oVPN client: TLS key not valid
-
@johnpoz
Many thanksI am following the instructions at https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-s2s-tls.html#recipe-openvpn-s2s-tls-examplesettings to configure a remote pfsense behind cgnat to connect to their main office pfsense.
In there it says:
The next task is to export the certificates and keys which the client requires when connecting to the OpenVPN server.Navigate to System > Cert Manager, CAs tab
Click fa-certificate on the row for the CA to export its certificate
Navigate to System > Cert Manager, Certificates tab
Click fa-certificate on the row for each client certificate to export the certificates
Click fa-key on the row for each client certificate to export the private key for the client certificates.When I slavishly copy the steps and then paste in the key obtained in the last step into the remote client ovpn setup I get the error.
-
@orangehand not sure what your exporting, but the tls key would not be in the cert manager.. But clicking the export cert and or key would export a .crt or .key file that you can open with any text editor..
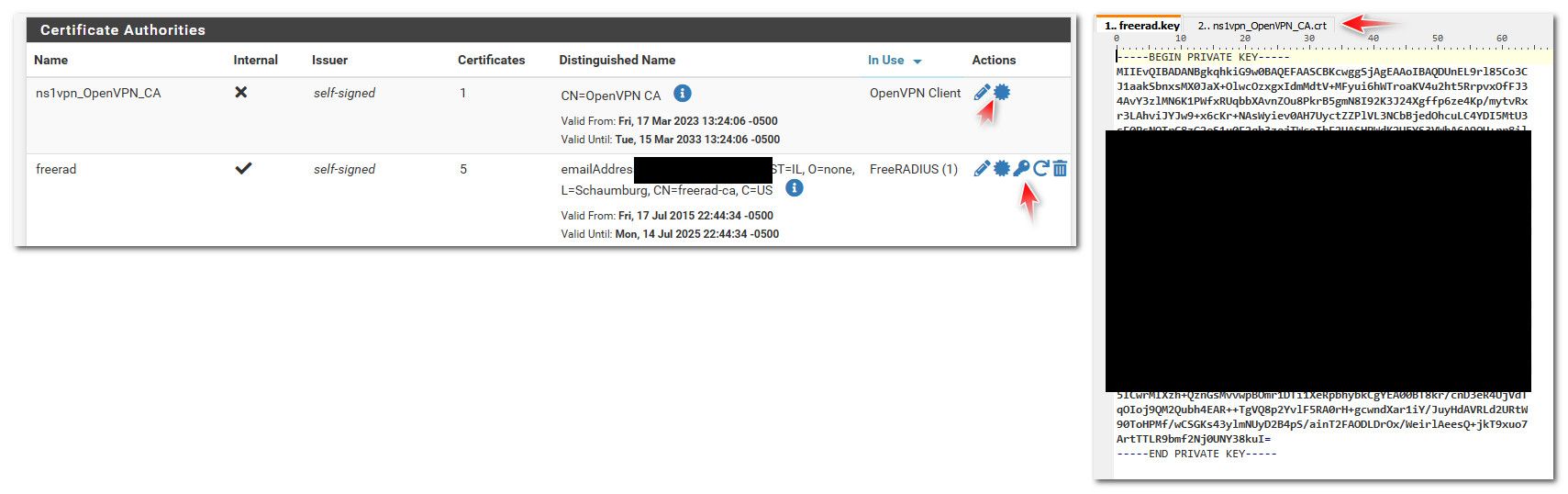
The tls key would be in the ovpn file you got or export.. Like I showed in my previous port
-
@johnpoz exactly what I did (clicked the key icon), opened it in 3 different text editors, then pasted it into the client config. On save I get the error.
-
@orangehand that is not the TLS key, that is the KEY to a cert or CA.. They are completely different things.. So no posting a cert key into the tls section is never going to work.
you would find the tls key in your server config for openvpn, or in the ovpn file you have.. They are NOT in the cert manager..
