could use some help with firewall/nat rules?
-
@comet424 if your going to policy route, you need a rule above that allows the traffic... Highly unlikely your vpn, or even yoru wan gateway is going to be able to get to one of your other local networks.
https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.html#bypassing-policy-routing
You should only need to outbound nat to your other networks, if for example your camera doesn't have a gateway, so doesn't know how to answer your client that is on some other of your local networks.
-
@johnpoz
ok not 100% sure what you mean i did for cameras in the dhcp server i set gateway to 192.168.10.1 and same for iot 192.168.20.1 etcand i did do the !local_subnets and i tried private networks i have the names.. of the networks.. but it didnt work.
as i watched videos it says doing ! it allows internet but doesnt allow access to the other networksbut where i finding the problem is under LAN if the gateway is set to * then i can access the cameras and IOT but if i change the gateway to VPN_group its 2 nordvpn clients i set up for fail over.. well when i set it to that then i can no longer ping the IOT and i only partial cameras kinda work on the Cameras net.. so thats where i lost what to do and change just changing from * to vpn_group as a gateway stops all network activity
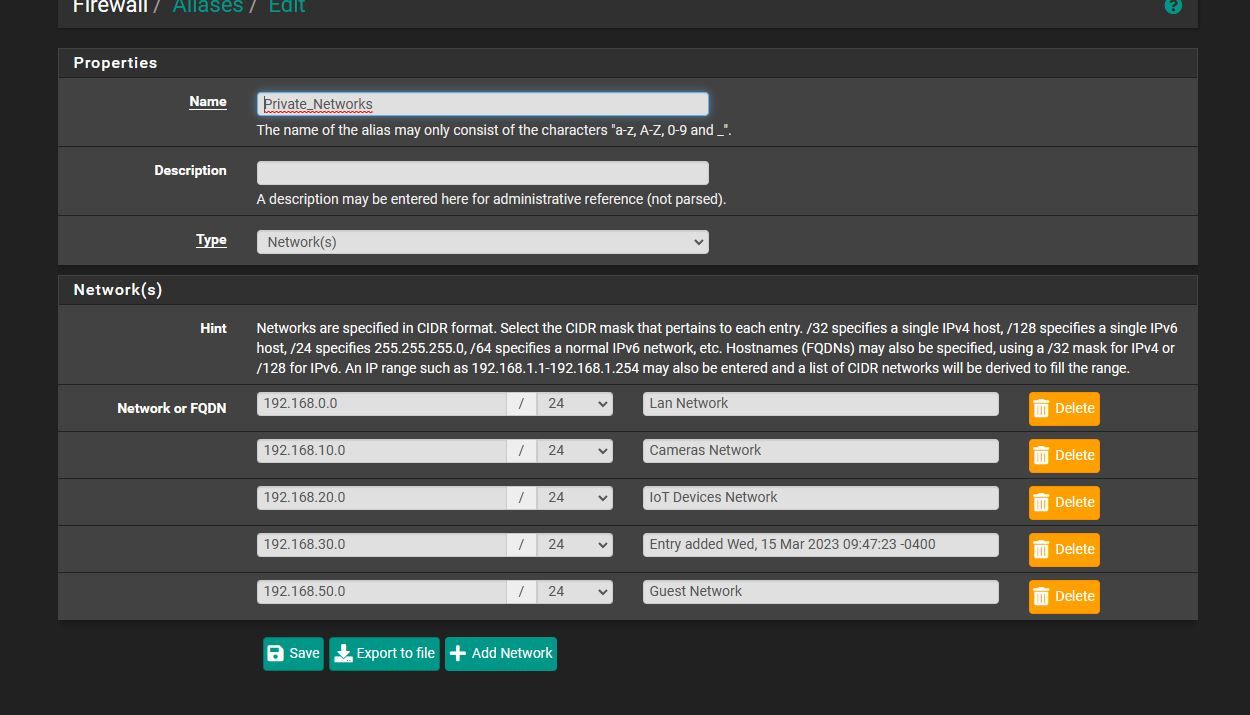
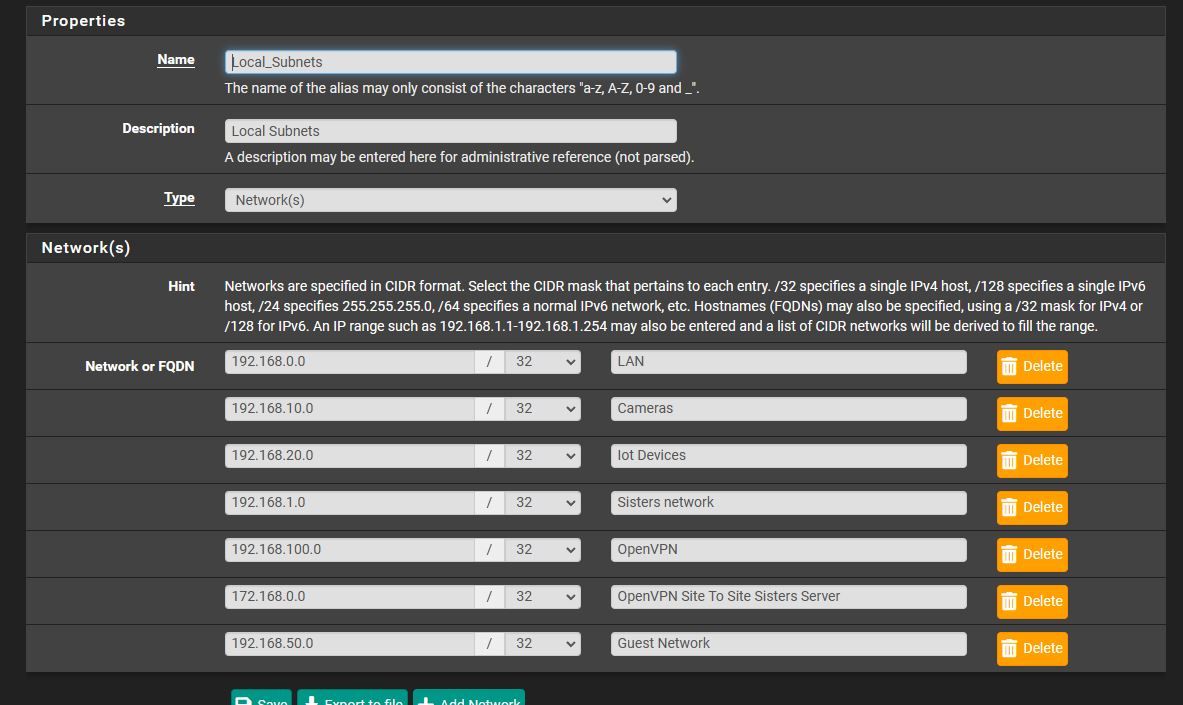
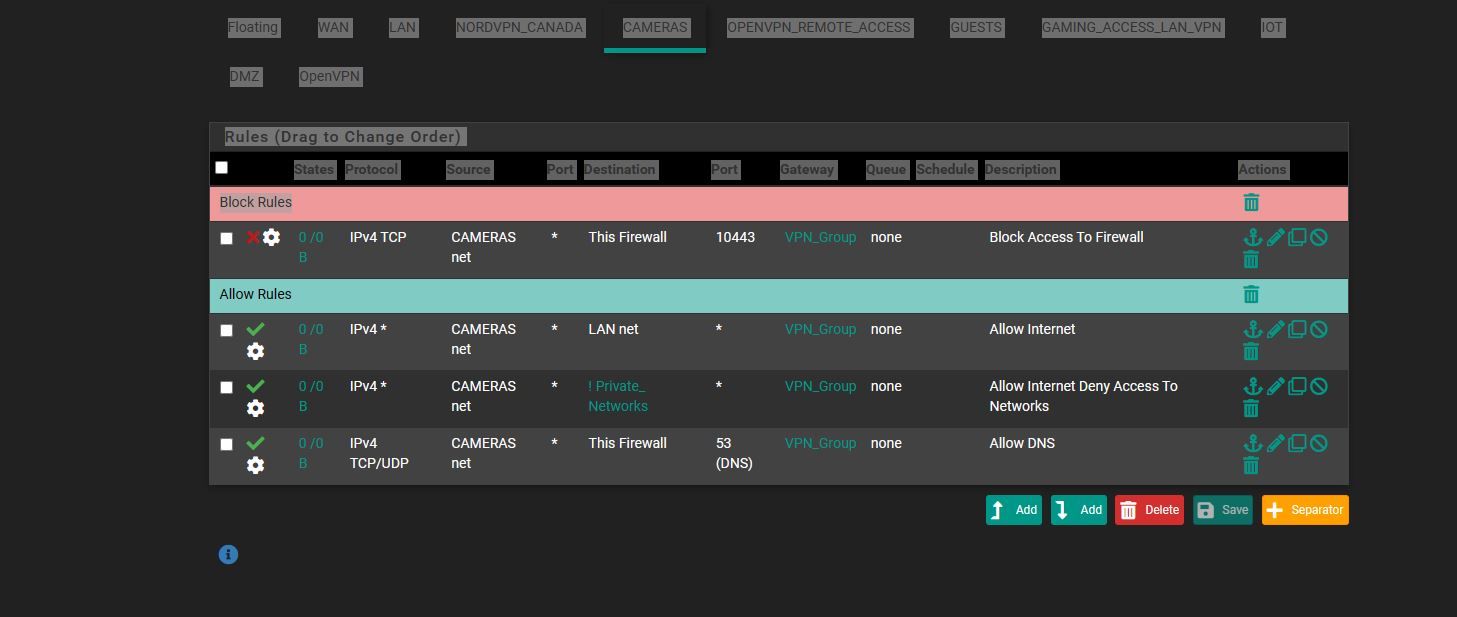
i also noticed i gotta make a fix.. if i do !local_subnets or !_private_networks if its camera network and the camera is in either one i also cant access cameras or so cancels itself out i guess.
-
i guess what i confused about is why does the gateway matter?
