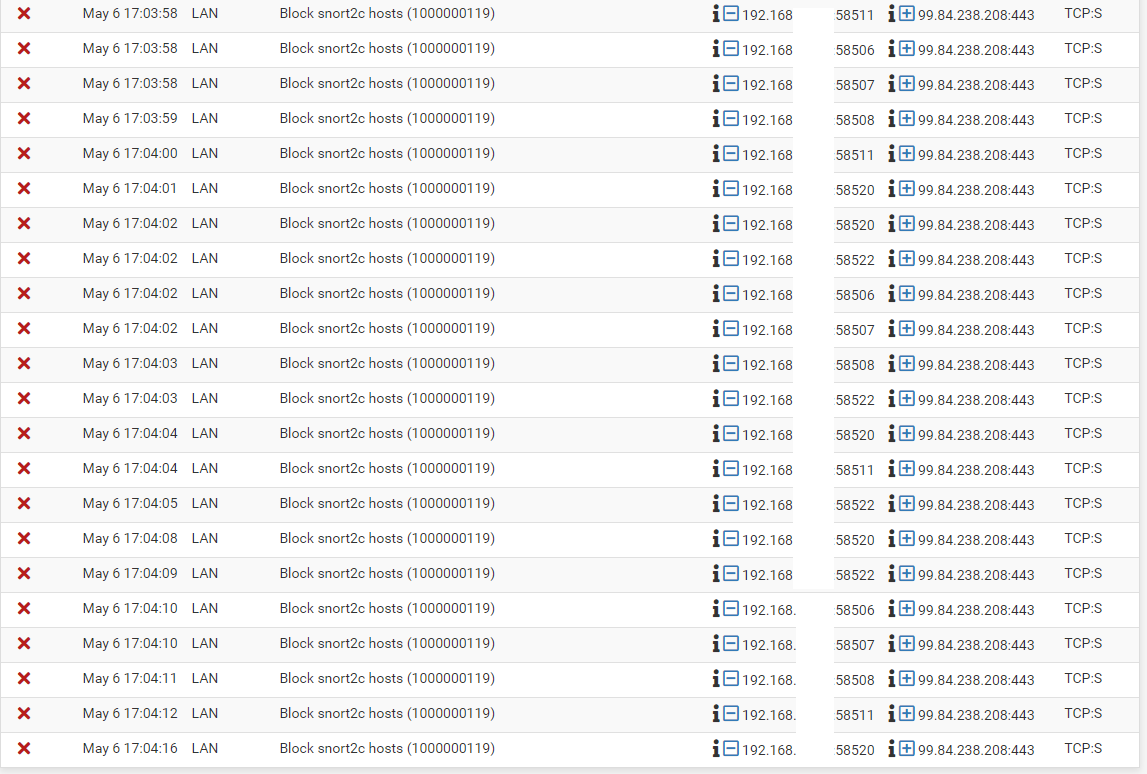
Source of IP addresses blocked by Snort
-
When I use Suricata, Suricata sometimes block IP addresses that don't even show up in whois with the company name, but how do you guys find out which site/company the blocked address is from?
I've been looking through my Brave and chrome history and can't seem to find any history that matches the time Suricata blocked it.
-
simple whois shows its amazon
NetRange: 99.84.0.0 - 99.84.255.255 CIDR: 99.84.0.0/16 NetName: AMAZO-CF Parent: AMAZO-4 (NET-99-83-64-0-1) Organization: Amazon.com, Inc. (AMAZON-4);; QUESTION SECTION: ;208.238.84.99.in-addr.arpa. IN PTR ;; ANSWER SECTION: 208.238.84.99.in-addr.arpa. 0 IN PTR server-99-84-238-208.sfo5.r.cloudfront.net. -
@johnpoz
Thank you, it would be easy to understand if the Whois says Amazon. But what about Cloudflare? This log also does not match the time in the browser history.
I would like to know how everyone identifies the source site of IP addresses that should be allowed access.
-
@yet_learningpfsense huh?
NetRange: 104.16.0.0 - 104.31.255.255 CIDR: 104.16.0.0/12 NetName: CLOUDFLARENET NetHandle: NET-104-16-0-0-1 Parent: NET104 (NET-104-0-0-0-0) NetType: Direct Allocation OriginAS: AS13335 Organization: Cloudflare, Inc. (CLOUD14) -
@johnpoz Thank you very much. I thought that it was possible to deduce the address of a website from just one IP address, but perhaps it is better to assume that only a rough range can be determined. Alternatively, it may be possible to investigate further, but I will try to do it on my own. Once again, thank you very much.
-
@yet_learningpfsense while you can always lookup who owns a specific IP.. Via a whois, no its not possible say find out that say 104.18.x.x is www.somesite.com
Only if the owner of the IP range provides PTR for the IP can you deduce what it might be, but then again PTR does not always equate to what the forward is.
These services that run large CDNs, like clouldflare - IP address 1.2.3.4 might be used for www.domain.tld today, but tomorrow it might host www.otherdomain.tld
There are sites on the internet that might provide what a forward is for an IP.. example for your last IP
https://www.robtex.com/ip-lookup/104.18.12.173
Using as IP number
www.contourplusone.sk.cdn.cloudflare.net www.abbotts.co.uk.cdn.cloudflare.netAnother option could be to log your dns queries, and look to see what got asked for when that IP is returned.
or you could just grep in unbounds cache and see what it shows specific IP.
