Need help to configure pfsense + Cisco switch + vlans
-
Hello,
I am in trouble with Cisco Switch and vlans...
As you can see below, I did all theses steps :
- Add vlan10
- Assign vlan to LAN interface.
- Add firewall rules
- configure Cisco trunk mode & vlan 10 on ports?
Problem : laptop can't ping vlan's gateway.
I probably missed something but I don't know where !Could you please help me to fix this problem?
Thank you.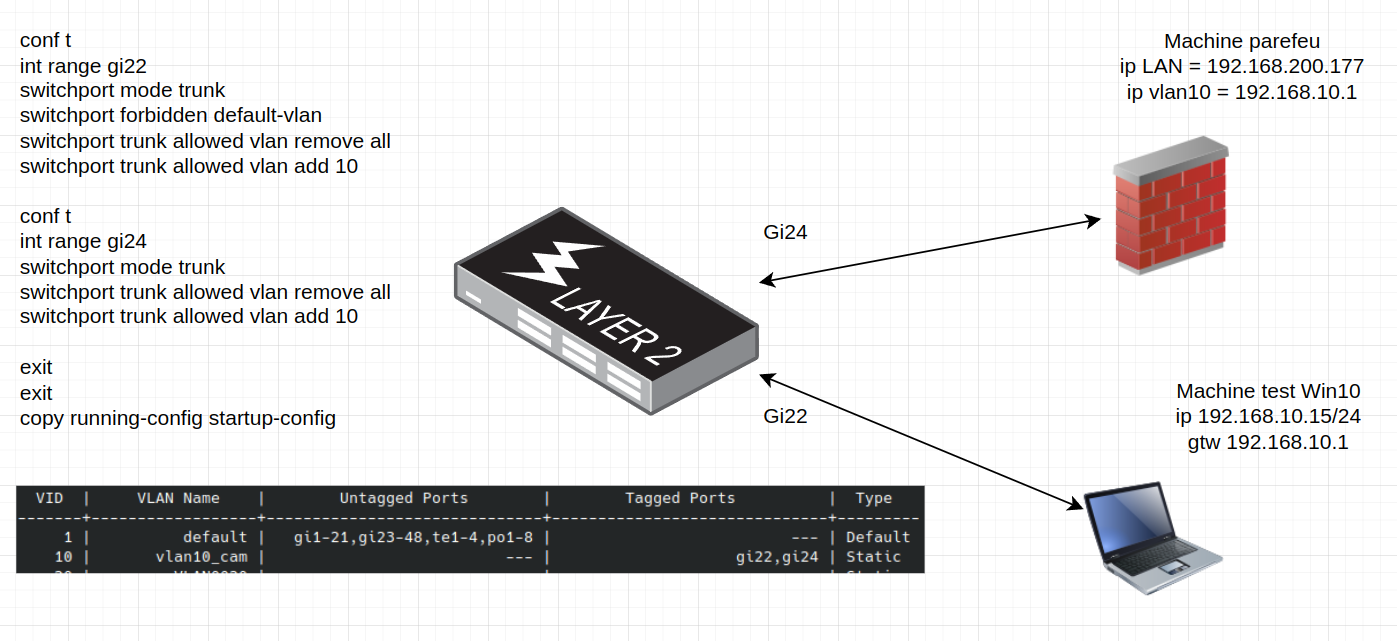
-
@dvb said in Need help to configure pfsense + Cisco switch + vlans:
laptop can't ping vlan's gateway.
did you create firewall rules on your new interface for vlan 10?
Why would you tag vlan 10 to your laptop on gi22? Did you set your laptop to tag traffic? How is it going to understand the tag?
Interface 22 should be access on vlan 10.
Here is example my work laptop on my guest vlan 6
interface gigabitethernet18 description "Vlan 6 - work laptop" switchport mode access switchport access vlan 6Here is uplink from switch for vlan 2 (native untagged) and 2 vlans 4 and 6
interface gigabitethernet5 description "sg4860 WLan and vlans" switchport trunk allowed vlan add 4,6 switchport trunk native vlan 2Also what interface is g24 on exactly in pfsense, looks like you forbid vlan 1, and only allow vlan 10.. So if there is no other vlans on this interface, why would you not just use native (access port).. Unless you have plans of adding more vlans to it?
