Need help to configure pfsense + Cisco switch + vlans
-
Yes I was a little confused for ports that need to support several vlans.
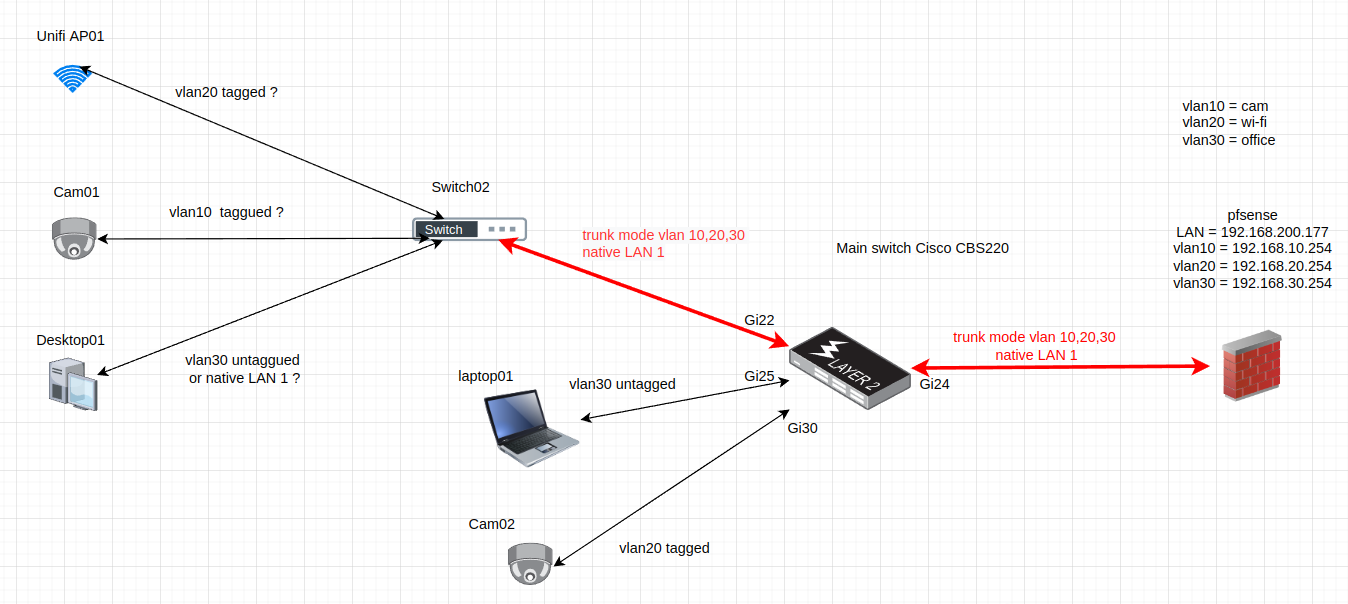
Lets explain with the schema below :
Configurations OK (I think) :
- Gi25 -> only laptop01 -> easy -> access mode / vlan30 untagged
- Gi30 -> only cam02 -> easy -> acess mode / vlan30 untagged
- gi22 and Gi24 = trunk mode to pass all vlans -> trunck mode / all vlans and 1 native
Configurations I am not sure :
Unifi AP01, cam01, and Desktop 1 are connected to a no administrated mini switch. I would like to connect each device on a different vlan in untagged mode. -> But it seems to be impossible with this type of switch.Than I think I need to connect each device on a different taggued vlan. need to check if Hikvision camera and Unifi accept that.
If you suppose (for example) that Desktop01 can't support vlan taggued connexion, is there a solution to connect all type (taggued and non tagged) vlans on this type of switch ?
-
@dvb said in Need help to configure pfsense + Cisco switch + vlans:
But it seems to be impossible with this type of switch.
Yeah if you have a switch that doesn't understand vlans that not a viable setup.. If you connect a dumb switch to a managed switch, all devices on the dumb switch would be in the untagged vlan you hand off to that switch.
Now in theory - sure you could pass tags across that switch, and then all your devices could be in different vlans if they understand and are setup to work with the tags. But that is not a good idea, since the switch is dumb and doesn't understand them all multicast and broadcast traffic from all vlans handed to that switch would go to all ports, etc.
If its like the unifi mini flex switch, while how it does vlans is a bit odd, you can get it to work with a non unifi switch - you can not just really prune vlans on its uplink, but it can work. I have one of those that I play with, and it can work.. But in general for how your drawing is with devices hanging off switch02, you really need a vlan capable switch. If all the devices were going to be in the same vlan then any dumb switch would work.