[23.01-RELEASE][admin@sg4860.local.lan]/root: unbound-control -c /var/unbound/unbound.conf dump_cache | grep 142.250.191.132 www.google.com. 1625 IN A 142.250.191.132 [23.01-RELEASE][admin@sg4860.local.lan]/root:[23.01-RELEASE][admin@sg4860.local.lan]/root: unbound-control -c /var/unbound/unbound.conf dump_cache | grep 208.123.73.199 forum.netgate.com. 328 IN A 208.123.73.199 [23.01-RELEASE][admin@sg4860.local.lan]/root:On windows you could look in the clients specific cache
PS C:> Get-DnsClientCache | ? { $_.Data -eq "208.123.73.199" } Entry RecordName Record Status Section TimeTo Data Data Type Live Length ----- ---------- ------ ------ ------- ------ ------ ---- forum.netgate.com forum.netgate.com A Success Answer 60 4 208.123.73.199 PS C:\>With powershell, or you could just dump the whole cache via the ipconfig /displaydns >file.txt and then search in that file.txt for the IP to see what they looked that returned that IP.
If your using firefox, you could look in the browser cache.. go to
about:networking#dns
Then find on that page the IP your interested in.
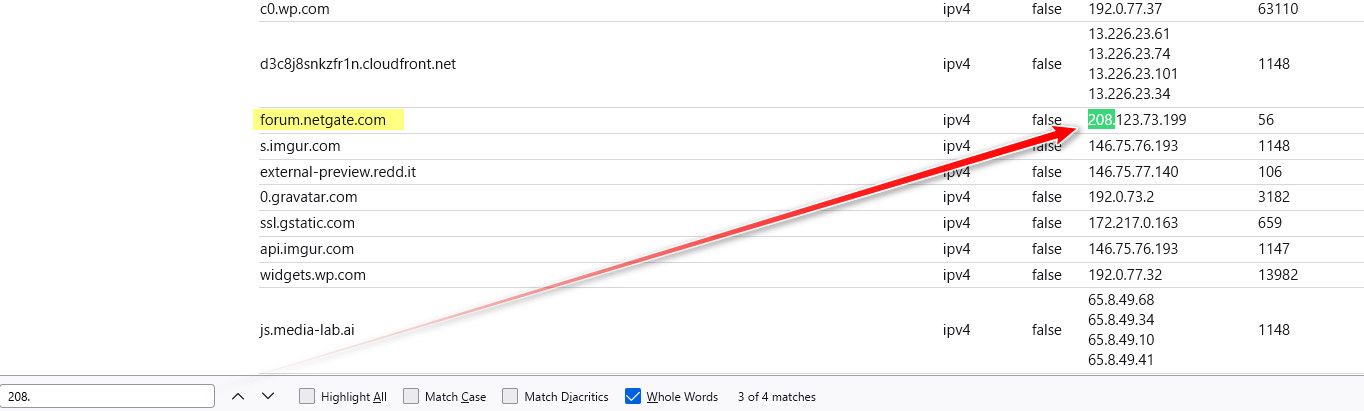
But the browser cache isn't all that large, so unless it was very recent you might not see it there. Also any of the cache looks will only be there for the life of the TTL of that lookup, etc. if you wanted history you would need to log all your dns queries, etc.
I believe firefox cache is only like 60 seconds, you could prob increase that - look in about:config for dnsCacheExpiration and modify what it set too
But maybe it wasn't firefox going there - could of been some other application/service on the box doing the dns query. so its prob best to look in unbounds cache.
-
@johnpoz Thank you very much for answering me politely and appropriately. The websites, commands, and browser cache that you provided as references were very helpful. I am not familiar with these types of tools and methods, so it really helped me.
Personally, I would like to be able to allow the sites that I access through my browser, so I will try to find Firefox or other browser extensions that can keep the cache unlimited.
-
@yet_learningpfsense said in Source of IP addresses blocked by Snort:
I would like to be able to allow the sites that I access through my browser,
You might find that is a lot of work, and going to be very problematic in nature trying to keep up with everywhere your browser might go and whitelisting it.
CDNs have made this even more difficult.. Say you whitelist 1.2.3.4 that is hosted on cloudflare, today it might be www.goodsite.com, but tomorrow it might be www.badsite.com
Or if you allow 1.2.3.0/24 while your site might be on .x and good, there might be a bad site on 1.2.3.y etc..
less work method is using say a list of bad sites/IPs etc. and filter on those either via firewall rules directly, or letting pfblocker do the filtering of the lists that are "bad" etc.
Whitelisting, or only allowing xyz would be a never ending wack-a-mole game of shoot, xyz isn't working - allow that, oh now abc not working, allow that.. Then you could to find out later that xyz (ip) is now bad, etc.
So its easier to find a list of bad stuff, and filter on it - and have that list updated every so often, etc. Verse trying to only allow specific stuff.. Also its not just say forum.netgate.com that you have to allow, most all sites these days have loads and loads of other fqdn used, that resolve to other IPs even. Sure some might be ads that you don't want - but many might be loading up some css that makes the page look good, or some script that the site needs to function correctly, etc. etc.
-
@johnpoz Thank you very much. I didn't realize that even if I use Cloudflare, there may be cases where a supposedly safe website could become a dangerous one that is allowed tomorrow. So, I think I will allow access by IP address only for cases like Amazon.com where it is clearly identifiable, as the IP address is unlikely to change.
Additionally, I plan to install pfBlocker and load its list to block dangerous websites. This has been very informative. I had something I wanted to ask but couldn't, but now the issue has been resolved. Thank you very much

-
@yet_learningpfsense said in Source of IP addresses blocked by Snort:
may be cases where a supposedly safe website could become a dangerous one
That is anysite on the planet to be honest - sites get compromised all the time, and then become hosts to malware, etc.