Bye Pass traffic with two different P2P tunnel using Open VPN
-
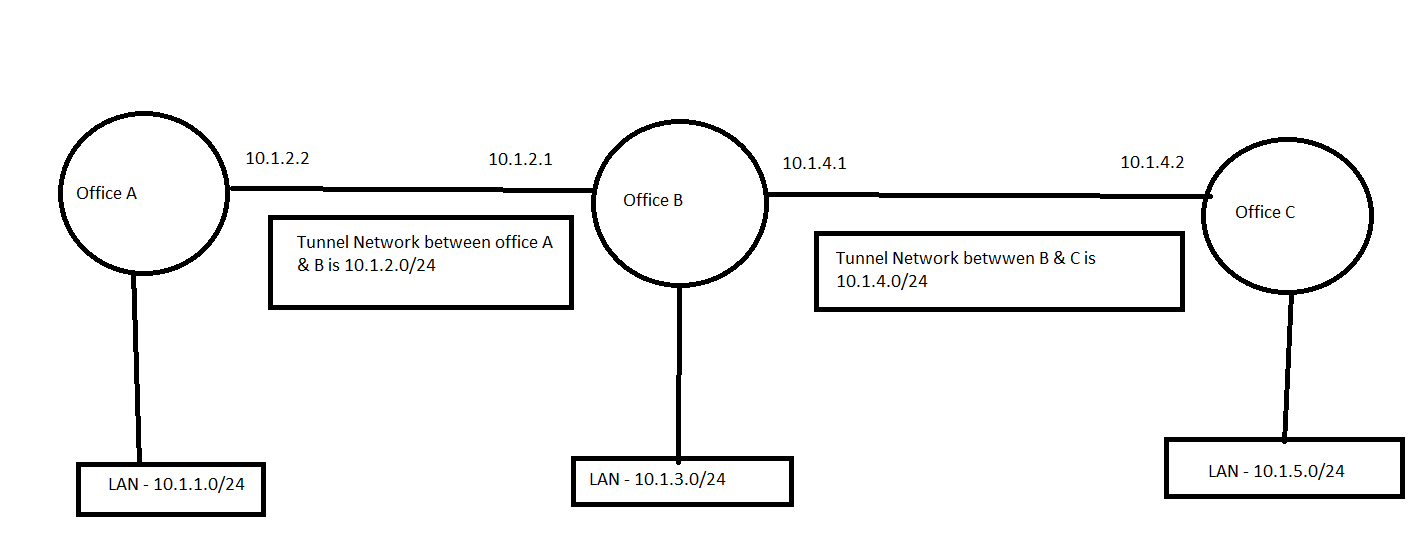
We have 3 offices in different locations, we have a peer to peer tunnel between office A & B and We have another Peer to peer tunnel between Office B & C. We can communicate between Office A LAN to Office B LAN, also can communicate between Office B LAN to Office C LAN.
Here we want to establish connection from Office C LAN to Office A LAN via peer to peer tunnel office B & C and peer to peer tunnel office B & A (10.1.5.0/24 → 10.1.4.0/24 → 10.1.2.0/24 → 10.1.1.0/24). Can anyone help me with this ?
-
@gokulapandi
You simply have to add the respective remote subnet to the "Remote Networks" in the OpenVPN settings at A and C.So at A you will have then:
10.1.3.0/24,10.1.5.0/24and at C:
10.1.3.0/24,10.1.1.0/24Also ensure that the firewall rules on all involved incoming interfaces allow the access.
-
Hi viragomann,
Thanks for your response, As you mentioned, i have already added the remote network at A & C.
At A, I Have allowed inbound/outbound for 10.1.5.0/24, 10.1.4.0/24, 10.1.3.0/24 Network to LAN Network in LAN Rule and Open VPN rule.
At C, I have allowed inbound/outbound for 10.1.1.0/24, 10.1.2.0/24, 10.1.3.0/24 Network to LAN Network in LAN Rule and Open VPN Rule.
At B, I have allowed inbound/outbound for 10.1.1.0/24 and 10.1.5.0/24 Network to other Network (10.1.2.0/24, 10.1.4.0/24, 10.1.3.0/24) in ** only Open VPN Rule.**
I have configured and tried all the combination firewall rule as above mentioned but still not working.
-
@gokulapandi said in Bye Pass traffic with two different P2P tunnel using Open VPN:
At A, I Have allowed inbound/outbound for 10.1.5.0/24, 10.1.4.0/24, 10.1.3.0/24 Network to LAN Network in LAN Rule and Open VPN rule.
At C, I have allowed inbound/outbound for 10.1.1.0/24, 10.1.2.0/24, 10.1.3.0/24 Network to LAN Network in LAN Rule and Open VPN Rule.Rules need only to be added to the incoming interfaces, i.e. the VPN interfaces.
The tunnel networks are not needed to pass, as long as you do not masquerade the traffic with an outbound NAT rule on the VPN interface.
At B, I have allowed inbound/outbound for 10.1.1.0/24 and 10.1.5.0/24 Network to other Network (10.1.2.0/24, 10.1.4.0/24, 10.1.3.0/24) in ** only Open VPN Rule.**
If you have stated the destination networks, you need 10.1.1.0/24 and 10.1.5.0/24 here.
-
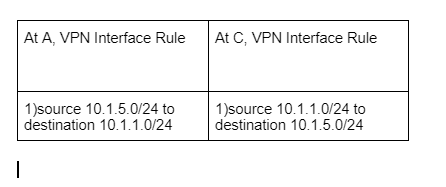
Hi viragomann,
Will this work ?
-
@gokulapandi
Yes should work for A and C.
But if you restrict access on B to certain subnets as well, you need to add the same rule as you have at A on the interface connected C and that one you have at C on the interface connected to A.