2100 Can't ping firewall on second VLAN
-
I've got the typical setup where I've got two internal VLANs.
The first one, LAN (192), works fine.
The second one, BUSINESS (172), works fine for almost everything but it can't ping the firewall or use the local DNS resolver.
The VLAN config is:
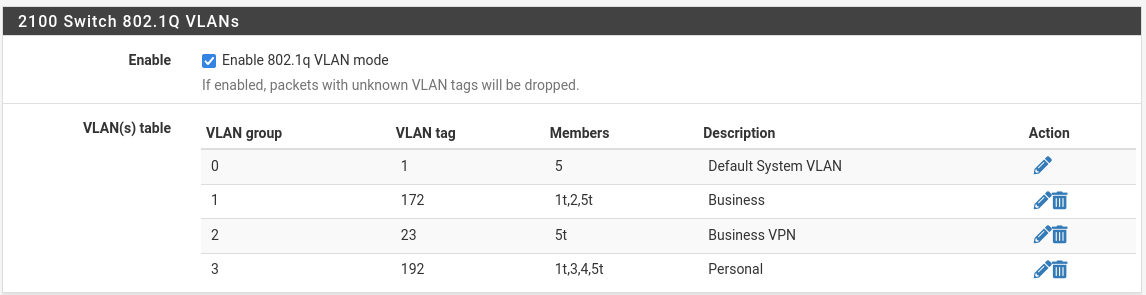
Ports:
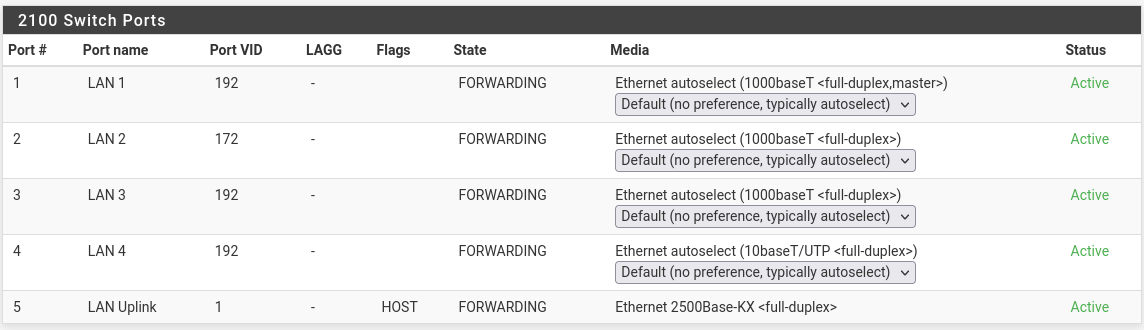
Interface assignments:
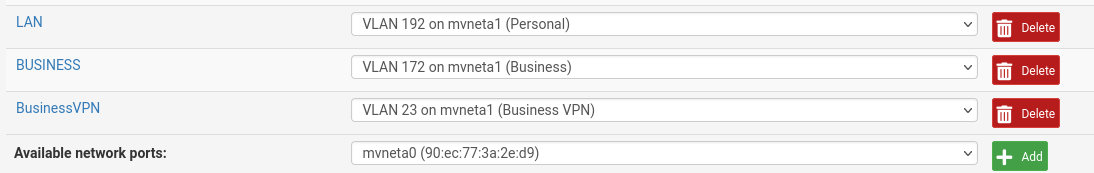
Rules are any/any just for testing.
I can:
Directly connect a host to port 2.
Get a DHCP address in the correct range.
Send a DNS request towards the firewall.
Packet capture it arriving on the correct interface.
See it being accepted by the firewall by turning logging on in the accept rule.But using using truss I can see the unbound process never sees the request.
ping doesn't work either but there's no process to trace to prove that.
All other traffic which doesn't have the firewall as the destination works fine.
I can access between the two VLAN interfaces and use them both to go out to the net.Has anybody see this before?
I've been over the config again and again and I don't think I've missed anything.Cheers,
Scott -
It was an IPsec VPN!
If the near and far networks overlap then traffic heading for the firewall IP needs to bypass the VPN.
That's normally sorted out by the 'Enable bypass for LAN interface IP' setting with is on by default.
However, that only handles the lan interface and not any other lan-type interfaces which get created.
The fix was to add an 'Additional IPsec bypass' rule.
I'm not sure if this is a bug or not.
Should there be a list of interfaces to bypass rather than just the lan interface being special?Cheers,
Scott