VLAN 1 Best Practices?
-
Hey,
I stumbled over similar questions for my home network. Read about never ever using vlan 1 (default vlan in cisco speech as well as native vlan).
So I set my management vlan away from vlan 1.
My concern was that some guest might disconnect the trunk LAN cable and plug a guest device in. I tried to protect vlan 1 from being used, so now no device gets an ip there, since now only tagged packets are run (from productive vlans) the switch puts all untagged in a vlan (native vlan 99) where no ip, no dns no nothing is possible. I tested it a few times an yes, was quite isolated.
The switches and firewall sit in closed racks. Unused ports are all offline.
It is IMHO not necessary for my home network, same goes for pfsense, cisco switch and so on...it is a hobby and I like to learn about that stuff, since I have no IT or networking background on a professional level at all.
:)So, go for it and try out stuff, even if it would be overkill.
-
@the-other said in VLAN 1 Best Practices?:
So, go for it and try out stuff, even if it would be overkill.
Agree - Is there a real reason to run eap-tls on one of my wifi ssids - no not really. If anything it makes my life harder. But hey its fun to see what you can do with what amounts to cheap hardware and some understanding an configuration.
A close friend and colleague of mine for 13 some years at my previous gig that is well versed in all things networking, he runs some soho wifi router he got from his ISP and its all just 1 flat network.. Drives me nuts heheh.. But to him IT is just a job.. For me its also a passion and hobby not just a job... I can not get enough of all things techy..
Do I really need a sg4860 for my home network ;) most likely not, do I need small business class managed switches from cisco - no not really ;) Do I need unifi APs with multiple vlans.. Again most likely not - could prob get away with some isp wifi router.. But then again that network would suck!! hehehe
And what would I do with my free time other than play with my network and help others with theirs.. It would leave much more time for drinking - hmmmm ;) maybe I should rethink this whole setup hahahah
-
@uplink Regarding best practices involving VLAN 1, I'd implement alt setup 1, but with some small changes:
-
Leave the parent LAN adapter(s) unaddressed and use all tagged VLANs
-
Disable VLAN 1 on your switch if possible
-
Continuing down the best practice trail, create an unused vlan (i.e. 666, 1999, etc) and change the native VLAN to that unused VLAN on all your switch ports. But TBH, this step is probably overkill in a home setup.
On the other hand, in a home setup, most of this stuff is overkill in most cases. IMO, in a home setup... if someone breaks into your house to do nefarious things... they're likely not there to plug into your switch to leverage VLAN 1 exploits... they're just going to take all your gear ;)
-
-
@marvosa said in VLAN 1 Best Practices?:
they're just going to take all your gear ;)
exactly..
The only problem with trying to disable vlan 1, unless you have higher end stuff - full managed enterprise grade its unlikely the switches can be managed with a tagged vlan..
Same goes for other stuff, example the unifi AP for the longest time - with countless people asking for it, you could only manage the AP via untagged traffic.. It doesn't have to be vlan 1 on your switches, but it did have to be untagged. A while back they finally added the ability to manage the APs via a tagged vlan.
-
Hey @marvosa , @sic0048 , @johnpoz , @the-other
Thank you so much for all of the helpful advice! I think I understand the whole VLAN 1 situation bit better now. After hearing what you all had to say, I would agree, it’s probably overkill to move away from VLAN 1 in a home environment. But, like many of you, I also have a passion for tinkering with this stuff and learning how the “pros” do it.

So, I think I will attempt to “black hole” or move off of untagged VLAN 1 entirely. However, just looking at my networking equipment, it might not be that easy (just like @johnpoz said).
My Networking Equipment Abilities/Limitations:
- pfSense Firewall (running on bare metal): I don’t see a way in the GUI to disable untagged VLAN 1 or change the ID from 1 to something like 666.
- QNAP Switch (Layer 2): There is no way to change the default untagged VLAN 1 to something like 666 in the switch. However, I can unbind VLAN 1 from all of the ports and just run different tagged or untagged VLAN IDs on the ports.
