Multi WAN, Multi Tunnels (& Peers) Wireguard VPN - Load Balancing & Failover
-
I just want to share what I have done with Wireguard VPN on Pfsense. I’m using 2.5.2-RELEASE (amd64), IP4 only, and NORDVPN. I have 3 internet lines, 2 lines for load balancing, 1 line for failover. Previously I used Openvpn for each internet line (1 VPN Tunnel per each WAN), but with Wireguard I can use 2 VPN Tunnels per each WAN (for Load Balancing) without significant speed drop.
*This is My Pfsense Dashboard
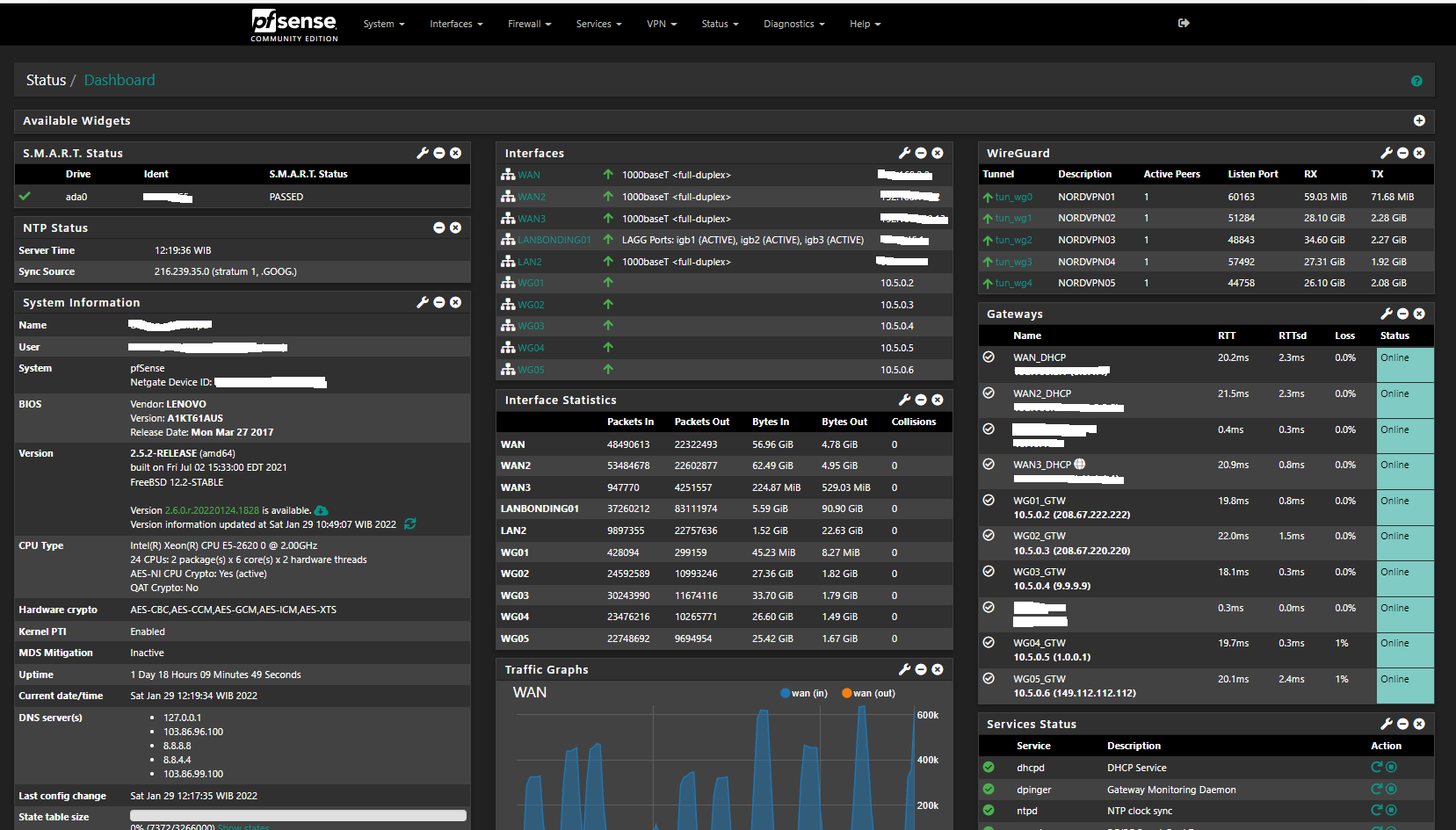
*5 Wireguard Tunnels
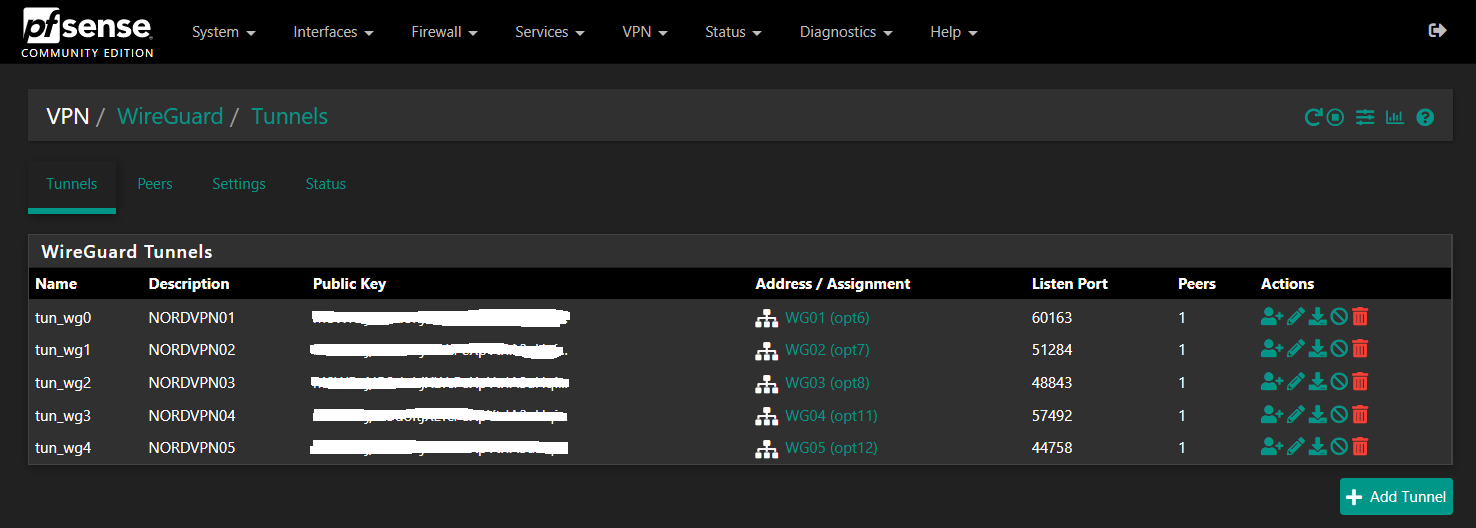
*1 Peer per Tunnel
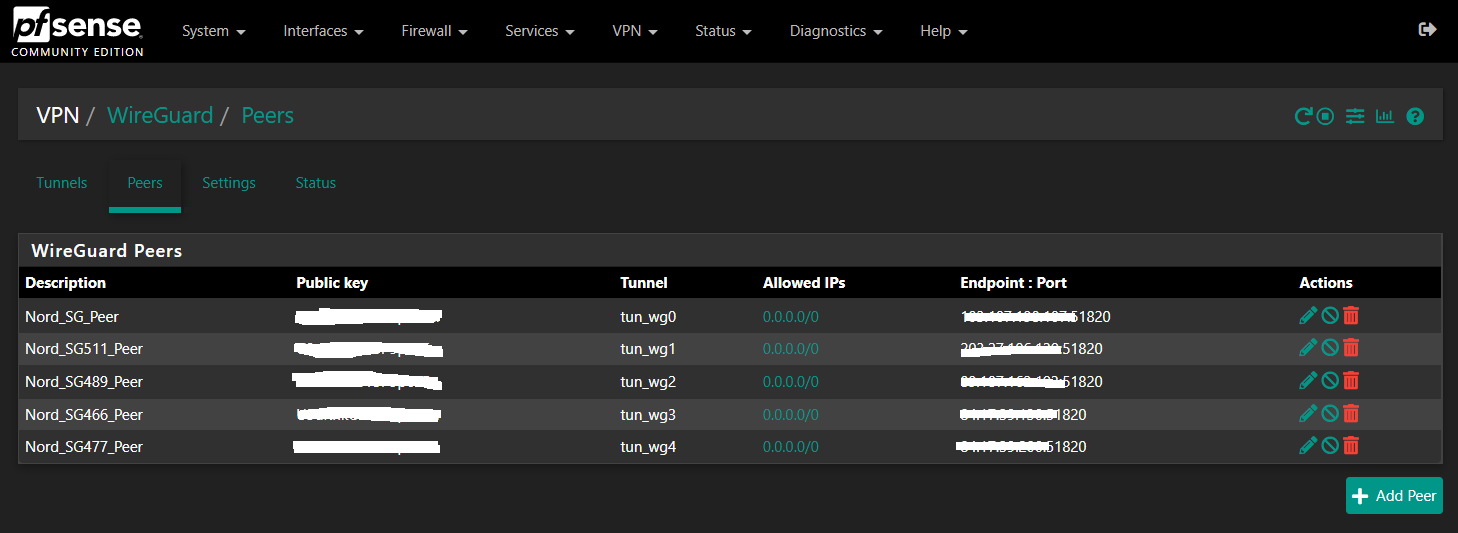
*Wireguard VPN Connection Status