-
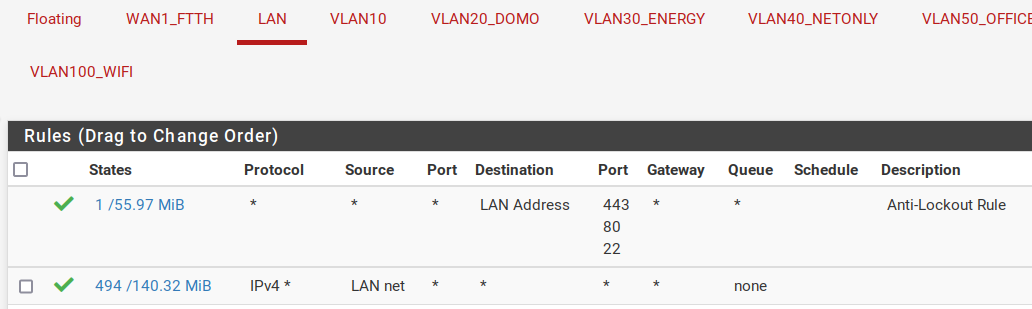
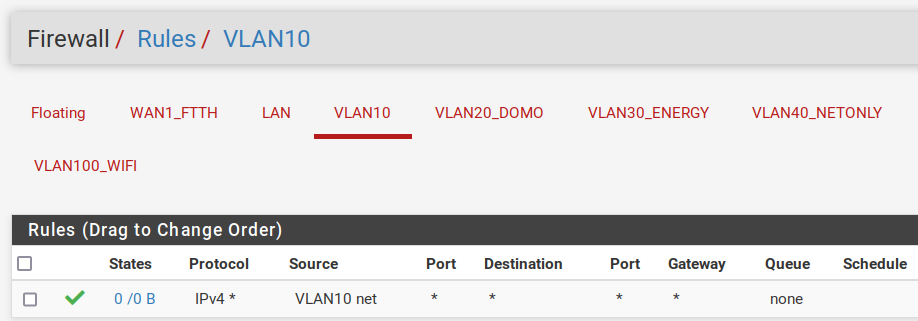
did you create firewall rules on your new interface for vlan 10?
Yes I create theses 2 rules :
Why would you tag vlan 10 to your laptop on gi22? Did you set your laptop to tag traffic? How is it going to understand the tag?
You point on a mistake : I forgot to configure windows network setup to add vlan.
I tag vlan10 for future multi vlans configuration. I will need to add a wifi access point on this port (through a mini switch).Interface 22 should be access on vlan 10.
OK I will try access mode setting.
Here is example my work laptop on my guest vlan 6
interface gigabitethernet18 description "Vlan 6 - work laptop" switchport mode access switchport access vlan 6Here is uplink from switch for vlan 2 (native untagged) and 2 vlans 4 and 6
interface gigabitethernet5 description "sg4860 WLan and vlans" switchport trunk allowed vlan add 4,6 switchport trunk native vlan 2Thanks, it helps me !
Also what interface is g24 on exactly in pfsense, looks like you forbid vlan 1, and only allow vlan 10.. So if there is no other vlans on this interface, why would you not just use native (access port).. Unless you have plans of adding more vlans to it?
I forbid vlan 1 just for the tests, because traffics was running on it instead of vlan10. I will authorize vlan 1 to manage pfsense from my desktop. At the end, I will do this via an special "admin" vlan.
Yes I plan to build several vlans : office, wifi, server, etc..
What is your advice for multiple vlans on one port ?Using trunk mode for theses ports, and configure clients with vlan10, vlan 20, etc ?
-
In my thinking, normal client devices should always be connected to untagged switch ports.
Mainly just other switches (that forward vlans), WiFi APs (if using multiple vlans) and virtualization hosts need trunk ports.I have a interface in my pfSense configured with vlans (tagged) only.
