OpenVPN Client for VLAN specific routes to Internet
-
@scottlindner said in OpenVPN Client for VLAN specific routes to Internet:
So back to the question, I don't have a clue what the proper descriptive terms are for what I'm attempting to do.
First you have to assign an interface to the OpenVPN client (Interfaces > Assignments).
Next to "Available network ports:" select the proper client instance, e.g. ovpn1, and hit Add. Open the new interface settings, enable it and state a friendly name.
This automatically also add a gateway.Go to Firewall > NAT > Outbound. If it is in automatic mode check if there are rules already present for your subnets on the new VPN interface. If there aren't any, you have to switch into hybrid mode and add a rule for the respective VLAN manually.
Then you can policy route the traffic on the concerned interface by adding a firewall pass rule or by editing the existing one. Open the advanced settings, go down to gateway and state the VPN gateway.
Consider that this rule directs all matching traffic to the VPN gateway and doesn't allow any interface destination. If you also need access to internal resources you need to add additional rule for this without the gateway option.
In this case limit the policy route to internet destinations. Best to do this is to create an alias and add all RFC1918 network to it. Then state this alias in the policy routing rule as destination in conjunction with "invert match" checked. -
This post is deleted! -
@viragomann
You mention VPN Gateway. How do I configure the VPN Client as a VPN Gateway to achieve this? I have the client configured and connecting. I have the WiFi SSID to VLAN ID and Interface in pfSense setup. So I'm thinking I'm close and need this VPN Gateway and then build the route from there. I don't need to access internal resources from external. I just want to use the VPN Client in pfSense as a new gateway to the internet instead of the WAN (although I do know the VPN is going over the WAN). -
@scottlindner
Yes, the gateway is required for policy routing.
How you can get it, I've described in the first section of my post above. -
@viragomann said in OpenVPN Client for VLAN specific routes to Internet:
@scottlindner
Yes, the gateway is required for policy routing.
How you can get it, I've described in the first section of my post above.My reading skills suck when I'm under caffeinated. Sorry man. I'll give this a go again tonight. Looks like I might be close. Thank you.
-
@viragomann said in OpenVPN Client for VLAN specific routes to Internet:
Go to Firewall > NAT > Outbound. If it is in automatic mode check if there are rules already present for your subnets on the new VPN interface. If there aren't any, you have to switch into hybrid mode and add a rule for the respective VLAN manually.
I am already in hybrid mode for other reasons. I am not entirely positive what to do here. I tried what made sense to me based on what you're saying, but I see an Automatic Rule that might take precendence over the rule I created under "Mappings".
The subnet for the VLAN I want to route to the VPN Client is 192.168.201.0/24
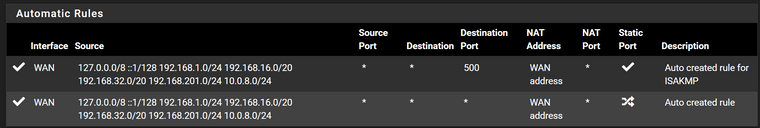
I'm asuming that's going to prevent me from success, right? Is there a way to stop this?
In the link you cited it mentions going to Firewall -> Rukes -> LAN and changing the Gateway from "Default" to the gateway I want. Thinking this being the default rule, I changed it to my WAN gateway to exclude my VPN Client gateway. That didn't have any affect on the automatic NAT rules or behavior.
I do have the WiFi SSID, VLAN and DHCP server all setup. WiFi devices are connecting and being issued an IP address from the correct subnet and DHCP server. The VPN Client is connected to the service and I can see those details in the log when I turn verbosity up. So I know my issue is just in the routing rules now. I get it... and at the same time don't get it.
-
@scottlindner said in OpenVPN Client for VLAN specific routes to Internet:
but I see an Automatic Rule that might take precendence over the rule I created under "Mappings".
No. I told you wo add a rule on the new VPN interface, which you've just created. The automatic generated rules seem to on WAN only.
In the link you cited it mentions going to Firewall -> Rukes -> LAN and changing the Gateway from "Default" to the gateway I want. Thinking this being the default rule, I changed it to my WAN gateway to exclude my VPN Client gateway. That didn't have any affect on the automatic NAT rules or behavior.
This does only direct matching traffic to the stated gateway. It doesn't do any changes in the outbound NAT rules.
Note that the NAT rules are only for NAT. They cannot redirect traffic. -
@viragomann said in OpenVPN Client for VLAN specific routes to Internet:
No. I told you wo add a rule on the new VPN interface, which you've just created. The automatic generated rules seem to on WAN only.
