ExpressVPN setup by beginner for beginners
-
This post is deleted! -
This post is deleted! -
Configure Outbound NAT rules
- The ExpressVPN manual setup documentation describes this process if my text-only descriptons are unclear.
<expressvpn pfsense guide>
-
Go to Firewall > NAT > Outbound
-
For the "Mode" field, select the radio button for "Manual Outbound NAT rule generation. (AON - Advanced Outbound NAT)"
Click the "Save" button under the Mode field. -
For all existing WAN NAT rules, use the copy option (double page icon) to replicate the rule. Modify the resulting new rule setting the "Interface" field to the new ExpressVPN interface that you set up and click Save.
Do this for all existing WAN outbound NAT rules. -
Click "Apply Changes"
- The ExpressVPN manual setup documentation describes this process if my text-only descriptons are unclear.
-
Check your setup using the ExpressVPN tools
- https://www.expressvpn.com/what-is-my-ip
- it should show the location of the ExpressVPN server for which you configured the OpenVPN client
- https://www.expressvpn.com/dns-leak-test
- it should show no DNS leaks detected
- https://www.expressvpn.com/webrtc-leak-test
- it should show no WebRTC leaks detected
- Check other web sites. Pages should load successfully
- https://www.expressvpn.com/what-is-my-ip
-
Other notes
- You can still run any VPN client (ExpressVPN application) software on your devices that are connecting through the pfsense firewall. HOWEVER - YOU MAY NOT BE ABLE TO ACCESS THE PFSENSE WEB CONFIGURATOR IF YOU DO THIS. If you cannot access the Web Configurator, make sure you disable/stop the VPN client software on your device and then try again to use the Web Configurator/pfsense IP address.
I recommend staying with this step and do not continue until you have the ExpressVPN configuration and any networks/VLANs/firewall rules working the way you want things to work.
- If things aren't working the way you want, I recommend changing all the firewall rules that you can to have "logging" turned on. Then use Status > System Logs > Firewall to try to understand what is going on due to the firewall rules and make adjustments. If there's a rule that is filling up your logs then make any firewall rules/setting changes (if needed), refresh the log view, and once you're confident that the rule is behaving correctly, turn off the logging for that rule.
!!Once you get things working the way you want, take a backup of this setup before you continue.
- Go to Diagnostics > Backup & Restore and create a backup file for your settings.
-
Section 2 - Setting up a floating block firewall rule/ "kill switch" rule
Add a rule to tag all VPN traffic
-
I set this up by following the video linked here. If you're having issues with the floating firewall/"kill switch" rule, cross-reference settings against the video from Lawrence Systems.
Youtube VideoThis firewall rule will tag all traffic coming from any interfaces/devices that you want to only use the ExpressVPN connection so that you can use additional rules to filter this traffic
-
Go to Firewall > Rules > LAN
-
Click the "Add" button with the up arrow
-
Fill out the options:
- Action: Pass
- Interface: <Choose your new ExpressVPN interface>
- Address Family: IPv4
- Protocol: any
- Source: choose "Single host or alias" enter the IP address of any devices/networks that will use the VPN tunnel. If you have all devices on 1 network/subnet, you can enter that. If you have multiple networks/subnets, either create multiple rules or create an alias under "Firewall > Aliases" and use that alias on this rule
- Destination: *
- Log: (I recommend checking this initially so you can confirm the rule behavior is working)
- Description: give it a name that is easy to pick out of a log (recommend starting with a standard unique word)... like "myrule-allow ExpressVPN devices and tag"
- Click the "Display Advanced" button
- Tag: enter a value to be used to tag VPN packes. Maybe "tagvpn"
- Gateway: <Select the new ExpresVPN gateway you're setting up>
-
Click Save
-
Click "Apply Changes"
Repeat creating this rule for any LAN, OPT, or VLAN Interfaces in pfsense that you are going to route through the ExpressVPN tunnel.
Add Kill Switch Floating Firewall rule
The intent of this rule is to prevent your tagged packets (from the OpenVPN interfaces) from going out over the normal WAN... you want them to only go out of your firewall over the ExpressVPN interface.
-
Go to Firewall > Rules > Floating
Click the "Add" button with the up arrow to add this as the first rule.- Action: Block
- Interface: WAN
- Address Family: IPv4
- Protocol: any
- Source: any
- Destination: any
- Log: check this box so the log will capture any traffic being blocked by this rule.
- Description: give it a name that is easy to pick out of a log (recommend starting with a standard unique word)... like "myrule-block tagged traffic from using WAN to access internet"
- Click the "Display Advanced" button
- Tagged: enter the same tag value that you used to tag packets on your OpenVPN rule.