Here's a sample what I have configured on the switch,
(I have the switch native vlan set to 4000 and no networks are using it, if you're wondering about that... )
)interface GigabitEthernet1 description "Firewall" switchport mode trunk switchport trunk native vlan 4000 switchport trunk allowed vlan 10,20,25,30,35,40,50 interface GigabitEthernet2 description "Wifi AP" switchport mode trunk switchport trunk native vlan 4000 switchport trunk allowed vlan 10,20,25,30,35,40,50 interface GigabitEthernet3 description "Main PC" switchport access vlan 20 switchport trunk native vlan 4000 switchport trunk allowed vlan 4000 interface GigabitEthernet7 description "HomeNAS Eth1" channel-group 1 mode auto switchport access vlan 20 switchport trunk native vlan 4000 switchport trunk allowed vlan 4000 interface GigabitEthernet8 description "HomeNAS Eth2" channel-group 1 mode auto switchport access vlan 20 switchport trunk native vlan 4000 switchport trunk allowed vlan 4000 -
@dvb said in Need help to configure pfsense + Cisco switch + vlans:
I forgot to configure windows network setup to add vlan.
Not a mistake you shouldn't do this.. There is NO reason.. A port your going to add a single device should be untagged on the vlan you going to add..
-
@mvikman said in Need help to configure pfsense + Cisco switch + vlans:
In my thinking, normal client devices should always be connected to untagged switch ports.
Mainly just other switches (that forward vlans), WiFi APs (if using multiple vlans) and virtualization hosts need trunk ports.Yes, it's clear for me now !
I have a interface in my pfSense configured with vlans (tagged) only.
Here's a sample what I have configured on the switch,
I didn't know that I could mix "address mode" and "trunk mode" on the same port. Very interesting !
(I have the switch native vlan set to 4000 and no networks are using it, if you're wondering about that...
 )
)...

@johnpoz said in Need help to configure pfsense + Cisco switch + vlans:
Not a mistake you shouldn't do this.. There is NO reason.. A port your going to add a single device should be untagged on the vlan you going to add..
I was on the wrong way, because I thought that trunk = tagged required until final device. Thanks to this post, I have a better understanding "how it works".
Good news, after reconfiguration, it's OK !
Last question about the firewall.
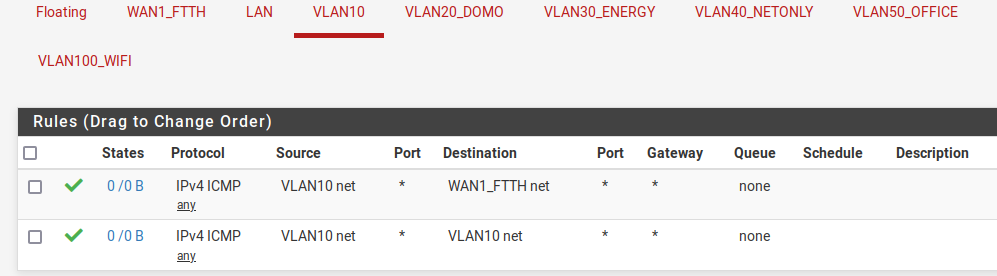
I made theses two rules to allow ping :- only inside the vlan
- only to the Internet.
The outward rule does not work, and if I put "any", I can ping to the internet but also in all the LAN/vlans.
How do you proceed in this case ?
Regards.
-
@dvb those rules are only icmp - so I don't see any dns - so if your trying to resolve something or actually connect to something that isn't going to work.
also wan net is only that - that is not the internet. and your vlan10 net rule is pretty pointless, pfsense has nothing to do with clients talking to each other, etc.
you put in a rule above to block access to what you don't want to access, but allow internet - here is like a locked down network.
-
@johnpoz said in Need help to configure pfsense + Cisco switch + vlans:
@dvb those rules are only icmp - so I don't see any dns - so if your trying to resolve something or actually connect to something that isn't going to work.
Yes no dns because I was just pinging and external IP like 8.8.8.8. Just for testing.also wan net is only that - that is not the internet. and your vlan10 net rule is pretty pointless, pfsense has nothing to do with clients talking to each other, etc.
Oups ! You've totally right !
Same lan -> layer 2 OSI, no need for layer 3.you put in a rule above to block access to what you don't want to access, but allow internet - here is like a locked down network.
Perfect -> I will try this tomorrow !
@mvikman
I tried this without success :interface GigabitEthernet4 switchport access vlan 10 switchport trunk native vlan 1 switchport trunk allowed vlan 1But I got en error message -> "port isn't in trunk mode".