There aren't any options to not add a rule when I create the interface for the VPN client.
I have re-read your original comment and those following it multiple times looking for the key detail I'm missing and I'm not seeing it. I'm trying. I really am. I appreciate the help because everything I read online that I find seems to have some assumption such as I want ALL traffic to go through the VPN client, or I don't have anything else going on in my routing rules so it's Automatic NAT rule generation rather than hybrid.
I don't even know where I'm hosed. Is it the VPN CLient that is jacked? The VPN Client Interface, the VLAN configuration for DHCP, that fact I'm jacking with NAT rules and not some other type of rule? That I need a Firewall Rule that isn't NAT? That I have an over aggressive rule somewhere sucking up everything before it gets a chance to another rule I have already been trying.
-
@scottlindner said in OpenVPN Client for VLAN specific routes to Internet:
There aren't any options to not add a rule when I create the interface for the VPN client.
So add the rule after creating the interface.
I have re-read your original comment and those following it multiple times looking for the key detail I'm missing and I'm not seeing it.
Yes, I tried to describe all necessary steps with common words, since I don't know you detailed configuration. But maybe you can tell, what you have so far, so that I can try to be more responsive to your set up.
Have you already assigned an interface to the VPN client?
What's its name?
Is it shown up in Status > Interfaces?Which subnet to you want to direct over the VPN?
What are the firewall rules for this subnet?
Do you need to access also internal resources from it? Which?What are your outbound NAT rules?
-
@viragomann said in OpenVPN Client for VLAN specific routes to Internet:
Yes, I tried to describe all necessary steps with common words, since I don't know you detailed configuration. But maybe you can tell, what you have so far, so that I can try to be more responsive to your set up.
I appreciate that. Give me the jist and let me figure out the rest. Other than apparently I don't understand enough.
Have you already assigned an interface to the VPN client?
VPN Client connected:
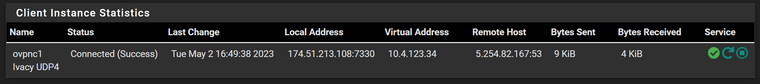
Here are the interfaces:
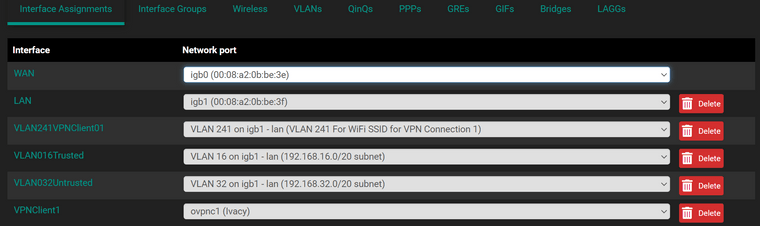
What's its name?
VPNClient1
Is it shown up in Status > Interfaces?

Which subnet to you want to direct over the VPN?
192.168.241.0/24
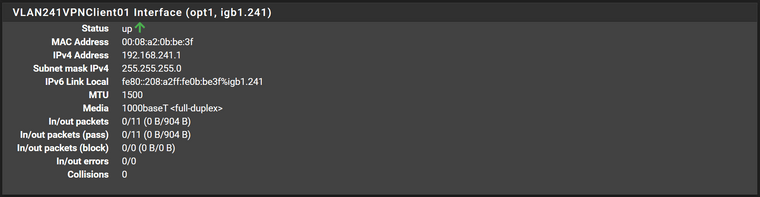
What are the firewall rules for this subnet?
I keep messing all over with that. right now I have nothing because everything I try doesn't work.
Do you need to access also internal resources from it? Which?
I don't need to do any port forwarding. This is an outgoing gateway only, but I do need NATing for the entire subnet.
What are your outbound NAT rules?
