Firewall randomly blocking traffic
-
@kracken64 Are you actually not able to connect to that web site, or could it be this?
-
@steveits Hi Steve. I cannot access the website, on any device (computer, phone, etc.) that connects to this interface. The issue seems to only affect the VPN gateway because if I enable the Bypass rule during the few minutes where things are getting blocked, they will then be allowed and I can access the site.
-
@kracken64 My take would be your rule that allows traffic out your gateway, if the gateway fails - the rule just goes away, and now your traffic would fall through to your block rule.
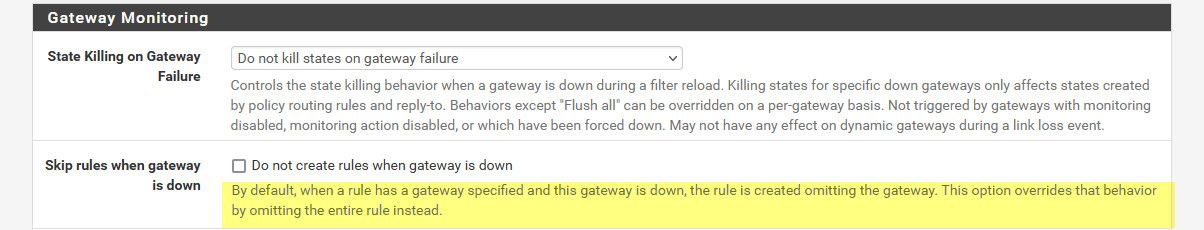
Do you have that checked? if not then traffic should just flow out your default interface.
Normally people want the traffic to fail when the vpn gateway is down, as a kill switch.
edit: this setting is under System Advanced Miscellaneous
-
@johnpoz It appears that I do have that item checked
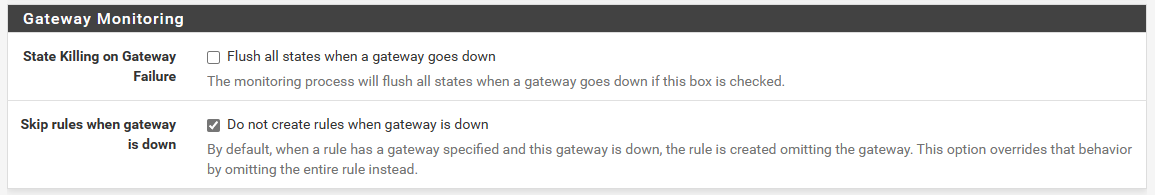
You are correct that I do not want traffic to get out if the VPN is down.
So does this mean that it's functioning as intended and the problem lies directly with the gateway? In this case I would presume I may need to contact the VPN Provider to get it resolved?
-
@kracken64 yeah if pfsense thinks that gateway is down, and you have that checked - the rule would be skipped completely, and then traffic would fall through to your deny rule, or the default deny.
The only thing that is a bit odd to me, is your block(reject) rules there at the end - which show in your log via the description don't seem set to log, so why are you seeing it logged? Did you change the rule to not log?
You will need to look into why pfsense thinks your vpn gateway is down to why the traffic is falling through to your block rule.
-
@johnpoz Yes I turned on logging after I took the rules picture. Sorry about that

Thanks for the help. Not sure why pfSense keeps losing the vpn gateway and then finding it again. It's a wireguard setup and the handshake between tunnel and peer seems to be ok. I've tried restarting the service and the pfSense box completely, but that had no impact. I've tried another wireguard config to a different server as well, but I get the same result.
-
@kracken64 is monitoring failing? Pfsense should log if it sees a gateway go away, or thinks it goes away.
-
@johnpoz Yes it does fail quite frequently, which I noticed on the dashboard. Logs seem to show the same, but no indication as to the reason behind it.
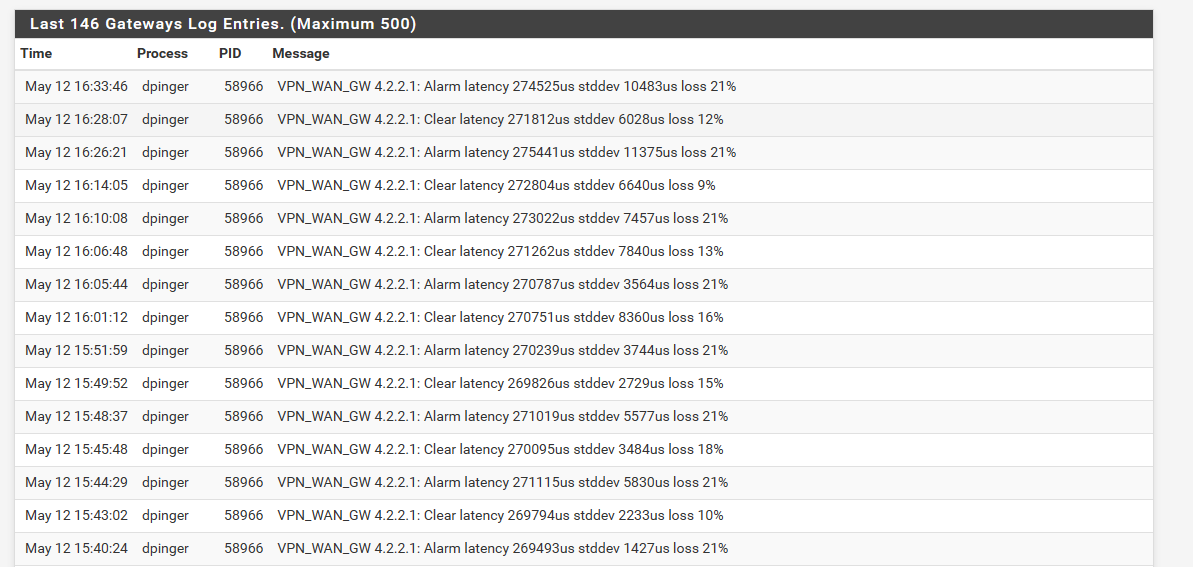
-
@kracken64 well you sure shouldn't be seeing that sort of packet loss.. What are you pinging for the monitor?
-
@kracken64 Along those lines you can change the gateway monitoring IP, or disable the gateway monitoring and/or its action so it will never drop offline.
-
I was using 4.2.2.1 for monitoring, and never had an issue before. I would like to keep monitoring the gateway so I changed it to an OpenDNS server instead.
I've kept an eye on it over the past day and everything seems to be working ok now. No logs for the gateway and no undesired blocks from the firewall.
Thank you both for the help!
-
@kracken64 Sometimes sites/routers will drop/ignore pings if they get busy. Sometimes a hop or two out will work better, sometimes worse.