Looking for local probers
-
I am looking for local hosts that might be scanning ports locally. Probes that don't pass through the router will have to be discovered in other ways. However, there are some probes that attempt to reach go beyond the local subnet. To find those, I set up this rule.
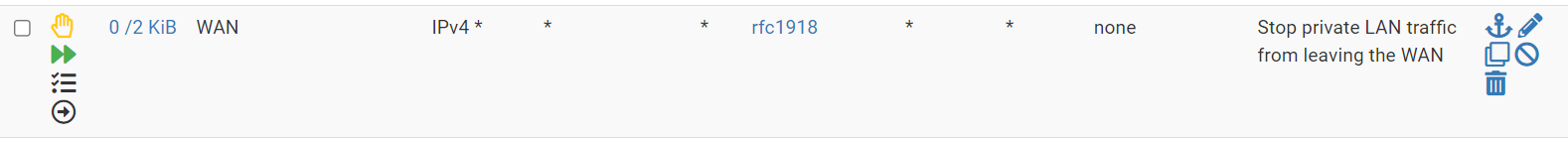
Now I know this doesn't help us pick up activity that stays on the L2 LANs, but it does pick up traffic with a destination that's not in our local LAN list. For example, I am seeing this rule log many requests to 192.168.49.1 and 10.134.15.43 some ICMP and some TCP:S. Neither subnet is one of ours, so they are routed to the WAN and the above rule is logging them.
The log entry shows the source as the WAN address. How do I write a rule that will report the originating host address? Is there a way to log the requests leaving my LAN interfaces that are destined for rfc1918 subnets that aren't used locally? I can't just log all outbound rfc1918 traffic because that will capture legitimate cross VLAN activity.
Any help you might give would be greatly appreciated. And as always, I apologize in advance if this is a repeat or otherwise dumb question.
-
@bigtfromaz if you want to see this traffic from source IP, you would need the rule on the interface where it inters the firewall, for example the lan interface.
The reason your seeing the wan, is traffic from lan side interfaces has already been natted to the wan IP - and you stopping it from leaving, ie outbound
-
@johnpoz I knew that but am unsure how to make it happen.
Would this get it done?
-
Create an Alias containing the 11 or 12 rfc1918 subnets that we use. Call the Alias "FooNets".
-
Create an immediate inbound Floating Rule, on a lightly used test LAN interface that Blocks and Logs all TCPIP/UDP packets from Any, where the destination is an Inverted Match to "FooNets".
-
Turn it on and generate a test packet from a test host on the test LAN.
-
Confirm the block in the logs and if it looks good, add the remaining LAN interfaces to the Floating Rule.
I was hoping there would be a way to avoid maintaining a manual list of LAN subnets but can't see any other way to do it.
Thoughts?
-
-
@bigtfromaz if all your wanting to do is figure out where the traffic coming from might be easier to just create a floating rule to the IPs your seeing and have it log, and put it on all your lan side interfaces.
If the goal is going forward and you want to see any traffic to any rfc1918 that you do not own.. Then yeah you would want to allow traffic to the networks you own, which would require either specific rules or an alias sort of rule to allow the traffic you want to allow to your other rfc1918 networks. And then a block to all other rfc1918 before you allow to the internet, etc
-
That did the trick. I found a few things to investigate. Here are the rules:
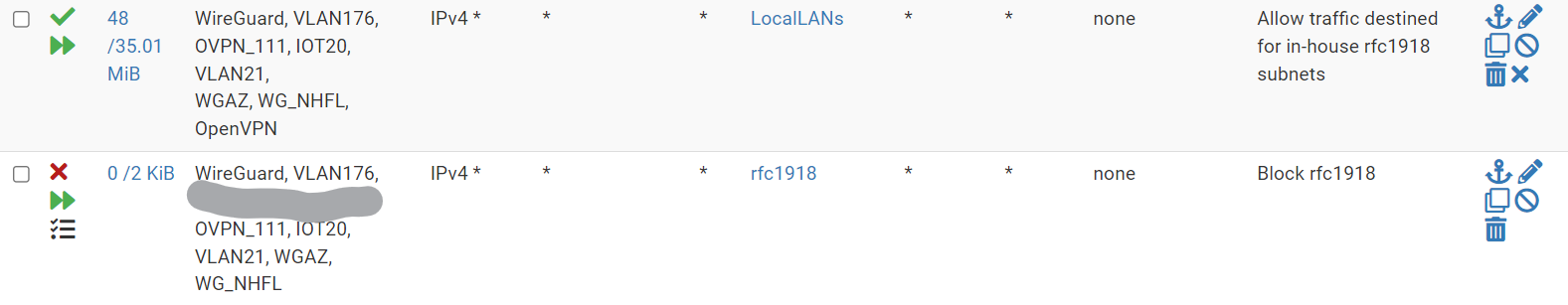
Thanks for the help. It is greatly appreciated.