Vlan capable switches can be had for like the 40$ price range - 8 ports gig, etc.
Your drawing there with cam02 - that port should be access.. I highly doubt some cam can work with tags, and since there is only 1 device connected, that port should just be untagged anyway. The only time you should be tagging traffic on a port is if you need to carry more than 1 vlan over the physical interface. And then the device on the other end will do with what you tell it with the tags.. So like another vlan capable switch, or a AP where you have different ssids in different vlans, etc.
Your AP01 - are you not going to have different ssids on different vlans?
If you use some vlan capable switch there for 02, you can do what your after by being able to put any device on switch02 on any vlan, or even multiple vlans like an AP..
if your going to just use the default vlan (vlan 1) as native (untagged) on a trunk port you don't need that "switchport trunk native vlan X" command.. The default vlan is what is normally untagged on a trunk port, that command allows you to set some other vlan as untagged vs the default vlan.
-
@johnpoz said in Need help to configure pfsense + Cisco switch + vlans:
Vlan capable switches can be had for like the 40$ price range - 8 ports gig, etc.
Good news, I didn't expect to find small (I mean 5 to 8 ports) manageable switches at such low prices.
Your drawing there with cam02 - that port should be access.. I highly doubt some cam can work with tags, and since there is only 1 device connected, that port should just be untagged anyway.
Sorry I made a bad copy and paste when drawing. Of course this port should be untagged.