if its set to WAN * it works you changed it to vpn_group i have 2 vpn clients it no longer works i thought the gateway was for the internet not for internal networking
-
@comet424 said in could use some help with firewall/nat rules?:
i guess what i confused about is why does the gateway matter?
Because how exactly does your vpn get to one of your other segments, if you shove traffic down the vpn?
So yes it matters.. Why would want/need traffic to go out your vpn or wan connection to get to another segment directly connected to pfsense.,
That is fine if you want traffic not going to some other segment on your network to go out a vpn, but you need a rule above that that says you can go to the other network without shoving it out a gateway.
When you set a gateway on a rule, you take out of the mix any routes that pfsense knows about, and traffic that matches that rule goes out the gateway set.. It gets shoved out that gateway, without looking at pfsense routing table that says oh 192.168.10.x is locally connected to my optX interface.
Pfsense oh you match this rule go get sent to this gateway...
So you need a rule before you policy route it out that gateway, that says oh you can go to 192.168.10.x - that is locally connected to my optX interface let me send the traffic out that interface, via my routing table.
-
@johnpoz
trying to post a reply but its telling me its spam trying to edit my post to figure what word it is -
@comet424 this rule doesn't even make any sense
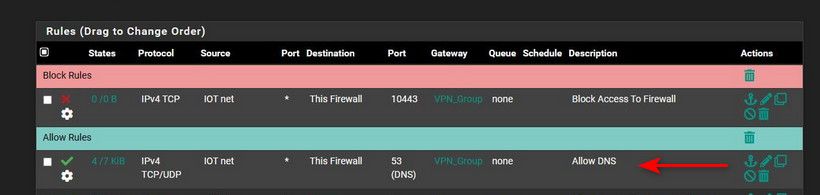
if your client on your iot net is trying to talk to an IP on pfsense "this firewall" why would you shove it down your vpn group gateway?
