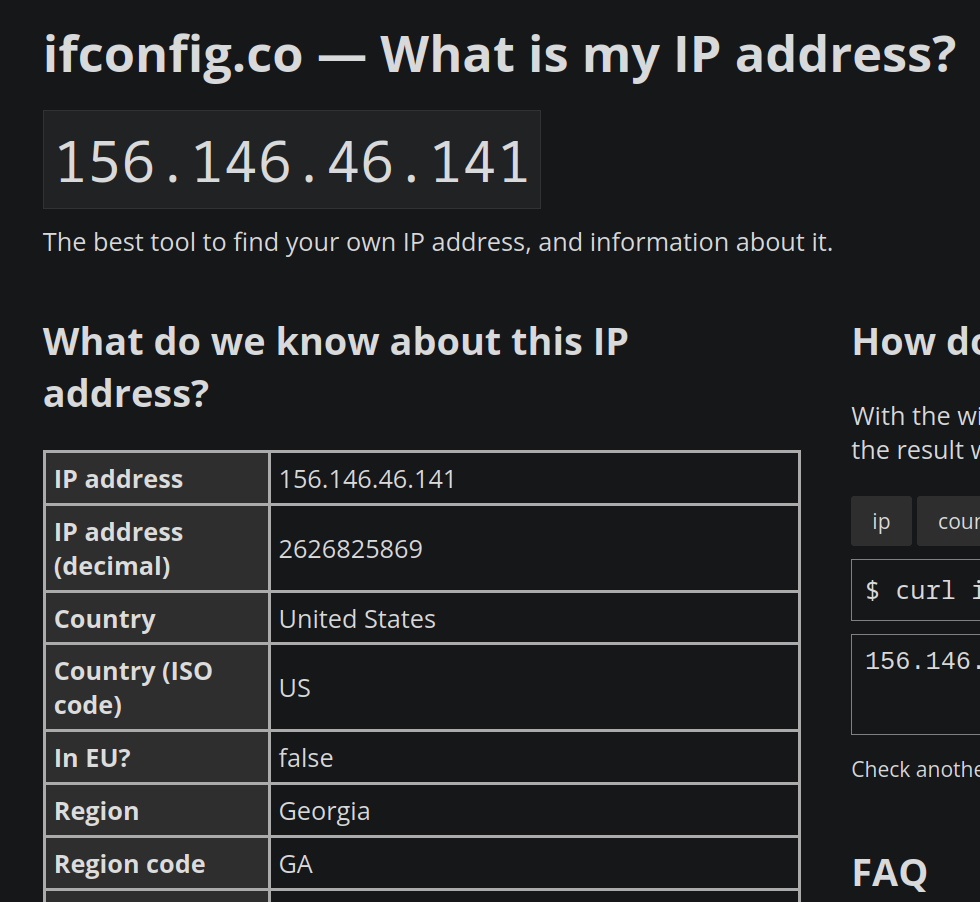
But still, my public IP is one linked to the VPN (PIA Atlanta server in Georgia) :
-
@04cc40 Is this ticked in your pfsense openvpn client configuration?
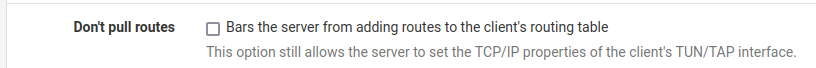
-
-
@04cc40 Then you may have a mess in Outbound NAT I guess.
-
@04cc40 said in Routing a single VLAN to a VPN:
My problem is that I want only a specific VLAN to pass through the VPN
You don't pass a VLAN through a VPN, you route the subnet.
-
Sorry I "misspoke".
-
@bob-dig
I decided to reset the appliance and redo all the config. It seems to be working as expected now, but I guess I'll never know where I f'ed up the first time.
-
I found this walk-through by Lawrence at Lawrence Systems. Goes through the setup of exactly what you want to achieve and explains why settings should be where they are and what simple mistakes can catch you out. I know you have it working now but it may help you to discover what the error was or it could help someone with the same problem in the future:
https://youtu.be/ulRgecz0UsQ
-
@i-t-_lee Thanks. I actually switched to pfSense around 3 years ago because of his channel. I also switched to Unifi switches and AP's because of him. I did follow the nguvu guide because I'd rather be reading than pause-playing a video on YT, but you're right, his channel is a great resource.
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.