I need to choose from access or trunk, or did I missed something ?
-
@dvb
I have a CBS350-series switch, it doesn't have the full-featured IOS, so supported configuration/commands are slightly different...But yeah, access port is for untagged (client device ports) and trunk port is for, well... for vlans trunks :)
-
@dvb said in Need help to configure pfsense + Cisco switch + vlans:
But I got en error message -> "port isn't in trunk mode".
Not sure why your trying to put trunk commands on a access port.. reset the port, put it access and put in vlan 10 that is all you need to do.
-
@johnpoz
He's trying to use lines from my switch config in his switch.
The CBS350 (Cisco Small Business) Series switches are a bit weird, you can set native vlan to all ports with the "switchport trunk native vlan" command and it keeps it in the port config even if you then set the port as an access port... -
@mvikman not sure why he would want to do that? This isn't rocket science - the port connected to his laptop is a simple access port in whatever vlan he wants that port on.
There is no reason to set any trunk native vlan.. Makes no sense to do that.. You would set that command on a port you have in trunk that you want a specific vlan to be untagged.. I run it myself on my sg300, see my post above on gi5 interface... This port connects to a port on my pfsense that has a native network, ie no vlan - which is vlan 2 on my switch.. And then 2 vlans 4 and 6 that are tagged.
But you sure do not put that command on an access port that is going to connect to a single device like a laptop or pc that is going to be in 1 vlan.
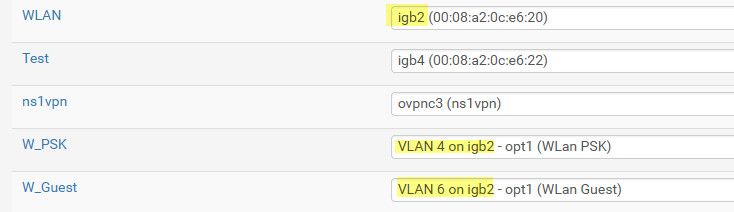
I run untagged on because when I first set up my unifi AP they could not use a vlan for their managment, it had to be untagged.. They have since then allowed for management on tagged vlans - but I saw no point to changing to that.
You can run an untagged network on a trunk, that is what that command does..
If he wants to run a native network directly on the interface he is also going to be running tagged vlans - then sure he would use that command on the trunk port he has connect to his pfsense interface that has a native network on it - like you see above on my ig2 interface, this is vlan 2 on my switch..
-
@johnpoz
I changed the native vlan from 1 to 4000 on my CBS350 switch and that kinda weird way is how it handles it...
Him looking at my sample config probably confused him for the need to set the native vlan on his switch, which is not the same series as mine. -
@mvikman said in Need help to configure pfsense + Cisco switch + vlans:
which is not the same series as mine.
You sure and the hell don't need to set it on yours either on an access port.. Are you confusing default vlan and native? My default vlan isn't 1 either..
This would not change across switch models or lines - the only reason to set that command is when you want an untagged vlan on your trunk. This command allows you to change it from the default vlan, etc. And tell the trunk which vlan to not tag.
The only time you would need that command is when you want that specific vlan to be untagged on your trunk, and its not the default vlan of the switch.
-
Yes I was a little confused for ports that need to support several vlans.