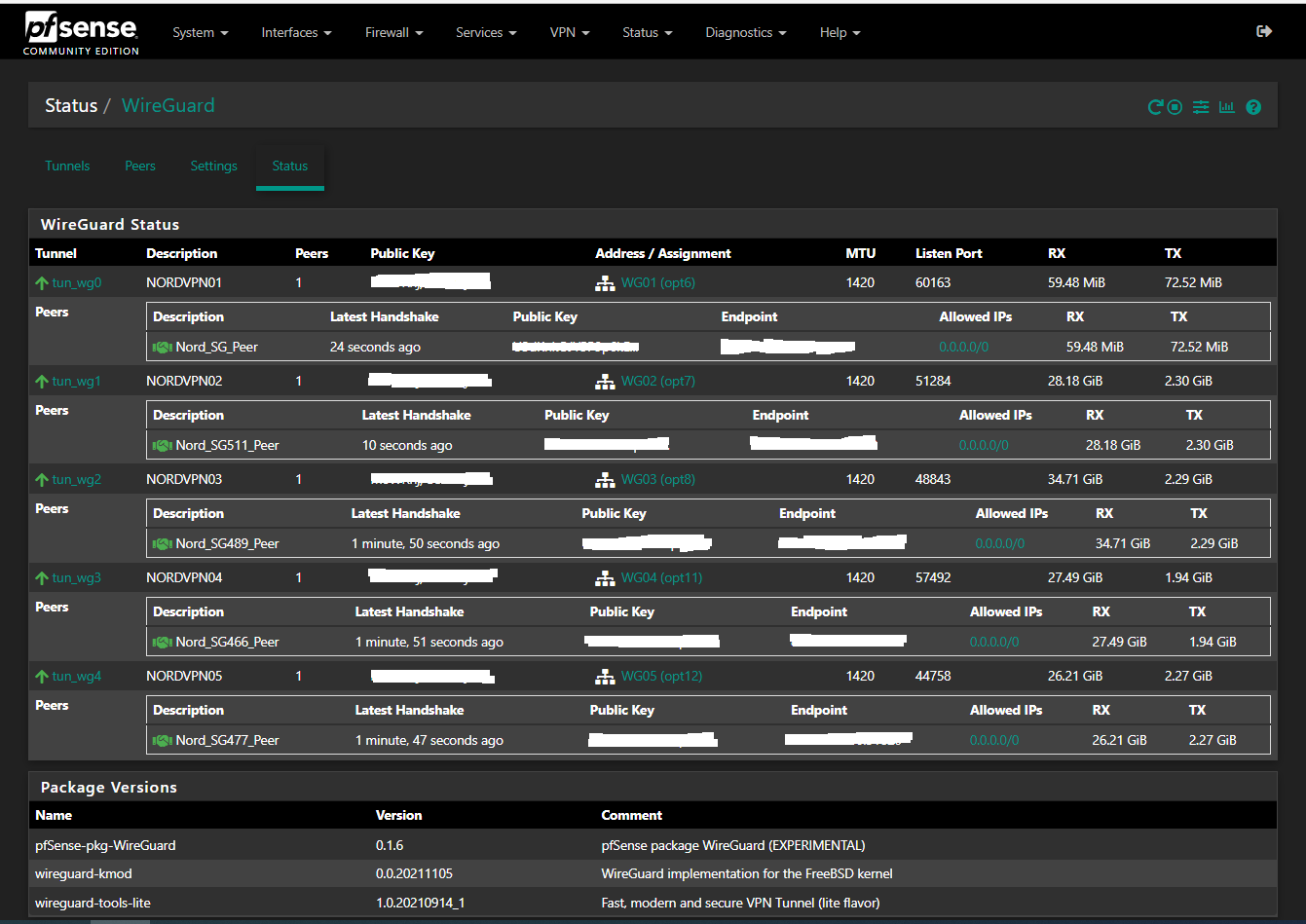
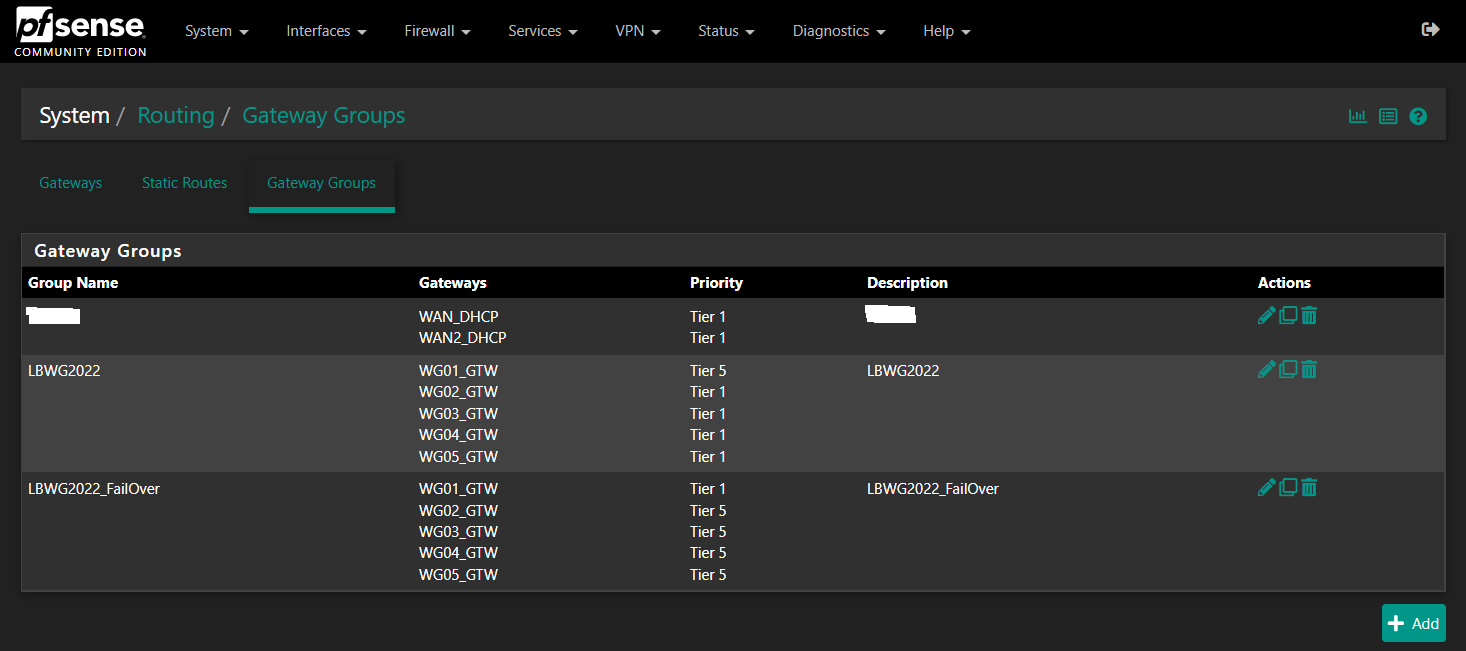
*Gateway Groups for Load Balancing & Failover
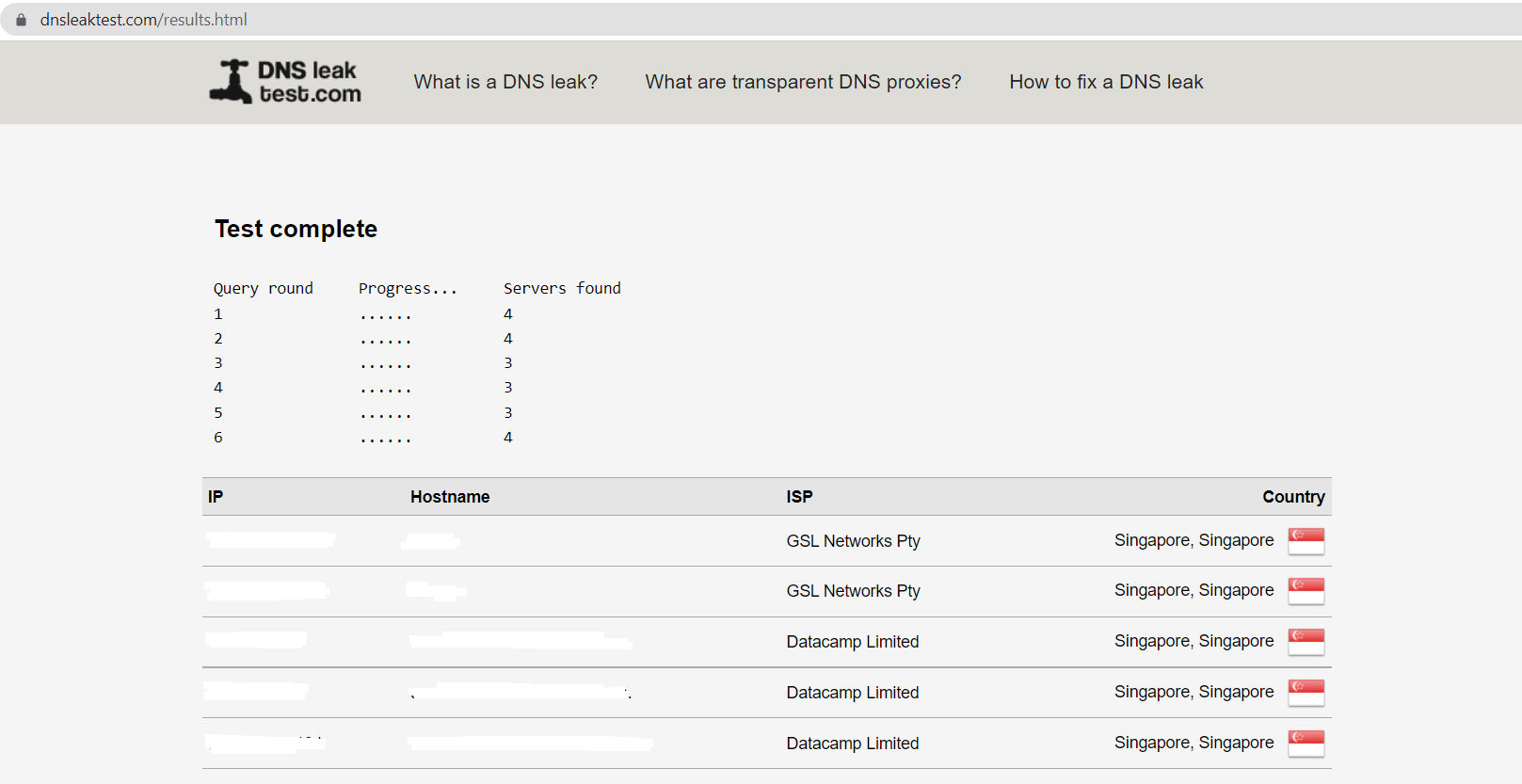
*Dns Leak Test always shows 5 VPN Server
-
 T thebabufrik referenced this topic on
T thebabufrik referenced this topic on
-
@thebabufrik If info I have is correct all your WG tunnels are going to be sourced from the same WAN interface so you may not have true failover if that interface goes down. Can you confirm this?