Your AP01 - are you not going to have different ssids on different vlans?
Yes of course, I drew very quickly and did not mention that. I plan to have 2 or 3 vlans for security. (I have to learn in Unifi documentation how to associate an ssid to a vlan).
In conclusion :
-
I will upgrade "unmanaged switch" to "managed switch"
-> when they need to support untagged vlans. -
"WIFI AP" and "switch to switch link"
-> will be connected via trunk mode (untagged ports). -
All other devices
-> will be connected via access mode (tagged ports).
Two more questions :
-
With 3 or 4 managed switches, what do you advise to admin them with a good security, if I consider to avoid native vlan 1 :
-Create a specific vlan ?
-Using a native vlan ? (different than 1, like @mvikman did). -
I've a mini switch behind a CPL. I believe that CPL are not vlan compatible. If it's true, I am limited to one untaggued vlan. -> Do you agree with that ?
Thanks !
-
-
Hi,
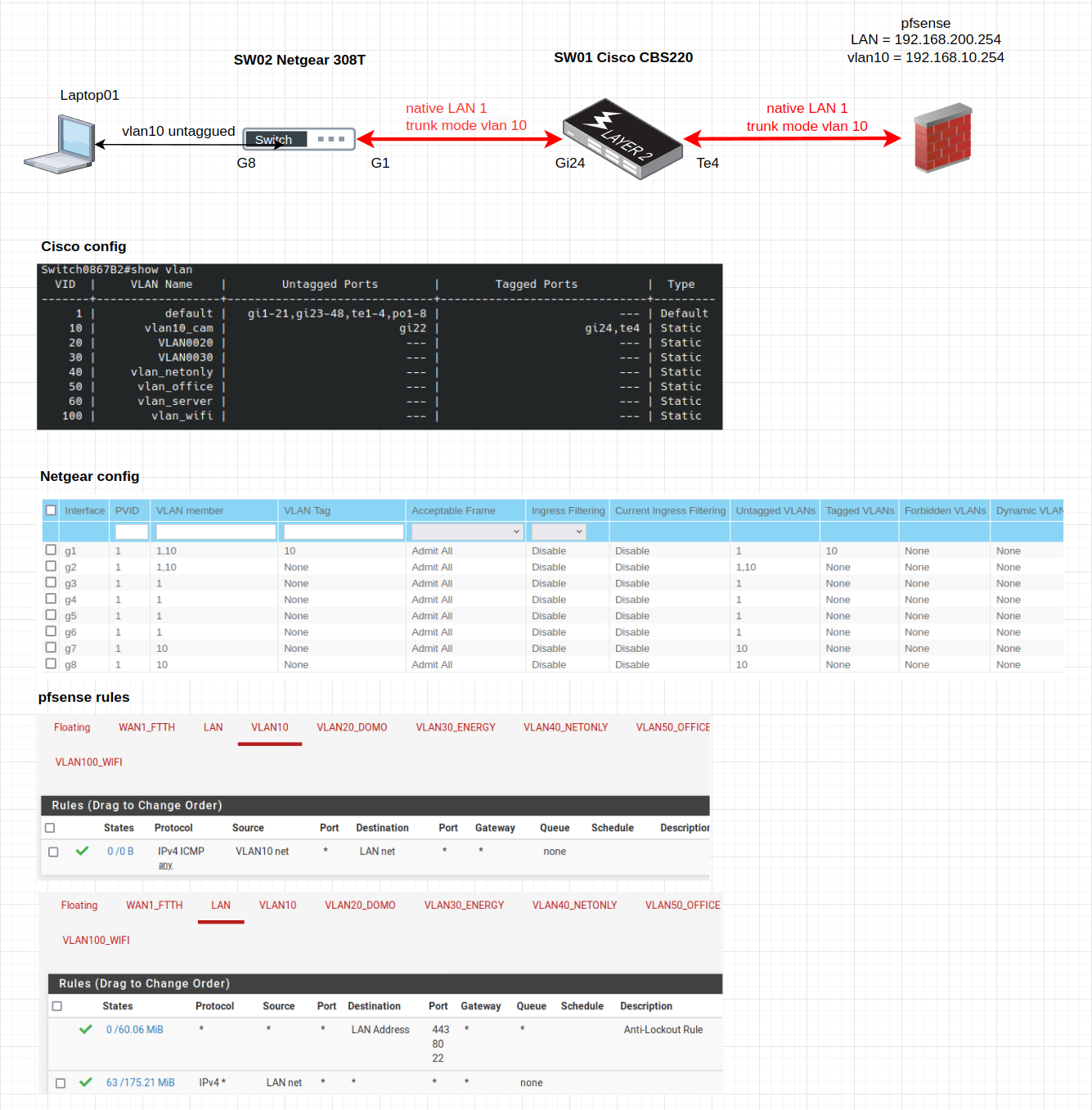
I received a second managed switch today, and I tried to check tagged /untagged configuration.
After I double checked all settings, I can't afford laptop to ping pfsense via vlan10.
Here is the schema and configuration. Could you please help me to point the problem ?
Thank you !
-
So the laptop has 192.168.10.x ip and you are trying to ping vlan10 gateway 192.168.10.254?
Your vlan10 rule currently only allows you to ping lan addresses from vlan10 (source: vlan10 net, destination: lan net).
If you want to ping vlan10 gateway, add a rule to allow ping from vlan10 net to vlan10 address. -
@mvikman said in Need help to configure pfsense + Cisco switch + vlans:
So the laptop has 192.168.10.x ip and you are trying to ping vlan10 gateway 192.168.10.254?