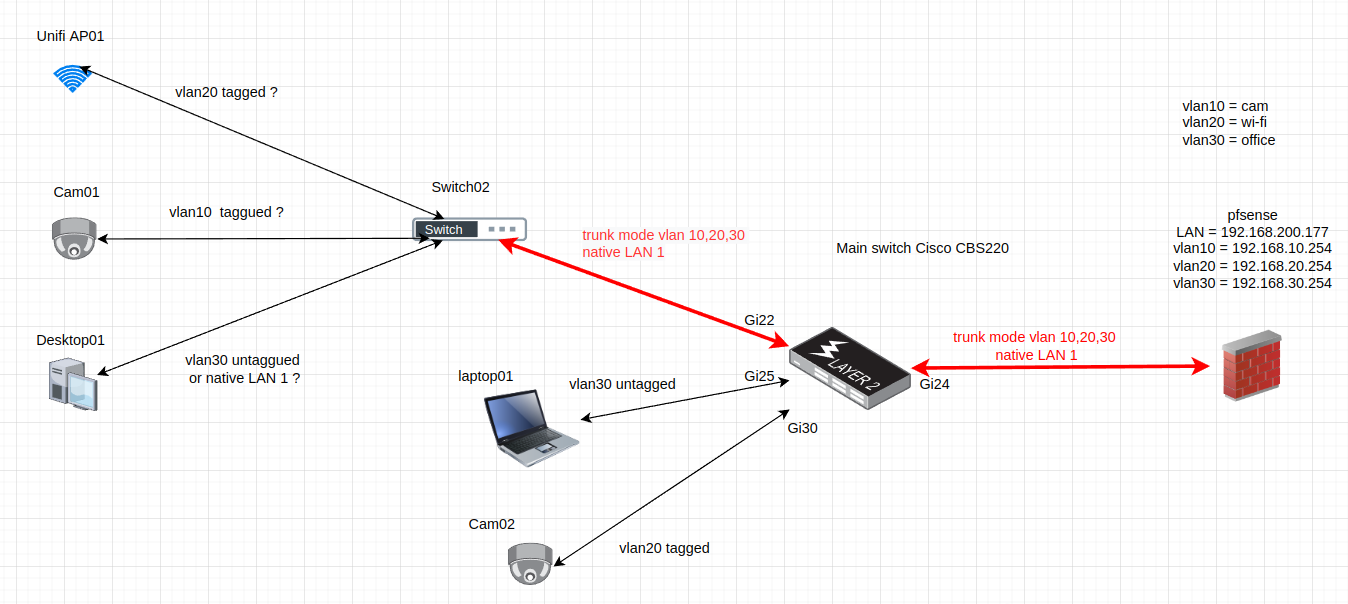
Lets explain with the schema below :
Configurations OK (I think) :
- Gi25 -> only laptop01 -> easy -> access mode / vlan30 untagged
- Gi30 -> only cam02 -> easy -> acess mode / vlan30 untagged
- gi22 and Gi24 = trunk mode to pass all vlans -> trunck mode / all vlans and 1 native
Configurations I am not sure :
Unifi AP01, cam01, and Desktop 1 are connected to a no administrated mini switch. I would like to connect each device on a different vlan in untagged mode. -> But it seems to be impossible with this type of switch.Than I think I need to connect each device on a different taggued vlan. need to check if Hikvision camera and Unifi accept that.
If you suppose (for example) that Desktop01 can't support vlan taggued connexion, is there a solution to connect all type (taggued and non tagged) vlans on this type of switch ?
-
@dvb said in Need help to configure pfsense + Cisco switch + vlans:
But it seems to be impossible with this type of switch.
Yeah if you have a switch that doesn't understand vlans that not a viable setup.. If you connect a dumb switch to a managed switch, all devices on the dumb switch would be in the untagged vlan you hand off to that switch.
Now in theory - sure you could pass tags across that switch, and then all your devices could be in different vlans if they understand and are setup to work with the tags. But that is not a good idea, since the switch is dumb and doesn't understand them all multicast and broadcast traffic from all vlans handed to that switch would go to all ports, etc.
If its like the unifi mini flex switch, while how it does vlans is a bit odd, you can get it to work with a non unifi switch - you can not just really prune vlans on its uplink, but it can work. I have one of those that I play with, and it can work.. But in general for how your drawing is with devices hanging off switch02, you really need a vlan capable switch. If all the devices were going to be in the same vlan then any dumb switch would work.
Vlan capable switches can be had for like the 40$ price range - 8 ports gig, etc.
Your drawing there with cam02 - that port should be access.. I highly doubt some cam can work with tags, and since there is only 1 device connected, that port should just be untagged anyway. The only time you should be tagging traffic on a port is if you need to carry more than 1 vlan over the physical interface. And then the device on the other end will do with what you tell it with the tags.. So like another vlan capable switch, or a AP where you have different ssids in different vlans, etc.
Your AP01 - are you not going to have different ssids on different vlans?
If you use some vlan capable switch there for 02, you can do what your after by being able to put any device on switch02 on any vlan, or even multiple vlans like an AP..
if your going to just use the default vlan (vlan 1) as native (untagged) on a trunk port you don't need that "switchport trunk native vlan X" command.. The default vlan is what is normally untagged on a trunk port, that command allows you to set some other vlan as untagged vs the default vlan.