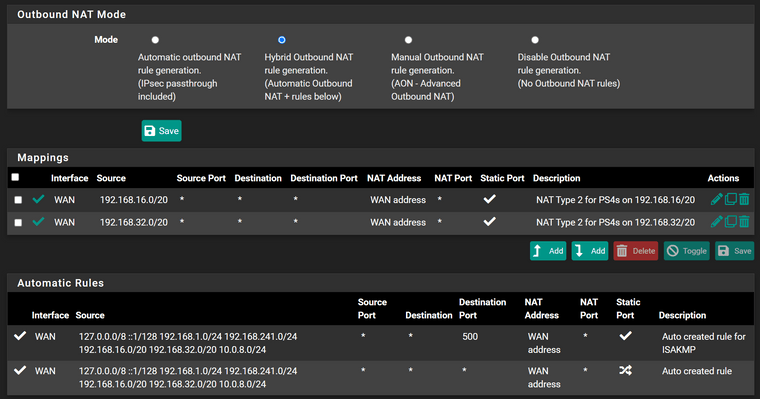
-
@scottlindner said in OpenVPN Client for VLAN specific routes to Internet:
VPNClient1
So you have an interface assigned to the OpenVPN client and named it "VPNClient1".
As you can see on the interface status page, there is also a gateway assigned to this interface. You can look at Status > gateways for its name, probably VPNClient1_VPN4.
This is the gateway that you have to state in the policy routing firewall rule.So let us configure the policy routing.
In Firewall > Rules > VLAN241VPNClient01 you might have already a pass rule allowing anything at this time.
You can edit this rule or add a new one if you don't have any yet, open the advanced options, go down to "gateway" and select the VPN gateway (e.g. VPNClient1_VPN4) and save it.Outbound NAT:
Add a new rule:
Interface: VPNClient1
protocol: any
source: VLAN241VPNClient01 net
destination: any
translation: interface addressThat's basically all you need. However, this setup doesn't allow any internal access, because all matching traffic of the policy routing rule is directed to the VPN gateway.
But normally your internal devices (and as well that in VLAN241VPNClient01 subnet) are configured to use the pfSense interface address for DNS resolution. However, this would end up in DNS leaks anyway. So best practice is to forward DNS requests on the respective interface to a public DNS server (this goes across the VPN due to the policy routing rule.
Maybe your DNS provider provides a DNS server, but you can also use Googles DNS, e.g. 8.8.8.8.So let us forward DNS requests to Google:
Firewall > NAT > Port forward
Add a new rule:
Interface: VLAN241VPNClient01
protocol: TCP/UDP
Destination: This Firewall
Dest. port: 53
Redirect target: Single host > 8.8.8.8
redirect port: 53 -
@viragomann said in OpenVPN Client for VLAN specific routes to Internet:
So you have an interface assigned to the OpenVPN client and named it "VPNClient1".
As you can see on the interface status page, there is also a gateway assigned to this interface. You can look at Status > gateways for its name, probably VPNClient1_VPN4.I hadn't looked at the gateway status before. Thank you for that tip. Is this an issue or just indicative that I don't have the firewal rules setup correctly yet?
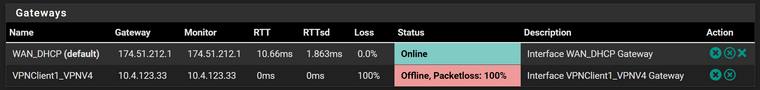
and the client status says things are good
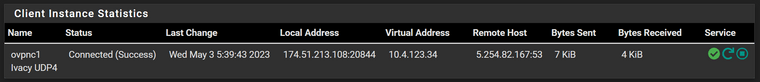
I'm going to continue on assuming this just means I need to set up your next steps.
This is the gateway that you have to state in the policy routing firewall rule.
So let us configure the policy routing.
In Firewall > Rules > VLAN241VPNClient01 you might have already a pass rule allowing anything at this time.
You can edit this rule or add a new one if you don't have any yet, open the advanced options, go down to "gateway" and select the VPN gateway (e.g. VPNClient1_VPN4) and save it.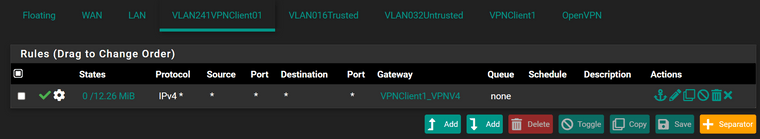
Outbound NAT:
Add a new rule:
Interface: VPNClient1
protocol: any
source: VLAN241VPNClient01 net
destination: any
translation: interface address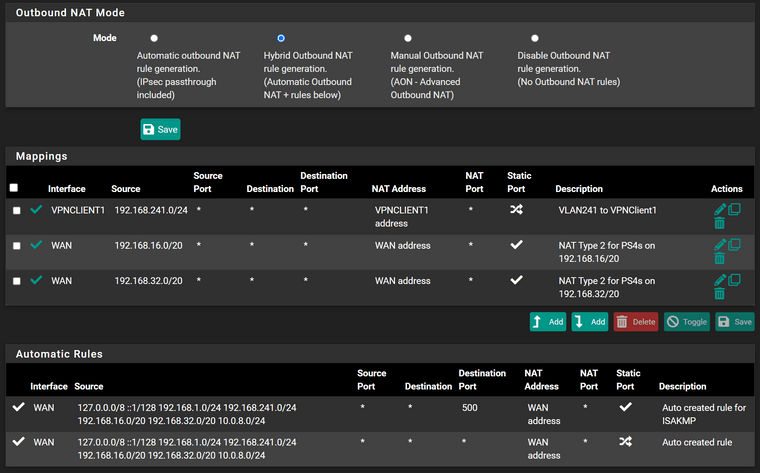
With both of those rules added, my phone connected to this WiFi SSID going through the VLAN241 will get internet access but the whatsmyip.com site says it is my local Colorado Springs IP address rather than Frankfurt Germany which this VPN Client is configured to use.