-
Click Save
-
Click "Apply Changes"
Stay with this step and do not continue until you have your networks/VLANs/firewall rules working the way you want things to work.
- If things aren't working the way you want, I again recommend changing all the firewall rules that you can to have "logging" turned on. Then use Status > System Logs > Firewall to try to understand what is going on and make adjustments.
!!Once you get things working the way you want, take a backup of this setup before you continue.!!
- Go to Diagnostics > Backup & Restore and create a backup file for your settings.
!!Check MBUF Usage as an indicator of proper functioning!!
(update from July 2023)
After some time I was having issues with MBUF Usage (shown on the front page of the WebGUI) growing very quickly and things generally were not working well... web pages would load sometimes, other times not and I would have to restart the firewall when it filled up all the MBUF. I even added a custom parameter for MBUF allocation and gave it a large value, but there was obviously a problem as I could watch the number go up by 1000+ every time the front page refreshed. I found a post that led me to believe it was something in my OpenVPN client set up. I wish I was able to tell you exactly which change I made fixed the issue, but so far I have not been able to recreate the issue by trying to put things back the way they were. But if you have this issue, seems it is most likely related to a setting in your OpenVPN client. -
-
The End
(sorry for all the self-replies and bad links... the Spam filter is not happy with me)
I'll try to clean it up later when my reputation score improves.... correction... I won't be able to edit it due to the 1 hour edit time limit.
-
@123123 The "openvpn-client-import" package is no longer available. Do you have any instructions for entering the settings manually? Would also help to give details on the Custom Options
-
@wendellkbest said in ExpressVPN setup by beginner for beginners:
Would also help to give details on the Custom Options
Right now, I've a connection to expressvpn with this very minimal :
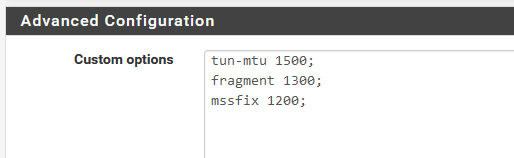
as these 3 settings do not exist in the pfSense GUI, but they are needed (I guess) when using ExpressVPN. Without them : failure to connect.
I've removed all other proposed custom options.
Also, I've set "compression" to 'no' :
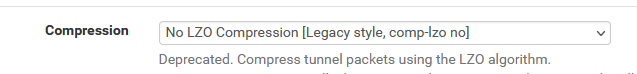
but the more future proof :
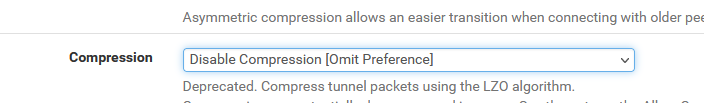
also seems to work.
I can ping test using my EXPRESSVPN interface :
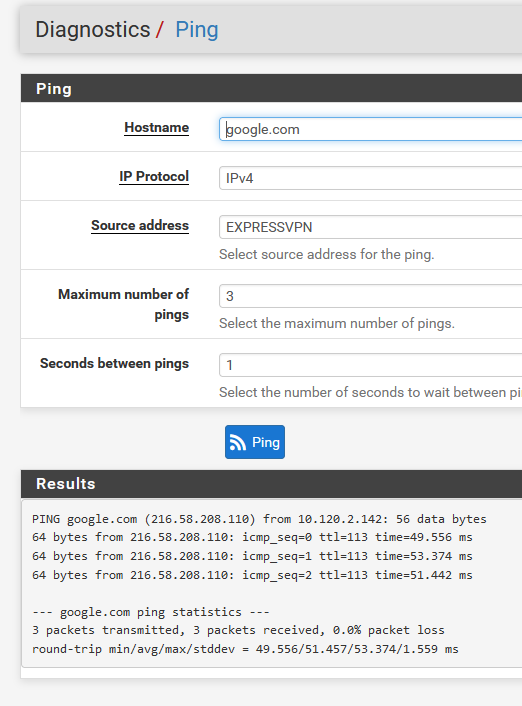
and the OpenVPN client: Express VPN interface :
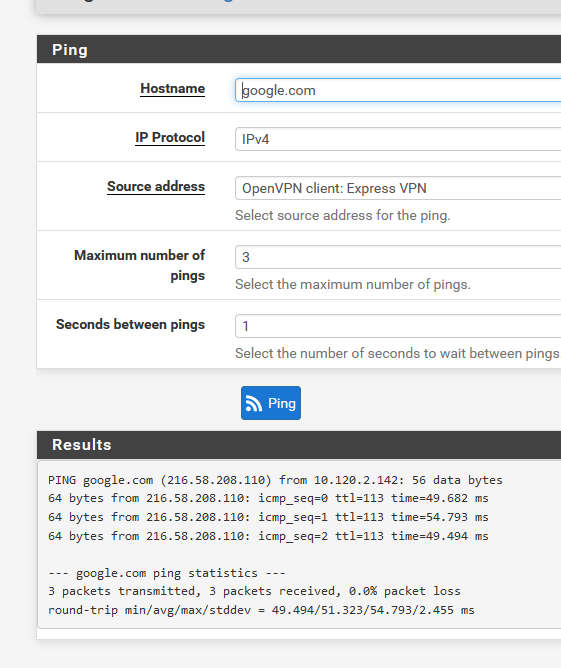
Note : I didn't test any routing at this moment, as I use the client VPN only 'when really needed'.