-
@johnpoz said in Need help to configure pfsense + Cisco switch + vlans:
Vlan capable switches can be had for like the 40$ price range - 8 ports gig, etc.
Good news, I didn't expect to find small (I mean 5 to 8 ports) manageable switches at such low prices.
Your drawing there with cam02 - that port should be access.. I highly doubt some cam can work with tags, and since there is only 1 device connected, that port should just be untagged anyway.
Sorry I made a bad copy and paste when drawing. Of course this port should be untagged.
Your AP01 - are you not going to have different ssids on different vlans?
Yes of course, I drew very quickly and did not mention that. I plan to have 2 or 3 vlans for security. (I have to learn in Unifi documentation how to associate an ssid to a vlan).
In conclusion :
-
I will upgrade "unmanaged switch" to "managed switch"
-> when they need to support untagged vlans. -
"WIFI AP" and "switch to switch link"
-> will be connected via trunk mode (untagged ports). -
All other devices
-> will be connected via access mode (tagged ports).
Two more questions :
-
With 3 or 4 managed switches, what do you advise to admin them with a good security, if I consider to avoid native vlan 1 :
-Create a specific vlan ?
-Using a native vlan ? (different than 1, like @mvikman did). -
I've a mini switch behind a CPL. I believe that CPL are not vlan compatible. If it's true, I am limited to one untaggued vlan. -> Do you agree with that ?
Thanks !
-
-
Hi,
I received a second managed switch today, and I tried to check tagged /untagged configuration.
After I double checked all settings, I can't afford laptop to ping pfsense via vlan10.
Here is the schema and configuration. Could you please help me to point the problem ?
Thank you !
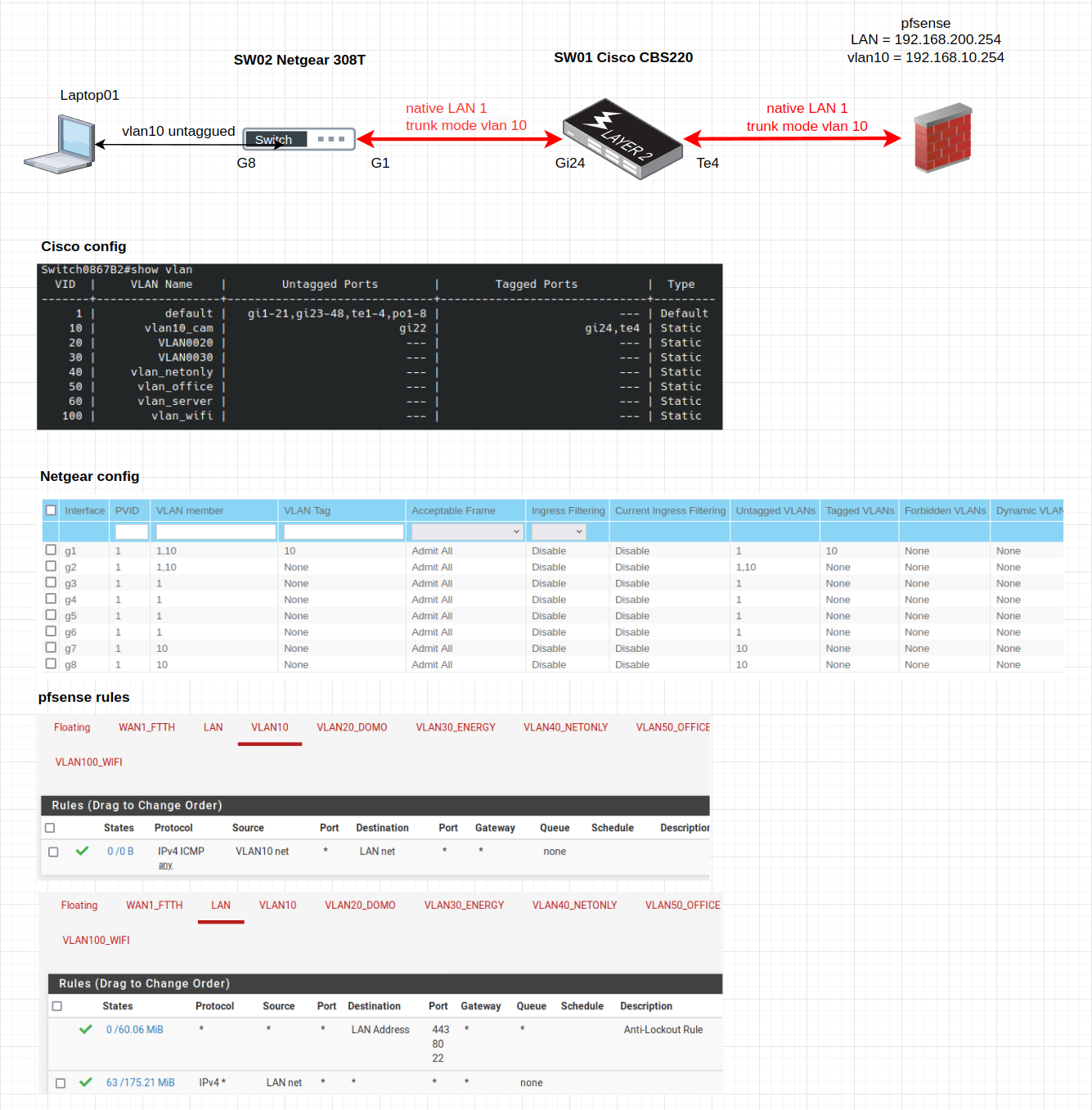
-
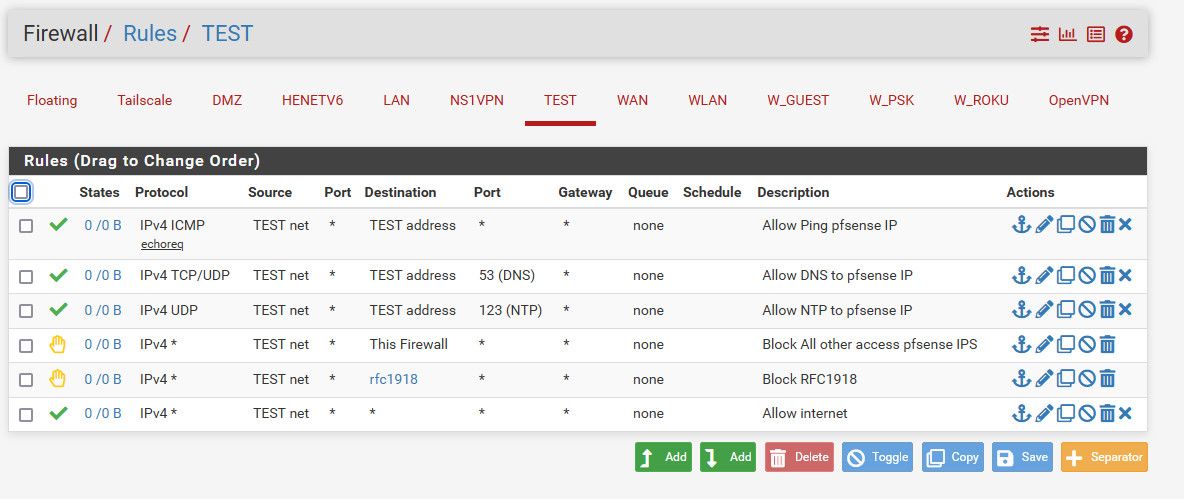
So the laptop has 192.168.10.x ip and you are trying to ping vlan10 gateway 192.168.10.254?
Your vlan10 rule currently only allows you to ping lan addresses from vlan10 (source: vlan10 net, destination: lan net).
If you want to ping vlan10 gateway, add a rule to allow ping from vlan10 net to vlan10 address. -
@mvikman said in Need help to configure pfsense + Cisco switch + vlans:
So the laptop has 192.168.10.x ip and you are trying to ping vlan10 gateway 192.168.10.254?
Yes, laptop has 192.168.10.9.
(and gtw -> 192.168.10.254)Your vlan10 rule currently only allows you to ping lan addresses from vlan10 (source: vlan10 net, destination: lan net).