That's basically all you need. However, this setup doesn't allow any internal access, because all matching traffic of the policy routing rule is directed to the VPN gateway.
But normally your internal devices (and as well that in VLAN241VPNClient01 subnet) are configured to use the pfSense interface address for DNS resolution. However, this would end up in DNS leaks anyway. So best practice is to forward DNS requests on the respective interface to a public DNS server (this goes across the VPN due to the policy routing rule.
Maybe your DNS provider provides a DNS server, but you can also use Googles DNS, e.g. 8.8.8.8.So let us forward DNS requests to Google:
Firewall > NAT > Port forward
Add a new rule:
Interface: VLAN241VPNClient01
protocol: TCP/UDP
Destination: This Firewall
Dest. port: 53
Redirect target: Single host > 8.8.8.8
redirect port: 53 -
@scottlindner said in OpenVPN Client for VLAN specific routes to Internet:
I hadn't looked at the gateway status before. Thank you for that tip. Is this an issue or just indicative that I don't have the firewal rules setup correctly yet?
Presumably the server (monitoring IP) doesn't respond to ping.
Yes, it should be online, otherwise the rule is omitted with default settings.Best to monitor any public IP, which is responding to ping requests. 8.8.8.8 is often used for this.
You can change it in the gateway settings. System > Routing > Gateways -
@viragomann said in OpenVPN Client for VLAN specific routes to Internet:
@scottlindner said in OpenVPN Client for VLAN specific routes to Internet:
I hadn't looked at the gateway status before. Thank you for that tip. Is this an issue or just indicative that I don't have the firewal rules setup correctly yet?
Presumably the server (monitoring IP) doesn't respond to ping.
Yes, it should be online, otherwise the rule is omitted with default settings.Best to monitor any public IP, which is responding to ping requests. 8.8.8.8 is often used for this.
You can change it in the gateway settings. System > Routing > GatewaysI wasn't aware of that setting but it makes a lot of sense to switch it like that. It didn't have any effect.
May 3 06:39:41 dpinger 79457 send_interval 500ms loss_interval 2000ms time_period 60000ms report_interval 0ms data_len 1 alert_interval 1000ms latency_alarm 500ms loss_alarm 20% dest_addr 174.51.212.1 bind_addr 174.51.213.108 identifier "WAN_DHCP " May 3 06:39:41 dpinger 79840 send_interval 500ms loss_interval 2000ms time_period 60000ms report_interval 0ms data_len 1 alert_interval 1000ms latency_alarm 500ms loss_alarm 20% dest_addr 8.8.8.8 bind_addr 10.4.123.37 identifier "VPNClient1_VPNV4 " May 3 06:39:43 dpinger 79840 VPNClient1_VPNV4 8.8.8.8: Alarm latency 0us stddev 0us loss 100% May 3 06:41:01 dpinger 79840 exiting on signal 15 May 3 06:41:01 dpinger 79457 exiting on signal 15 May 3 06:41:01 dpinger 68264 send_interval 500ms loss_interval 2000ms time_period 60000ms report_interval 0ms data_len 1 alert_interval 1000ms latency_alarm 500ms loss_alarm 20% dest_addr 174.51.212.1 bind_addr 174.51.213.108 identifier "WAN_DHCP " May 3 06:41:01 dpinger 68767 send_interval 500ms loss_interval 2000ms time_period 60000ms report_interval 0ms data_len 1 alert_interval 1000ms latency_alarm 500ms loss_alarm 20% dest_addr 8.8.8.8 bind_addr 10.4.123.34 identifier "VPNClient1_VPNV4 " May 3 06:41:03 dpinger 68767 VPNClient1_VPNV4 8.8.8.8: Alarm latency 0us stddev 0us loss 100%I'm going to poke around at potential ping issues connecting to this VPN service using my laptop and see if I can understand why this isn't working. My gut is I might have something off in the pfSense OVPN Client settings that is causing this, but I'll find out soon.
