Secure Remote Connection for InfluxDB
-
Hello,
I'm currently using a Netgate 4100 running pfsense+ version 23.01-RELEASE. Behind pfsense, I have a AWX server to deploy ansible configurations as well as a metrics server I use to run Grafana and InfluxDB. Internally, all that works great but now I need to deploy some telegraf configurations on external remote hosts and of course it's not going to work since there is no way for the external hosts to communicate with the internal host. The only rule I have on the WAN is for OpenVPN so I can connect to my home network remotely.
InfluxDB uses port 8086 to collect data from clients and store them for Grafana to read. Now, I do know that I do NOT want to use any port forwarding because that would open up the port to the wonderful world of the public, wide open internet which probably isn't going to end well. I've seen the mention of using a VPN to make this possible without any port forwarding, but I'm not 100% sure on which VPN method to use but this is what I assume they mean by that:
Remote Host ----> VPN Connection ----> Pfsense Router ----> Internal Host:8086
The remote host as well as the metrics host are both using Rocky Linux 9. Which VPN method would allow the remote host to communicate with the internal host securely without the use of any port forwarding? Thank you in advance for your assistance. If any additional information is needed, please let me know and I will provide it as soon as possible.
Thank You
-
@hovnetworks said in Secure Remote Connection for InfluxDB:
would open up the port to the wonderful world of the public
It doesn't have too - do these remote hosts IP change? If the IPs of these locations doesn't change that often you could just allow the specific IPs of the remote host to talk to your internal host on port 8086 via port forward.
Even if the remote hosts IPs change now and then, use of a dynamic dns could be used to limit who can talk to your port forward.
-
@johnpoz Hello John,
Thank you for your reply! The IP address for these hosts do not change unless I destroy the VM. They will also have public hostnames. So basically, I can make firewall rule to allow port 8086 from the remote host directly to the internal host. I believe I did try something like that but I'm sure it's more of me doing it wrong than anything else.
One thing I would like to confirm is where I need to make the rule on the WAN or VLAN the internal host is on? I believe I tried on the WAN but again it did not work so I probably did the rule wrong or didn't do it for the correct network. But this is the rule I tried to do:
Action: Pass
Interface: WAN
Address Family: IPv4
Protocol: TCP
Source: External Host IP
Port Range: From 8086 to 8086
Destination: Internal Host IP
Port Range: 8086 to 8086The internal host sits on VLAN 30 for example would I have to do the rule there instead?
Thank you!
-
@hovnetworks The Source port range should be any…source ports are random.
Edit: also if using private IPs on LAN this would need to be a NAT rule.
-
@hovnetworks yeah you would almost never set the source port.. There are a few instances where the source port might be known. But even if you knew that application used a specific source port, needing to set it on your firewall rule to limit would be normally not needed, especially if you were locking down to a source port.
Locking down to specific IP or IPs would be done on the port forward rule.. Then pfsense would auto create the wan rule needed to allow. For example I limit what can access my plex via this port forward.
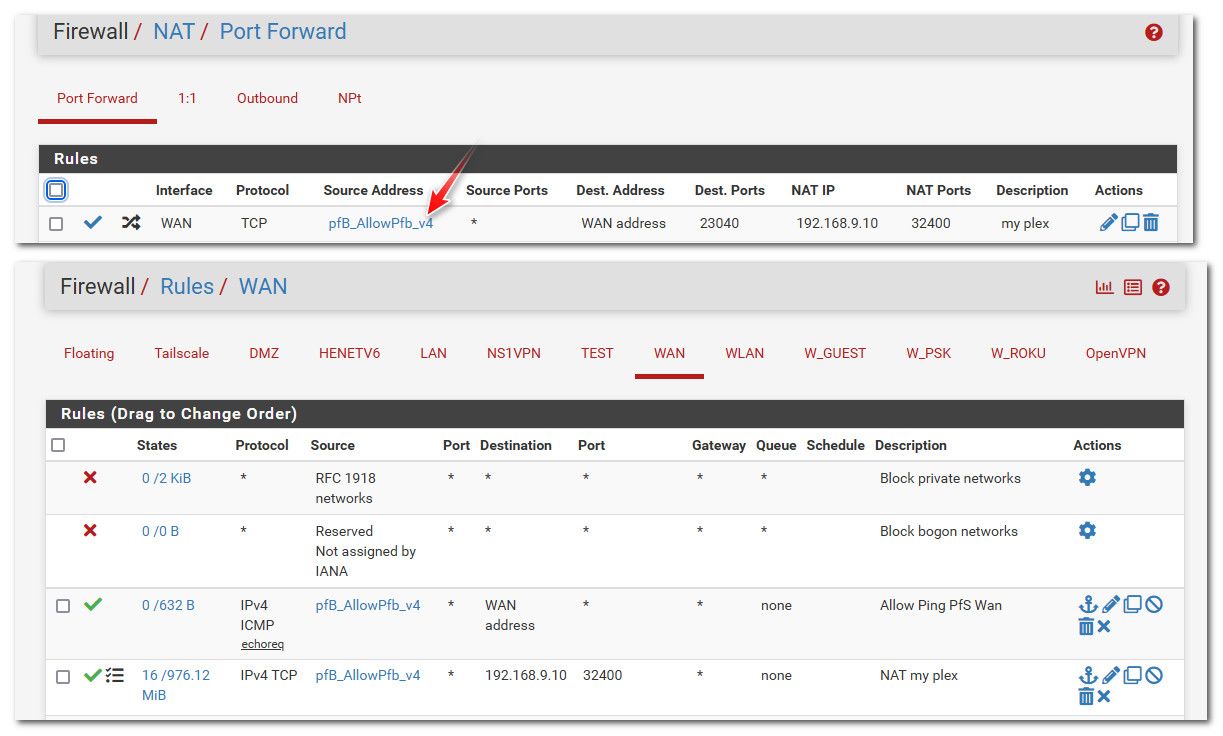
Notice in my port forward I limit source IPs to that alias pfb_allowPFB_v4 alias. This is an alias I run in pfblocker that includes only US IPs, and some other IPs that uptime robot and status cake, and plex checking (these change now and then) to check and know if my plex service is online.