-
@johnpoz not 100% sure how to make that rule
is that like this? ive tried this and this doesnt work but im sure its wrong
do you have an example i can go by
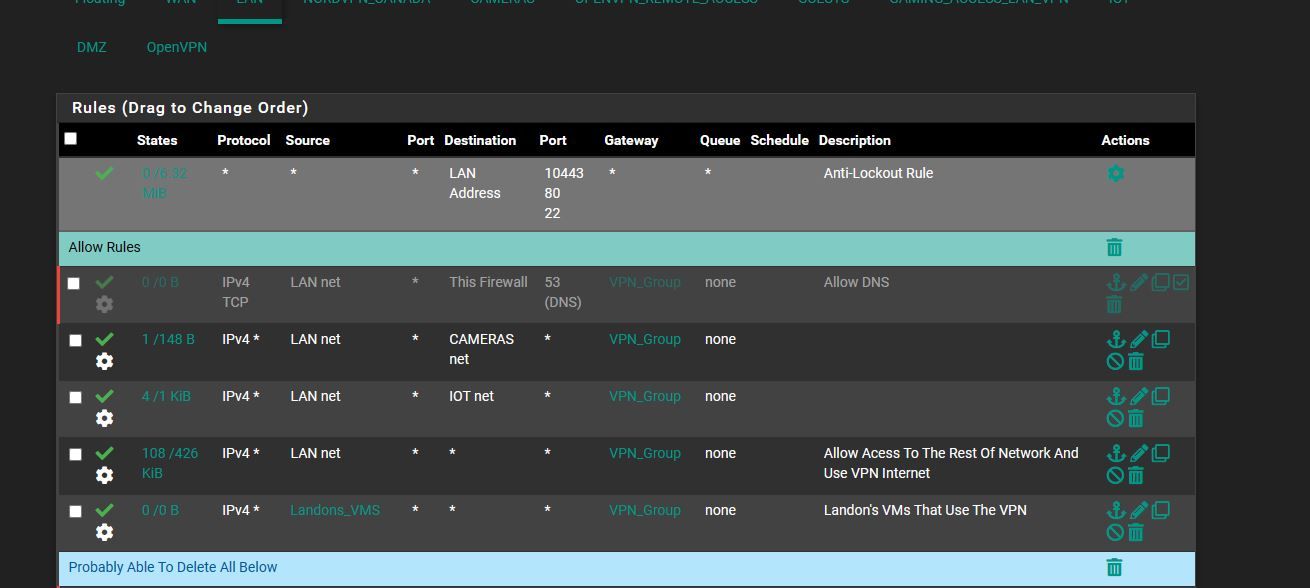
@johnpoz
was part of the video i watched.. if you want DNS on your vlan thats what you enter in.
and cuz i dont know from what i saw- = WAN
so i dont want IOT to use WAN at all .. since * is default WAN so my understanding is i dont want IOT to ever see WAN so thats why i tell it do not use WAN
thats my understanding
- = WAN
-
all i know is i know if i do * then nordvpn website says i not secure tells me my ip is leaking so but the network works and when i try to change the default gateway to vpn_group