-
@scottlindner
Possibly you're missing an outbound NAT rule for this.
Copy that one you've add recently (copy symbol on the right) and change the source to 127.0.0.0/8. -
@viragomann said in OpenVPN Client for VLAN specific routes to Internet:
127.0.0.0/8
No change in VPN Gateway status.
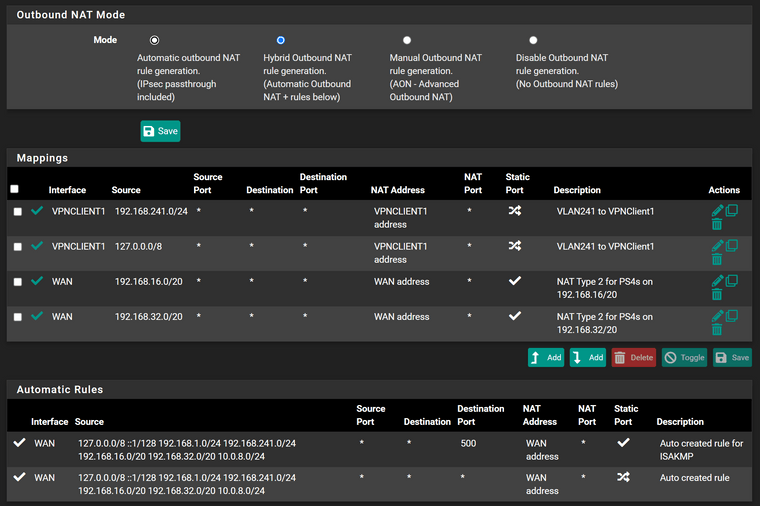
-
@scottlindner
Hmmm. Maybe there is something wrong with your VPN connection or traffic is blocked elsewhere.Do you have any floating rules?
Reconnect the VPN client and post the OpenVPN log section from there, please.
-
@viragomann said in OpenVPN Client for VLAN specific routes to Internet:
@scottlindner
Hmmm. Maybe there is something wrong with your VPN connection or traffic is blocked elsewhere.Do you have any floating rules?
I do but I don't see how they could cause this.
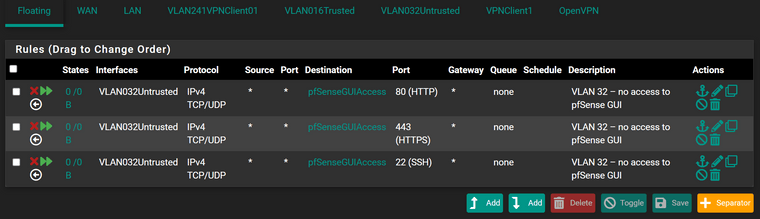
Reconnect the VPN client and post the OpenVPN log section from there, please.
Check this out. With those rules I setup this morning I tried connecting remotely from work over lunch to get you the screenshots you wanted and although I connected, I couldn't access anything like I usually can. And just now I tried restarting the client and it wouldn't connect. So I tried connecting from my laptop and it wouldn't connect. I disabled the rules we wrote just a bit ago and now everything connects fine.
-
What are my diagnostic options to figure out why traffic on the VPN VLAN isn't making it to the VPN Client gateway?
-
@scottlindner
As I mentioned above, I'd suspect that there is something wrong with the VPN. So check the log for hints. Possibly set the log level to 3 or 4 before connecting.Did you also try a reboot of pfSense? Outbound NAT changes sometimes work need that.
Try different monitoring IPs. Use public IPs that you know they're responding when pinging from WAN.
When you sniff the traffic (packet capture) on the VPN interface, you should see the ICMP packets to the monitoring IP going out there:
<VPN IP> > <monitoring IP> ICMP request.
Ideally you also see respond packets, but obviously there are none.If that's the case, I would assume that there is an issue on the VPN providers side. Which one do you connect to?
Maybe he does not pass any traffic or do not nat it on his internet outbound interface.
You can also try to tear down the client and configure a new one.