Also : The pfSense GUI is only, as usual, the front end.
pfSense uses the classic openvpn binaries and configuration files.My /var/etc/openvpn/clientx/config/opvn (x can be 1, 2 etc) looks like this right now :
dev ovpnc3 disable-dco verb 3 dev-type tun dev-node /dev/tun3 writepid /var/run/openvpn_client3.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 auth SHA512 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown local 192.168.10.4 engine rdrand tls-client lport 0 management /var/etc/openvpn/client3/sock unix remote france-strasbourg-ca-version-2.expressnetw.com 1195 udp4 pull auth-user-pass /var/etc/openvpn/client3/up auth-retry nointeract remote-cert-tls server capath /var/etc/openvpn/client3/ca cert /var/etc/openvpn/client3/cert key /var/etc/openvpn/client3/key tls-auth /var/etc/openvpn/client3/tls-auth 1 data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:AES-256-CBC data-ciphers-fallback AES-256-CBC allow-compression asym resolv-retry infinite fast-io sndbuf 524288 rcvbuf 524288 tun-mtu 1500 fragment 1300 mssfix 1200 route-nopullYou can see that the custom option are added at the end with an extra blank line after each line. And a final "route-nopull" is added at the end.
Always check & compare this file with the original Express config.ovpn file.
Difference might exist, as we can't know what openvpn (version) ExpressVPN is using.
pfSense 23.01 uses :[23.01-RELEASE][admin@pfSense.omg.net]/cf/conf: openvpn --version OpenVPN 2.6_beta1 amd64-portbld-freebsd14.0 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] [DCO] library versions: OpenSSL 1.1.1t-freebsd 7 Feb 2023, LZO 2.10 ....Nice, a beta version

-
@wendellkbest said in ExpressVPN setup by beginner for beginners:
@123123 The "openvpn-client-import" package is no longer available. Do you have any instructions for entering the settings manually? Would also help to give details on the Custom Options
-
If you want to enter the certificate details manually, you can follow the manual setup document available on the ExpressVPN site.
But I would double-check the pfsense Package Manager whether the import package tool is available (or maybe is already installed on your pfsense).
https://www.expressvpn.com/support/vpn-setup/pfsense-with-expressvpn-openvpn/
-
Now that I got some reputation points, I was able to update the old posts. I updated the original posts with details about the "Custom Options" field values, but my intent was for the instructions to be somewhat dynamic as things change over time (like if ExpressVPN updates the .ovpn files or something like that).
-
-
@123123 said in ExpressVPN setup by beginner for beginners:
(like if ExpressVPN updates the .ovpn files or something like that)
Or the OpenVPN version used by pfSense changes !
Or the OpenVPN version used by Express changes.
For the normal Express clients, this is a none-issue as they 'just have to upgrade their Express VPN client and done.
When you use an VPN ISP with pfSense, you don't use their client.
You and I and many others do things 'the hard way, also known as 'manually'.
When the version changes, parameters can get declared 'not wanted' - and new parameters can get added.
For some, there will be a pfSense GUI equivalent so you handle their usage with some ease.
For some, the custom option box is needed.Right now, pfSense ans Express seems to be in sync, as my custom options box contains the bare minimum :
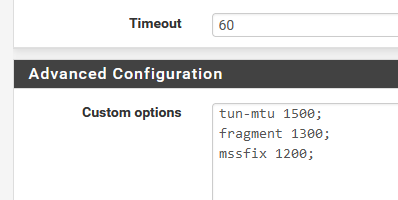
I'm pretty sure these parameters, fragment and mssfix, the decimal values, are not optimal.