so its forcedi did do a Reject that lan.net cant use wan address and wan net but i found it didnt help unless i didnt wait long enough
but if there is pictures to learn better or a dummies book explantion style be great.. i appreciate the help so far
-
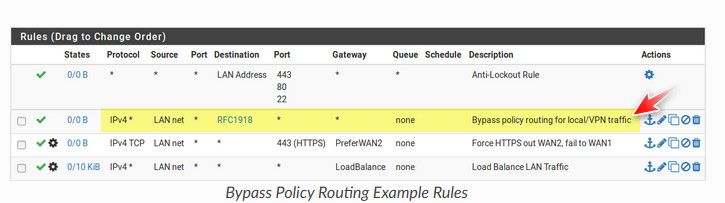
@comet424 if your want your clients to use your vpn for dns that is fine - but the destination wouldn't be this firewall.. Point the clients directly to some outside dns, or your vpn dns..
If you want lan net to get to say your camera net, put a rule above where you shove it out your vpn that allows that.
Rules are evaluated top down, first rule to trigger wins, no other rules are looked at..
Its pretty straight forward in the link I provided..
-
@johnpoz ya i had to re read it several times.. i think i got it working... but whats weird i not sure
if you test dnsleaktest website.. the LAN picks up 4 dns's but the IOT picks up just 1 dns
figured the LAN would only be picking up the one dns too... dunnook so if first rule wins doesnt that mean it goes out the default gateway of wan.. or is that the acception to the rule?
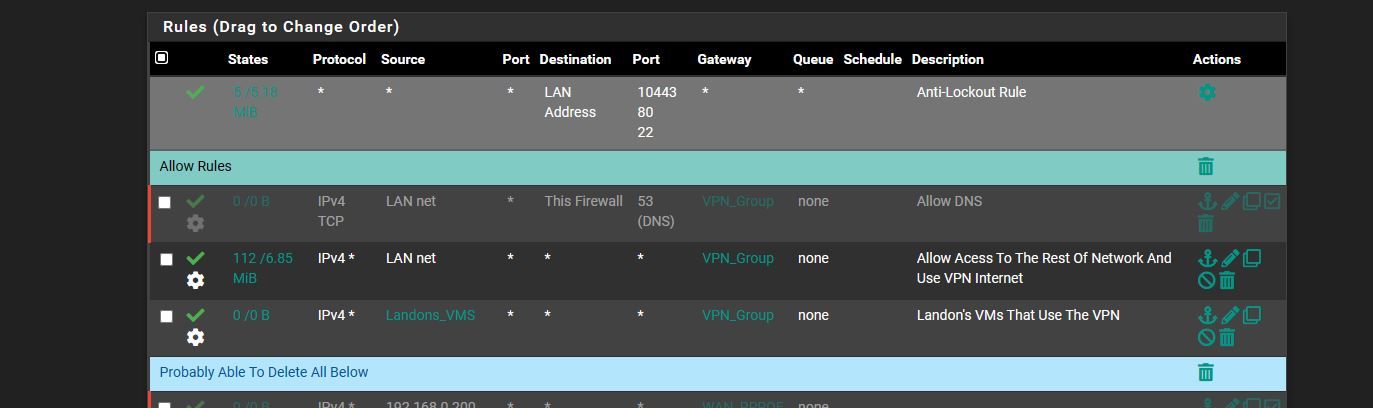
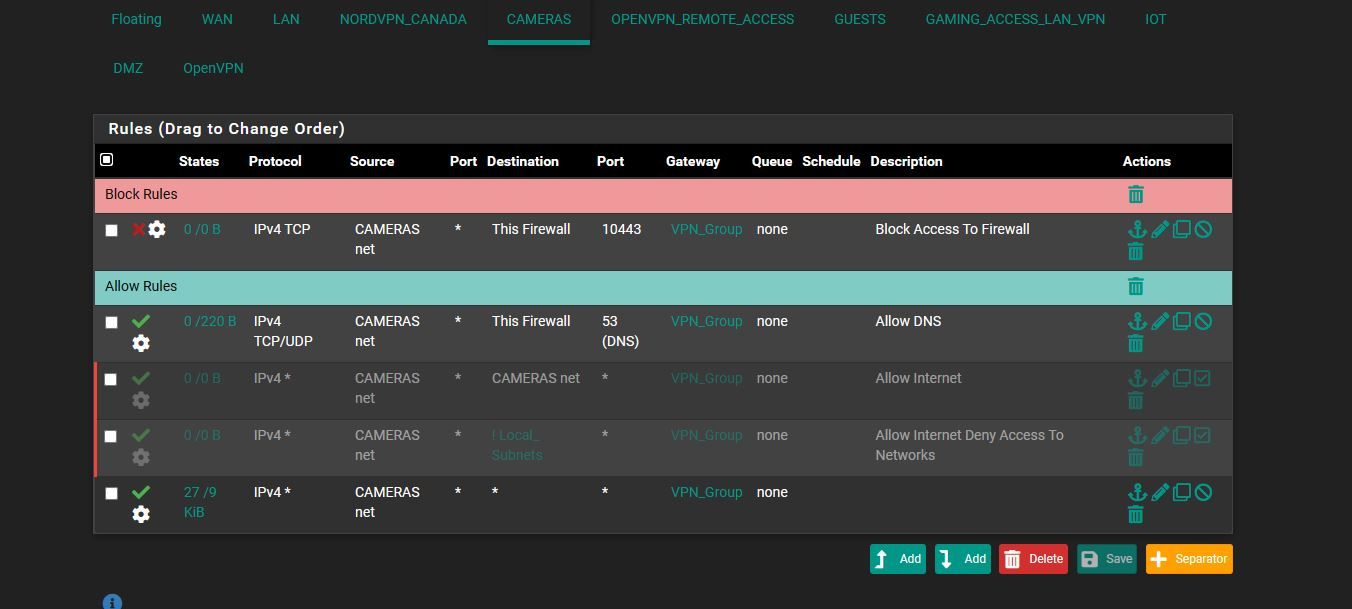
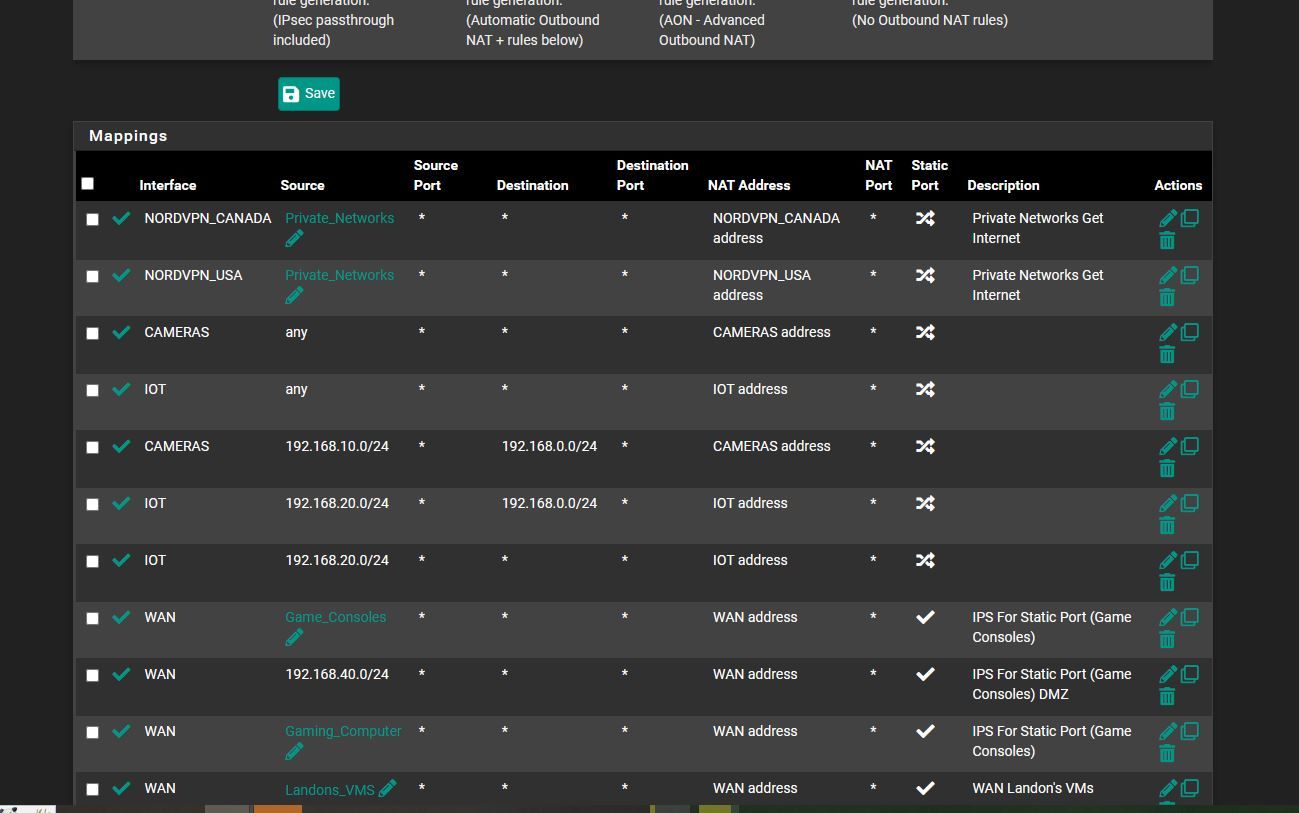
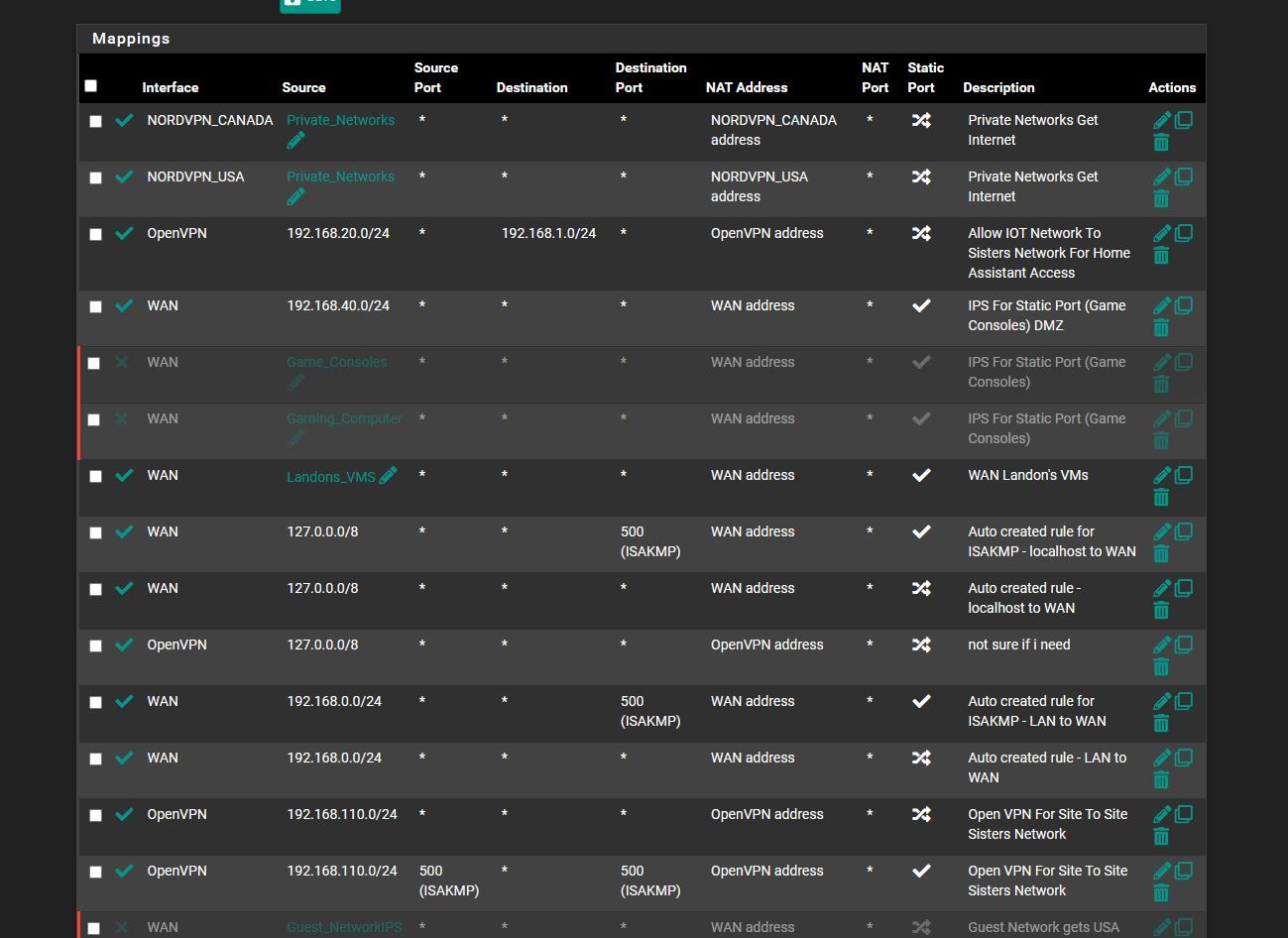
and ok i added block rules.. in the pics below... is it irrelivant to do that.. or it wont block because the other is above it..
now i re tried things i think its way it should be.. i dont want the iot to access anything other then internet.. and same for cameras... now do i need to add the like
