OpenVPN UNDEF connections!
-
Hello,
I own a Netgate 3100
Running pfSense 23.01-RELEASE
I have a OpenVPN server that I've been using for a while now.
Today I have connected to the pfSense UI to see this:
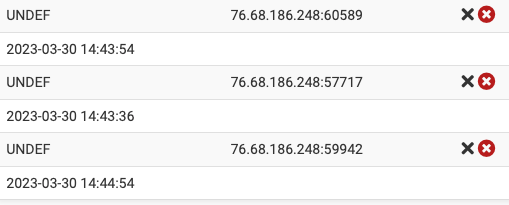
A bunch of connexion with UNDEF identifier, with unknown IP, and they don't get an internal IP either.
In the logs I see this:
Time Process PID Message Mar 30 14:39:51 openvpn 90756 76.68.186.248:59140 TLS Error: Unroutable control packet received from [AF_INET]76.68.186.248:59140 (si=3 op=P_CONTROL_V1) Mar 30 14:39:52 openvpn 90756 76.68.186.248:59140 TLS Error: Unroutable control packet received from [AF_INET]76.68.186.248:59140 (si=3 op=P_CONTROL_V1) Mar 30 14:39:53 openvpn 90756 76.68.186.248:59140 TLS Error: Unroutable control packet received from [AF_INET]76.68.186.248:59140 (si=3 op=P_CONTROL_V1) Mar 30 14:39:53 openvpn 90756 76.68.186.248:59141 peer info: IV_VER=3.git::d3f8b18b Mar 30 14:39:53 openvpn 90756 76.68.186.248:59141 peer info: IV_PLAT=win Mar 30 14:39:53 openvpn 90756 76.68.186.248:59141 peer info: IV_NCP=2 Mar 30 14:39:53 openvpn 90756 76.68.186.248:59141 peer info: IV_TCPNL=1 Mar 30 14:39:53 openvpn 90756 76.68.186.248:59141 peer info: IV_PROTO=30 Mar 30 14:39:53 openvpn 90756 76.68.186.248:59141 peer info: IV_CIPHERS=AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:BF-CBC Mar 30 14:39:53 openvpn 90756 76.68.186.248:59141 peer info: IV_GUI_VER=OCWindows_3.3.6-2752 Mar 30 14:39:53 openvpn 90756 76.68.186.248:59141 peer info: IV_SSO=webauth,openurl,crtext Mar 30 14:39:53 openvpn 90756 76.68.186.248:59141 peer info: IV_BS64DL=1 Mar 30 14:39:53 openvpn 90756 76.68.186.248:59141 TLS Error: Auth Username/Password was not provided by peer Mar 30 14:39:53 openvpn 90756 76.68.186.248:59141 TLS Error: TLS handshake failedI don't know what to make of this.
Please advise!!
-
This IP is knocking on your door (OpenVPN). Just ignore it or change your OpenVPN to a high non default Port.
-Rico
-
@blazestar UNDEF I believe is because openvpn can not determine the client name..
client-cert-not-required is that in your server config? What is your server config? Are you just using "user auth" vs SSL/TLS
-
UNDEFmeans the client hasn't identified itself in any way yet. Usually that means something that isn't OpenVPN is hitting the port. For example, a port scanner or other network probing method.If it's an RA OpenVPN there isn't much more you can do there to stop those, except to make sure you are using TLS authentication so that nobody could ever get farther than hitting the port even during TLS negotiation.
-
@jimp said in OpenVPN UNDEF connections!:
TLS authentication so that nobody could ever get farther than hitting the port even during TLS negotiation.
This is the way ;)
-
@johnpoz I'm using SSL/TLS + User Auth
There is a Peer Certificate Authority set up , which is the Certificate I created for the OpenVPN server.
Certificate Depth is set to One (Client+Server).
I'm not sure it that answers your question, if not let me know what I can provide in terms of configuration.
I don't see the "client-cert-not-required" anywhere in my config (looking at the UI). -
@blazestar are you not using TLS key for auth or both auth and encryption? As mentioned, by Jim - using that the traffic shouldn't be able to really even get past that to even start a session with openvpn.
-
I do think I'm using TLS key for auth or both auth and encryption.
I'm sorry for being such a n00b but can you tell me how to check if I my config is doing that?
-
@blazestar said in OpenVPN UNDEF connections!:
you tell me how to check
tell us and some one from here will tell you :
Tip : Add a "start watch" on this thread : HEADS UP: OpenVPN deprecating shared key mode, requires TLS, deprecating cipher selection
-
@blazestar now I have my openvpn logs limited in verbosity.. But you can see stuff like this
Mar 30 02:04:15 openvpn 63033 TLS Error: tls-crypt unwrapping failed from [AF_INET]167.94.138.106:1863 Mar 30 02:04:15 openvpn 63033 tls-crypt unwrap error: packet too shortThis IP didn't get past the test on the TLS that valid client would send when using the TLS key..
Now that specific IP is from Censys, which is a internet scanning company.. I really need to add their netblocks to my blocks. I block a few different scanners, shoden, shadowserver and stretchoid and a few and most of Digital Oceans IP space.. I look at logs now and then add add more scanners I notice so they can not even get to my open ports..
https://openvpn.net/community-resources/hardening-openvpn-security/
tls-auth
The tls-auth directive adds an additional HMAC signature to all SSL/TLS handshake packets for integrity verification. Any UDP packet not bearing the correct HMAC signature can be dropped without further processing. The tls-auth HMAC signature provides an additional level of security above and beyond that provided by SSL/TLS. It can protect against:
DoS attacks or port flooding on the OpenVPN UDP port. Port scanning to determine which server UDP ports are in a listening state. Buffer overflow vulnerabilities in the SSL/TLS implementation. SSL/TLS handshake initiations from unauthorized machines (while such handshakes would ultimately fail to authenticate, tls-auth can cut them off at a much earlier point).Another thing you can do other than just trying to hide your port by using non standard openvpn port, which I am not a real fan of anyway. The whole obscurity thing point of view when it comes to security - but it help reduce log spam sure. Is limit what IPs can even talk to your ports via your own rules, like blocking known scanners, or known bad actors IP space - many a list can be used for those. I use geoip lists from pfblocker - so for example only US based IPs can talk to my open ports - don't have any users what would be coming from other than US IP space, just remember if your going to travel you might want to add were your traveling too allowed if your going to want to access your vpn, or other services. My buddy just took a trip to Ireland, so I opened up access to my plex from Ireland IP space while he was on his trip, that sort of thing.
-
@gertjan thanks
Well I only have TLS Authentication right now :(
I will change it but my understanding is that I'll need to change the config of all clients, and they won't be able to connect until I do that, am I correct?
-
A solution might be : activate a second, more secure OpenVPN server, on a second port, and create client profiles one by one, help switching over all your clients one by one.
-
@blazestar pretty sure auth should drop stuff as well, you don't actually need to be using tls-crypt.. just tls-auth should work? Notice link I pointed too is about tls-auth..