Basic firewall rule not working?
-
Hello fellow Netgaters. I recently installed my first netgate and began playing around with it. I have an interface setup with my homenetwork on its own subnet, and then a worknetwork on its own subnet. I don't want these 2 networks to talk to eachother. I figured I would setup a firewall rule that blocks any traffic between the two networks, and testing with a simple ping ICMP message it does not get blocked.
This seems like it should be so simple, what am I missing here?
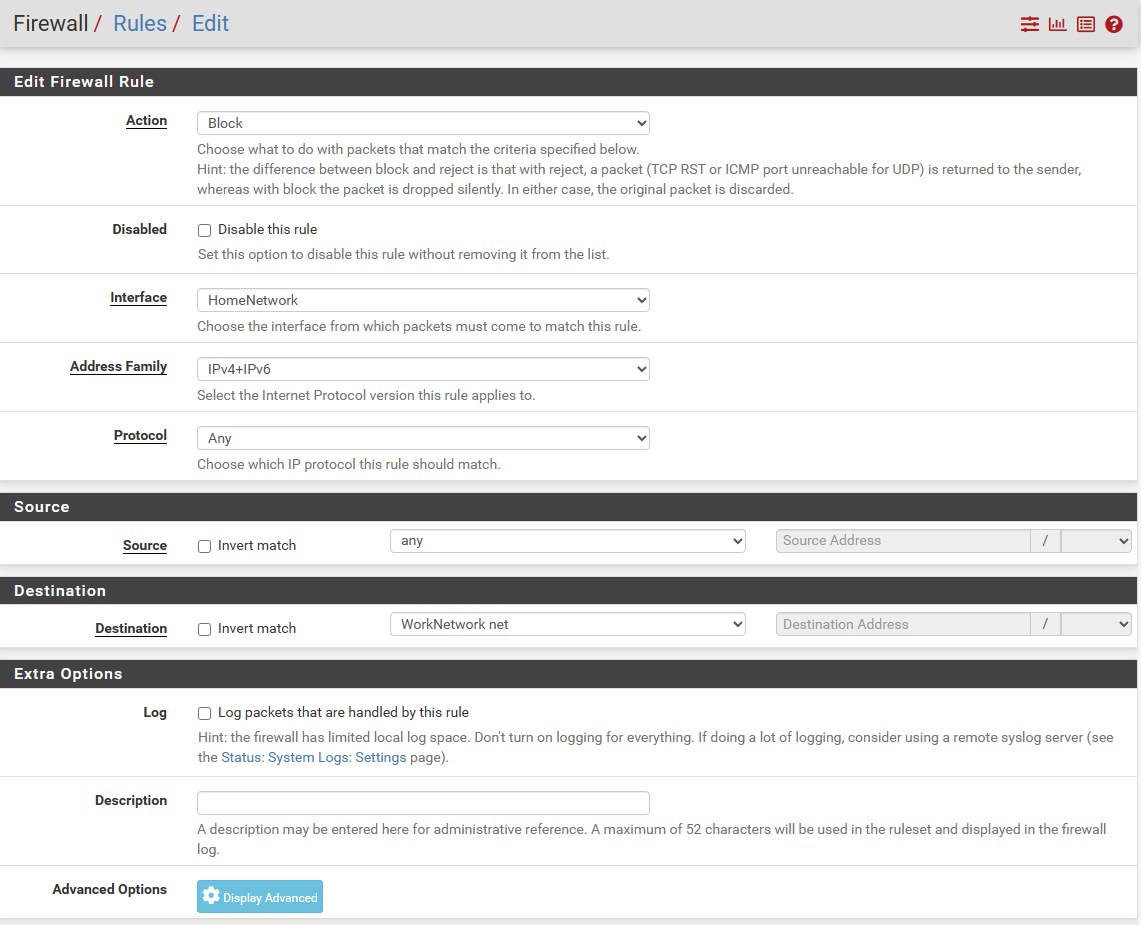
-
- I would log it just to see if the rule is being triggered
- Rule looks correct but to my first point do you see it being triggered?
There could be state already created in pf so thats whats being used in which case you need to kill those sessions.
-
@michmoor Thank you for the quick reply. I have it logging now but nothing is triggered. I had a couple floating firewall rules for pfblockerNG, i disbled those temporarily and same result. These are the only rules configured on that homenetwork interface.
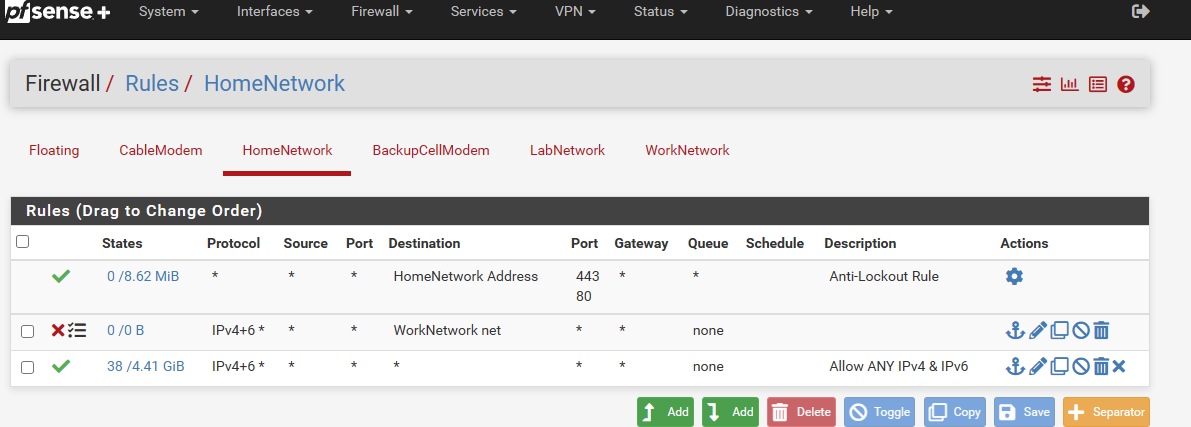
-
@mrchuck101 your blocked rule is not matching traffic. Have you tried killing the states on your last rule? The X button will do it
-
@michmoor that did the trick thank you! didn't realize what that little X button did.
-
IMO you're generally better off letting the default deny do this rather than having the HomeNet be able to connect to any destination outgoing wise.
So IMO a better rule layout would look something like:
- Source: HomeNet Destination: HomeNet Allow
- Source HomeNet Destination: RFC1918 inverse match alias (so all public IP space) Allow
I simplified things but I think you'll get the idea.
The way I personally do it is just like above except that I also have a deny all rule to "This Firewall" with acceptions above for management traffic and DNS.