Yes, laptop has 192.168.10.9.
(and gtw -> 192.168.10.254)Your vlan10 rule currently only allows you to ping lan addresses from vlan10 (source: vlan10 net, destination: lan net).
If you want to ping vlan10 gateway, add a rule to allow ping from vlan10 net to vlan10 address.I was just tring to ping "vlan10 gateway" -> 192.168.10.254 but it fails. For this, no rule is needed beause we stay on OSI layer 2 (correct me if I am wrong).
I also tried to put laptop in dhcp mode, it can't find the server on 192.168.10.254.
I don't understand this behaviour.
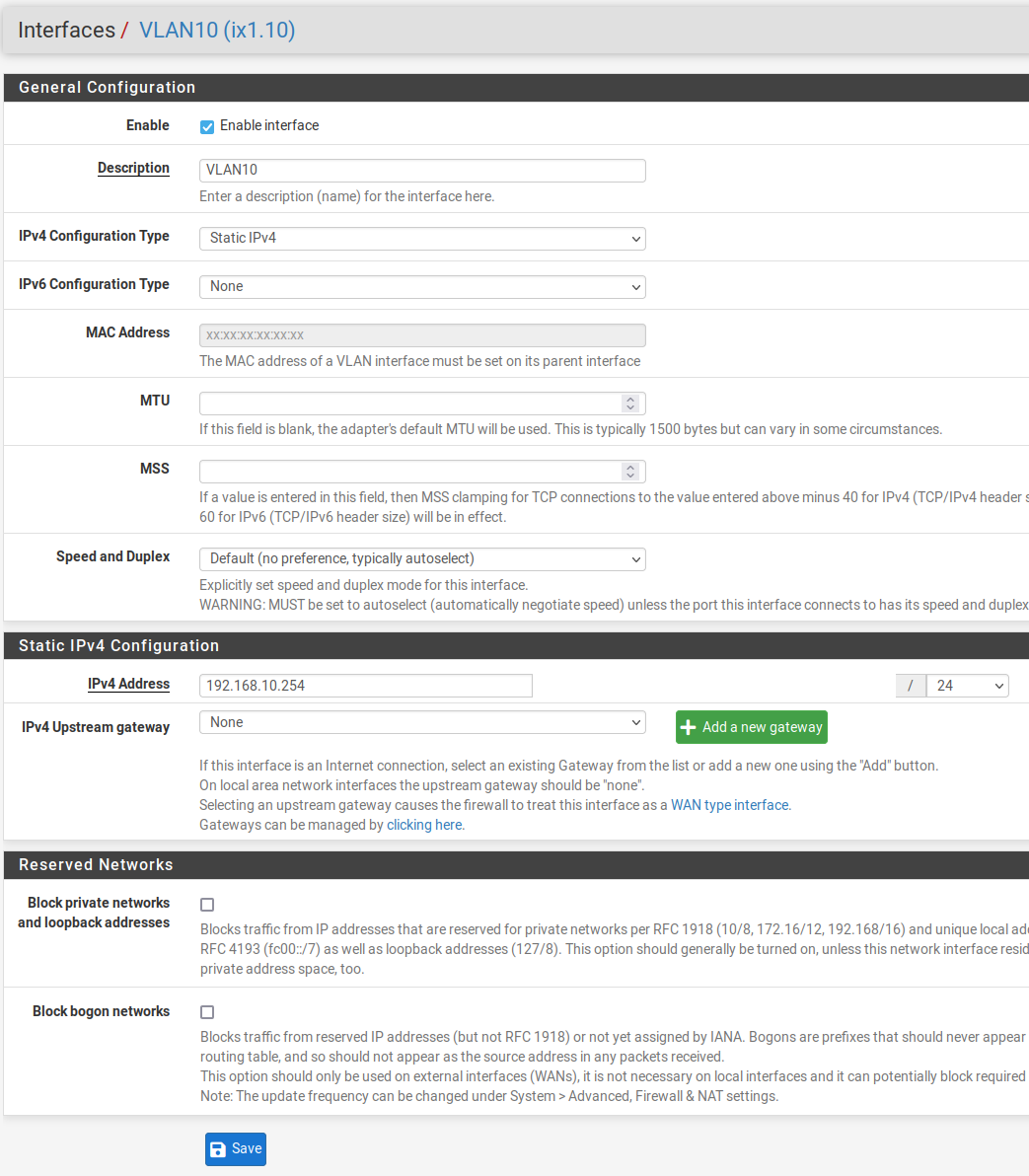
Configuration of vlan10 interface just in case :
-
@dvb said in Need help to configure pfsense + Cisco switch + vlans:
I was just tring to ping "vlan10 gateway" -> 192.168.10.254 but it fails. For this, no rule is needed beause we stay on OSI layer 2 (correct me if I am wrong).
Yes, the gateway is in the same address space, but it is a pfsense interface and the firewall rules apply to traffic incoming to that interface.
The default action is "deny all", so the interface ip will not respond to ping unless you create rule to allow it. -
@mvikman said in Need help to configure pfsense + Cisco switch + vlans:
Yes, the gateway is in the same address space, but it is a pfsense interface and the firewall rules apply to traffic incoming to that interface.
The default action is "deny all", so the interface ip will not respond to ping unless you create rule to allow it.OK I understood !
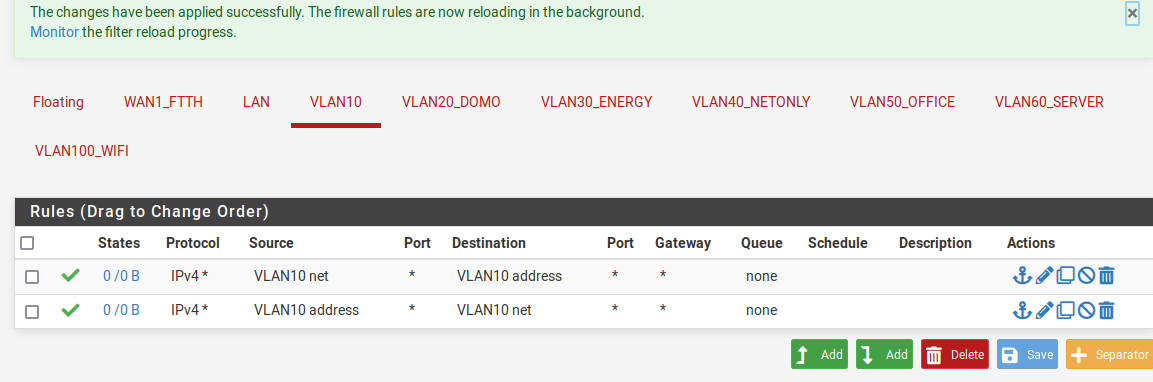
I just created these two rules (to ping from host and from laptop). No succes, ping still fails. Any idea ?