If some other IP that is not included in the aliases attempted to hit that port, that traffic would just be dropped. So if you know these remote IPs, or the fqdn that would resolve to these IPs you want to limit access to. Just create an alias that contains them and then use that alias as the source IP in your port forward rule.
edit:
For completeness of example - here is the alias, yeah I also allow IPs from Morocco, I currently have a family member living there that accesses my plex.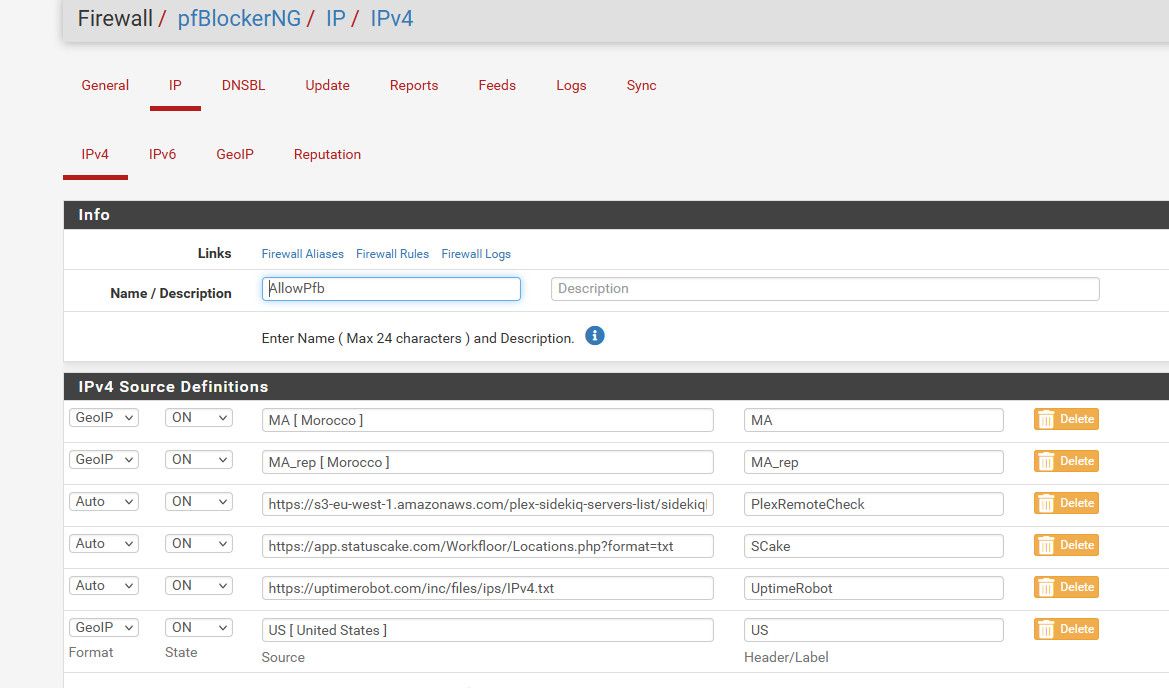
-
@johnpoz This was perfect and exactly what I needed! Thank you so much for taking the time out to explain this. I was a bit confused at first since most of the stuff I was reading was mentioning not to use port forwarding however, none of them mentioned locking anything down via an alias which makes total sense the way you explained it. I tested it out after applying everything and it's working as intended. I also tested it from other public networks and it fails.
Thank you!!
-
@hovnetworks happy to help.. Yeah you would think for example that plex and uptime and statuscake IPs would all be in the us so wouldn't need those - but some of the IPs are outside the US when checking.. So its best to be specific.
Generally speaking port forwards are less secure for sure than say a vpn. But if you can lock down who can access it, it can be very secure.. In a scenario where you know the IP or even a small netblock of where the remotes are going to be coming from.. Limiting your port forward to that IP or IPs is pretty secure..
When I first started sharing plex, I was going to limit it to my specific users IP.. But you ask a user for their IP and most of the time its a deer in headlight look you get back. And then their IP changes, or they are trying to watch via their phone while they are out and about.. So did the next best thing and just locked it down to country where they would be coming from, etc.
I had a buddy travel to Ireland a few weeks back - so I opened up for him, and he did watch some stuff while he was there ;) And then when he got back I removed those IPs from the alias.