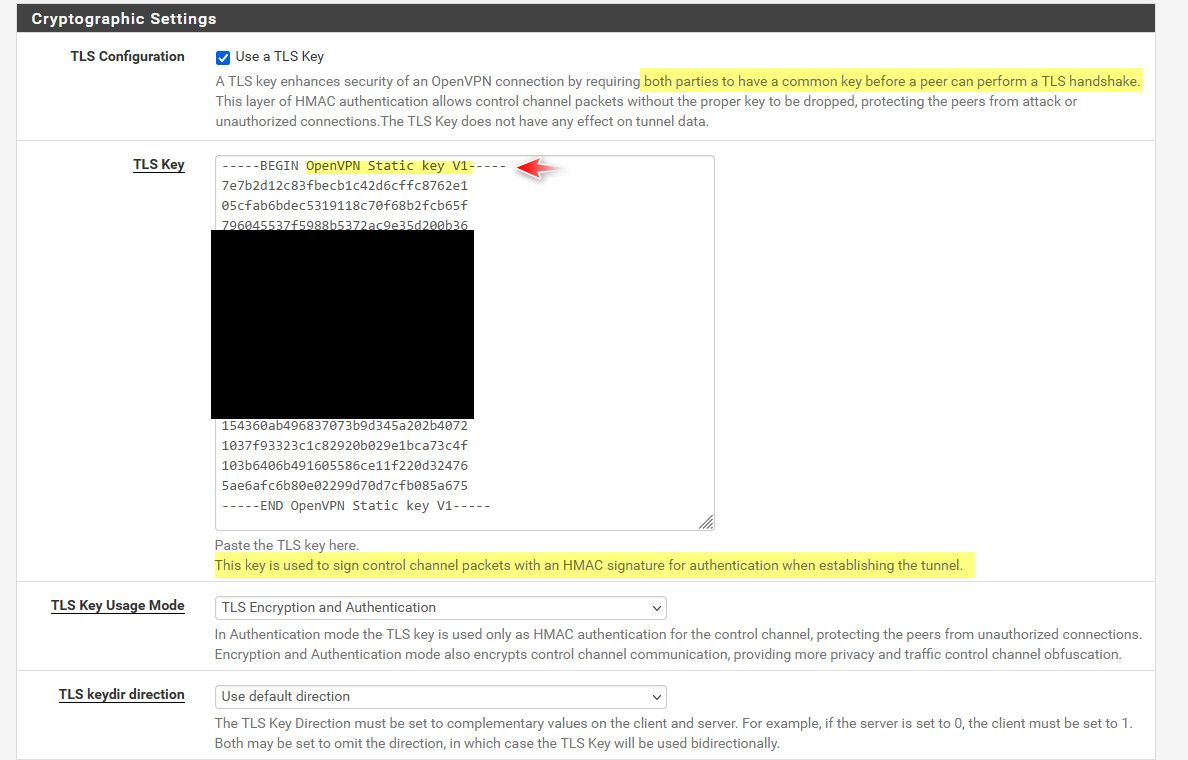
From the link you posted
-
@johnpoz Thank you so much. I had totally misinterpreted the instructions.
However, although pfSense remote can ping hosts at the other end, I cannot ping them from a LAN client at the remote end. Any guesses? -
@orangehand said in oVPN client: TLS key not valid:
I cannot ping them from a LAN client at the remote end.
where are you trying to ping, and what are the networks involved..
192.168.1/24 - pfsenseA -- vpn tunnel 172.16.0/24 -- pfsenseB - 192.168.2/24
So that is example s2s setup.. Who can not ping who.. And do you have routes on both ends pointing to the other network down the vpn, etc
also don't forget possible host firewall.. Just because the routes are there and pfsense allows traffic if say 192.168.1.x tried to ping 192.168.2.y doesn't mean that 2.y is going to answer the ping from some remote network, etc.
-
@johnpoz
remote client 10.0.169.0/24 -- 10.0.89.0/24 oVPN tunnel -- 10.0.69.0/24 main office serverI'm pinging 10.0.69.16 from remote client pfsense at 10.0.169.1 and get a response. Ping from client on remote lan no response.
There is nothing in the remote routing table for destination 10.0.69.0/24, but the guide doesn't say that one needs to deal with routing, hence I haven't!
-
@orangehand said in oVPN client: TLS key not valid:
I'm pinging 10.0.69.16 from remote client pfsense at 10.0.169.1 and get a response. Ping from client on remote lan no response.
That screams .16 firewall to me, or .16 not using pfsense as its default gateway.
You mean from 69.1 you get a response?
-
@johnpoz yes, I get a response from 10.0.69.1 AND 10.0.169.1 at the remote end
-
@orangehand where exactly are you pinging from.. 169.1 would be pfsense lan IP on the remote end.. There wouldn't be any different with your routing, or normally firewall on the 69.x device.
10.0.69.16 -- 69.1 pfsenseA -- vpn tunnel --- pfsenseB 169.1 -- 10.0.169.x
If you ping 69.16 from 169.1 interface on pfsenseB, it should work from 169.x unless 169.x is not using pfsenseB as its gateway. Or you doing some sort of policy routing on your 169.1 interface, or you have some firewall rule blocking access to this remote network?