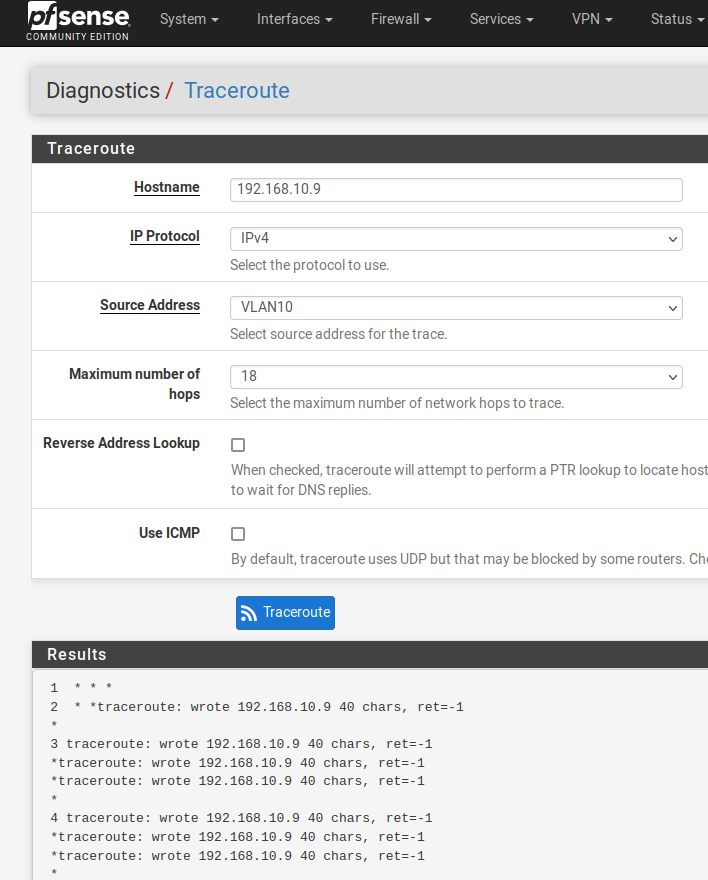
-
@dvb for one you have the pvid on port 8 as 1, that should be 10.. Or no nothing is ever going to work.. laptop sends traffic and port puts it on vlan 1..
Also your firewall rules - you don't need that rule from address to net.. Rules are only evaluated as traffic enters the internet from the network..
-
@johnpoz said in Need help to configure pfsense + Cisco switch + vlans:
@dvb for one you have the pvid on port 8 as 1, that should be 10.. Or no nothing is ever going to work.. laptop sends traffic and port puts it on vlan 1..
Also your firewall rules - you don't need that rule from address to net.. Rules are only evaluated as traffic enters the internet from the network..
I tried one untagged vlan per port, all is working perfect :
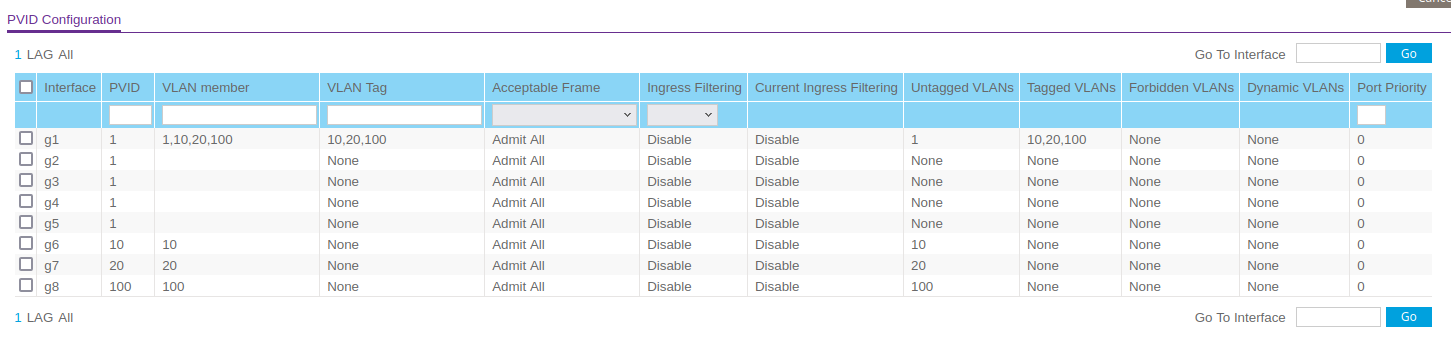
Thank you very much for your support and advice !