openvpn server and client simultanous no internet
-
i got a vps with pfsense 2.6 in a data center with a static public ip, i am connecting via openvpn to it, to use unbound with pfblockerng as dns server this works fine. Now i'd like to connect the pfsense itself with a server of protonvpn via openvpn to hide the ip of pfsense. During setup, I followed the following instructions: ProtonVPN Setup
The Connection between pfsense and Protonvpn is up and running, when i connect with my pc to pfsense the connection works fine, even the gateway of NETHERLANDPROT is reachable through the first opvenvpn connection but the internet is unreachable e.g. a ping to 8.8.8.8 fails. A Ping on pfsense via the NETHERLANDPROT Interface to 8.8.8.8 works properly.
-
@skonyt
Without knowing your local networks the screenshot of the outbound NAT is quite useless.But I'm wondering, what's the benefit of the LAN rule.
Is your OpenVPN access server configured to force all client traffic over the VPN?
-
@viragomann sorry for that
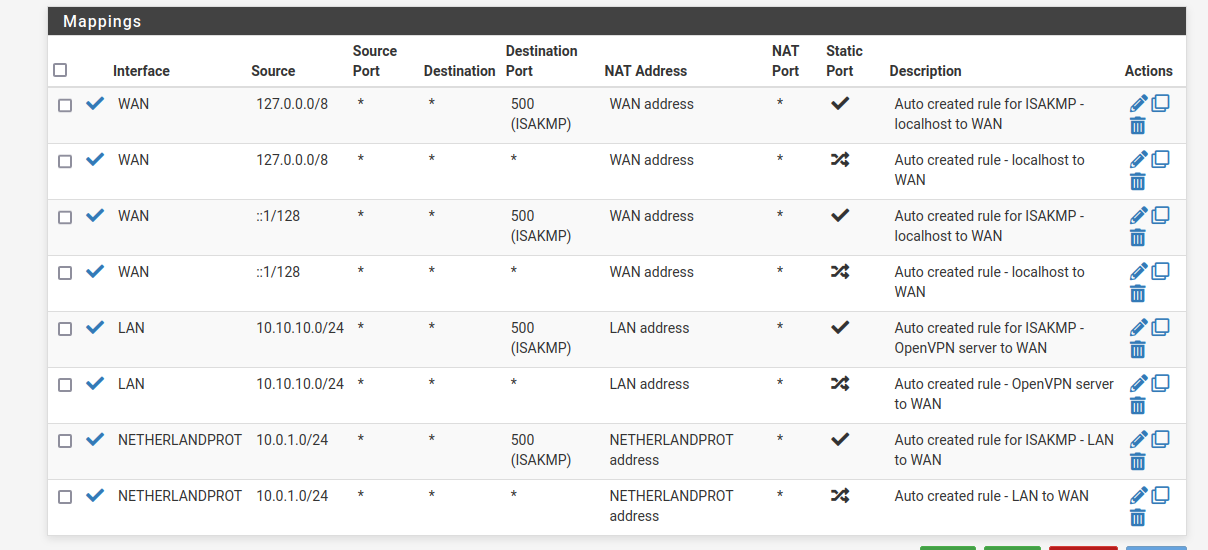
LAN 10.0.1.10/24
openvpn server tunnel 10.10.10.0/24According to my logic the lan rule redirects the incoming traffic from the openvpn server tunnel to the lan interface and the rule in the line below redirects the lan traffic in the NETHERLANDPROT Interface
yes i activated Redirect Gateway on Server Setup
-
@skonyt
So you're missing a rule for the OpenVPN tunnel network on the NETHERLANDPROT interface.
Copy the last rule and replace the source with 10.10.10.0/24.According to my logic the lan rule redirects the incoming traffic from the openvpn server tunnel to the lan interface and the rule in the line below redirects the lan traffic in the NETHERLANDPROT Interface
Outbound NAT rules redirect nothing. They simply do source address (masquerading) or source port translations.
This is necessary on outgoing interfaces like WAN and the VPN, because outside there, the interface address is the only known one.With such rule on LAN, the destination devices sees access coming from pfSense IP instead of the OpenVPN client IP.