I am trying desperately to build a fault tolerant setup with two WAN connections and two WG tunnels each of one using a different WAN interface but it is not working for me: both WG tunnels build from the same WAN interface (the default gateway) so that, if that interface goes down, both WG tunnels go down too breaking the whole setup.
-
Sorry, for the late reply. I have 3 WANs: 2 WANs with 2 WG Tunnels per WAN, and 1 WAN with 1 WG Tunnel.
-
@thebabufrik Thanks for your reply.
Sorry but I still do not catch up. In that screen you are telling pfSense to allow traffic from a given WAN interface going to a given destination alias to pass but I think that you are not redirecting anything (unless I am wrong, of course). The traffic the rule applies to is already in that interface.
That means that unless there is another static or dinamic route configured elsewhere, traffic is going to use the default gateway to go out. And, more specifically, WG traffic of any of the defined WG VPNs is going to use the default gateway to go out and thus to build the tunnel.
This should be seen in your VPN provider (the remote end of those WG tunnels) that should show the remote IP address of the WG tunnels you have built; are they being sourced from your different WAN interfaces IPs or are all them built from the same IP address?
In my case both tunnels are being sourced from the same IP address no matter what I try in the 'source' pfSense. And I know because the remote device WG status screen was showing IP address of WAN interface in both connections, not the IP addresses of WAN and WAN2 interfaces.
And as the WG tunnel destination in my case is the same (not different public IPs but a single remote branch location with a single public IP address) I have no way, that I am aware of or that I can imagine, to force WG to use a different WAN interface to build the VPN.
Having seen your success story I asked myself how you did to bind a given WG tunnel to a given WAN interface.
-
Sorry, I see this post is quite old but I just stumbled across your setup and I am wondering how you configured the "WG0X" interfaces in your screenshots.
If I understand correctly, the NordVPN interface always has to have 10.5.0.1 as its IP, so I get error messages upon creating those interfaces.
Any help is greatly appreciated!
Thanks! -
@mikee said in Multi WAN, Multi Tunnels (& Peers) Wireguard VPN - Load Balancing & Failover:
WG traffic of any of the defined WG VPNs is going to use the default gateway to go out and thus to build the tunnel.
This should be seen in your VPN provider (the remote end of those WG tunnels) that should show the remote IP address of the WG tunnels you have built; are they being sourced from your different WAN interfaces IPs or are all them built from the same IP address?@mikee did you find an answer to this? i.e. binding a wg tunnnel to an specific wan / exit gw?
-
@umme
You can't create same ip on a gateway because that will overlap, so you have to change the ip on each gateway it doesn't matter what ip as long as interface is the same with the gateway, then try changing listening port per tunnel on wireguard i figured that is nordvpn problem not connecting to peers spend 24 hours trial and error for that, specific endpoint you choose only the endpoint must remain on the default wireguard port.