- Ubiquiti LR6 WAP: I sounds like I can manage it via tagged VLANs now. I suppose this means I should be able to setup the SSIDs using tagged VLAN IDs instead of having at least one SSID with VLAN 1.
Given my current setup, I had a few questions:
- Is there a way in the pfSense GUI to change the default untagged VLAN ID from 1 to something else in pfSense?
- If I can’t change the default VLAN 1 ID, could I just change the Interface Assignments for LAN = IGC1 (in my case) to a VLAN (example: LAN = VLAN 10 on IGC1 – lan (MGMT))? Wouldn’t that effectively disable the untagged VLAN 1 LAN network and set the router to now operate on a VLAN?
Again, any suggestions would be very appreciated

-
@uplink said in VLAN 1 Best Practices?:
I can unbind VLAN 1 from all of the ports and just run different tagged or untagged VLAN IDs on the ports.
And then how will you get to the switch IP to manage it? If you make the management vlan 666 for example that is untagged.. This is no different than the switch just calling it vlan 1..
As to pfsense - where do you think there is vlan 1 setting? Normally pfsense doesn't have switch ports.
So maybe you not fully understanding what vlan 1 is?? Vlan 1 is just the vlan ID the switch uses for the default untagged traffic. You can isolate other vlans that are untagged enter leaving a port with another ID number 2, etc. But if the traffic is untagged what does it really matter what the ID number is on the switch, be it 1, be it 2, be it 100..
Where in pfsense do you see vlan 1 setting?
-
Where in pfsense do you see vlan 1 setting?
Yep, I already mentioned that I was unable to find a way to change or the ID of the native untagged VLAN ID in pfSenese. That’s why I was asking.
If you make the management vlan 666 for example that is untagged.. This is no different than the switch just calling it vlan 1..
You’re right, I would be effectively be replacing untagged VLAN 1 with another untagged VLAN (5,100,666,etc.). It seems I wouldn’t gain much by doing that. Dumb idea.
So maybe your not fully understanding what vlan 1 is??
LoL, I 100% agree, I don’t have a full understanding, but I’m trying to learn

Moving on... I was looking at the suggestions from @marvosa (see bulleted list) on getting away from using VLAN 1. Sure, I could “delete” or unassigned the parent LAN adapter and keep only tagged VLANs on the router, but I don’t think I can get the switch itself on a tagged VLAN. In the switch’s IP settings, I can’t see a way to specify a VLAN ID, so I assume it needs to be on an untagged network. Also, there isn’t a management VLAN ID option either.
From @marvosa
• Leave the parent LAN adapter(s) unaddressed and use all tagged VLANs
• Disable VLAN 1 on your switch if possibleSo, considering I cannot get the switch to operate on a VLAN, then I think all I can do is:
-
Move all of the devices (expect the switch of course) off of untagged VLAN 1 and into a tagged VLANs
-
Remove untagged VLAN1 assignments from all of the ports on my switch (except of course the trunk)
Alternative Setup 3:
igc0: WAN
igc1: LAN (Default untagged VLAN 1) - 192.168.1.0/24 – Just the Switch
igc1: VLAN 10 - 'Server' - 192.168.10.0/24 - NAS, WAP, VM Servers, WAP
igc1: VLAN 20 - 'IoT' - 192.168.20.0/24 - PCs, Phones, Printer, IP Cameras, etc
igc1: VLAN 30 - 'Work' - 192.168.30.0/24 - Work PCMy apologies if I'm all over the place with this stuff. I'm really trying to wrap my head around VLANS, but it's making my head spin.

-
-
@uplink said in VLAN 1 Best Practices?:
Move all of the devices (expect the switch of course) off of untagged VLAN 1 and into a tagged VLANs
You don't put devices on tagged vlans - while you can, that is not normally done.. The vlan you want a "device" on is untagged at that port.. Windows, linux, etc. don't normally expect a tag.. Nor does your printer, etc. etc
Tags are for when you carry more than one vlan over the same wire.. Ie from switch to switch, or from router to switch or from switch to access point, etc.