If you want to ping vlan10 gateway, add a rule to allow ping from vlan10 net to vlan10 address.I was just tring to ping "vlan10 gateway" -> 192.168.10.254 but it fails. For this, no rule is needed beause we stay on OSI layer 2 (correct me if I am wrong).
I also tried to put laptop in dhcp mode, it can't find the server on 192.168.10.254.
I don't understand this behaviour.
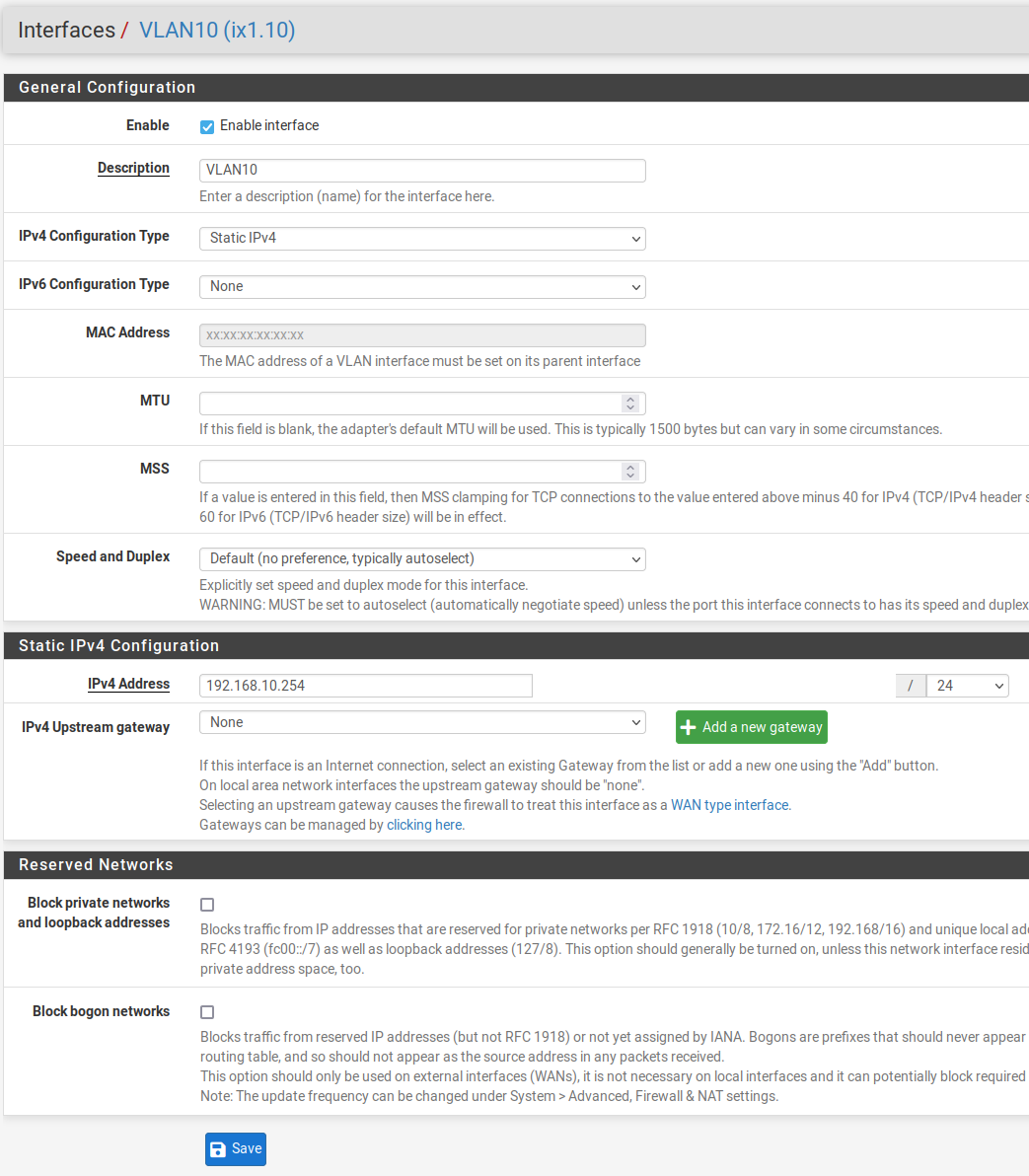
Configuration of vlan10 interface just in case :