Non-pfSense VPN routing
-
I am using pfSense as firewall also between local net segments, 192.168.1.0/24, 192.168.3.0/24, 192.168.5.0/24, 192.158.7.0/24, etc. Those subnets are configured as tagged VLANs. pfSense is .1 in all these subnets. Works.
I have a VM (192.168.1.117) that is running VPNs (OpenVPN, Wireguard). VPNs use 10.7.0.0/16, 10.8.0.0/16, 10.9.0.0/16 as address pools. 192.168.1.117 is configured as gateway in pfSense. For this gateway, static routes have been configured for 10.7.0.0/16, 10.8.0.0/16, and 10.9.0.0/16 to 192.168.1.117.
Problem: I can ping all devices from pfSense. From a VPN connected device, I can ping pfSense. From the VPN connected device, I cannot ping a device in 192.168.0.0/16 outside of 192.168.1.0/24. A traceroute from VPN connected devices to devices outside of 192.168.1.0/16 ends with pfSense. From VPN connected devices I CAN ping pfSense's IP in 192.168.0.0/16 subnets (e.g. 192.168.7.1).
My conclusion is that I need to configure something else in pfSense than the VPN host as gateway and static routes in order to enable routing of the VPN subnets. What have I been missing?
Do I somehow need to configure an interface with my 10.0.0.0 subnets so that it works with pfSense? If so, which network port should I assign such interface to?
Thanks!
-
@highc
What's about the firewall rule on the incoming interface?
If it's say LAN you have not to pass only "LAN net", but as well the VPN tunnel networks. -
For test purposes, I have added a rule at the top of LAN that lets pass all traffic from everywhere to everywhere. So if the LAN interface/rules (for 192.168.1.0/24) is applicable for such VPN traffic, I believe I have excluded firewall rules as the cause of this.
-
So for test purposes, I created a rule on the LAN interface specifically permitting VPN traffic. That rule triggers, including for pings which are not answered:
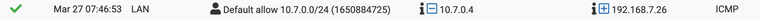
So I am pretty certain that this is rather a routing issue than a firewall issue.
-
@highc
Since pfSense is the default gateway in all your subnets, as I understood your setup, and you have added static routes for the VPN pools and pointed them to the VPN server, the routing should work.As you have multiple subnets, I"d expect that your machines are configured to allow access from outside of their subnets, but verify this setting to get sure.
In doubts sniff the traffic on the interfaces behind pfSense to see if you get responses. -
@highc
We need to see screenshots to see how your VPN is set up. I know with OpenVPN, you must specify each network segment that the VPN will have access to - so 192.168.1.0/24, 192.168.3.0/24, 192.168.5.0/24, 192.158.7.0/24, etc. It sounds like this isn't set correctly.