Normally PCs, Printers, Camera's etc. door bells, TVs, DVRs, apple tvs, any kind of end user device that you can plug into an ethernet port isn't going to understand a tag.. While you can tell it to in windows, linux, etc. You don't normally see a Printer that understands what a vlan tag is ;)
Again moving away fro the default vlan 1 on a switch is done to prevent the accidental placement of a device on the wrong vlan ;) And going to say this again - your going overboard for a home network being worried about what your switch a untagged network IDs that vlan as for its management.. Or what other vlan you might use on that switch that comes in untagged or goes to another switch even when there are tagged networks... You can have 1 untagged network on a wire, with other tagged vlans, etc.. Switch doesn't really care if switch 1 calls it vlan 1, and switch 2 calls it vlan 666, etc..
As I already stated most lower end smart switches are not going to allow you to change the management vlan to some other ID, other than 1.. While sure you can create other vlans that are untagged say 666 for other ports - you wouldn't be able to get to the management IP via that port.
-
Hey thanks for the quick reply.
You don't put devices on tagged vlans
I should have been more precise with my language when I said maybe I should move my devices in untagged VLAN 1 to tagged VLANs. I should have said move them to "untagged/tagged" VLANs. I do realize that most of 90% of my devices plugged into the switch are going to be untagged VLANS IDs.
While sure you can create other vlans that are untagged say 666 for other ports - you wouldn't be able to get to the management IP via that port.
At least with my switch, I have tested the case where the switch itself has an IP from untagged VLAN 1 , and I have port 8 is only configured for untagged VLAN 40. I actually can access the switch's IP (management interface) from my device in VLAN 40. My firewall just has to allow that across VLANs. Are you saying most switches wouldn't allow this? Maybe I misunderstood what you were trying to warn me about.
And going to say this again - your going overboard for a home network
Yes, I'm sure I'm going overboard for a home network, considering this is mostly for physical exploits via a poorly configured port. Although, I haven't really though about if someone were to remotely gain access to one of my servers sitting in untagged VLAN 1. I don't know enough about how tag injection attacks work to know if that could be a vector.
Besides the exploits, I thought there was still a case to move away from using untagged native VLAN 1. In the pfSense documentation they say it's best to isolate it for "internal traffic" reasons. Maybe I'm misunderstanding that too?
Switches will send internal protocols such as STP (Spanning Tree Protocol), VTP (VLAN Trunking Protocol), and CDP (Cisco Discover Protocol) untagged over the native VLAN, where the switches use these protocols. It is generally the best practice to keep that internal traffic isolated from data traffic.
lol, if I'm annoying you I do apologize. I don't mean to "beat a dead horse" as they say. I'm just a slow learner and I ask a lot of dumb questions sometimes

-
@uplink PVST+ and RPVST+ which are cisco and can be tagged..
A native vlan is any untagged vlan, not just vlan 1.
From one of the cert exam books for cisco
"Although maintenance protocols such as Cisco Discovery Protocol (CDP), Port Aggregation Protocol (PAgP), and Dynamic Trunking Protocol (DTP) normally are carried over the native VLAN of a trunk, they will not be affected if the native VLAN is removed or manually pruned from the trunk. They still will be sent and received on the native VLAN as a special case even if the native VLAN ID is not in the list of allowed VLANs."
Any untagged frame is native.. If you want to take something away from that it should be this.
" It is generally the best practice to keep that internal traffic isolated from data traffic."
