Instant Website Redaction Technology Not working
-
Hello Fellow Netgate Community Members,
I wanted to share some topics for discussion and possibly create a community resolution to this issue I have noticed.

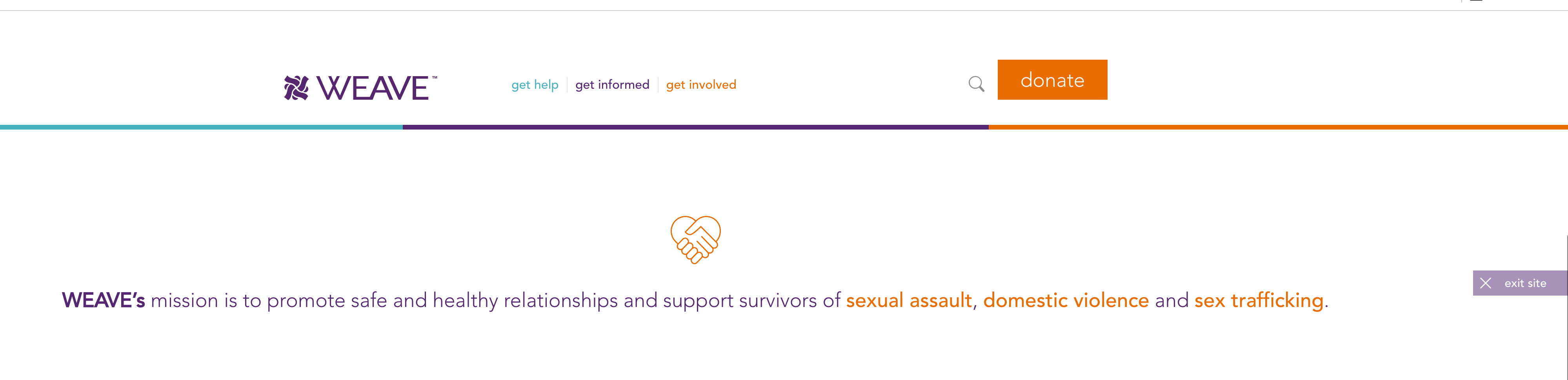
(Women Escaping A Violent Environment (WEAVE))WEAVE's website has instant website redaction technology that auto navigates away from the the website for privacy of the user when in need if they need to report an issue in a invasive environment. (EXIT BUTTON)
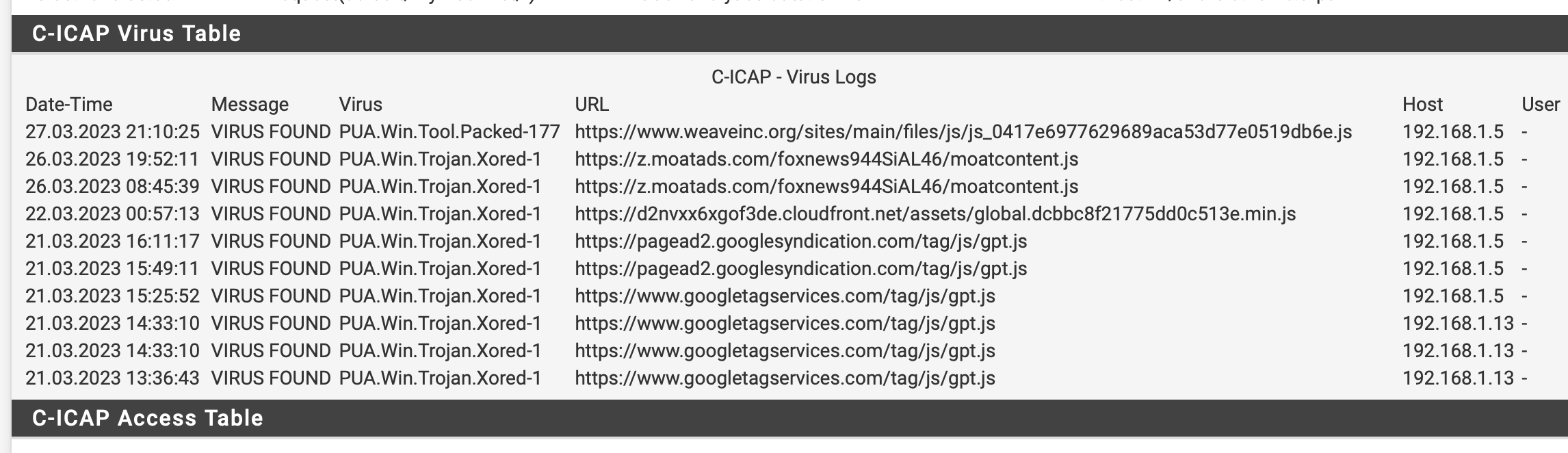
If this firewall was deployed in a business environment and someone was trying to report issues you can notice that the C-ICAP system will block the redirecting technology. This can leave the user of the website at great risk now without the auto redaction use.
This website deploys a instant website redaction technology that will hide the website from the abusers. Again this is being flagged by the Clam AV software.
How can the firewall automate some ethics with this use for when this should be allowed to be used example: WEAVE and or not be allowed example: Virus use abuse of cookies tracking spy technology.
Moreover what technology or code improvements can work hand and hand with firewalls to allow instant redaction and or warn that it will not work on such network if needed.
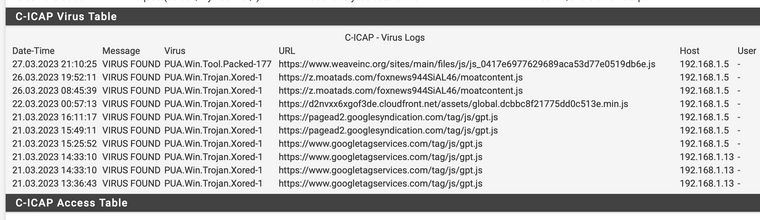
(The Instant Redaction Technology Failed in this test)Issue: Clamav cannot distinguish the ethics currently with use of such advanced redaction technology.
How can we code in some ethics for this situation?
-
@jonathanlee To be honest. Why are we even using Squid in this case? There is really no reason for this tech to be used in this way.
-
@michmoor most all advanced next generation firewalls use SSL certificates to decrypt and inspect traffic. This use is not out of the normal for it to inspect for viruses. Again why does it see this redirect inside of clam AV as a PUP potentially unwanted program. I don't know. Palo alto and many other firewalls work the same way for security useagae. It's clam AV that sees it as a virus, if it's disabled it will allow the redirect, again viruses abuse this technology so, again where does the ethics of what is a proper redirect come into play here?
-
@michmoor I think clam AV has it as a false positive.