-
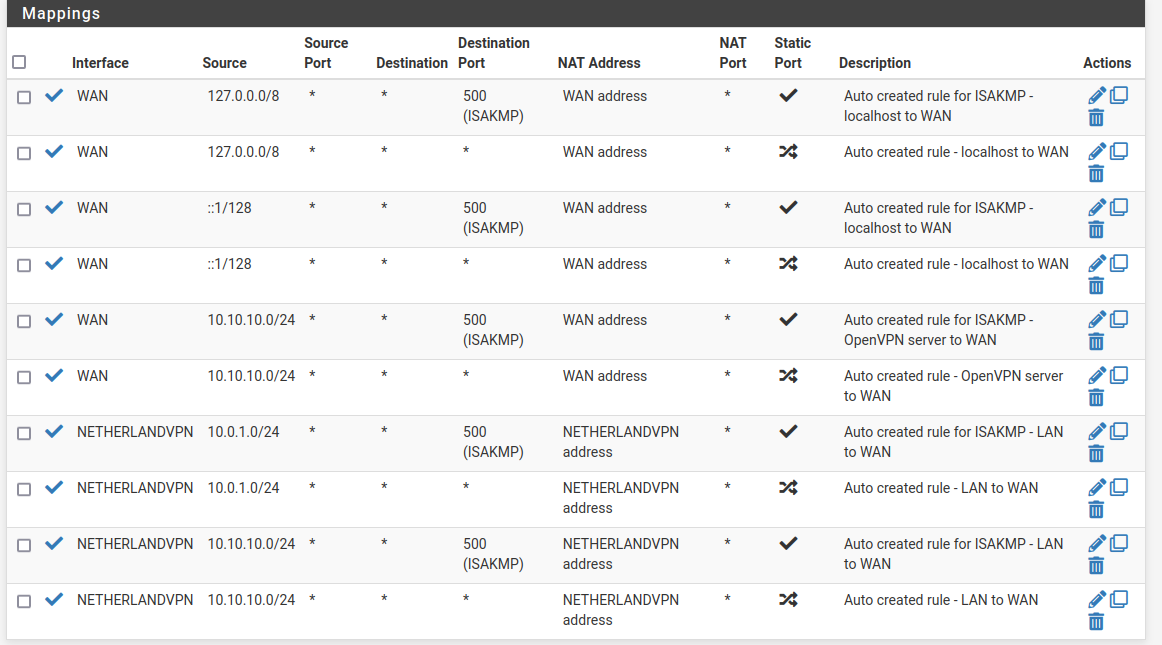
@viragomann in the meantime i tried something from another tutorial but it failed and i had to rebuild my server. Now i have set it up as before and have added the rule according to the above information. Now i have internet but the openvpn server doesn't use the openvpn client interface. When i delete the last two rules and set the interface of the rules in the fifth and sixth line to NETHERLANDVPN the openvpn server have no internet.
Note: The Rule on Interface NETHERLANDVPN Pass Any Any to Any is set
-
@skonyt
Try to remove the check from "Don’t pull routes" in the VPN client settings.
I'm wondering, why Proton is suggesting to check this. Other VPN providers push the default route and want it to be used as well.Even this only helps if Proton pushes the default route. If they don't you have to state NETHERLANDVPN as default gateway in System > Routing > Gateways > Default gateway.
-
@viragomann yes that works i removed the check from "Don't pull routes" in the VPN client settings. Now only the Proton VPN Server IP is visible, but now the dns resolver has a strange behavior, unbound resolves queries, but pfblockerng blocks nothing. I tried to remove the check from "Pull DNS" in the OpenVPN Client Settings, and i blocked DNS Traffic on LAN Interface and NETHERLANDVPN Interface. Or is there another way for pfsense to use foreign dns servers? But i afraid that this problem is unsolvable, because it might be that pfblockerng isn't designed for this usecase, because i've seen in other forum topics, there is no solution for comparable setups.
-
@skonyt
Since the NETHERLANDVPN is now an outbound interface, you will have to add it to the outbounds in pfBlockerNG.However, from resolving it's not clear to me what you try to achieve. Do you want to let the local Resolver do the resolution or you want to use a public DNS server on the VPN clients (this bypasses DNSBL of course) or do you want to use the Resolver and forward it's request to a public server through the VPN?
Consider that when using the local Resolver in default mode, it might end up into DNS leaks.
-
@viragomann I only became aware of the DNS leak problem now, from my point of view there is no really secure solution (except TAILS which is not very suitable for everyday use), either I give the VPN provider the data from my DNS queries or I hide my DNS queries from the VPN provider, but the target server can see the pfsense IP address which makes the use of the second tunnel pointless. Because its harder to profiling user behavior with ip adresses as with dns quieries because in most cases behind one ip adress there are multiple dns records. Or do you see an other solution for this problem? (except renting several VPS from different providers in different countries and setting them up on all pfsenses, this will be very complex and expensive, and the usage of multihop vpn by one provider is useless in my opion in the case of tracing)
-
@skonyt said in openvpn server and client simultanous no internet:
Because its harder to profiling user behavior with ip adresses as with dns quieries because in most cases behind one ip adress there are multiple dns records
I don't agree with that. The clients will access any host, which they had requested before from the DNS anyway (apart from local DNS caching).
So on the basis of both logs you can generate the same profile for my understanding. I'm missing something?So I don't see any need to hide DNS requests from the VPN provider. If you don't trust him you shouldn't deal with him.
But if you want to hide your DNS requests anyway, you can do DoT requests. You can configure this on pfSense and forward requests to a proper DNS server, however, you would have to direct out all DNS request through the VPN then. Alternatively you can set up DoT on the clients directly.
-
@viragomann Thank you very much for your answers, in particular I did not consider that the error could be in the official tutorial of ProtonVPN, probably I will set up the variant "Client - pfsense - ProtonVPN" with DNS over HTTPS.