So put your switches and AP management on a vlan not used for normal user traffic.. This is sometimes called an infrastructure vlan. But then again you have to work with the functionality of your infrastructure devices.. But even if your devices have to be managed with untagged - you don't have to use that vlan for user traffic.. So yes it best to isolate management of your network from user traffic ;)
But here is the thing - you can not really disable untagged traffic like that from being sent, you can keep it from being passed on, etc.. Here I have a dummy vlan 10, the vlan is disabled - it doesn't go anywhere.. I set the native vlan, because you can not really remove it from a port, cisco doesn't let you.. If you remove native vlan from a trunk in cisco it will just send it out what default vlan you have set on the switch.. which will be "untagged"
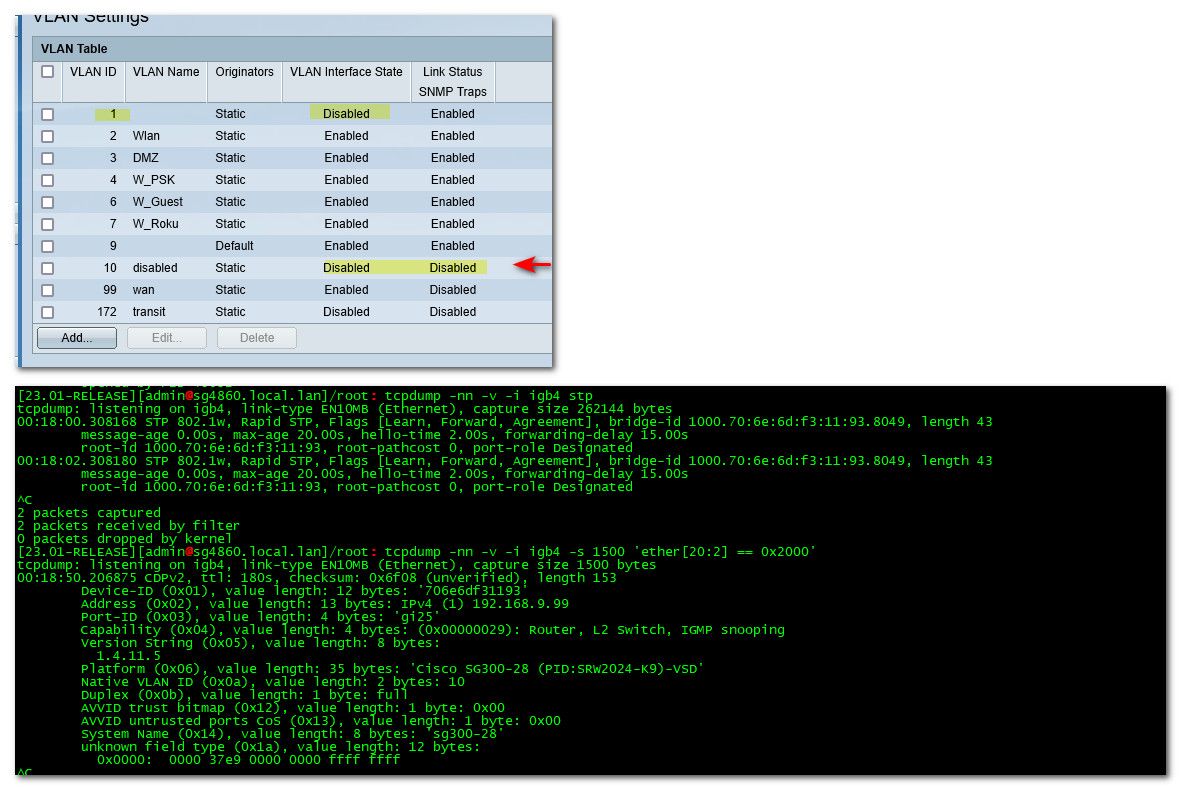
that is sniff on pfsense on a port connected to switch interface that is in trunk, where native is set to a disabled vlan, notice still see stp and cdp traffic on this port..
If your worried about someone plugging into a port, again the best thing to do is disable and put into a vlan not using, like my vlan 10, But if the port is active and you have cdp or stp enabled - there will be that traffic on that port untagged..
Your causing yourself added config and and work for no real good reason.. And again any port connected to a device is going to be native, ie untagged in some vlan be it the default vlan 1, or some other vlan you put that port in. Even if you told all your devices to do tags, iot devices, printers etc are unlikely to be able to do that, etc. And even if you setup a port to only be tagged, info like stp and cdp is still going to go out that port..
depending on your switch, you may be able to disable stp on specific ports, or stuff like cdp or lldp (non cisco kind of cdp).. But most lower end smart switches are not going to be able to do that, etc.
-
 J johnpoz referenced this topic on
J johnpoz referenced this topic on