IOT * private_network * * none do i need to add it for them or is the current way okhere the pics.. and is the NAT looking ok too?
oh and should block rules then should be before Allow rules then right .. not after then cuz the allow rule over writes the block rule then
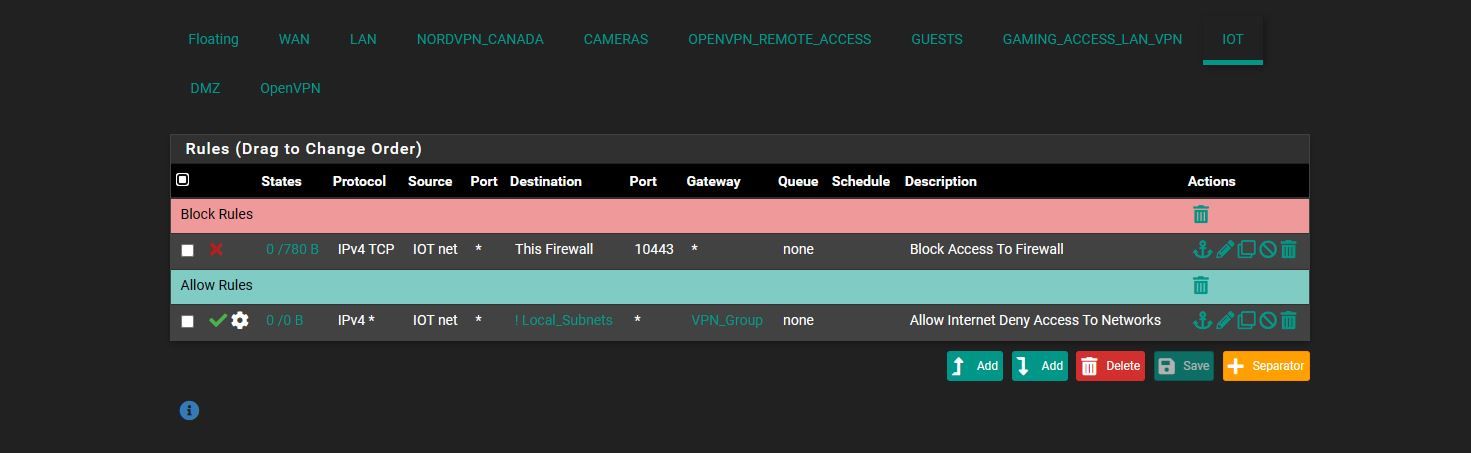
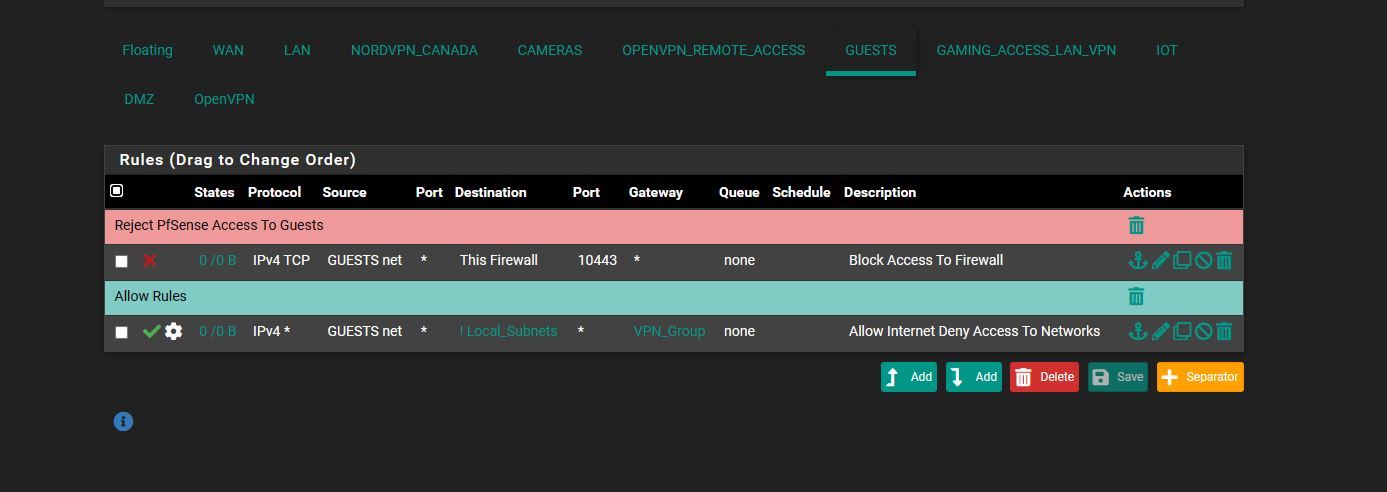
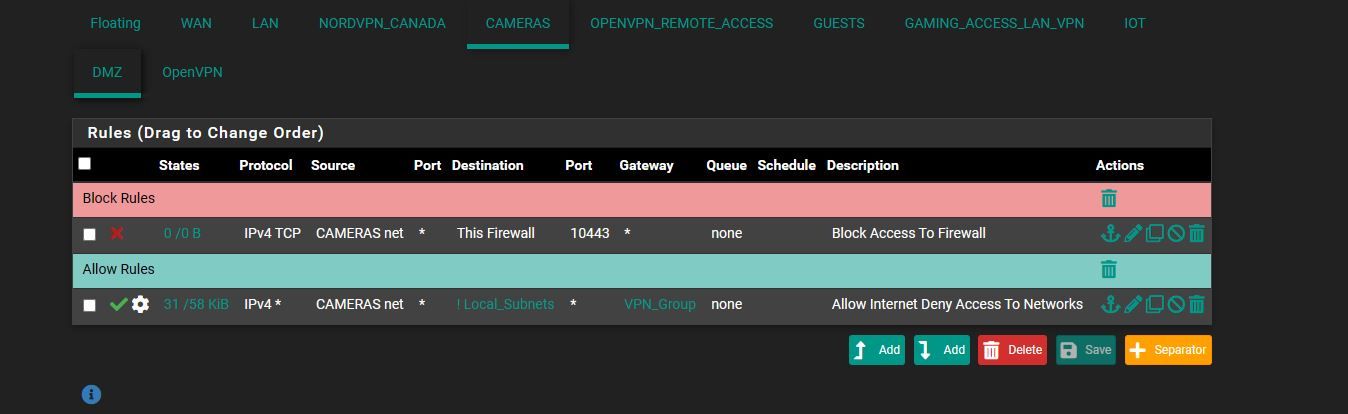
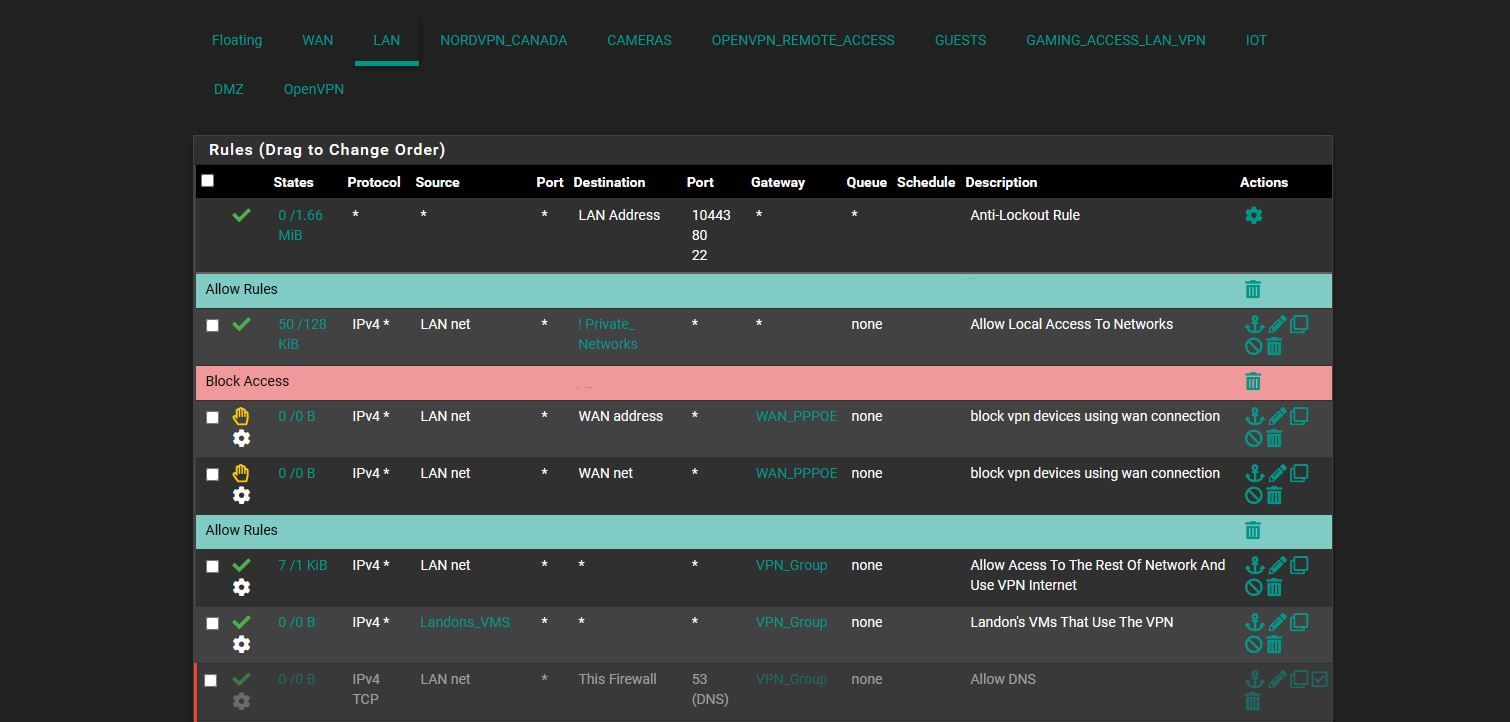
update i unchecked that invert you see on the LAN
-
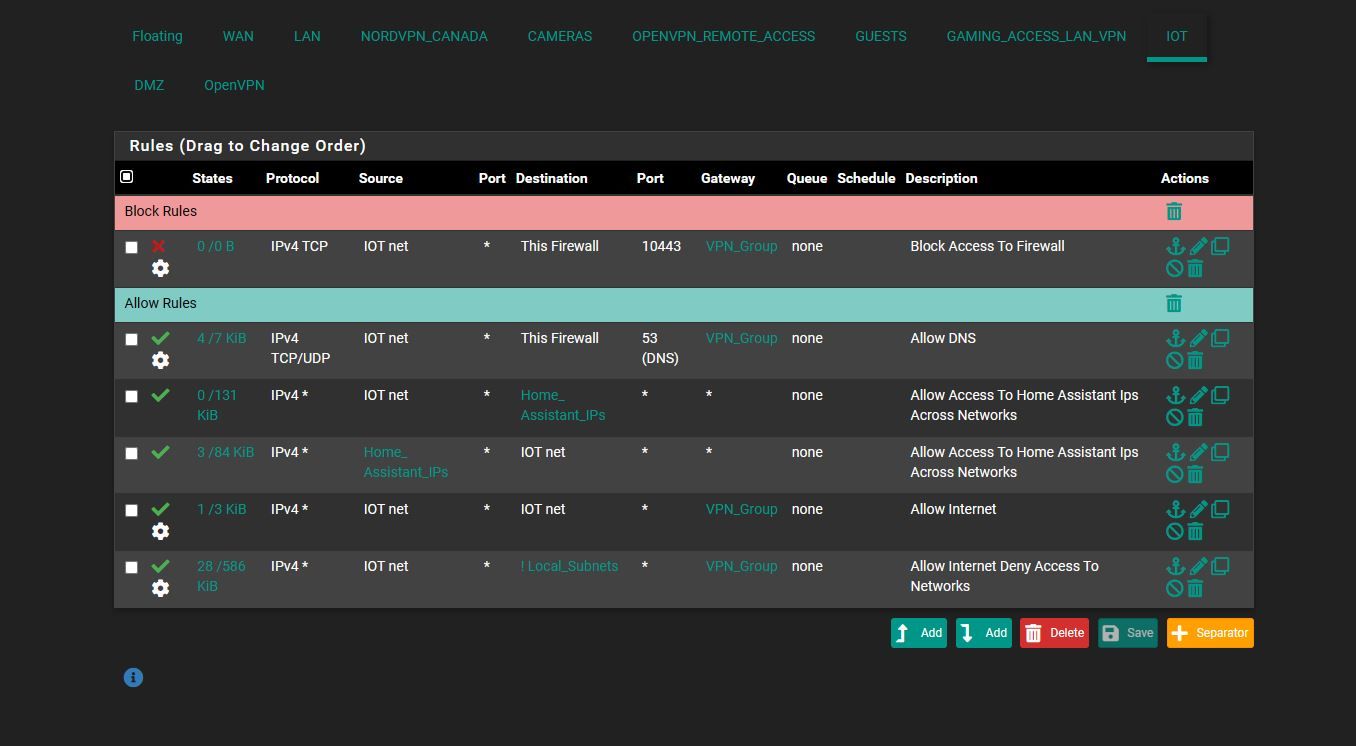
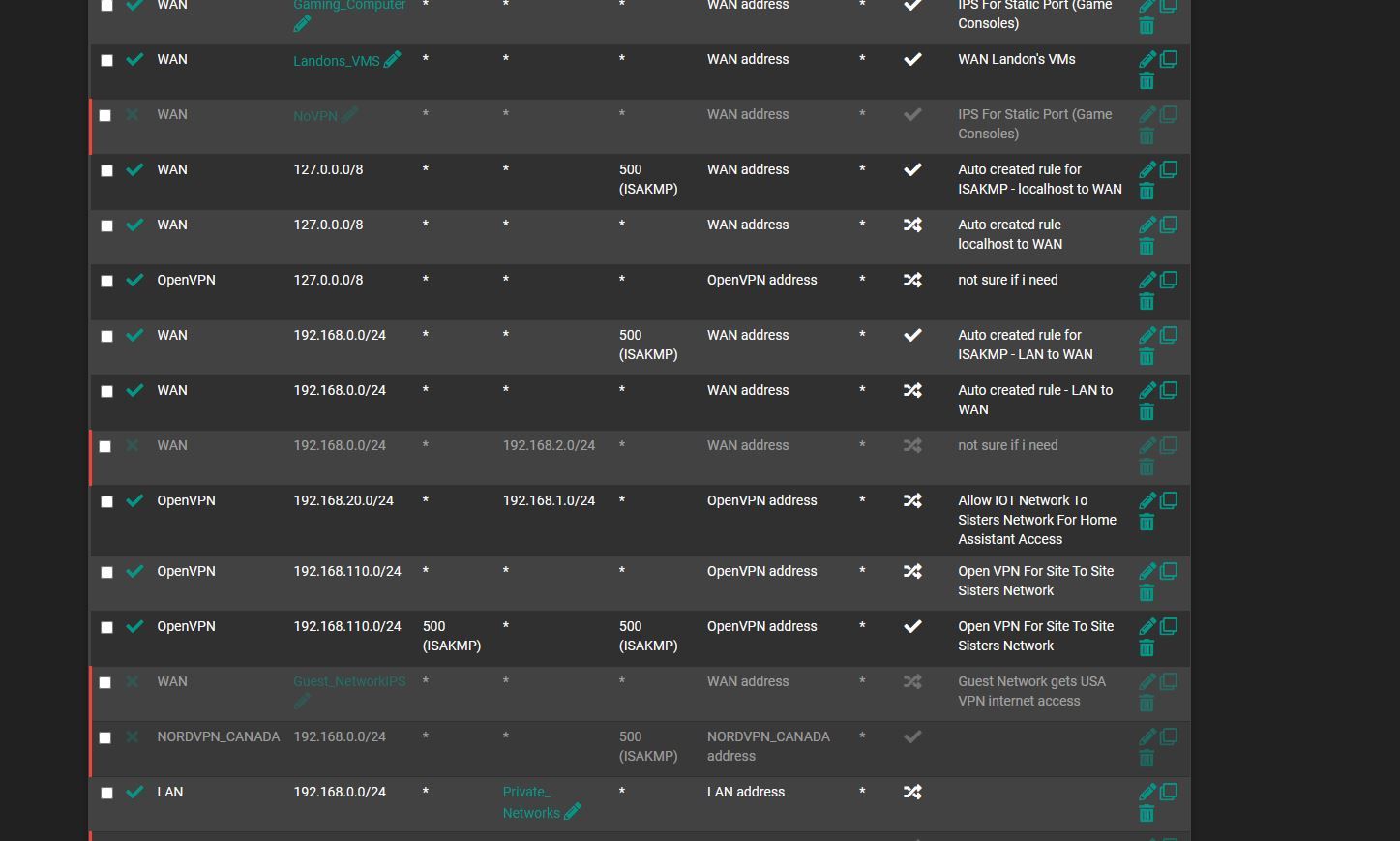
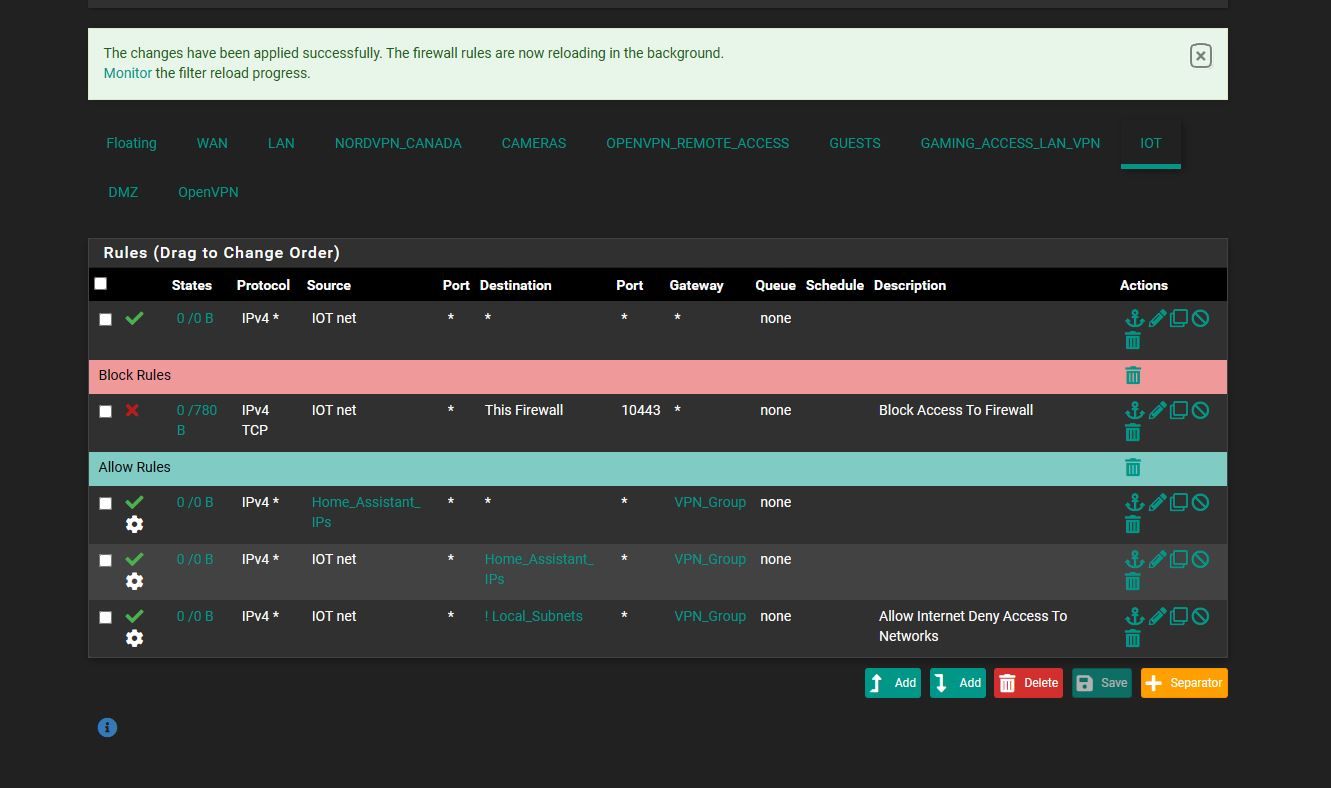
i think this is correct for IOT let me know
first line saying to enable the bypass rule
2nd line block firewall access
next is to allow home assistant ips back and forth
and last is allow internet but deny the rest of the network is that correct way ?
correct order?
-
@comet424 What part are you not understanding about routing traffic out your vpn gateway?
Where are those home_assistant_ips if they are on the iot network that 2nd allow rule is pointless. And if they are and yo want them to get to other stuff on your local networks how is routing them out your vpn going to get there?
And then all of those rules below the 1st one are completely pointless anyway.. Because that is the 1st rule and its an any any - so none of those other rules mean anything..
-
@johnpoz
ah ok as for my home assistant ips
they are
192.168.0.12
192.168.10.12
192.168.20.12
those are the vlants to the main home assistant
then
192.168.0.10 is anotherand then on my sisters network i do the openvpn site to site
its
192.168.1.12and what i didnt understand is if the first rule says use default gate way which is wan then the 2nd rule saying use the the vpn the wan superceeds using vpn thats what i ment..
im having troubles i going to play around and ok good i can delete the grayed out ones.. wasnt sure.. i going to try some things later..
i learning by trying... (: i appreciate the help so far.. least i can access the networks from LAN...
i just never figured why i get more dns results on LAN then the IOT but going to play a bit and see how i do (: im sure ill have questions tomorow.. so i really appreciated the help so far